Method and device for judging attack success through reverse connection
A successful, attacked technique used in cybersecurity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
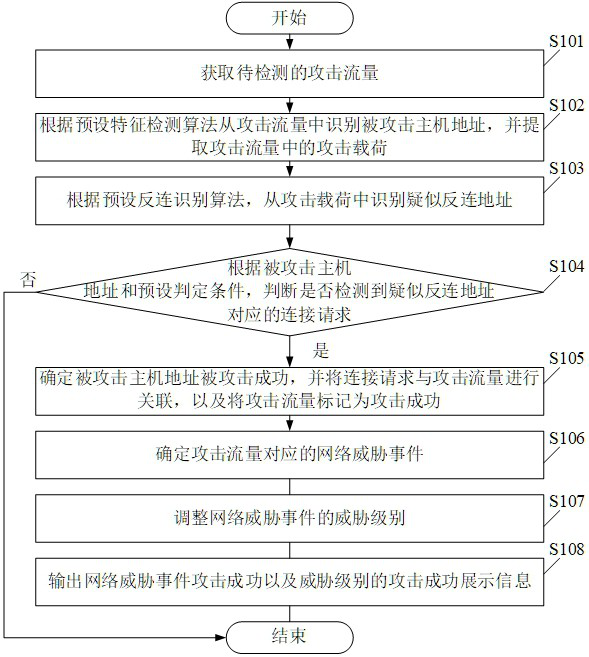
[0038] Please see figure 1 , figure 1 The embodiment of the present application provides a schematic flowchart of a method for determining the success of an attack through reverse connection. Among them, the method for determining the success of an attack through reverse connection includes:
[0039] S101. Obtain attack traffic to be detected.
[0040] In the embodiment of the present application, the method is applied in a network security scenario, and is specifically applied in a scenario of determining whether the attack is successful after the host is attacked.
[0041] S102. Identify the attacked host address from the attack traffic according to a preset feature detection algorithm, and extract the attack payload in the attack traffic.
[0042] In the embodiment of the present application, when detecting the attack traffic to identify the attacked host address, first detect the specific attack characteristics in the attack traffic, and then extract the attacked host a...
Embodiment 2
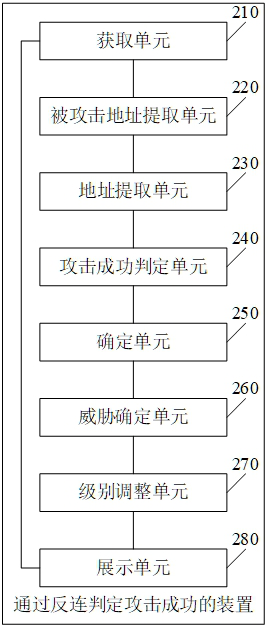
[0092] Please see figure 2 , figure 2 It is a schematic structural diagram of an apparatus for determining the success of an attack through reverse connection provided in the embodiment of the present application. Such as figure 2 As shown, the device for judging the success of the attack through reverse connection includes:
[0093] An acquisition unit 210, configured to acquire attack traffic to be detected;
[0094] The attacked address extracting unit 220 is used to extract the attack load in the attack traffic and the attacked host address corresponding to the attack traffic;
[0095] In the embodiment of the present application, when detecting the attack traffic to identify the attacked host address, the specific attack characteristics in the attack traffic are detected first, and then the attacked host address is identified according to the attack characteristics, and the attacked host address is cached.
[0096] In this embodiment of the present application, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com