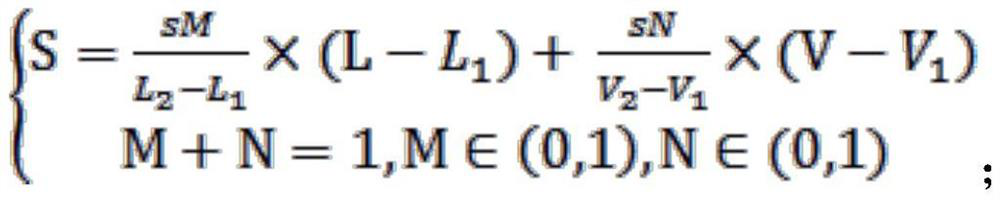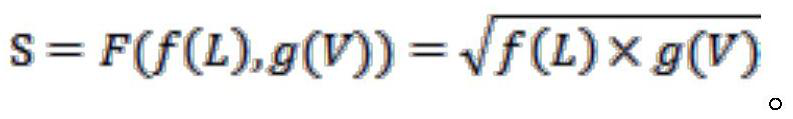A Statistical Method for Priority of Vulnerability Disposal and Repair
A statistical method and prioritization technology, applied in computing, electrical digital data processing, computer security devices, etc., can solve the problems of prioritization score restoration, prioritization, normalization and classification, etc. The effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
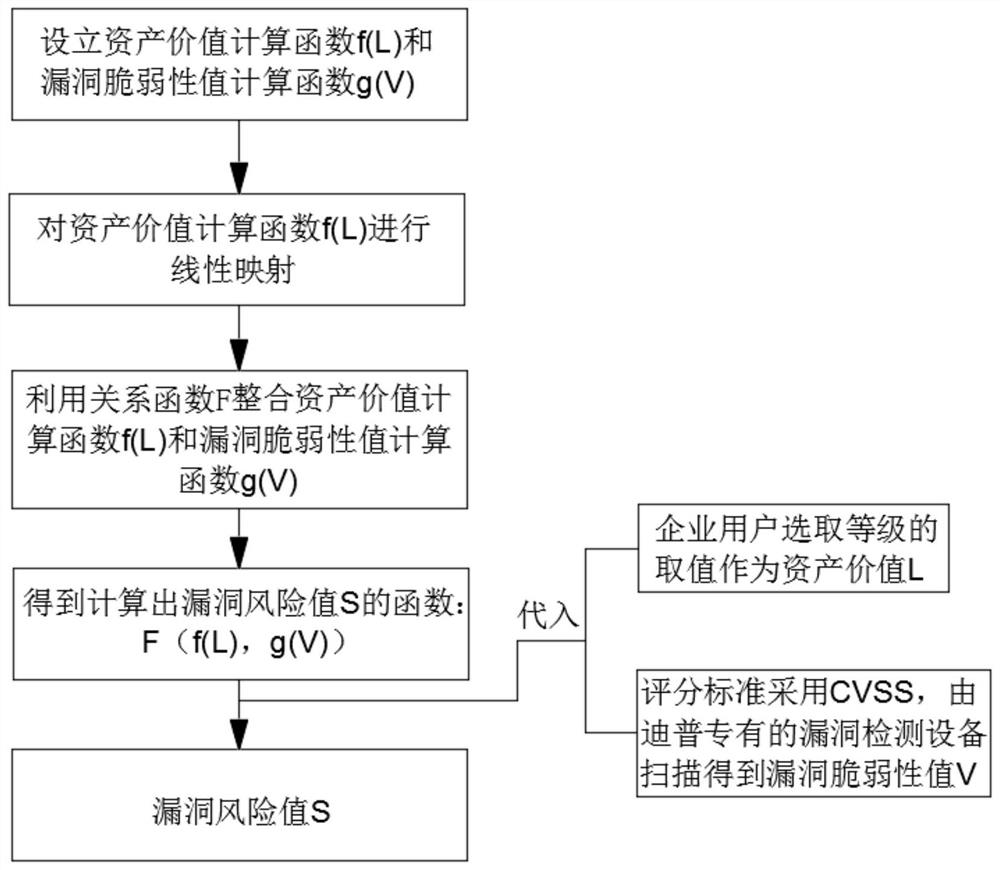
[0050] This embodiment proposes a statistical method for the priority of vulnerability disposal and repair, refer to figure 1 , including the following steps:
[0051] S1, obtain asset value L and vulnerability vulnerability value V;
[0052] The acquisition process of asset value L is as follows:
[0053] Establish an asset value grading table. The asset value grading table includes the grade, the corresponding logo of the grade, and the corresponding description of the standard corresponding to the logo. The grade values are 1, 2, 3, 4, and 5; the enterprise user divides the table according to the asset value grade as: Asset value assignment, the enterprise user selects the value of the grade as the asset value L.
[0054]According to the national standard GB / T 20984-2007, when an enterprise assigns value to an asset, it can obtain the asset value through a comprehensive assessment based on the confidentiality, integrity and availability of the asset. The final assignme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com