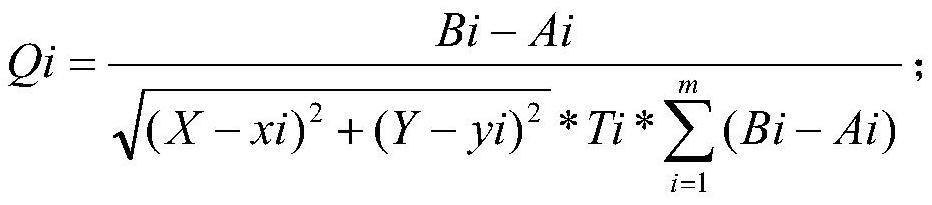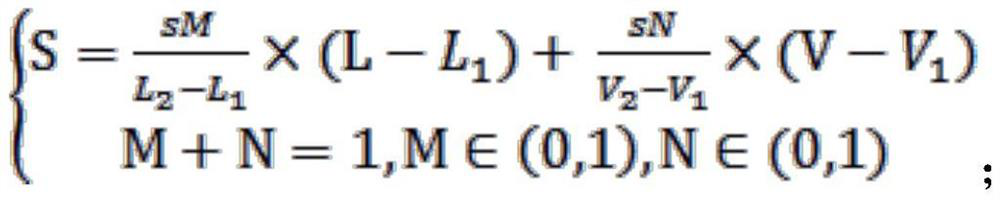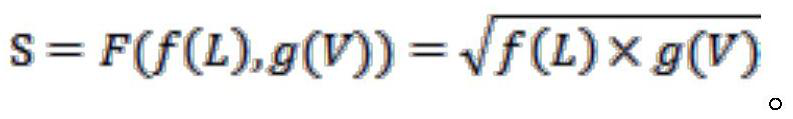Patents
Literature
36results about How to "Improve security protection efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
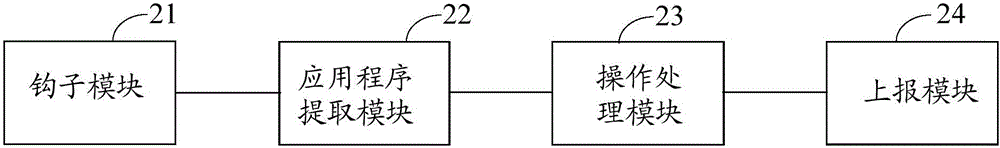
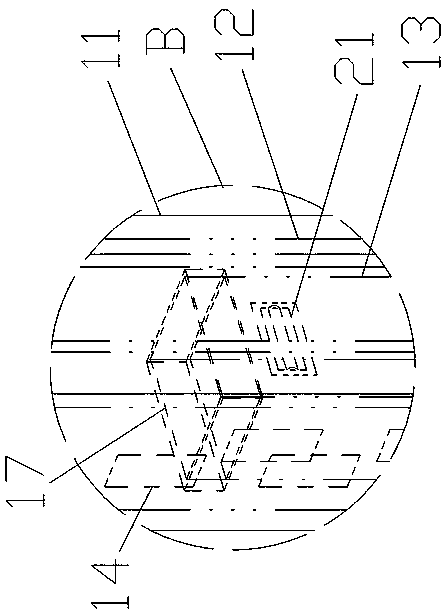
Screenshot processing method and device and electronic equipment
ActiveCN106201468AImprove security protection efficiencySolve the problem of low security protection efficiencyExecution for user interfacesOperational systemProtocol Application
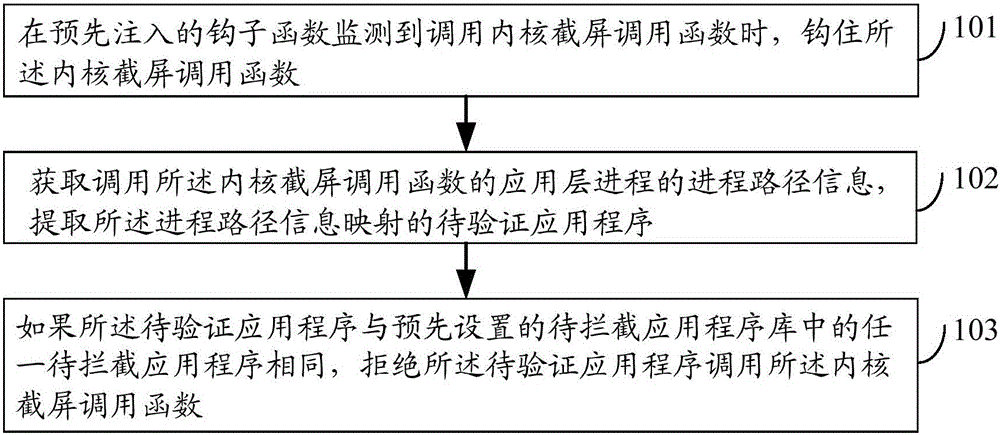
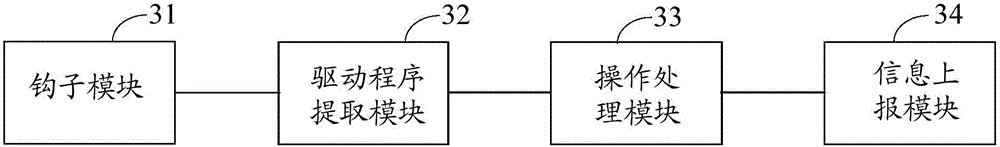
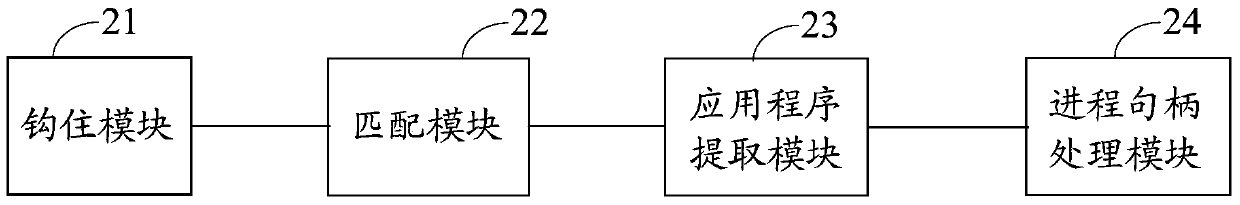
Embodiments of the invention disclose a screenshot processing method and device and electronic equipment, relates to a technology of information safety, and aims at improving the safety protection efficiency of operation systems. The screenshot processing method comprises the following steps of: when a kernel screenshot calling function is monitored in pre-injected hook functions, hooking the kernel screenshot calling function; obtaining progress path information for calling an application layer progress of the kernel screenshot calling function, and extracting a to-be-verified application program mapped by the progress path information; and if the to-be-verified application program is same as any to-be-intercepted application program in a preset to-be-intercepted application program library, rejecting the to-be-verified application program to call the kernel screenshot calling function. The method, the device and the electronic equipment are suitable for carrying out safety monitoring on environment screenshot of the operation systems.
Owner:ZHUHAI BAOQU TECH CO LTD
Method and device for protecting driving program, and electronic device
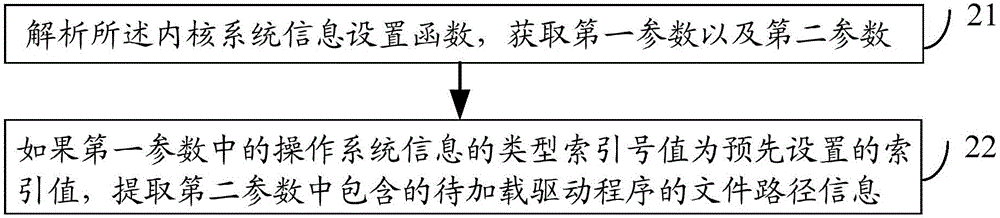
ActiveCN105844146AImprove security protection efficiencyImprove securityComputer security arrangementsOperational systemProtocol Application
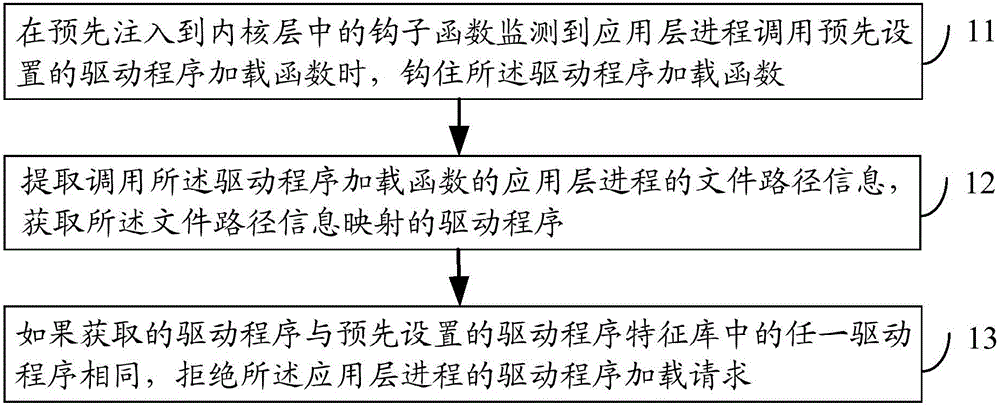
The embodiment of the invention discloses a method and device for protecting a driving program, and an electronic device. The method comprises: hooking a driving program loading function when a hook function pre-injected into an inner nuclear layer function monitors that an application layer process invokes the preset driving program loading function; extracting a file path information of the application layer process invoking the driving program loading function and acquiring a driving program mapped with the file path information; and refusing a driving program loading request of the application layer process if the acquired driving program is the same as any one driving program in a preset driving program characteristic database. By applying the method, device and the electronic device, safety protection efficiency of an operation system can be improved.
Owner:ZHUHAI BAOQU TECH CO LTD
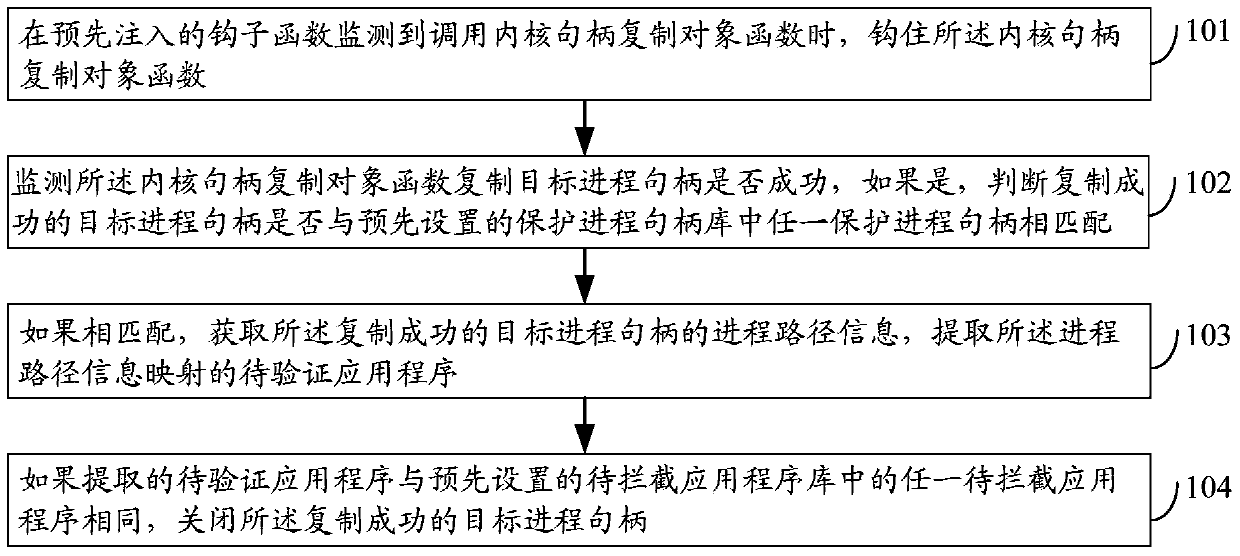
Duplicating information processing method and device, and electronic equipment
ActiveCN106203077AImprove security protection efficiencySolve the problem of low security protection efficiencyPlatform integrity maintainanceInformation mappingElectric equipment
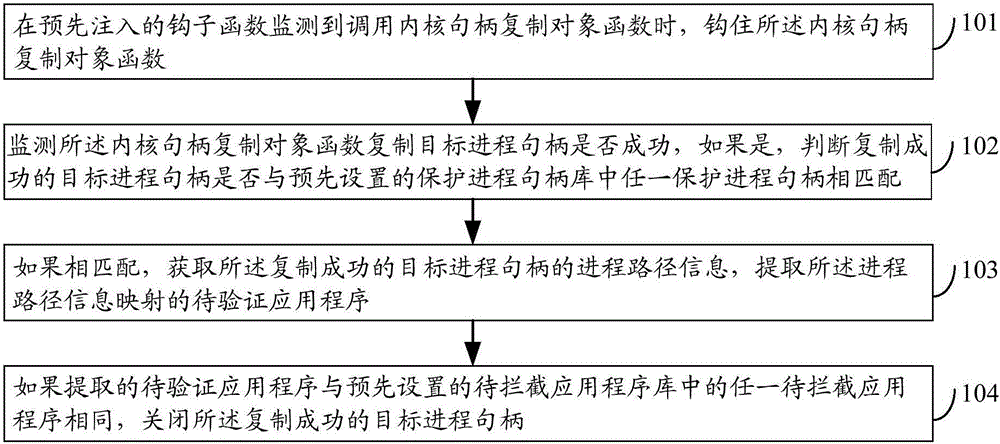
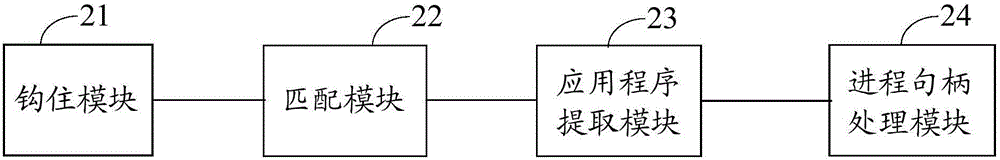
The embodiment of the invention discloses a duplicating information processing method and device, and electronic equipment, relates to the technology of information safety, and can improve the safety protection efficiency of an operating system. The method comprises the following steps: when the calling of a kernel DuplicateHandle object function is monitored in a pre-injected hook function, hooking the kernel DuplicateHandle object function; monitoring whether the kernel DuplicateHandle object function succeeds in duplicating a target process handle or not, and if the kernel DuplicateHandle object function succeeds in duplicating the target process handle, judging whether the target process handle which succeeds in duplicating is matched with any one protection process handle in a preset protection process handle library or not; if the target process handle which succeeds in duplicating is matched with any one protection process handle in the preset protection process handle library, obtaining the process path information of the target process handle which succeeds in duplicating, and extracting a to-be-verified application program mapped by the process path information; and if the extracted to-be-verified application program is the same with any one to-be-intercepted application program in a preset to-be-intercepted application program library, closing the target process handle which succeeds in duplicating. The duplicating information processing method and device is suitable for monitoring whether the target process handle is illegally duplicated or not.
