Cloud storage data deduplication method based on identity proxy re-encryption
A proxy re-encryption and cloud storage technology, applied in the field of data processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
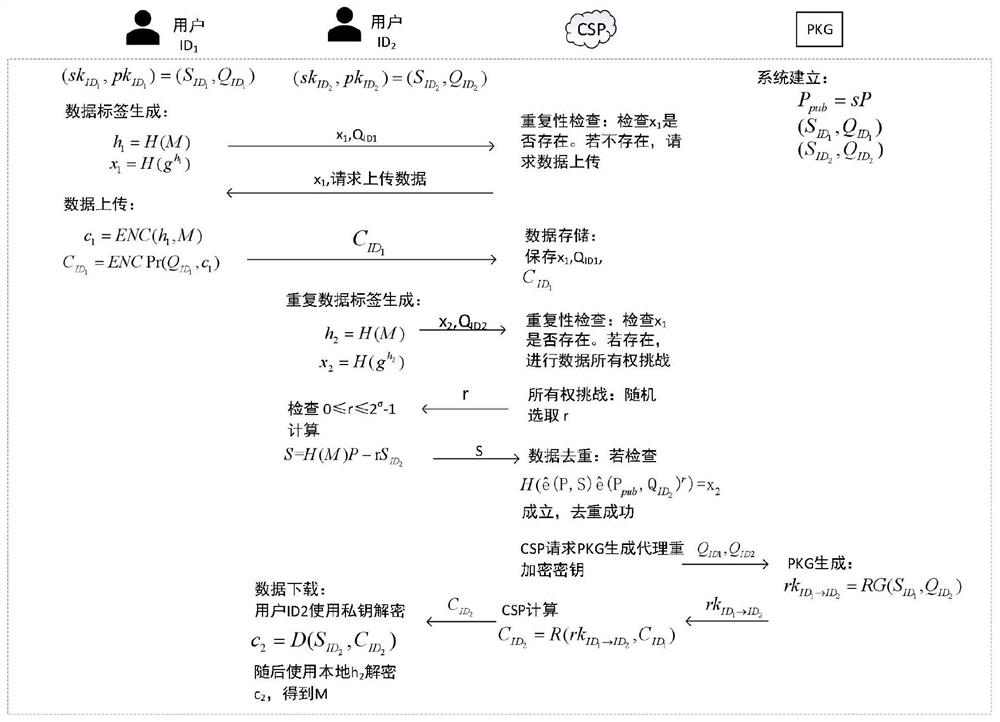
[0031] By the following figure 1 The present invention is further described, and the following examples are for more clearly illustrative of the technical solutions of the present invention without limiting the scope of the invention.
[0032] Step 1: Set system parameters and initialize the system;
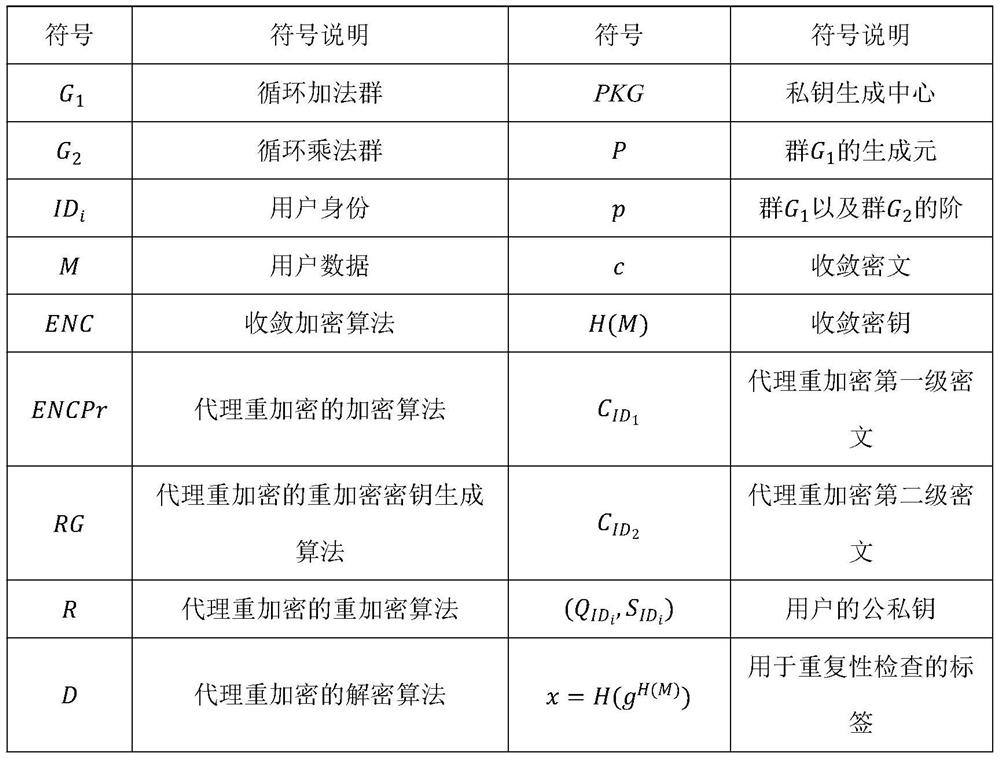
[0033] Set G 1 Circular addition groups generated by P, steps of p, g 2 In order to have the cyclic multiplication group with the same order P, For a bilinear mapping. Define five secure Hash functions h 1 : {0,1} * → g 1 , Hide 3 : G 2 × {0,1} * → g 1 H 4 : G 2 × g 1 × {0,1} * → g 1 , Setting parameters PKG randomly selects a master key Calculate P pub = SP. PKG public system parameters Confidential master key S.
[0034] For the user ID 1 , ID 2 , PKG calculates user private key, respectively. And send it to the user in a safe way. here,
[0035] Step 2: Data label generation;
[0036] User ID 1 Generate the label of the data M, send Give CSP and save h 1 = H 2 (M), used ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com