Method for sharing same authentication equipment by multiple persons based on certificate KEY
A technology for authenticating equipment and certificates, applied in the direction of user identity/authority verification, etc., can solve problems such as inability to recognize certificates, and achieve fingerprint and hardware authentication security and confidentiality, and fingerprint and hardware authentication are more effective
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] This embodiment is a preferred implementation mode of the present invention, and other principles and basic structures that are the same or similar to this embodiment are within the protection scope of the present invention.
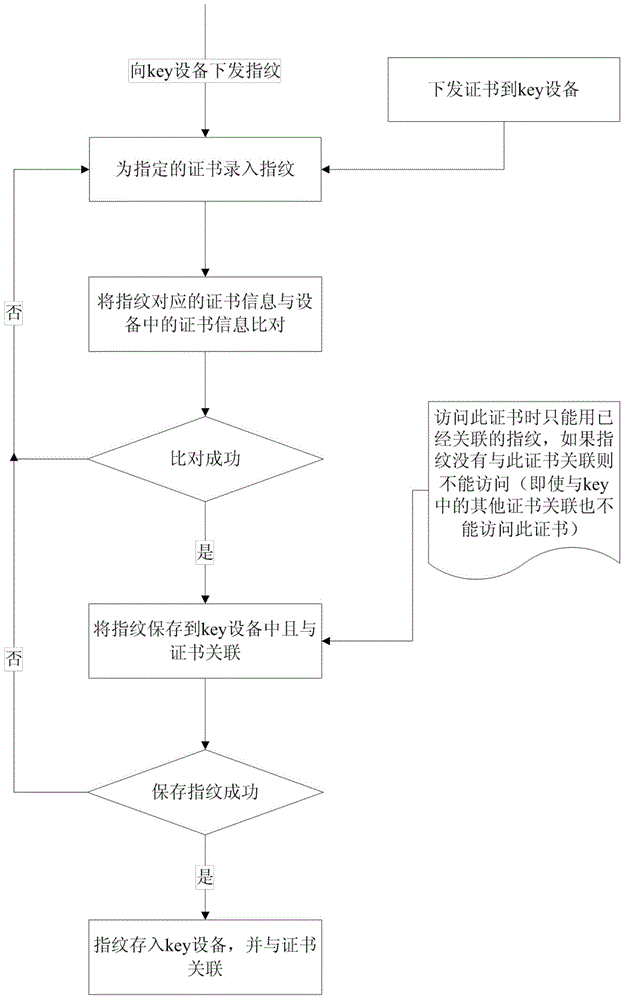
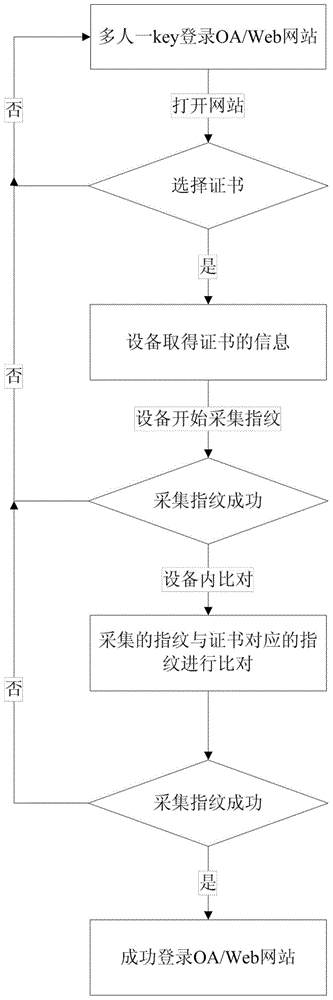
[0025] The present invention is a method for multiple people to share a key device, which associates the fingerprints and certificates stored in the key device, and realizes the advantage of using a key device for multiple people, and effectively This improves the utilization of the key device. The present invention mainly includes issuing certificates and fingerprints to the key device and the login process of logging into OA / web sites using the present invention.
[0026] Please see attached figure 1 , the present invention issues certificates and fingerprints to the key device as follows:
[0027] Step A1: Issue a certificate to the key device through the certificate structure, and there can be one or more certificates;
[0028] Step A2: Col...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com