Owner:ZHUHAI BAOQU TECH CO LTD
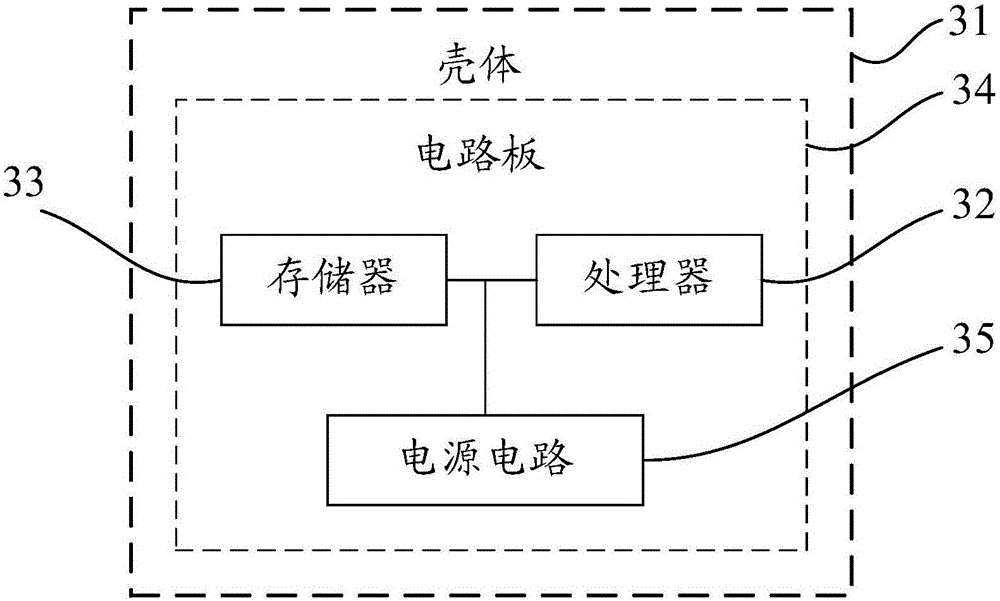
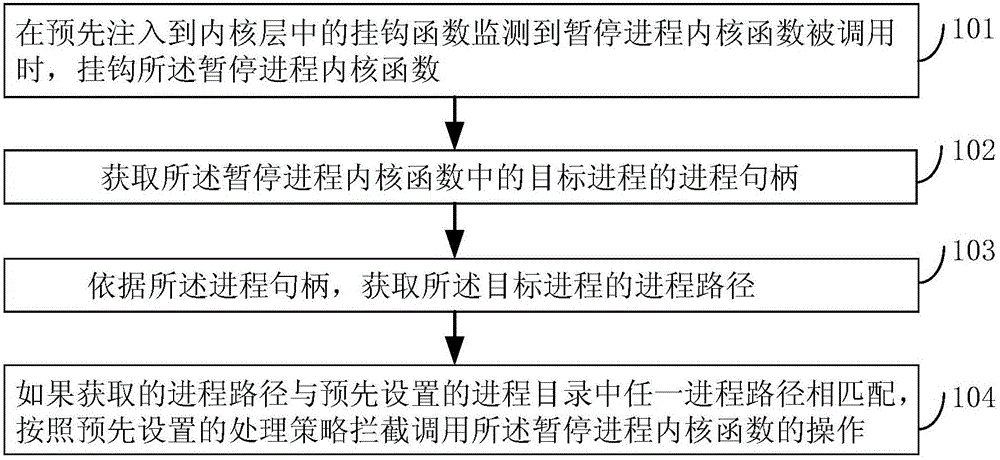
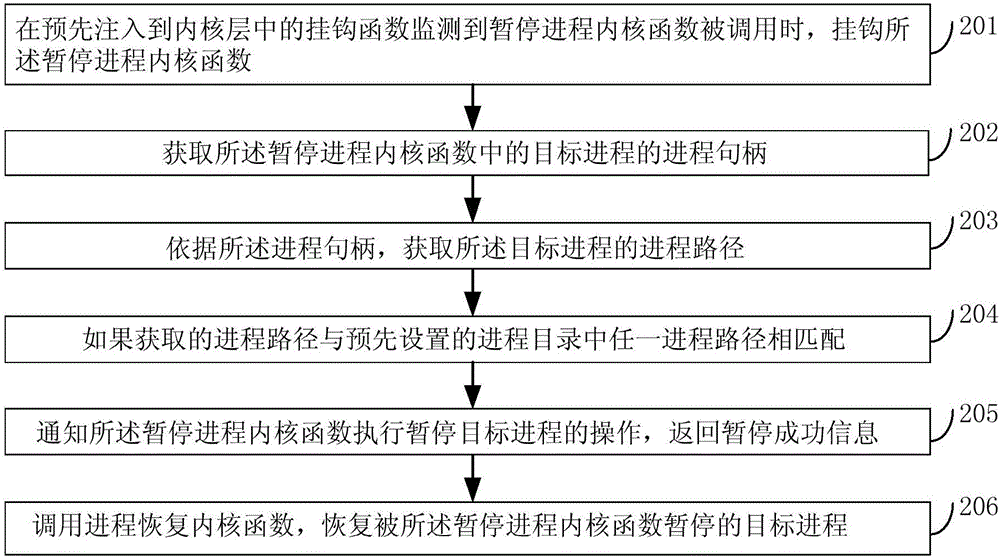
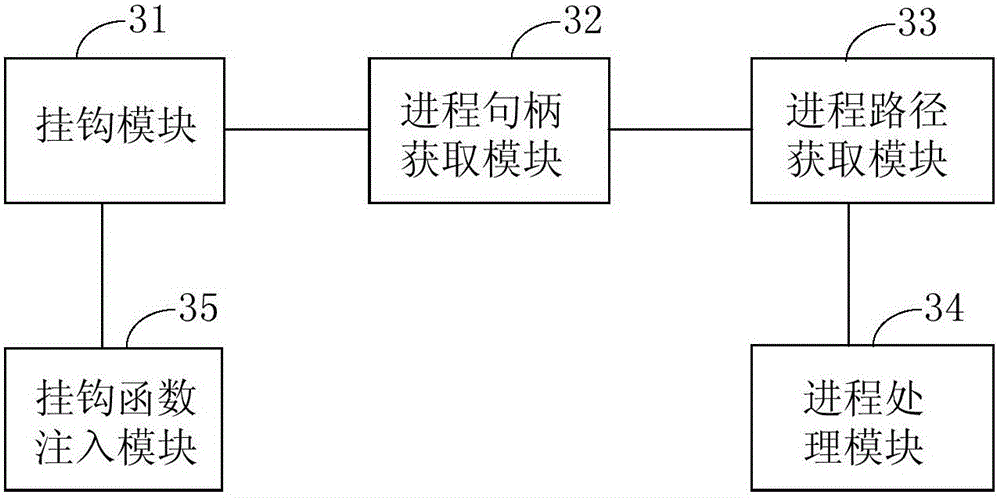
Method and device for protecting process and electronic device
InactiveCN106127031AImprove security protection efficiencySolve the problem of low security protection efficiencyPlatform integrity maintainanceInformation securityElectric equipment
The embodiment of the invention discloses a method and device for protecting process and an electronic device, and relates to the information security technology. The safety protection efficiency of an operation system can be improved. The method includes the steps that when a hook function pre-injected into a kernel layer monitors that a process pausing kernel function is called, the process pausing kernel function is hooked; a process handle of a target process in the process pausing kernel function is obtained, and according to the process handle, the process path of the target process is obtained; if the obtained process path is matched with any process path in a preset process catalogue, operation for calling the process pausing kernel function is intercepted according to the preset processing strategy. The method and device are suitable for protecting the process.
Owner:ZHUHAI BAOQU TECH CO LTD
Energy storage battery safety protection device and system
InactiveCN113381087AAccurate detectionImprove security protection efficiencyCells structural combinationFire rescueProcess engineeringGas concentration
The invention relates to an energy storage battery safety protection device and system. The temperature information of the battery module and the gas concentration information of the space where the battery module is located are collected through the gas concentration detector and the temperature sensor which are arranged in the cavity. Various fire information is rapidly detected in a small space of a battery PACK level, the thermal runaway state of the lithium battery is judged through the multiple information, and the fire extinguishing agent is automatically released to extinguish fire. The thermal runaway information of the lithium battery can be accurately detected, and the safety protection efficiency is improved.
Owner:环安有备族科技有限公司
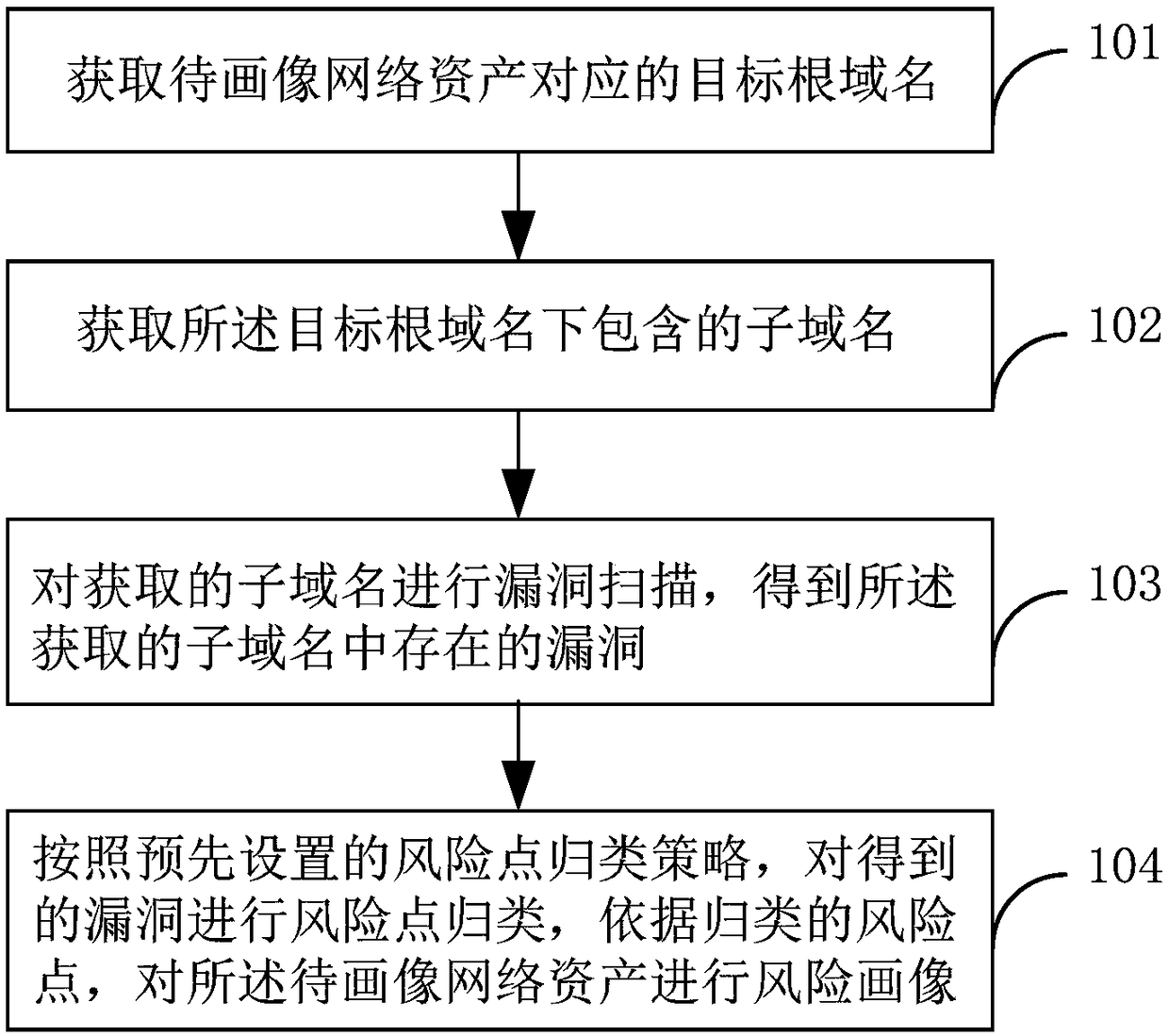
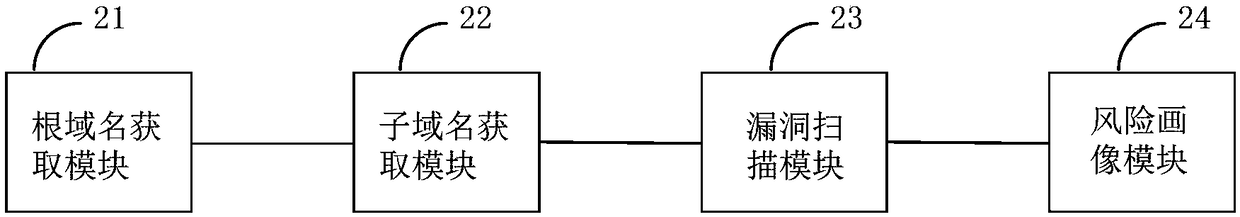
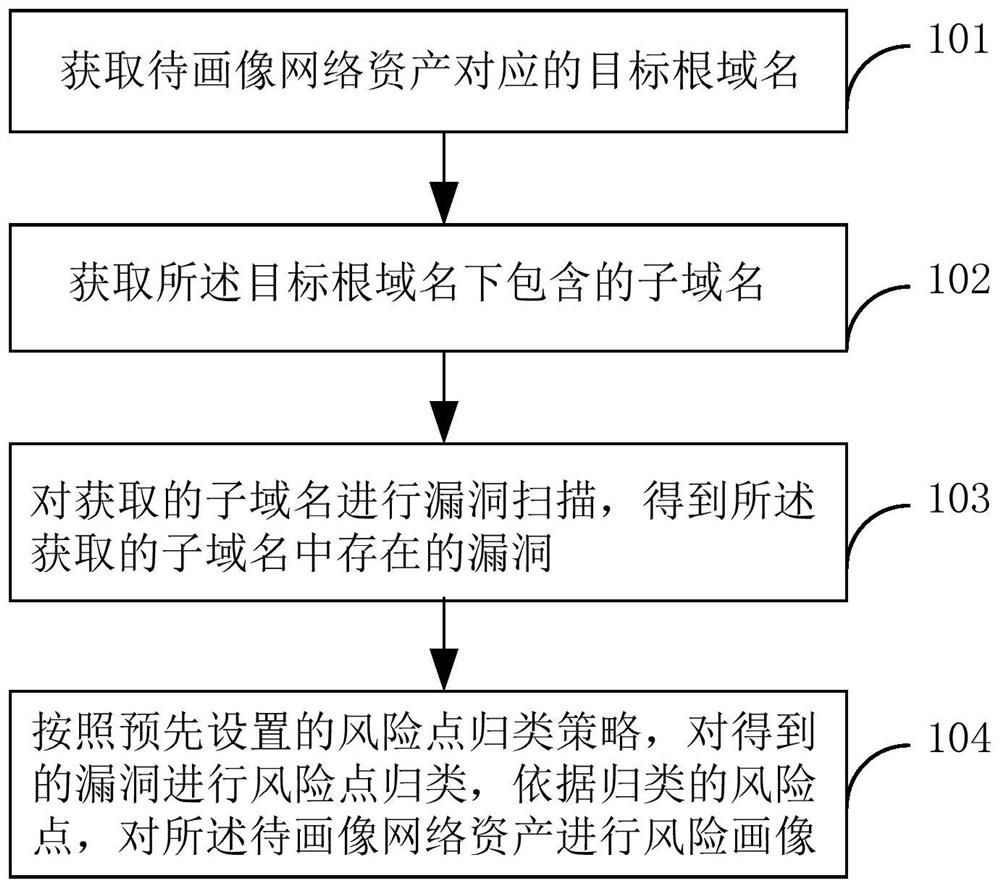
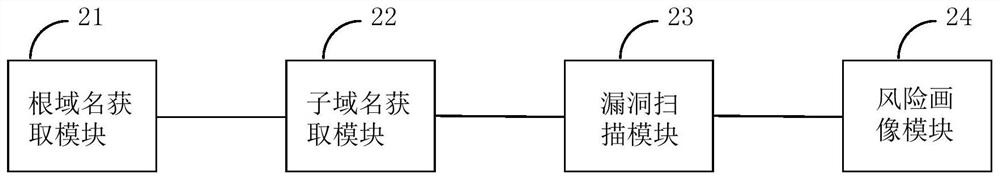
Network asset risk portraying method and device
ActiveCN108809928AImprove security protection efficiencyVulnerabilities discovered in timeTransmissionDomain nameVulnerability scanning
The application provides a network asset risk portraying method and a network asset risk portraying device, capable of improving network security protection efficiency. The network asset risk portraying method comprises: obtaining a target root domain name corresponding to the network asset to be portrayed; obtaining a sub-domain name included in the target root domain name; performing vulnerability scanning on the obtained sub-domain name to obtain vulnerabilities existing in the obtained sub-domain name; classifying the risk points of the obtained vulnerabilities according to the pre-set risk point classification strategy, and performing risk portrait on the network assets to be portrayed according to the classified risk points.
