A security path planning method and device for a mobile terminal
A mobile terminal, security path technology, applied in the field of communication, can solve the problems of not considering attack avoidance, leakage of user location privacy, and overall performance is unsatisfactory.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
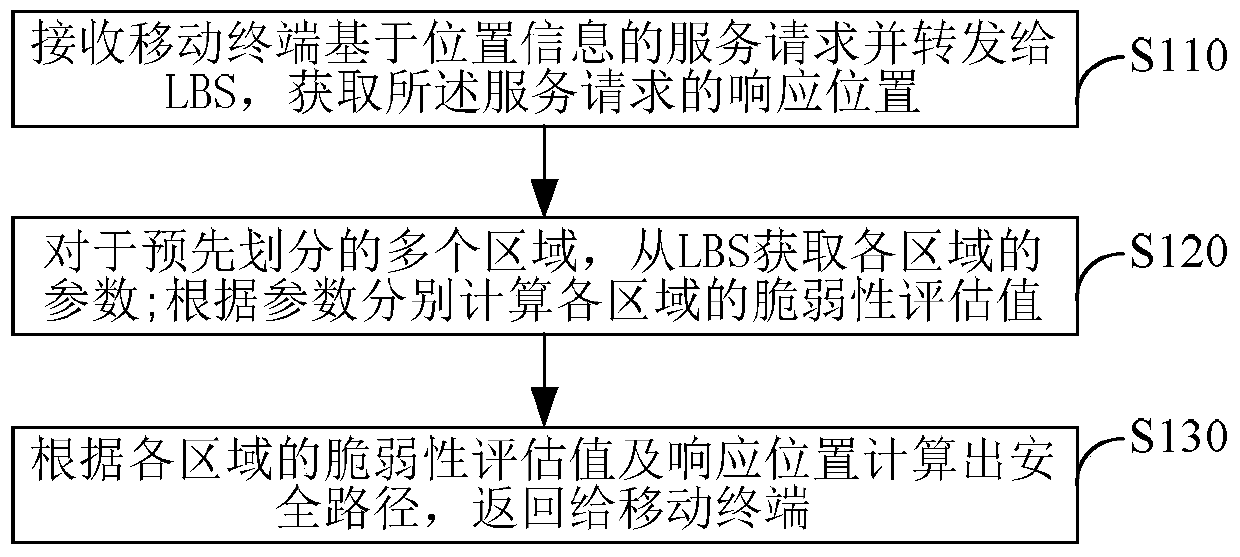
[0037] Embodiment 1. A safe path planning method for a mobile terminal, such as figure 1 Shown, including:
[0038] S110. Receive a service request based on the location information of the mobile terminal and forward it to a location-based server LBS, and obtain a response location of the service request from the LBS;
[0039] S120. For multiple pre-divided areas, obtain parameters of each area from the LBS; the parameters include the area size of the area, the number of mobile terminals entering and leaving the area within a predetermined time period, and each mobile terminal in the area at the current moment The customized desired privacy level; the vulnerability assessment value of each area is calculated according to the parameters;
[0040] S130. Calculate a safe path according to the vulnerability assessment value of each area and the response location, and return it to the mobile terminal; the safe path is from the current location of the mobile terminal to the response locati...
Embodiment 2
[0054] Embodiment 2. A secure path planning device for a mobile terminal includes:
[0055] The location obtaining module is configured to receive a service request based on the location information of the mobile terminal and forward it to the location-based server LBS, and obtain the response location of the service request from the LBS;
[0056] The evaluation module is used to obtain the parameters of each area from the LBS for a plurality of pre-divided areas; the parameters include the area size of the area, the number of mobile terminals that enter and leave the area within a predetermined time period, and the current time in the area The expected privacy level customized by each mobile terminal; calculate the vulnerability assessment value of each area according to the parameters;
[0057] The path calculation module is configured to calculate a safe path based on the vulnerability assessment value of each area and the response location, and return it to the mobile terminal; t...
Embodiment 3
[0065] Embodiment 3. A safe path planning system for a mobile terminal includes:
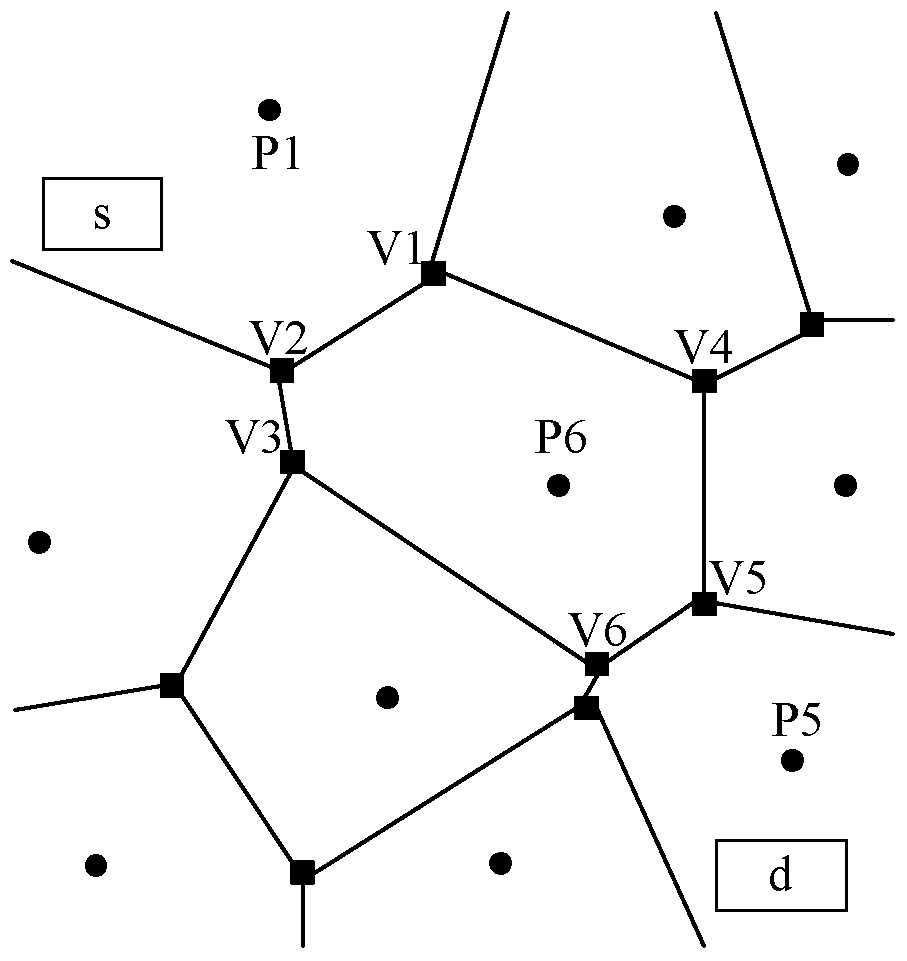
[0066] Location-based servers (LBS), trusted third parties (TTP) and mobile terminals. The functions of the three parts are as follows: the user uses the mobile phone as a mobile terminal to provide services based on geographic location information; TTP is a key part of the system, and the main function is to realize the anonymous operation of the service request submitted by the user and the vulnerability assessment of the system Work and dynamic path planning work; LBS provides services based on geographic location information, such as responding to the geographic location coordinates of the nearest restaurant and sending real-time traffic information.
[0067] The workflow of the entire system can be roughly divided into six steps, the specific steps are as follows:
[0068] ① The user makes a service request based on location information through a mobile terminal, such as finding the nearest hotel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com