Method and device for protecting process and electronic device
A process and target process technology, applied in the field of information security, can solve problems such as the inability to effectively prevent the security protection efficiency of the operating system, and achieve the effect of improving security protection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
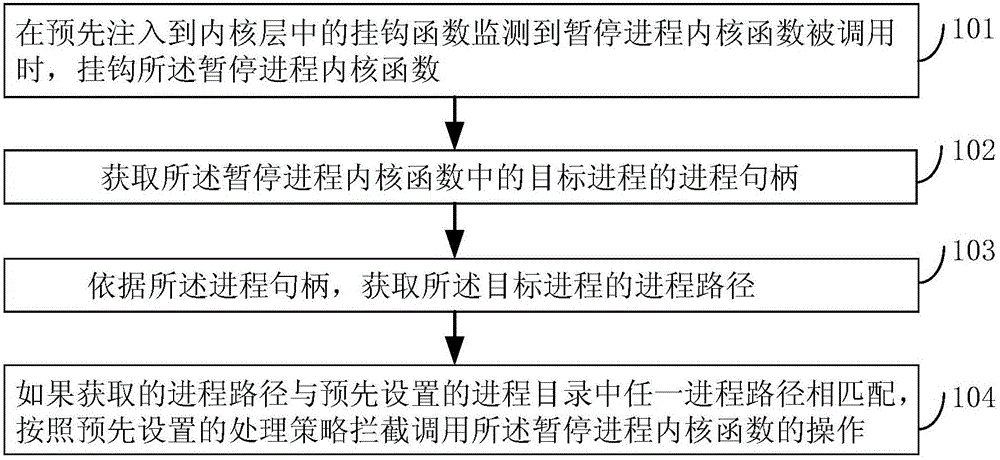
[0061] figure 1 It is a schematic flow diagram of a method for protecting a process in an embodiment of the present invention, such as figure 1 As shown, the method of this embodiment may include:
[0062] Step 101, when the hook function pre-injected into the kernel layer detects that the suspended process kernel function is called, hook the suspended process kernel function;
[0063] In this embodiment, as an optional embodiment, the suspend process kernel function is the NtSuspendProcess kernel function, which is used to suspend execution of the target process, that is, to suspend processing.
[0064] In this embodiment, the hook (Hook) function of injection is used to monitor the relevant operation (the operation of suspending process) of suspending process kernel function, intercepts this relevant operation, and in the target process corresponding to relevant operation and preset process directory When the process matches, the injected hook function will process the rel...
Embodiment 2
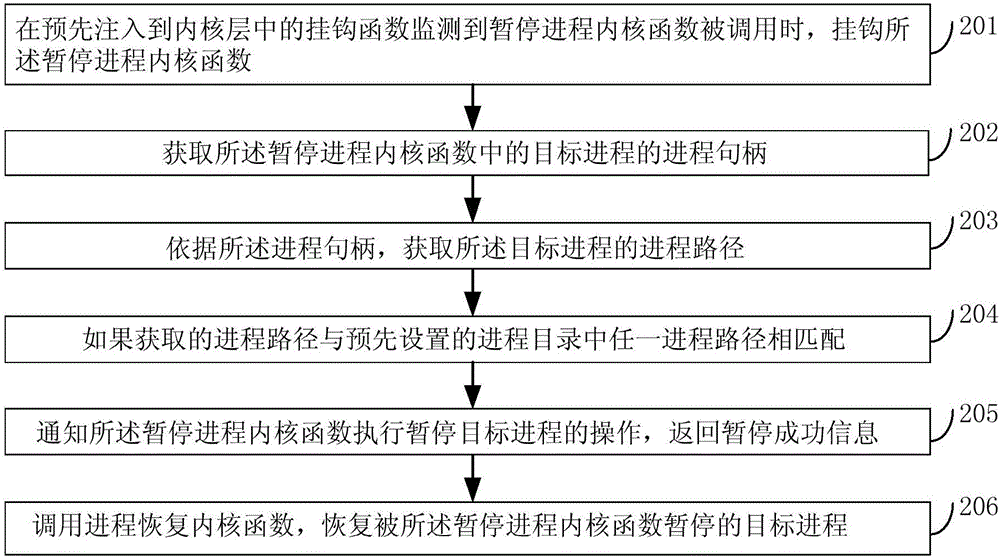
[0103] figure 2 It is a schematic flow diagram of a method for protecting a process in Embodiment 2 of the present invention, such as figure 2 As shown, the method of this embodiment may include:
[0104] Step 201, when the hook function pre-injected into the kernel layer detects that the suspended process kernel function is called, hook the suspended process kernel function;
[0105] Step 202, obtaining the process handle of the target process in the kernel function of the suspended process;
[0106] Step 203, obtain the process path of the target process according to the process handle;
[0107] In this embodiment, the processes from step 201 to step 203 are respectively similar to steps 101 to 103 in the first method embodiment, and will not be repeated here.
[0108] Step 204, if the obtained process path matches any process path in the preset process directory;
[0109] Step 205, notify the suspend process kernel function to perform the operation of suspending the t...
Embodiment 3
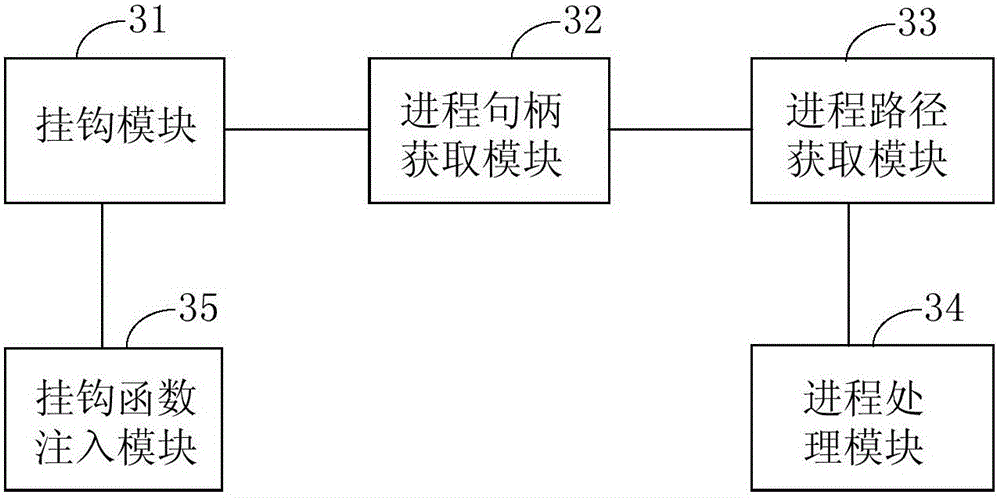
[0113] image 3 It is a schematic diagram of the device structure of the third protection process of the embodiment of the present invention, such as image 3 As shown, the device in this embodiment may include: a hook module 31, a process handle acquisition module 32, a process path acquisition module 33, and a process processing module 34, wherein,
[0114] The hook module 31 is used to hook the suspended process kernel function when the hook function injected into the kernel layer in advance monitors that the suspended process kernel function is called;
[0115] In this embodiment, as an optional embodiment, the suspend process kernel function is the NtSuspendProcess kernel function, which is used to suspend execution of the target process, that is, to suspend processing.
[0116] In this embodiment, the hook function can be programmed in any language that can realize the corresponding functions in the subsequent steps of this embodiment. For example, it can be programmed ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com