Owner:小安(北京)科技有限公司
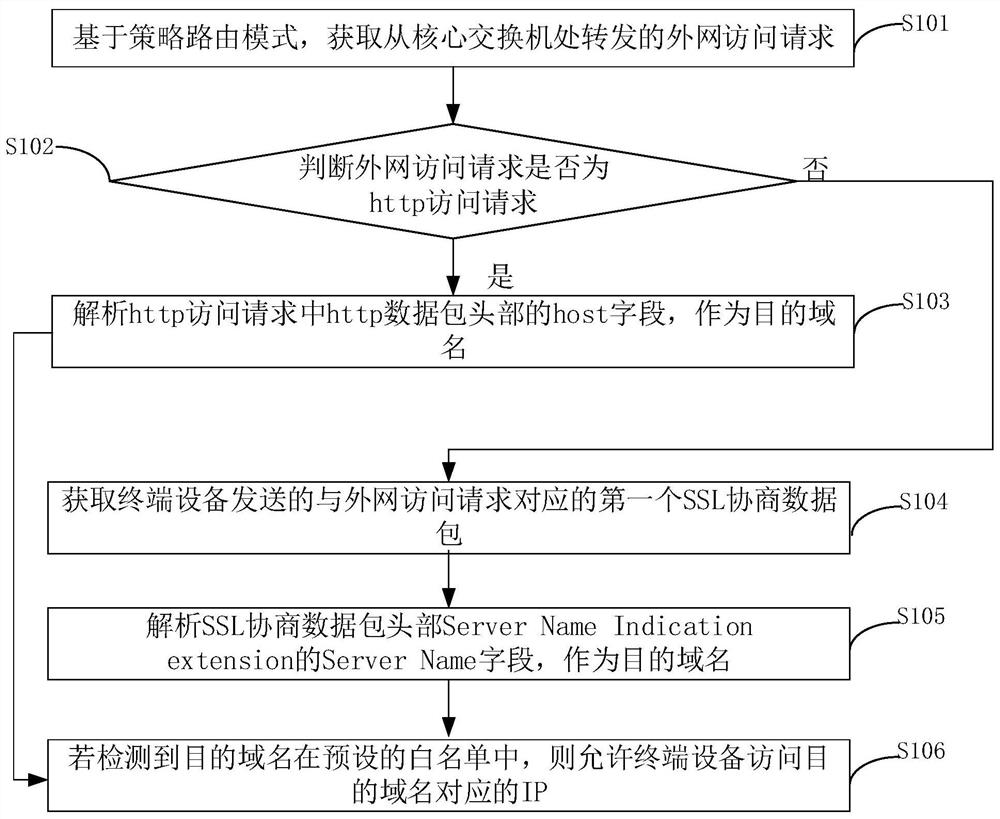
Management and control method, device, equipment and system for intranet malicious reverse connection behavior
ActiveCN111865990AImprove security protection efficiencyEasy to controlTransmissionDomain nameData pack
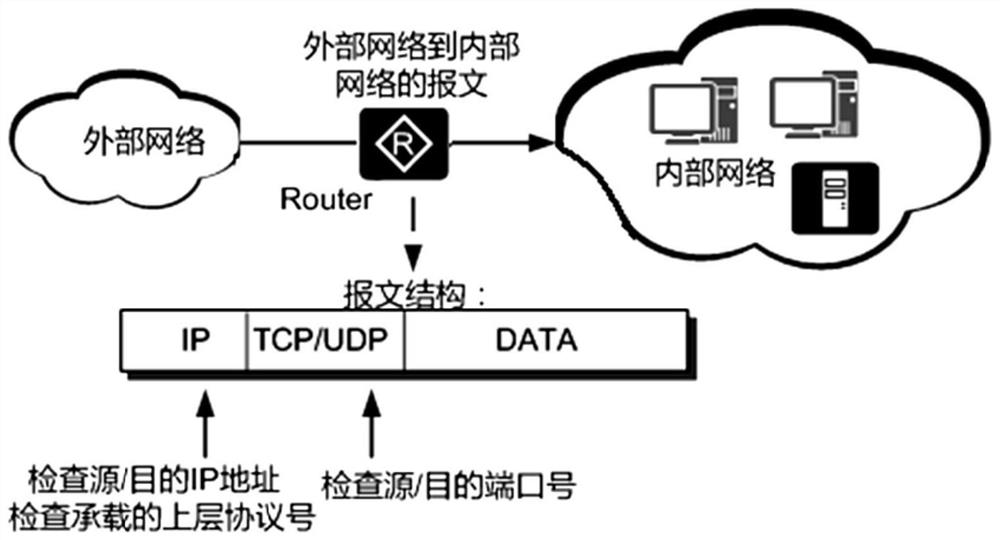
The invention relates to a management and control method, device, equipment and system for an intranet malicious reverse connection behavior. Based on policy-based routing, the method comprises the steps of: obtaining an external network access request forwarded from a core switch, if the external network access request is an http access request, analyzing a host field at the head of the http datapacket in the http access request to take as a target domain name,if the external network access request is an https access request, analyzing a Server Name field of a Server Name Indication extension at the head of the SSL negotiation data packet, taking the Server Name field as a target domain name, and if the target domain name is detected to be in a preset white list, allowing the terminal equipment to access an IP corresponding to the target domain name. According to the invention, security management and control are carried out through the target domain name, error interception caused by IP resolution errors is avoided, the target domain name is obtained without adding a certificate to decrypt the https data packet, all application systems can be covered, and management and controlof malicious reverse connection behaviors of an intranet are realized.
Owner:SHANGHAI ZHONGTONGJI NETWORK TECH CO LTD
Web protection method based on URL self-learning
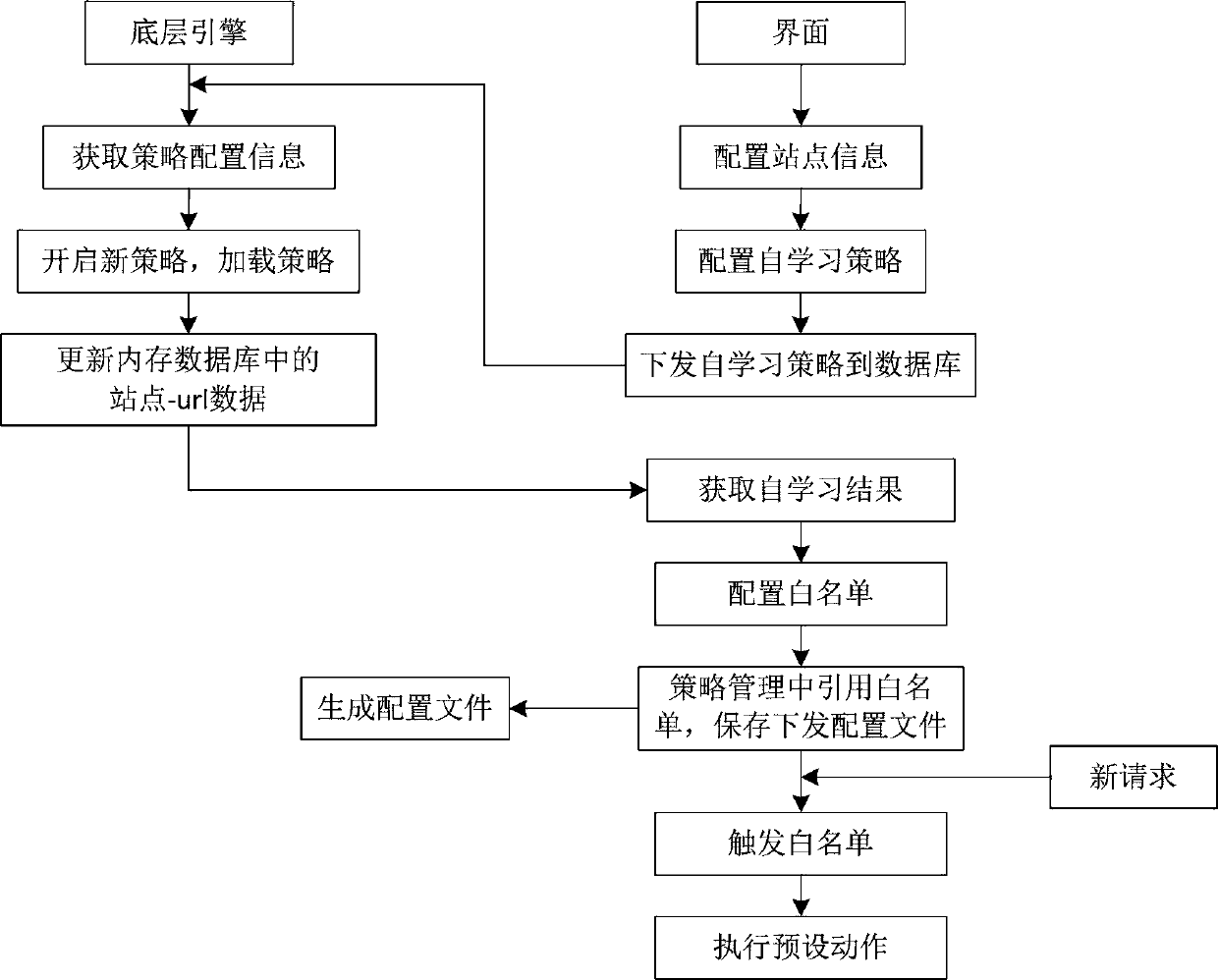
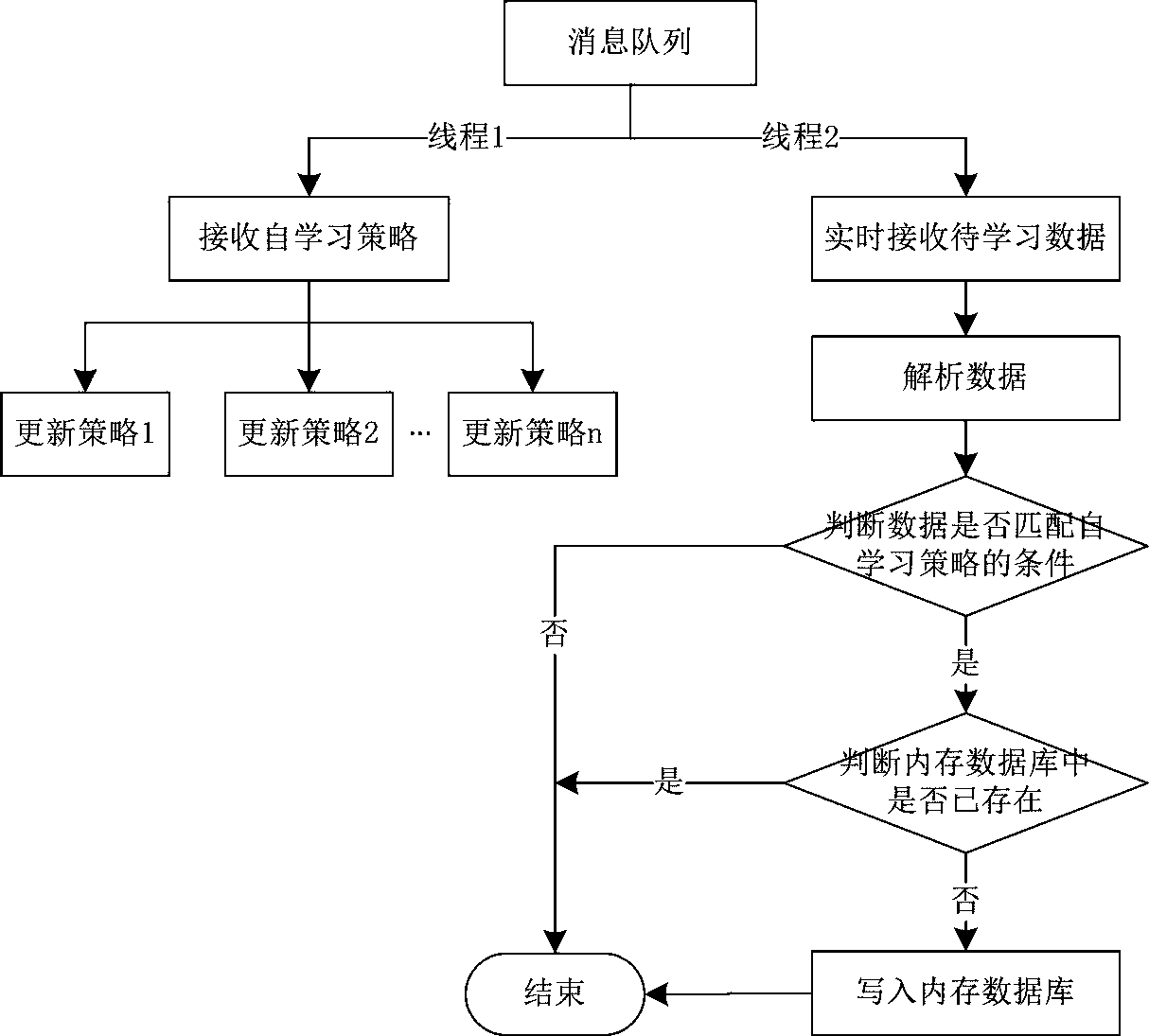
PendingCN111245788AImprove security protection efficiencyGuaranteed real-timeTransmissionIn-memory databaseEngineering
The invention discloses a Web protection method based on URL self-learning, and the method comprises the steps: executing a corresponding preset action when a requested URL triggers a white list, carrying out the URL self-learning and Web safety protection synchronously in real time, and judging whether the requested URL exists in a memory database or not; if yes, transferring the request to a Webserver for response; and if not, loading and executing the self-learning strategy, and updating the self-learning strategy to the memory database. According to the method, URL self-learning and Web protection are synchronously carried out in real time, so that the real-time performance of a learning result is ensured. Learning results are stored in a memory database, the reading speed is high, and the protection efficiency is ensured. An effective period is set for a learning result, and data is cleared for re-learning after expiration, so that the effectiveness of the learning result is ensured, and the Web security protection efficiency is improved.
Owner:西安交大捷普网络科技有限公司
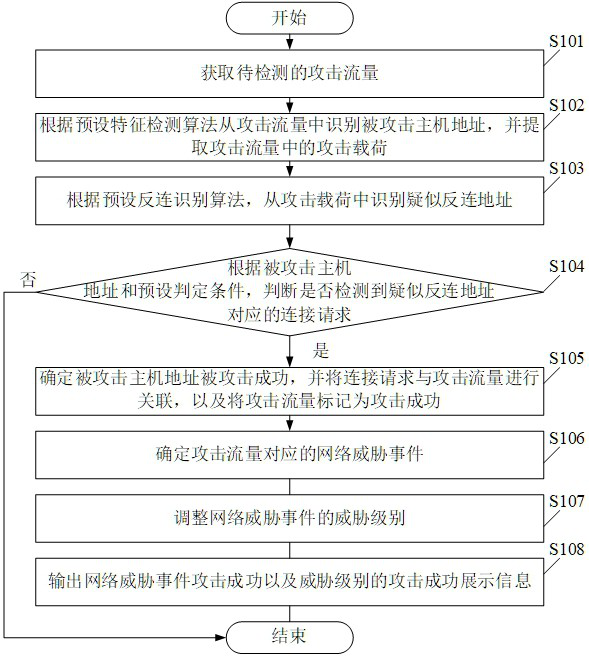
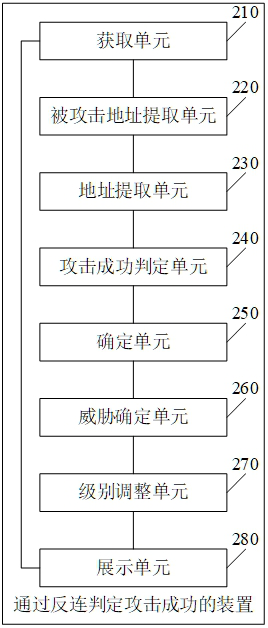
Method and device for judging attack success through reverse connection
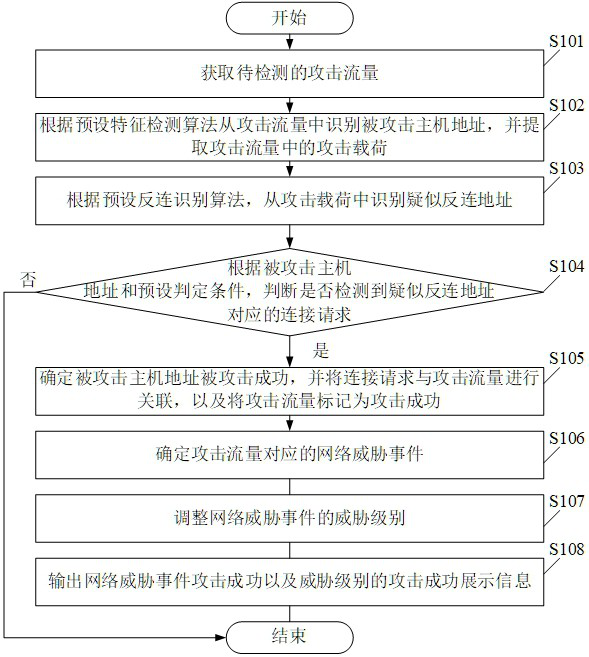
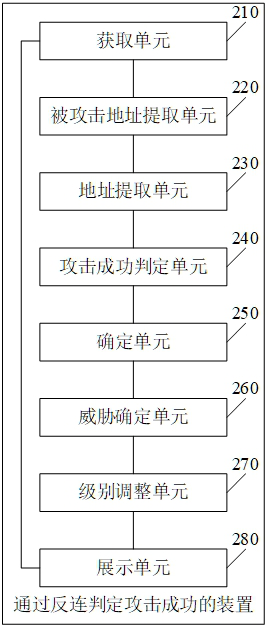
ActiveCN113965419ASolve the discrimination problemAvoid Threat AlertsSecuring communicationInternet privacyAttack
The embodiment of the invention provides a method and device for judging attack success through reverse connection, and the method comprises the steps: obtaining to-be-detected attack traffic, and extracting an attack load in the attack traffic and an attacked host address corresponding to the attack traffic; then extracting a suspected reverse connection address in the attack load; judging whether a connection request corresponding to the suspected reverse connection address is detected or not according to the address of the attacked host and a preset judgment condition; and if yes, determining that the attacked host address is successfully attacked, so that the problem of judging the success of the network attack can be solved, a large number of threat alarms are avoided, and the security protection efficiency is improved.
