A Signcryption Method from Certificateless Environment to Public Key Infrastructure Environment
A public key infrastructure and certificate-free technology, applied in the field of heterogeneous signcryption, can solve problems such as unusability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in detail below in conjunction with the accompanying drawings.
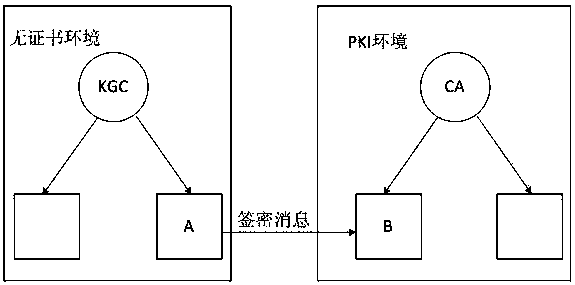
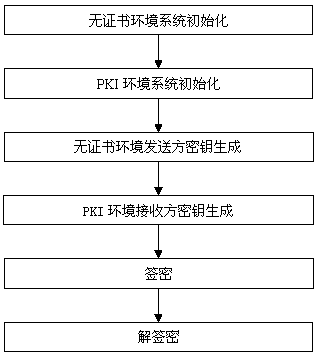
[0036] Such as figure 1 , 2 As shown, the present invention provides a heterogeneous signcryption method from a certificateless environment to a public key infrastructure environment, and the specific process of the present invention is as follows:
[0037] Step 1. Initialize the system in the non-certificate environment.
[0038] Security parameter k 1-1 is an integer, and the generator is P 1-1 An additive cyclic group G of 1-1 and a multiplicative cyclic group G 2-1 , the orders of both groups are prime numbers q 1-1 . e 1 :G 1-1 ×G 1-1 →G 2-1 is a bilinear map. Define four secure Hash functions h 2 :{0,1} * →{0,1} l , where {0,1} * Represents a collection of binary sequences of arbitrary bit length, Represents the additive group obtained by removing the identity element, {0,1} l Indicates a set of binary sequences with a bit length l, and l i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com