A cloud management behavior security control method and system
A security control and cloud management technology, applied in the field of cloud computing security, can solve problems such as not improving platform security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
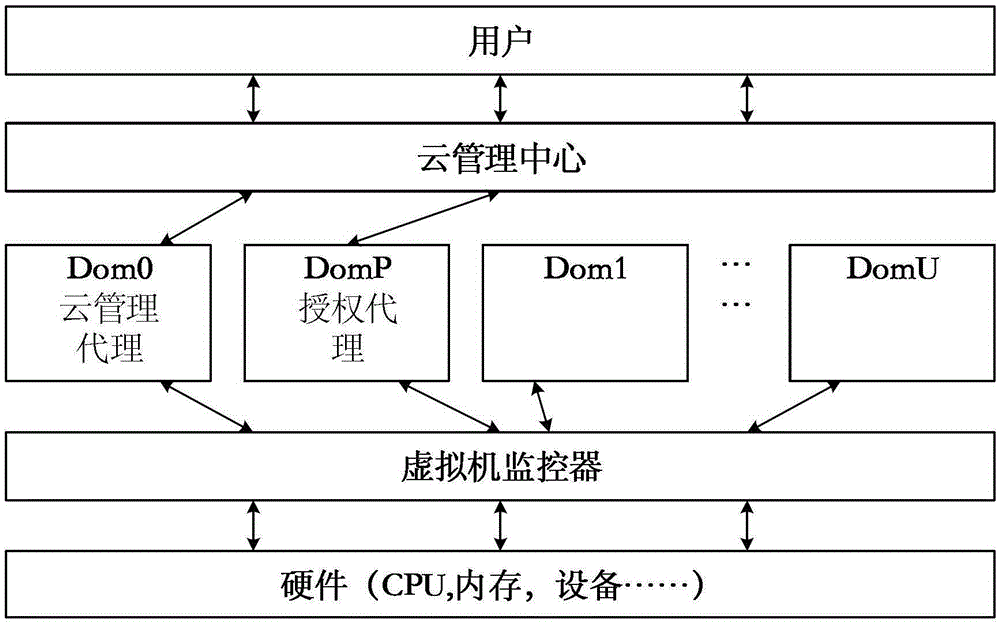
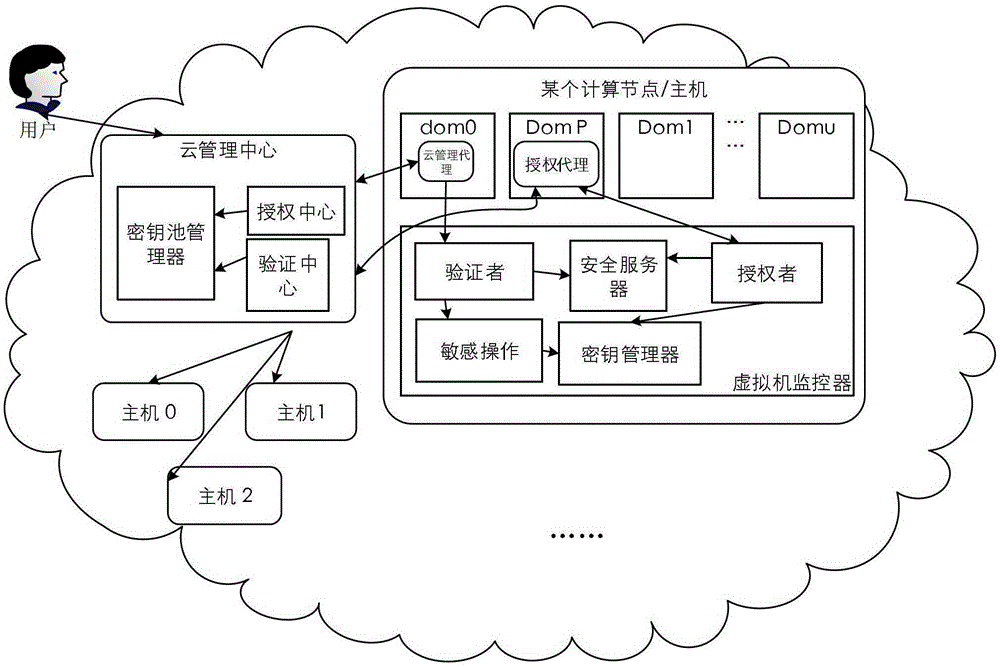
[0053] This paper establishes a trusted path between the cloud management center and the virtual machine monitor. In addition to the protection of the asymmetric key, this paper also adds a separate agent communication domain (DomP) on the virtualization node to reduce The risk of the link being snooped. At the same time, in order to ensure the normal and stable operation of the channel, this paper adds some new modules in the cloud management center and virtual machine monitor to encrypt or authenticate the management information. The main approach is to reduce the trusted computing base of the entire cloud platform. Such as figure 1 As shown, firstly, a new domain DomP is defined in this architecture as a proxy of the CMS, and all these secret and authentication information are transmitted through the authorized proxy. In addition, in order to allow CMS to strictly control the entire cloud, this article has added four components to the Xen virtual machine monitor: Verifier...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com