Owner:北京微步在线科技有限公司
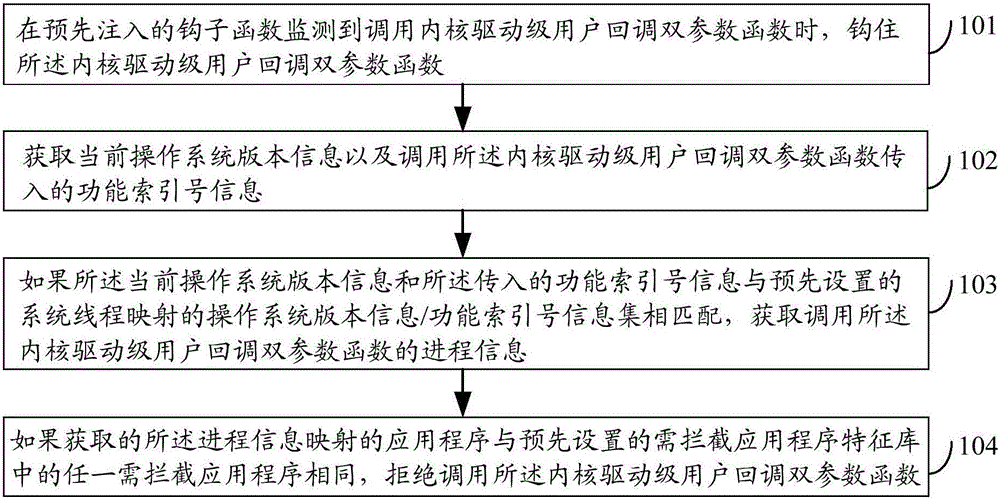
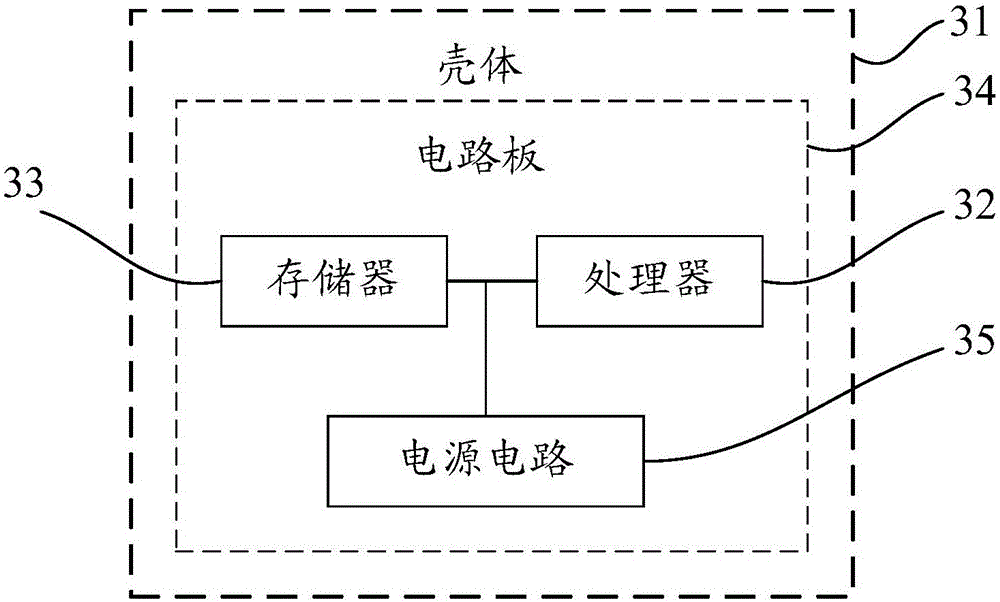
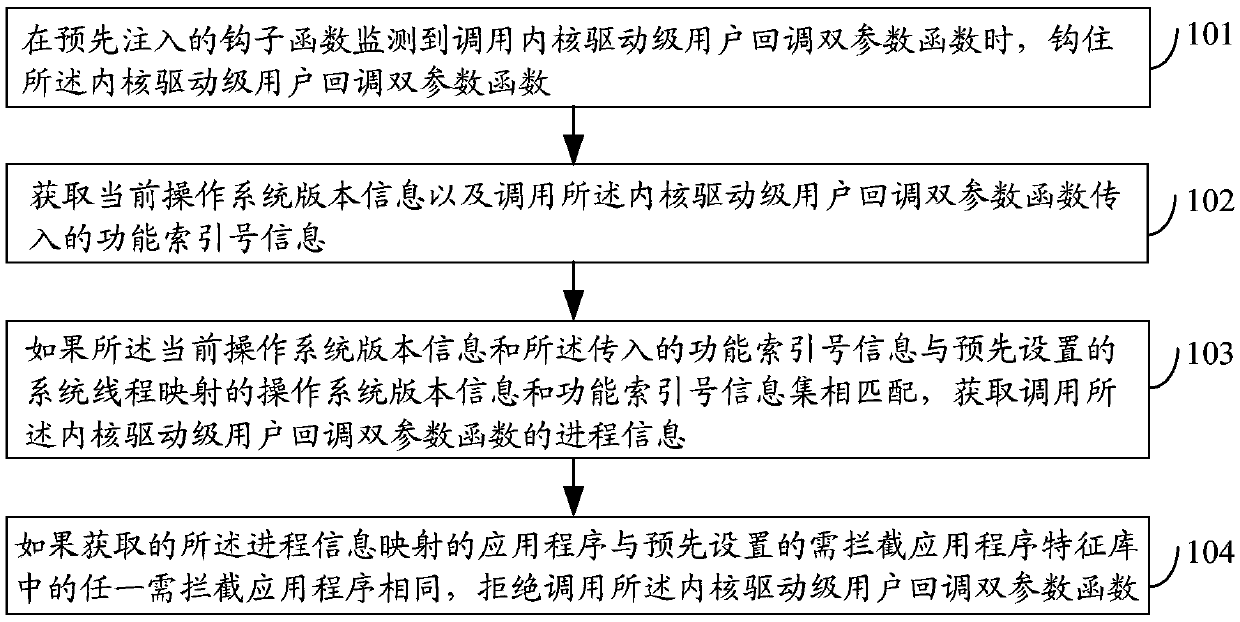
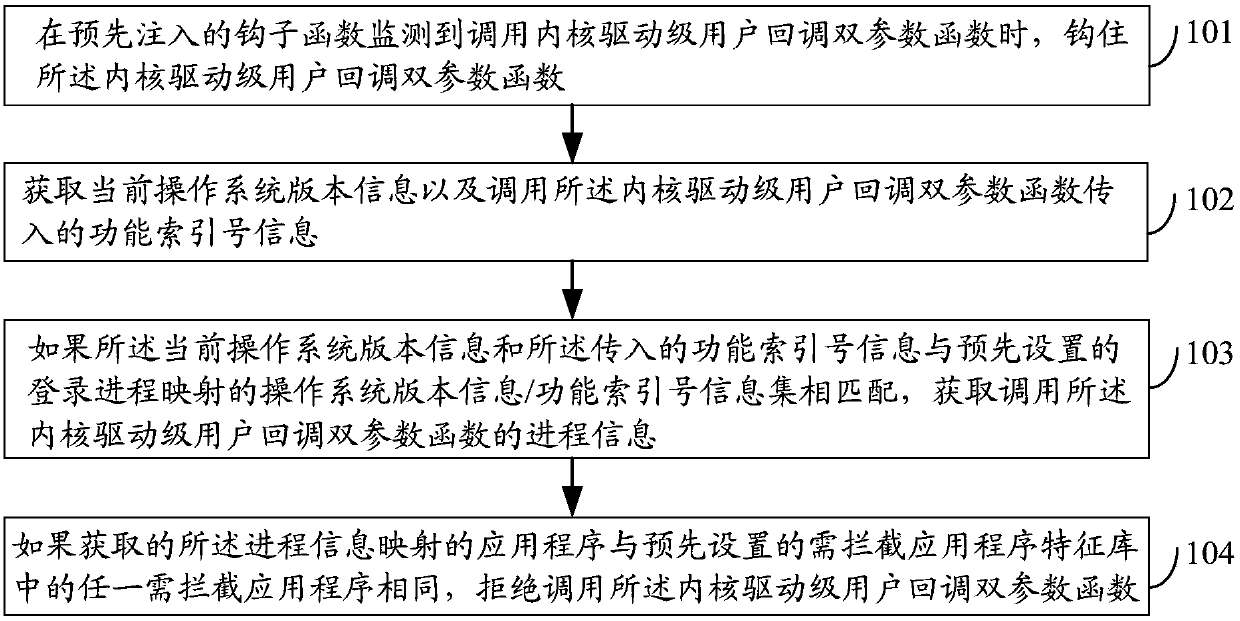
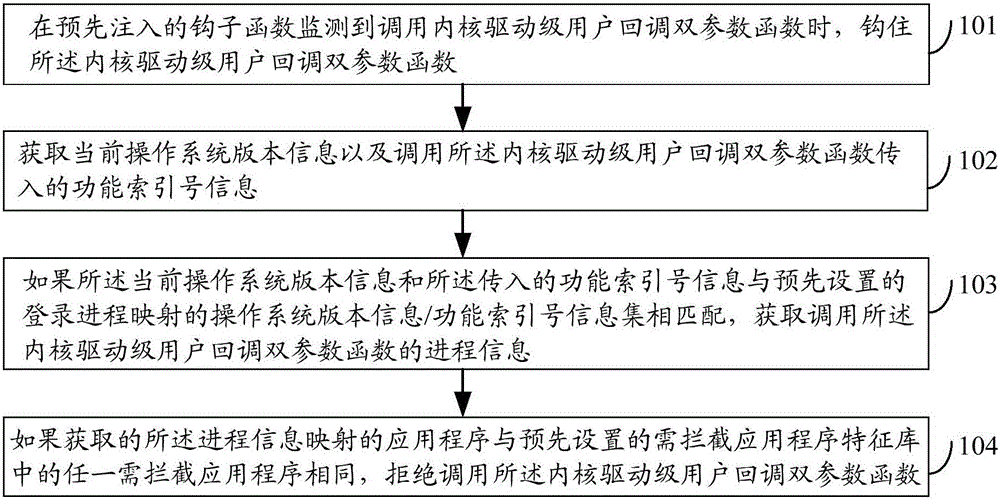
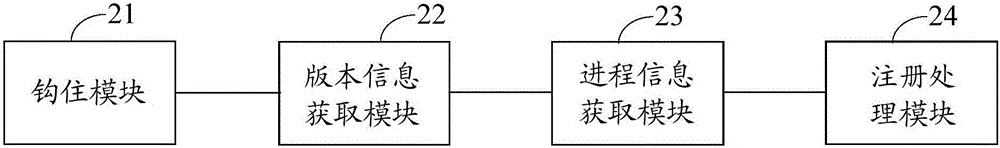
Processing thread register method and device and electronic device
ActiveCN106169049AImprove security protection efficiencySolve the problem of low security protection efficiencyPlatform integrity maintainanceOperational systemApplication software
The embodiment of the invention discloses a processing thread register method and device and an electronic device and relates to the technology of information safety. Safety protection efficiency can be improved. The method includes the steps that when a pre-injected hook function monitors that a kernel drive-stage user callback double-parameter function is called, the function is hooked; current operation system version information is obtained, and function index number information transmitted by the function is called; if the current operation system version information and the transmitted function index number information are matched with an operation system version information / function index number information set mapped by a preset system thread, process information for calling the kernel drive-stage user callback double-parameter function is obtained; if an obtained application mapped by the process information is the same with any to-be-intercepted application in a preset to-be-intercepted application feature library, calling of the kernel drive-stage user callback double-parameter function is refused. The processing thread register method is suitable for processing thread register.
Owner:ZHUHAI BAOQU TECH CO LTD
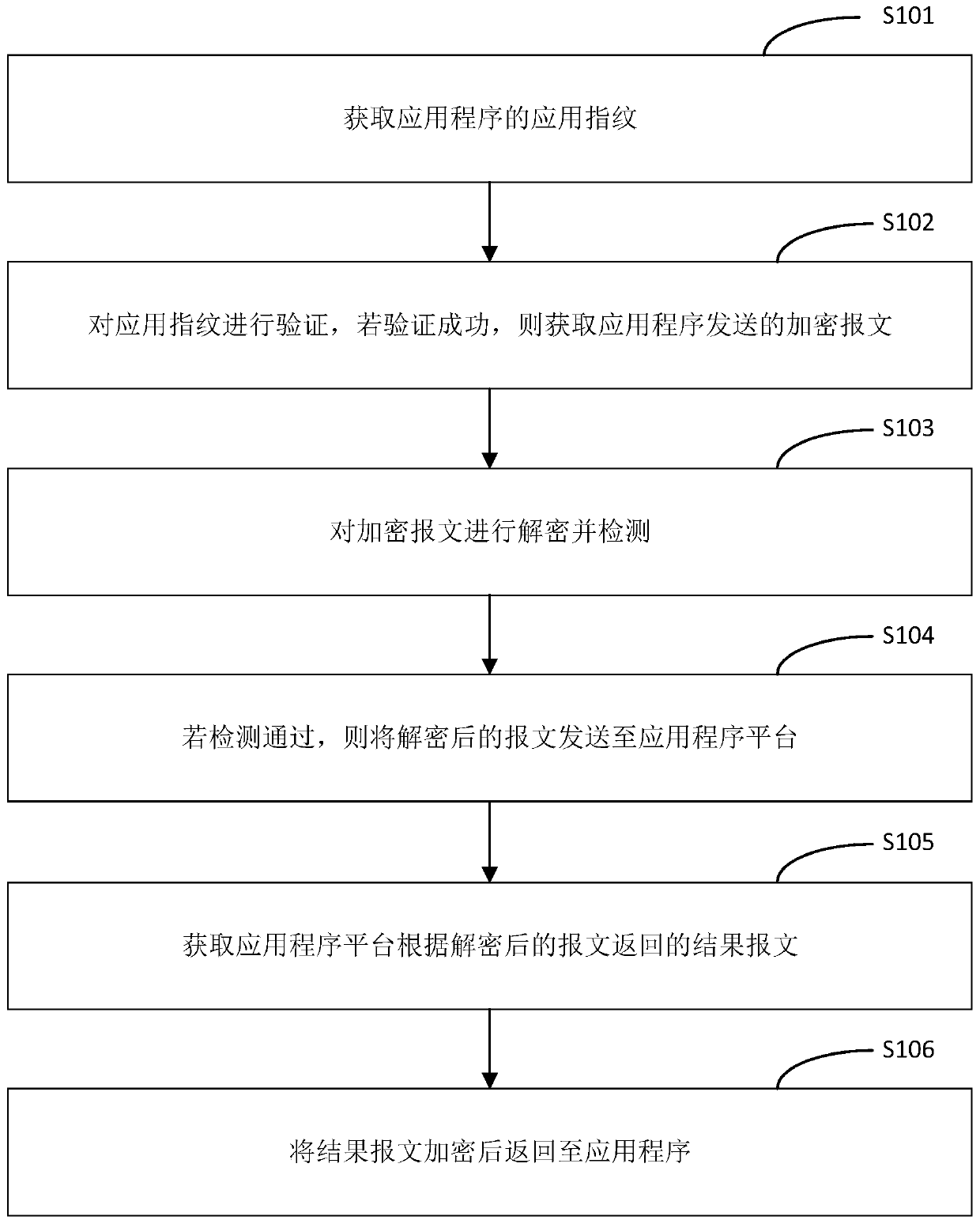
Message transmission method and device, network equipment and storage medium
The embodiment of the invention relates to the technical field of communication, and discloses a message transmission method, which comprises the following steps of: obtaining an application fingerprint of an application program; verifying the application fingerprint, and if the verification succeeds, obtaining an encrypted message sent by the application; decrypting and detecting the encrypted message; if the detection is passed, sending the decrypted message to an application platform; obtaining a result message returned by the application program platform according to the decrypted message;and encrypting the result message and returning the encrypted result message to the application program. The embodiment of the invention further discloses a message transmission device, network equipment and a storage medium. According to the message transmission method and the device, the network equipment and the storage medium provided by the embodiment of the invention, the security protection efficiency of the application program can be improved.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
Method and device for protecting operation system, and electronic device
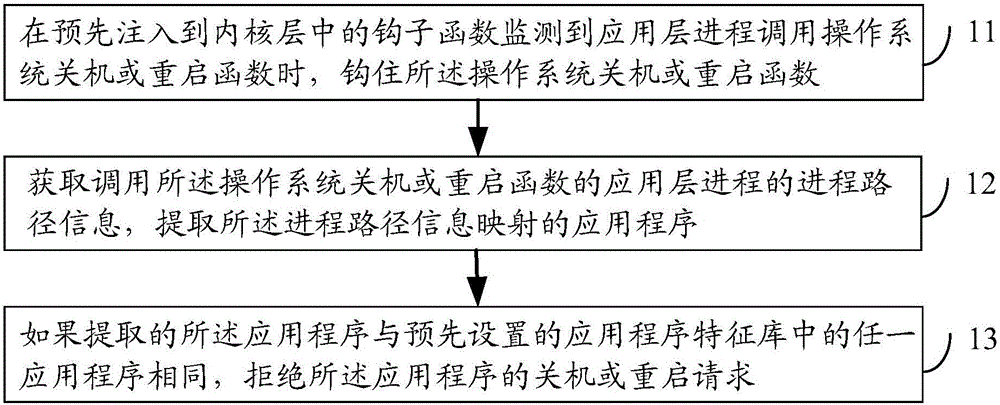
InactiveCN105844148APrevent being shut down or restartedImprove security protection efficiencyPlatform integrity maintainanceInformation mappingApplication software
The embodiment of the invention discloses a method and device for protecting an operation system, and an electronic device. The method comprises: hooking an operation system shutdown or restart function when a hook function pre-injected into an inner nuclear layer monitors that an application layer process invokes an operation system shutdown or restart function; acquiring process path information of the application layer process invoking the operation system shutdown or restart function, and extracting an application program mapped with the process path information; and refusing a shutdown or restart request of the application program if the acquired application program is the same as any one application program in a preset application program characteristic database. By applying the method and device and the electronic device, safety protection efficiency of the operation system can be improved.
Owner:ZHUHAI BAOQU TECH CO LTD
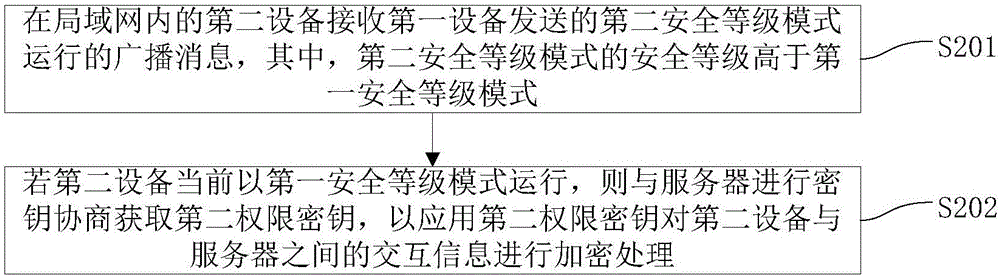
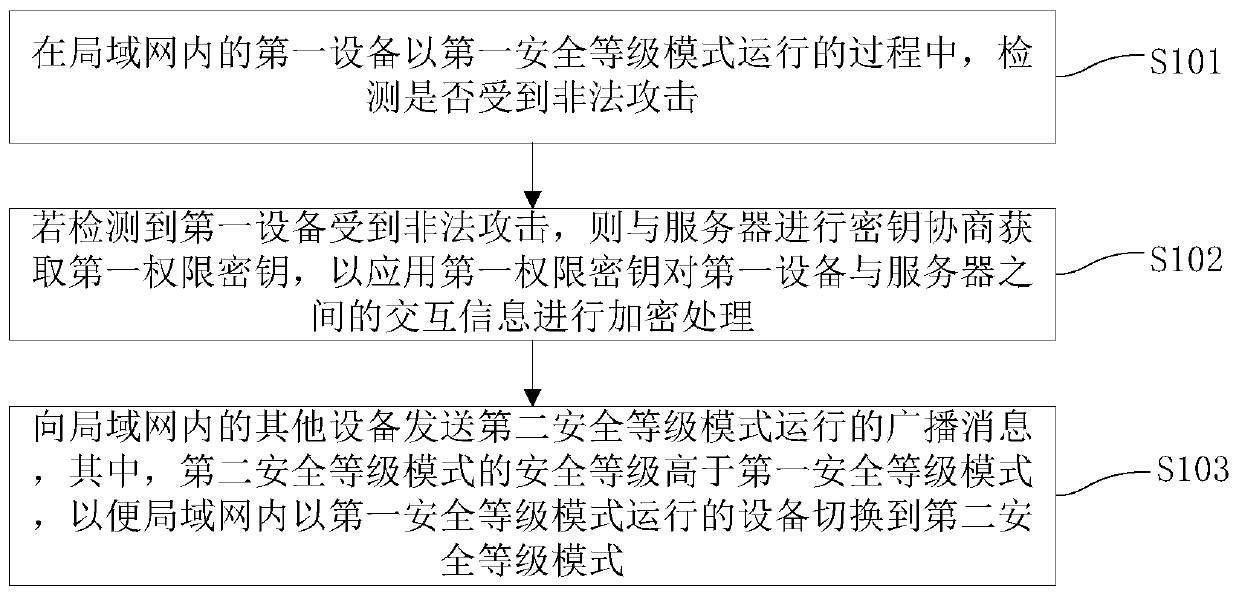
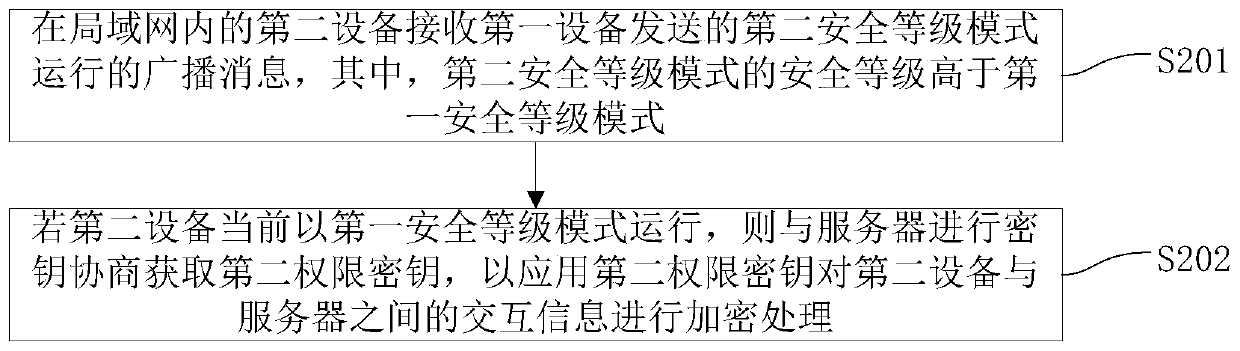
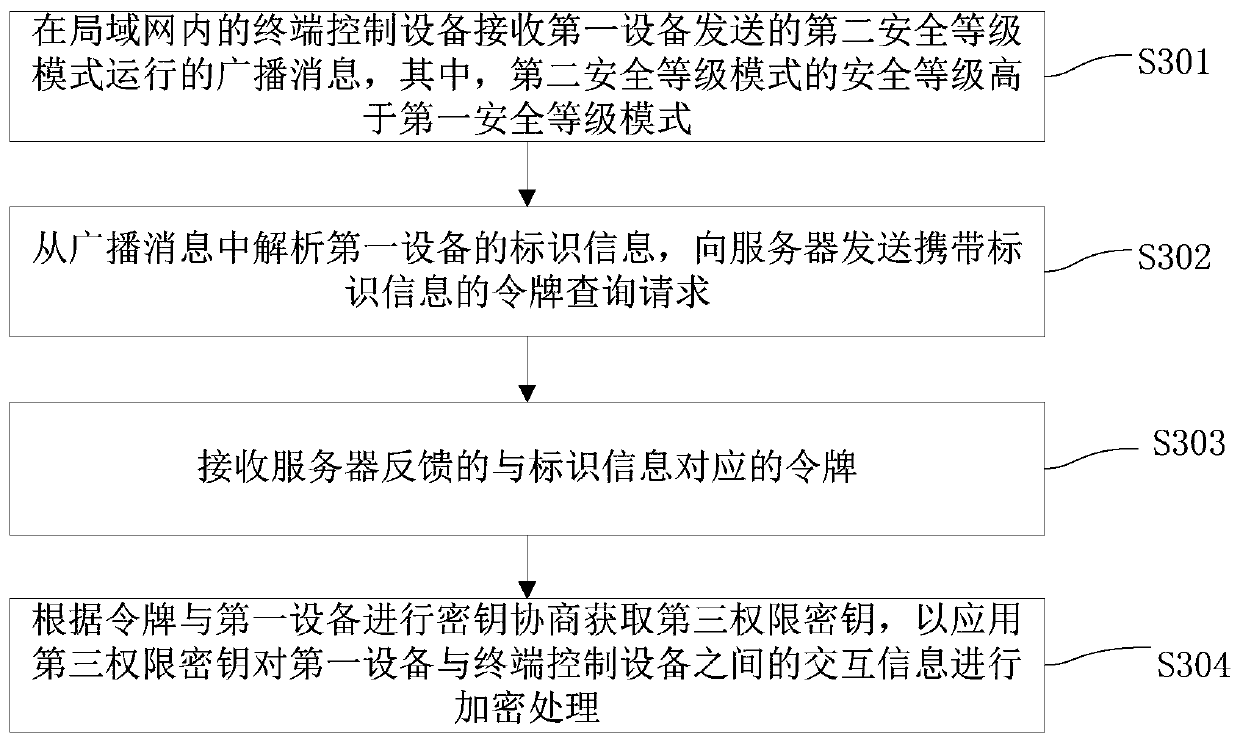
Safe control method and system of equipment in local area network and apparatus
ActiveCN106656984AImprove security protection efficiencyImprove interactivityTransmissionBody area networkBroadcasting
The invention discloses a safe control method and system of equipment in a local area network and an apparatus. The method comprises the following steps: when first equipment in a local area network is running in a first safety-level mode, detecting whether the first equipment is attacked illegally; if detecting that the first equipment is attacked illegally, conducting secret key negotiation with a server to obtain a first authority secret key, and conducting encryption on interaction information between the first equipment and the server by applying the first authority secret key; and sending broadcast messages of running in a second safety-level mode to other pieces of equipment in the local area network, wherein the safety level of the second safety-level mode is higher than that of the first safety-level mode so that the equipment running in the first safety-level mode in the local area network is switched to run in the second safety-level mode. According to the method, interactivity among the equipment in the local area network is realized, other pieces of equipment can be effectively reminded once one piece of equipment is attacked, and thus the safety protection efficiency of the equipment in the local area network is improved.
Owner:MIDEA SMART TECH CO LTD +1
Intelligent beach safety protection method and system based on machine vision
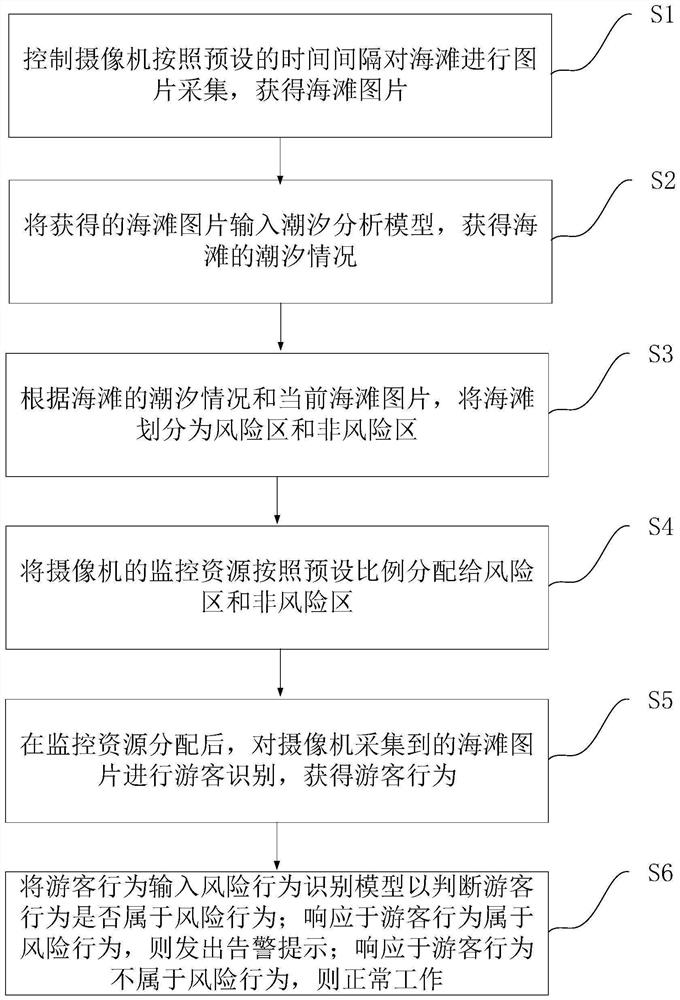
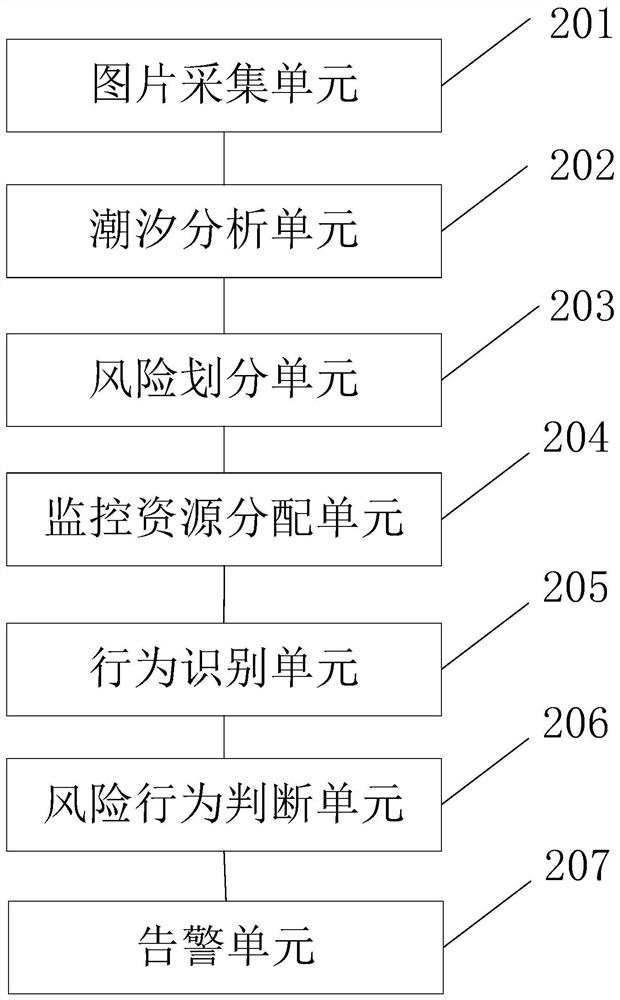
PendingCN114419535AImprove accuracyImprove efficiencyCharacter and pattern recognitionRisk behaviorBeach safety
The invention discloses an intelligent beach safety protection method and system based on machine vision, and the method comprises the steps: controlling a camera to carry out the image collection of a beach according to a preset time interval, and obtaining a beach image; inputting the obtained beach picture into a tide analysis model to obtain the tidal condition of the beach; dividing the beach into a risk area and a non-risk area according to the tidal condition of the beach and the current beach picture; distributing monitoring resources of the camera to the risk area and the non-risk area according to a preset proportion; the monitoring resources obtained in the risk area are larger than the monitoring resources obtained in the non-risk area; after the monitoring resources are distributed, tourist identification is carried out on beach pictures collected by a camera, and tourist behaviors are obtained; inputting the tourist behavior into a risk behavior recognition model to judge whether the tourist behavior belongs to a risk behavior; and giving an alarm prompt in response to the tourist behavior belonging to the risk behavior. The risk behavior identification accuracy and the safety protection efficiency are improved, and the life safety of tourists is guaranteed.
Owner:FUZHOU UNIVERSITY
Big data security protection system and method based on network security
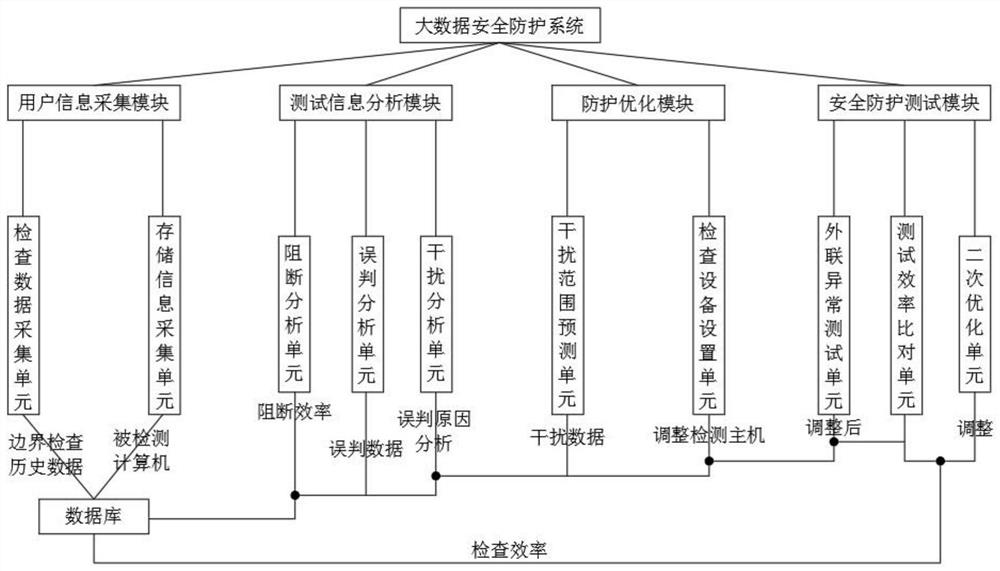
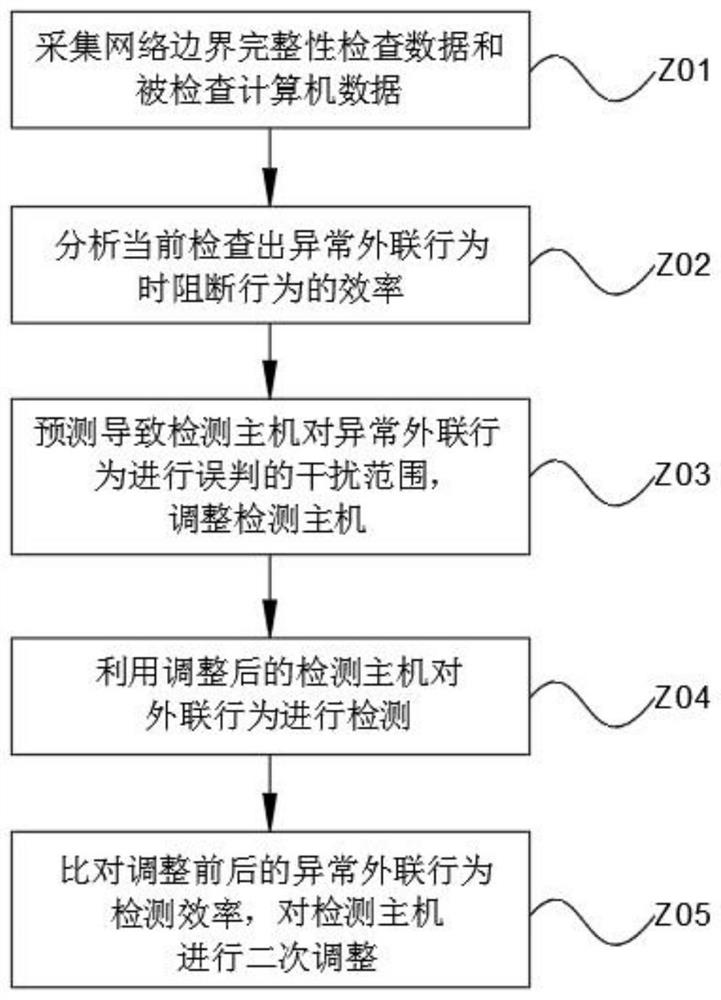
PendingCN114584395AReduce distractionsReduce misjudgmentSecuring communicationHigh level techniquesInformation analysisBig data security
The invention discloses a big data security protection system and method based on network security, and the system comprises a user information collection module, a database, a test information analysis module, a protection optimization module and a security protection test module. All collected data are stored through a database, the efficiency of current checking and abnormal condition processing is analyzed through a test information analysis module, a data security protection mode is optimized through a protection optimization module, the checking efficiency before and after optimization is compared through a security protection test module, secondary optimization is carried out, and the data security protection efficiency is improved. The efficiency of checking and blocking abnormal external connection behaviors is improved while the network boundary integrity checking range is expanded, and the erroneous judgment phenomenon of boundary integrity checking is reduced.
Owner:南京硕茂电子科技有限公司
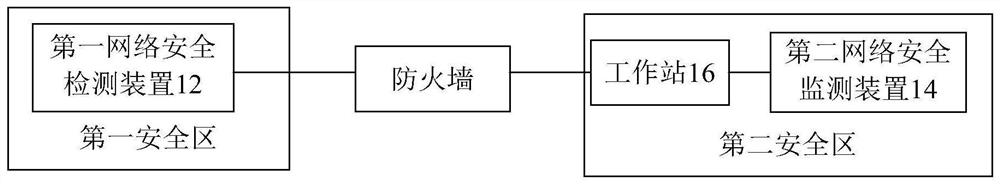
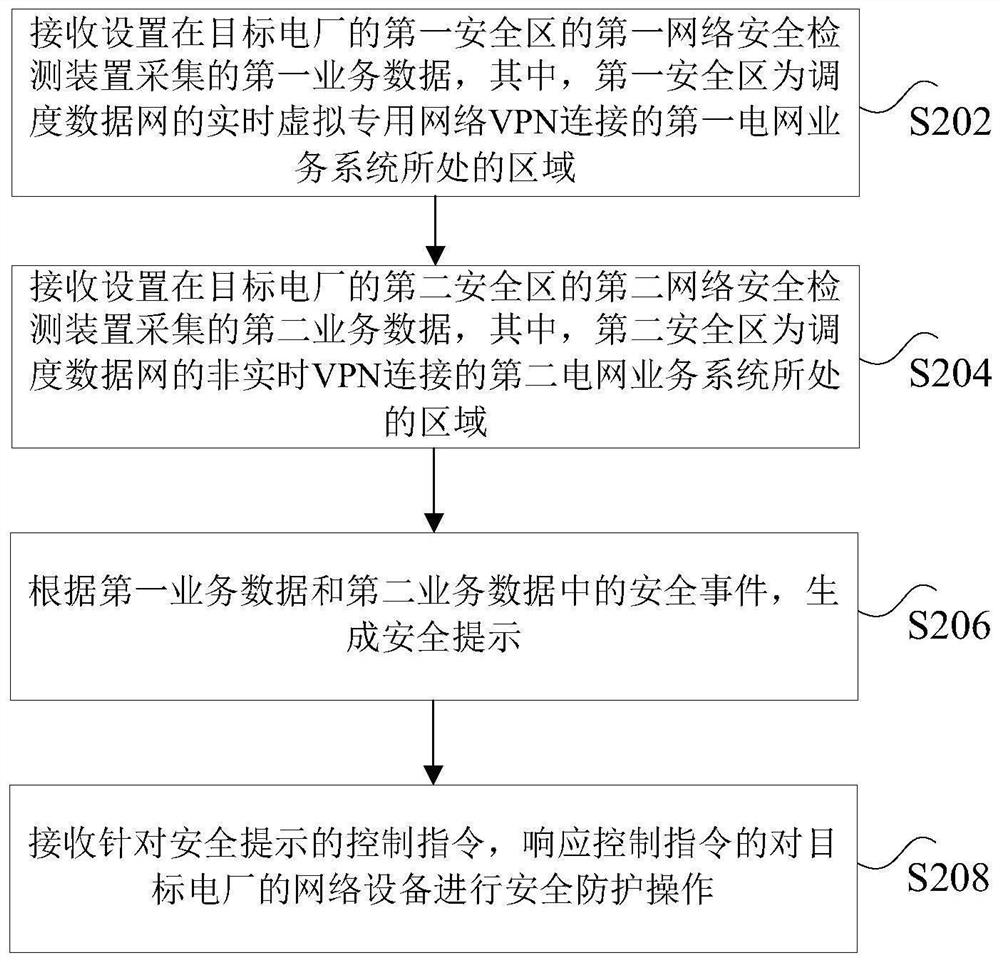
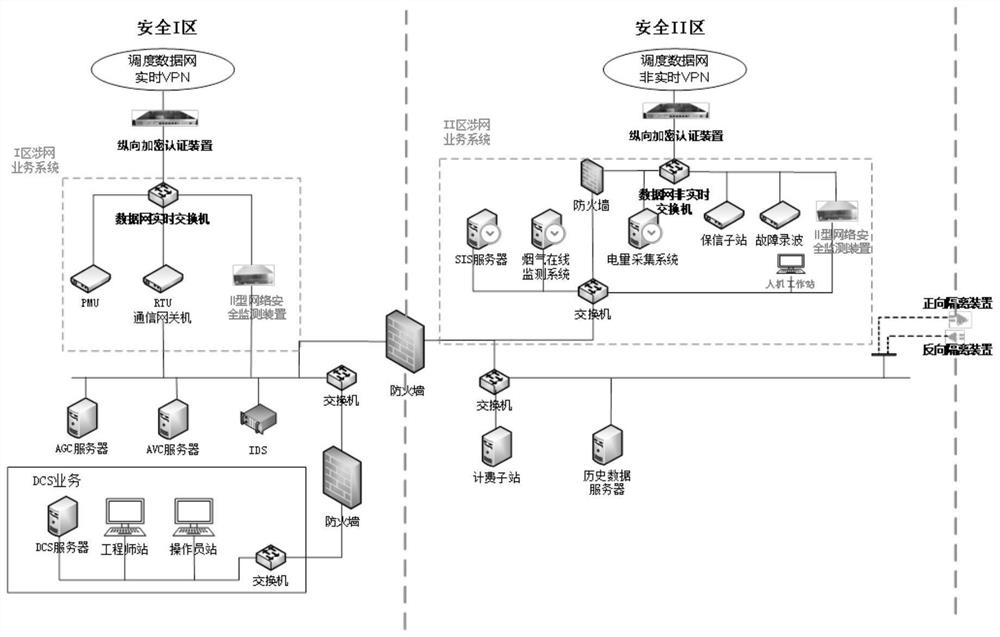
Power plant safety protection system and method
PendingCN113542100AImprove security protection efficiencyImprove securityNetworks interconnectionService systemPower grid
The invention discloses a power plant safety protection system and method. The system comprises a first network safety detection device, a second network safety monitoring device and a workstation, the first network safety detection device is arranged in a first safety area of the target power plant, and the first safety area is an area where a first power grid service system connected with a real-time virtual private network (VPN) of a scheduling data network is located; the second network safety detection device is arranged in a second safety area of the target power plant, and the second safety area is an area where a second power grid service system connected with the non-real-time VPN of the scheduling data network is located; the work station is connected with the second network safety detection device and is arranged in the second safety area; the first safety area and the second safety area are connected through a firewall. The technical problems that the network safety of the power plant is protected based on respective service devices, the efficiency is low and the overall network safety cannot be ensured in the related technology are solved.
Owner:INFORMATION & COMM COMPANY OF QINGHAI ELECTRIC POWER +2
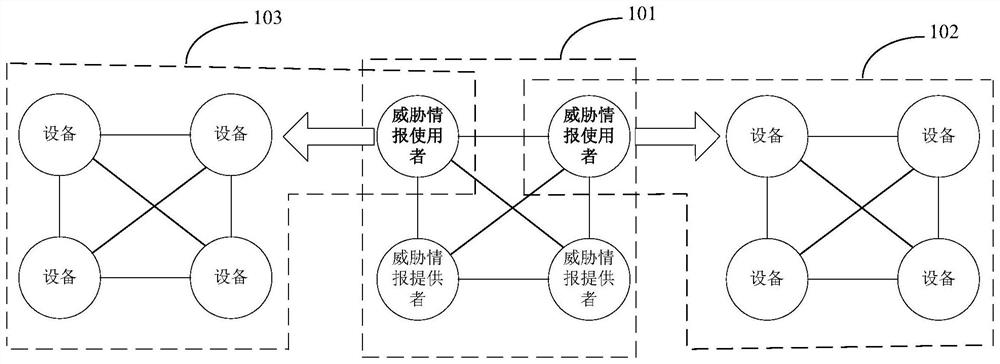
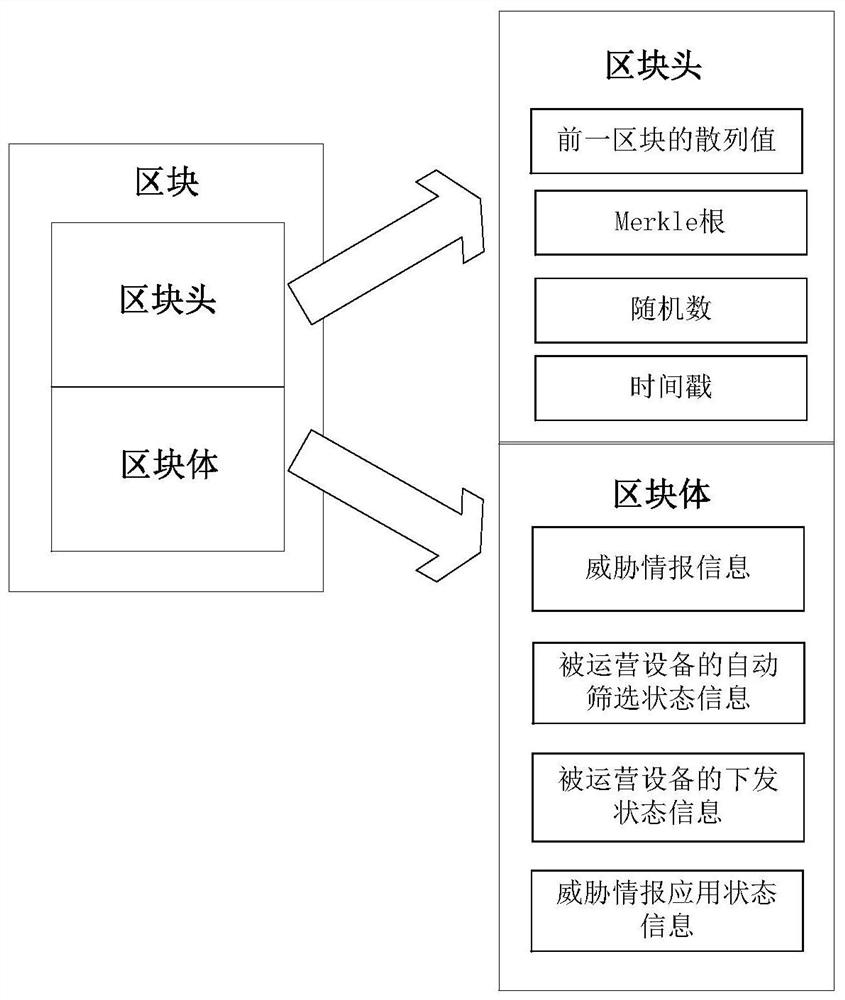
Threat intelligence application method and device
ActiveCN114095187ARealize automatic distributionRealize linkage applicatioSecuring communicationSmart contractThreat intelligence
The invention provides a threat intelligence application method and device. The method comprises the steps of: acquiring threat intelligence information; operating a first smart contract, and automatically screening a second node, wherein the second node is operated equipment needing to issue the threat intelligence information; based on a consensus mechanism, writing automatic screening state information output by the first smart contract and information of the second node into a blockchain; operating a second smart contract, automatically issuing the threat intelligence information to the second node, and writing issuing state information output by the second smart contract into a blockchain based on the consensus mechanism; and operating a third smart contract, and writing the threat intelligence application state information of the second node into the blockchain based on the consensus mechanism. According to the threat intelligence application method and device, automatic issuing and linkage application of threat intelligence can be realized, and the efficiency of network security protection is improved.
Owner:CHINA MOBILE COMM LTD RES INST +1
A processing method, device and electronic equipment for copying information
ActiveCN106203077BImprove security protection efficiencySolve the problem of low security protection efficiencyPlatform integrity maintainanceInformation processingOperational system
The embodiment of the invention discloses a duplicating information processing method and device, and electronic equipment, relates to the technology of information safety, and can improve the safety protection efficiency of an operating system. The method comprises the following steps: when the calling of a kernel DuplicateHandle object function is monitored in a pre-injected hook function, hooking the kernel DuplicateHandle object function; monitoring whether the kernel DuplicateHandle object function succeeds in duplicating a target process handle or not, and if the kernel DuplicateHandle object function succeeds in duplicating the target process handle, judging whether the target process handle which succeeds in duplicating is matched with any one protection process handle in a preset protection process handle library or not; if the target process handle which succeeds in duplicating is matched with any one protection process handle in the preset protection process handle library, obtaining the process path information of the target process handle which succeeds in duplicating, and extracting a to-be-verified application program mapped by the process path information; and if the extracted to-be-verified application program is the same with any one to-be-intercepted application program in a preset to-be-intercepted application program library, closing the target process handle which succeeds in duplicating. The duplicating information processing method and device is suitable for monitoring whether the target process handle is illegally duplicated or not.
Owner:ZHUHAI BAOQU TECH CO LTD
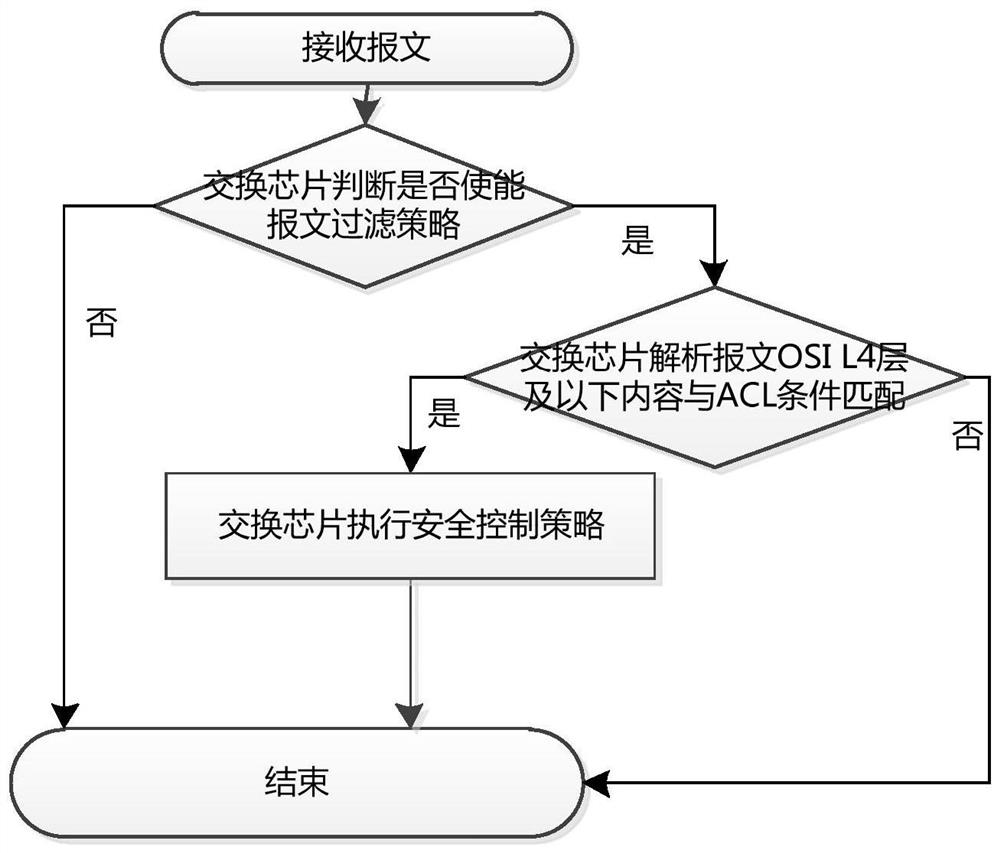
A processing method for endogenous security dynamic protection function of routing and switching equipment
ActiveCN112202814BGuaranteed reliabilityMeet the needs of high-performance security protectionSecuring communicationMultiplexingManycore processor
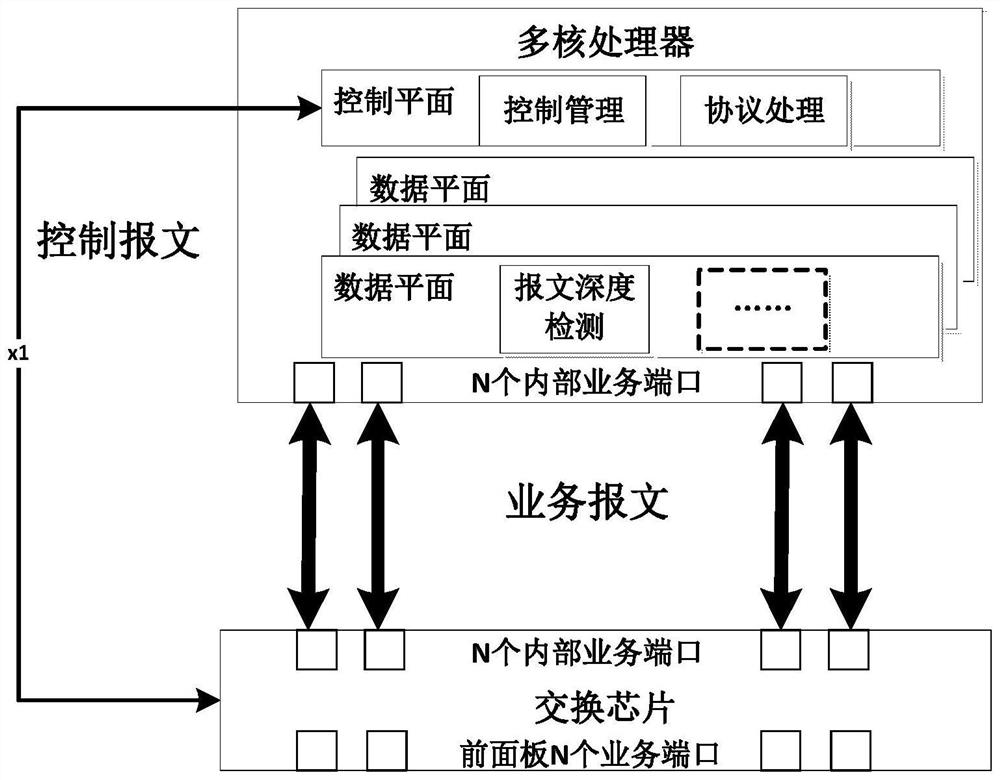
The invention discloses a processing method for endogenous safety and dynamic protection functions of routing switching equipment, relying on switching chips and multi-core processors inside the routing switching equipment to achieve security protection, including: detecting and identifying the content of the 2-7 layer of the message, Implement refined security control strategies based on classification results; the switch chip completes message filtering and attack defense functions for the 2-4 layer of the message; the multi-core processor detects the content of the 3-7 layer of the message, completes the deep security defense detection, and sends The switch chip actively issues security control policies, which are finally executed by the switch chip. The switch chip cooperates with the multi-core processor to realize the in-depth detection of the message content, and can actively implement the security control strategy in a targeted manner, which greatly improves the active protection capability of the routing and switching equipment. The method of one-time detection, matching, and multiple multiplexing greatly reduces the impact on system performance and avoids the risk of processing performance bottlenecks caused by the introduction of some safety protection equipment.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
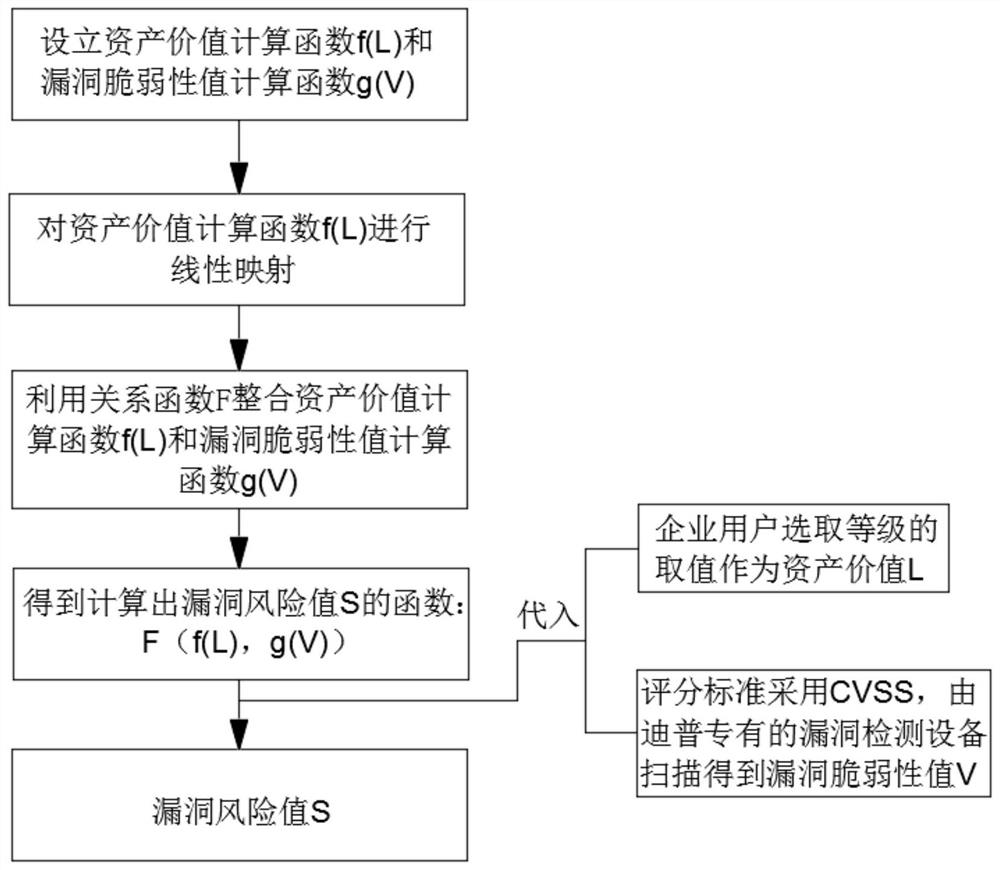
A Statistical Method for Priority of Vulnerability Disposal and Repair
ActiveCN113139191BSolve efficiency problemsSolve the cumbersome and disorderly disposal processPlatform integrity maintainanceData miningComputer science
The present invention proposes a method for statistics of vulnerability disposal and repair priority, which includes the following steps: S1, obtaining asset value L and vulnerability vulnerability value V; S2, using the following formula to substitute asset value L and vulnerability vulnerability value V into calculation to calculate Vulnerability risk value S, S=F(f(L), g(V)); where: f(L) is the asset value calculation function, g(V) is the vulnerability vulnerability value calculation function, F(f(L) , g(V)) is the relation function. The invention combines parameters of multiple dimensions to realize the transformation from qualitative to quantitative.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD QUZHOU POWER SUPPLY CO
A method and device for network asset risk portrait
ActiveCN108809928BImprove security protection efficiencyVulnerabilities discovered in timeTransmissionDomain nameEngineering
The application provides a network asset risk portraying method and a network asset risk portraying device, capable of improving network security protection efficiency. The network asset risk portraying method comprises: obtaining a target root domain name corresponding to the network asset to be portrayed; obtaining a sub-domain name included in the target root domain name; performing vulnerability scanning on the obtained sub-domain name to obtain vulnerabilities existing in the obtained sub-domain name; classifying the risk points of the obtained vulnerabilities according to the pre-set risk point classification strategy, and performing risk portrait on the network assets to be portrayed according to the classified risk points.
Owner:小安(北京)科技有限公司
A method and device for determining the success of an attack by anti-connection
ActiveCN113965419BSolve the discrimination problemAvoid Threat AlertsSecuring communicationInternet privacyAttack
The embodiments of the present application provide a method and device for determining the success of an attack through anti-connection, including: first obtaining the attack traffic to be detected, and extracting the attack payload in the attack traffic and the address of the attacked host corresponding to the attack traffic; then extracting the attack payload Then, according to the address of the attacked host and the preset judgment conditions, it is judged whether the connection request corresponding to the suspected anti-connection address is detected; if so, it is determined that the attacked host address has been successfully attacked, and the network attack can be solved successfully. Therefore, it is beneficial to improve the efficiency of security protection by avoiding the generation of a large number of threat alarms.
Owner:北京微步在线科技有限公司
Enterprise safety management method and system
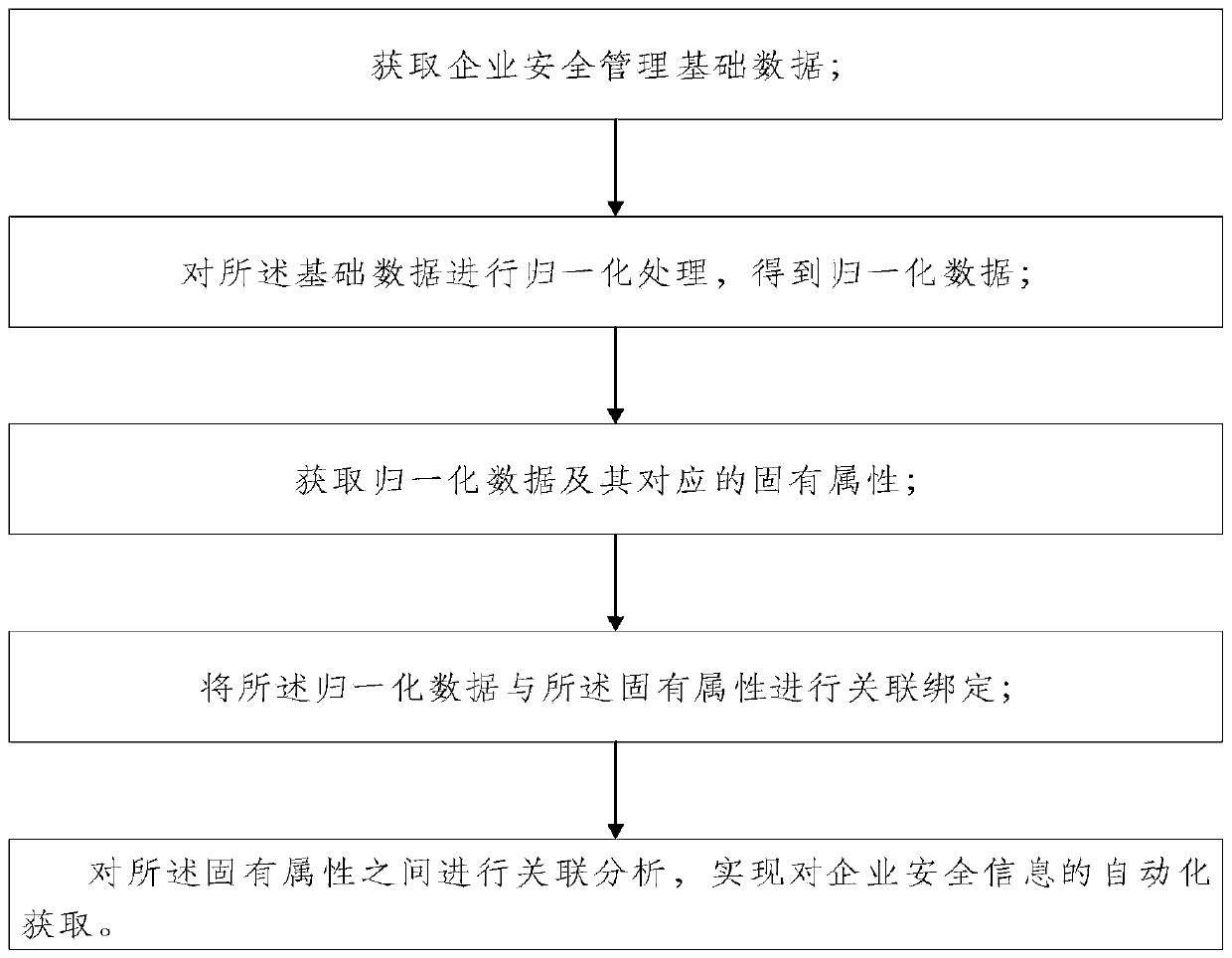
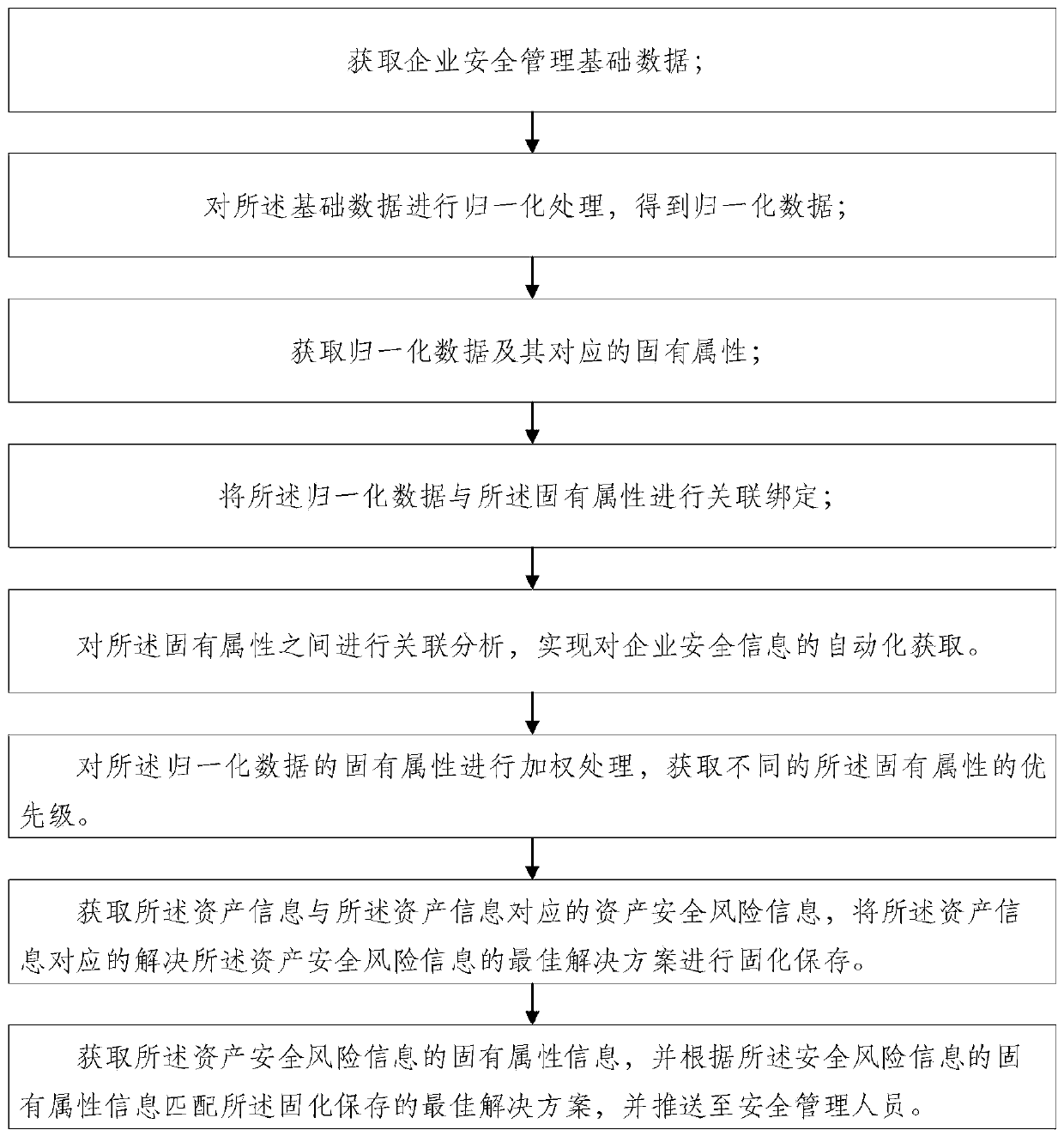
InactiveCN110348759AHigh degree of automationAutomate acquisitionResourcesEnterprise security managementData acquisition
The embodiment of the invention discloses an enterprise safety management method and device. The method comprises the following steps: obtaining enterprise safety management basic data; carrying out normalization processing on the basic data to obtain normalized data; obtaining normalized data and corresponding inherent attributes thereof; carrying out association binding on the normalized data and the inherent attributes; and carrying out association analysis on the inherent attributes to realize automatic acquisition of the enterprise safety information. Safety management basic data of an enterprise is obtained; normalization processing is carried out on the basic data and then binding the basic data with inherent attributes of the basic data; and finally, through association analysis between inherent attributes, automatic acquisition of the enterprise asset security information is realized, the dependence of enterprise information management on security personnel is minimized, autonomous decision and acquisition of basic data are performed, the automation degree of data acquisition is improved, and the efficiency is improved.
Owner:关瑜
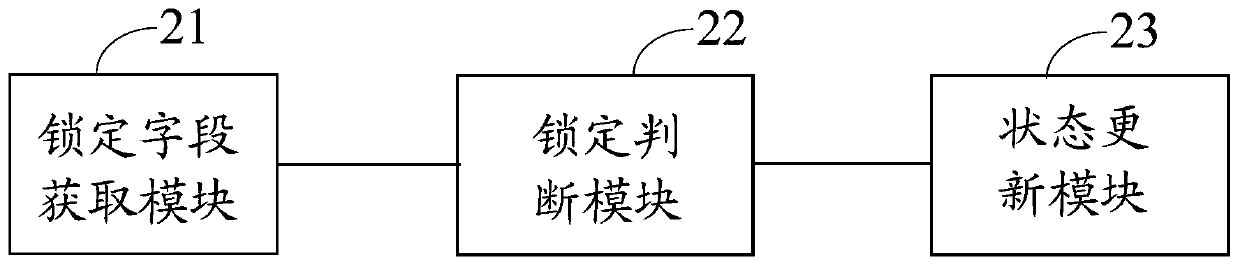
A method, device and electronic equipment for releasing a mutex
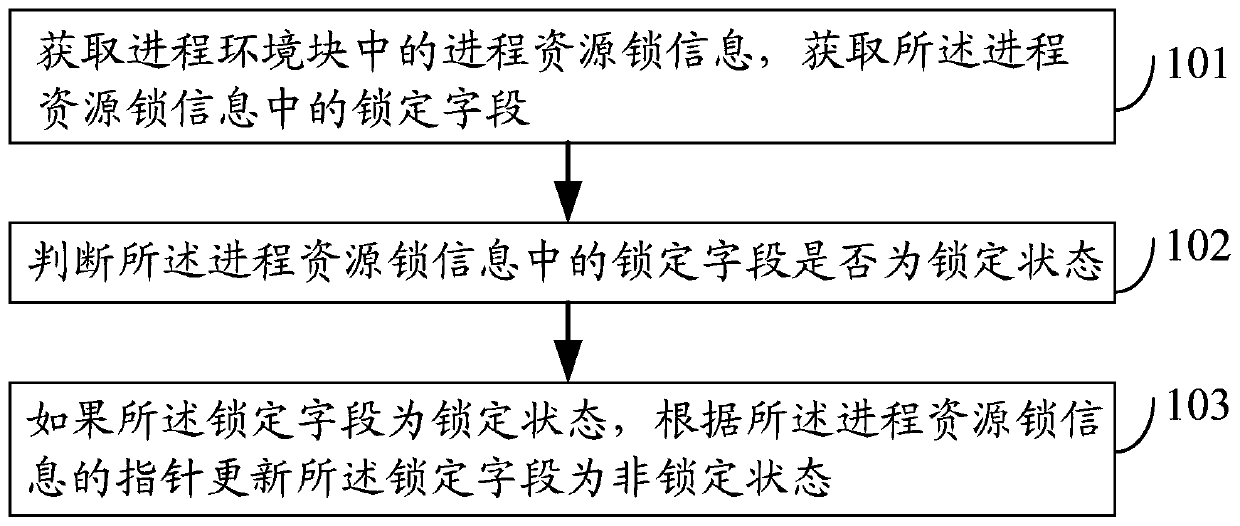
ActiveCN106250244BImprove security protection efficiencySolve the problem of low security protection efficiencyProgram synchronisationResource informationEmbedded system
An embodiment of the invention discloses a mutually-exclusive lock release method and device and electronic equipment and relates to information safety technology. The mutually-exclusive lock release method and device is conducive to improving safety protection efficiency of an operation system. The method includes: acquiring process resource lock information in a process environment block, and acquiring a locking field in the process resource lock information; judging whether the locking field in the process resource information is in a locked state or not; if yes, updating the locking field into a unlocked state according to a pointer of the process resource lock information.
Owner:ZHUHAI BAOQU TECH CO LTD
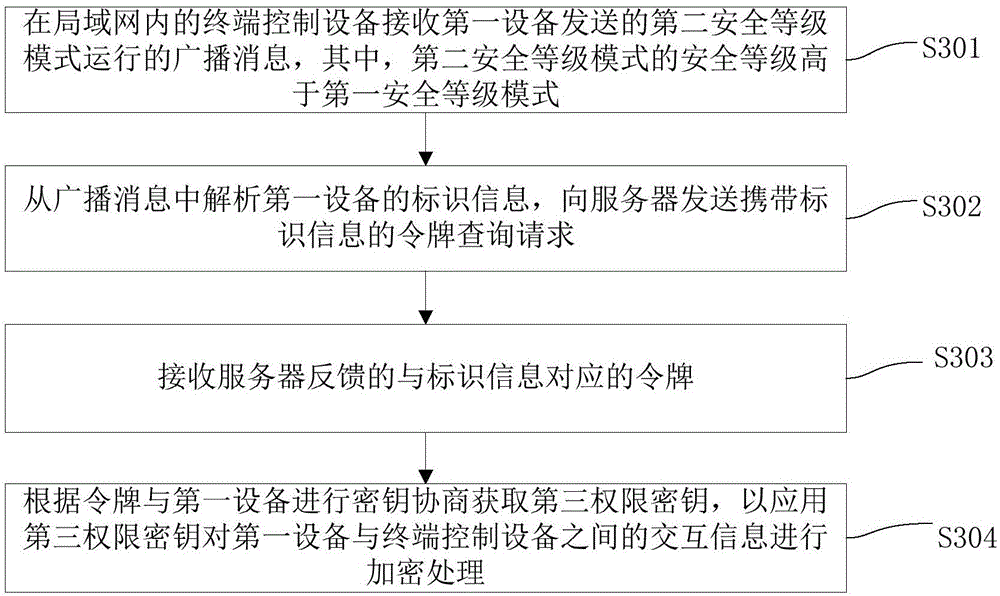
Security control method, system and equipment for equipment in local area network
ActiveCN106656984BImprove interactivityImprove security protection efficiencyTransmissionSafety controlBroadcasting
The invention discloses a safe control method and system of equipment in a local area network and an apparatus. The method comprises the following steps: when first equipment in a local area network is running in a first safety-level mode, detecting whether the first equipment is attacked illegally; if detecting that the first equipment is attacked illegally, conducting secret key negotiation with a server to obtain a first authority secret key, and conducting encryption on interaction information between the first equipment and the server by applying the first authority secret key; and sending broadcast messages of running in a second safety-level mode to other pieces of equipment in the local area network, wherein the safety level of the second safety-level mode is higher than that of the first safety-level mode so that the equipment running in the first safety-level mode in the local area network is switched to run in the second safety-level mode. According to the method, interactivity among the equipment in the local area network is realized, other pieces of equipment can be effectively reminded once one piece of equipment is attacked, and thus the safety protection efficiency of the equipment in the local area network is improved.
Owner:MIDEA SMART TECH CO LTD +1
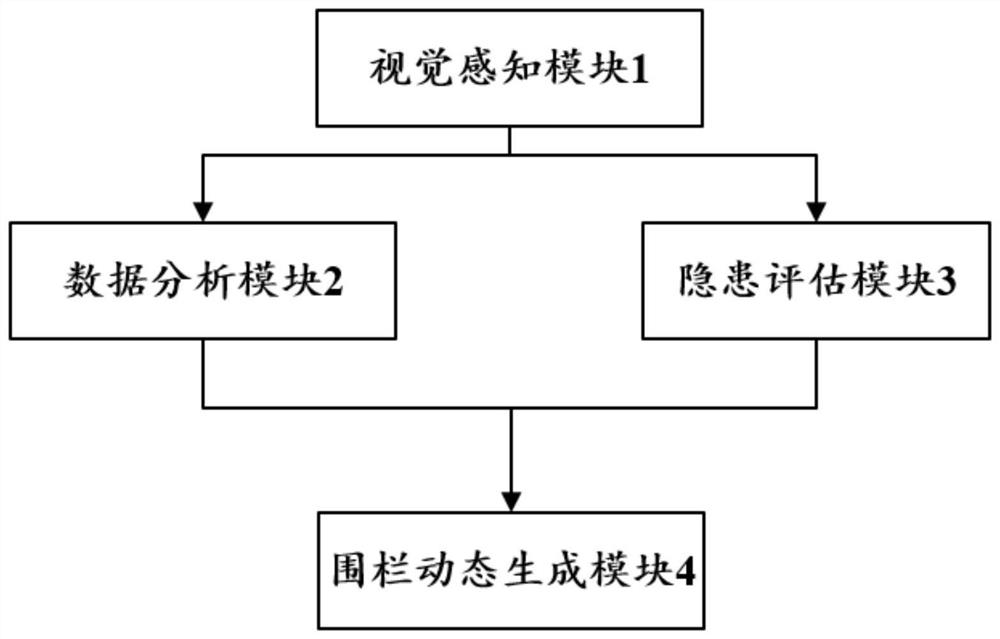
Electronic fence area generation system based on hazard monitoring and personnel positioning
ActiveCN113115225BReal-time adjustmentImprove security protection efficiencyCharacter and pattern recognitionNeural architecturesHazard monitoringPositioning technology
The invention relates to the technical field of computer vision, in particular to an electronic fence area generation system based on hazard source monitoring and personnel positioning, comprising a visual perception module, a data analysis module, a hidden danger assessment module and a fence dynamic generation module, which solves the problem of existing fixed The electronic fence cannot adjust the fence range in real time and accurately according to the environmental conditions, the safety is poor, and the cost is high. The present invention comprehensively analyzes the state and trend of danger sources, can effectively monitor a variety of major danger sources, and reduces the occurrence rate of danger; the virtual electronic fence generated by the present invention is organically and dynamically combined with the positioning technology, and is realized according to each heat level. Automatic grading alarm, and no need to manually arrange virtual electronic fences, which is convenient and quick to set up, which greatly reduces the cost and workload of security personnel, and can adjust the effective area in real time according to the degree of danger, which significantly improves the safety protection efficiency of dangerous areas.
Owner:国能智慧科技发展(江苏)有限公司
A method, device and electronic equipment for processing thread registration
ActiveCN106169049BImprove security protection efficiencySolve the problem of low security protection efficiencyPlatform integrity maintainanceOperational systemApplication software
The embodiment of the invention discloses a processing thread register method and device and an electronic device and relates to the technology of information safety. Safety protection efficiency can be improved. The method includes the steps that when a pre-injected hook function monitors that a kernel drive-stage user callback double-parameter function is called, the function is hooked; current operation system version information is obtained, and function index number information transmitted by the function is called; if the current operation system version information and the transmitted function index number information are matched with an operation system version information / function index number information set mapped by a preset system thread, process information for calling the kernel drive-stage user callback double-parameter function is obtained; if an obtained application mapped by the process information is the same with any to-be-intercepted application in a preset to-be-intercepted application feature library, calling of the kernel drive-stage user callback double-parameter function is refused. The processing thread register method is suitable for processing thread register.
Owner:ZHUHAI BAOQU TECH CO LTD
Method, device and electronic equipment for processing process registration
ActiveCN106228062BImprove security protection efficiencySolve the problem of low security protection efficiencyPlatform integrity maintainanceOperational systemApplication software
Owner:ZHUHAI BAOQU TECH CO LTD
Parking lifting platform real-time fall prevention device
ActiveCN105464436BImprove security protection efficiencySimple structureParkingsEngineeringElectric control
The invention relates to a real-time fall preventing device for a parking lift platform. The real-time fall preventing device comprises electric-control mechanical protecting units, U-shaped infrared detectors, a self-control unit and control cables, wherein the electric-control mechanical protecting units are arranged at positions, close to four corners, between the parking lift platform and a lateral-moving frame, the U-shaped infrared detectors are clamped to the outer sides of steel wire ropes, and each electric-control mechanical protecting unit comprises a primary protecting tube, a secondary protecting tube, fall preventing holes, an electromagnet, an fall preventing hook, a limit block, a primary positioning lock, a lock hole, a primary unlocking connecting piece, a secondary positioning lock and the like. The real-time fall preventing device for the parking lift platform has the advantages that real-time electronic detection of drive steel wire ropes is achieved, real-time and safe fall prevention of the parking lift platform can be achieved, and the safety problem that the parking lift platforms using the steel wire ropes and chains for driving has no real-time fall prevention is well solved.
Owner:朱旭红
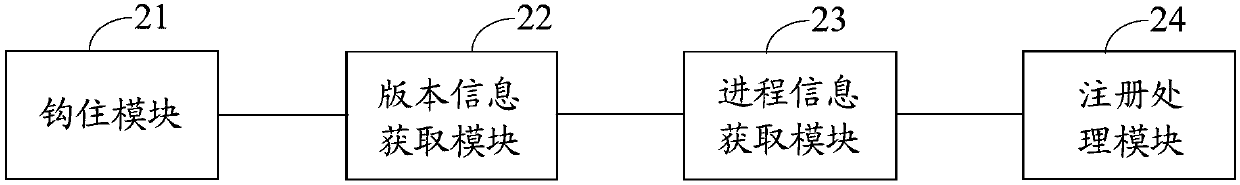
Course register processing method and device and electronic equipment
ActiveCN106228062AImprove security protection efficiencySolve the problem of low security protection efficiencyPlatform integrity maintainanceOperational systemApplication software
The embodiment of the invention discloses a course register processing method and device and electronic equipment and relates to information security technology. By the adoption of the course register processing method and device and the electronic equipment, safety protection efficiency can be improved. The method comprises the steps of hooking a kernel driver stage user callback two-parameter function when the calling of the function is monitored by a hook function which is injected in advance, obtaining the version information of a current operation system and function index number information introduced by calling of the function, obtaining the course information of calling the kernel driver stage user callback two-parameter function if the version information of the current operation system and the introduced function index number information are matched with an operation system version information / function index number information set mapped by a preset login course, and refusing the calling of the kernel driver stage user callback two-parameter function if an application mapped by the acquired course information is identical with any one application needing to be intercepted in a preset intercept-required application feature library. The method and device are suitable for course register processing.
Owner:ZHUHAI BAOQU TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com