Web protection method based on URL self-learning
A self-learning and security protection technology, applied in the field of network security, can solve the problems of no security protection, doubtful effectiveness, low reading rate, etc., and achieve the effect of ensuring protection efficiency, ensuring effectiveness, and high reading rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
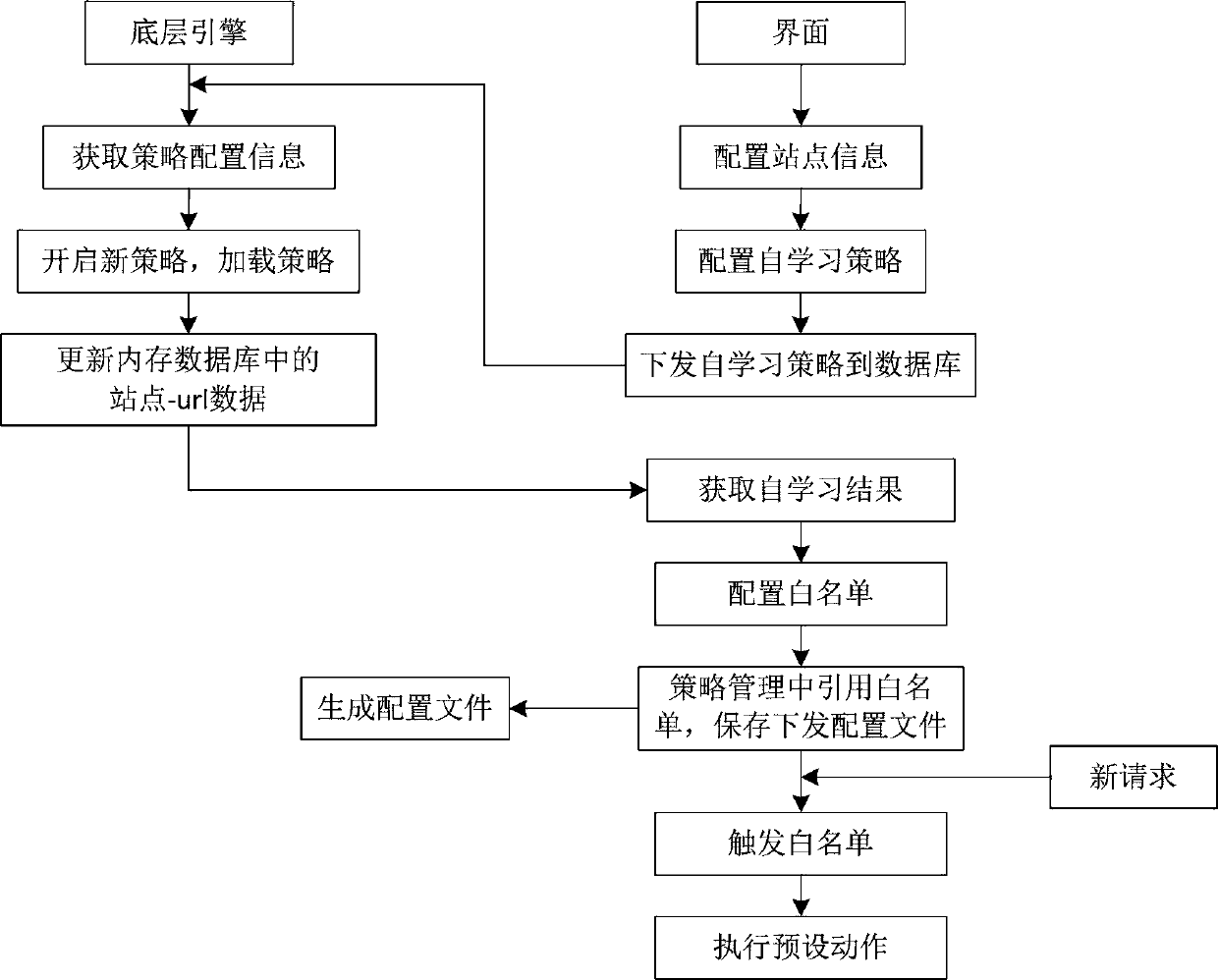
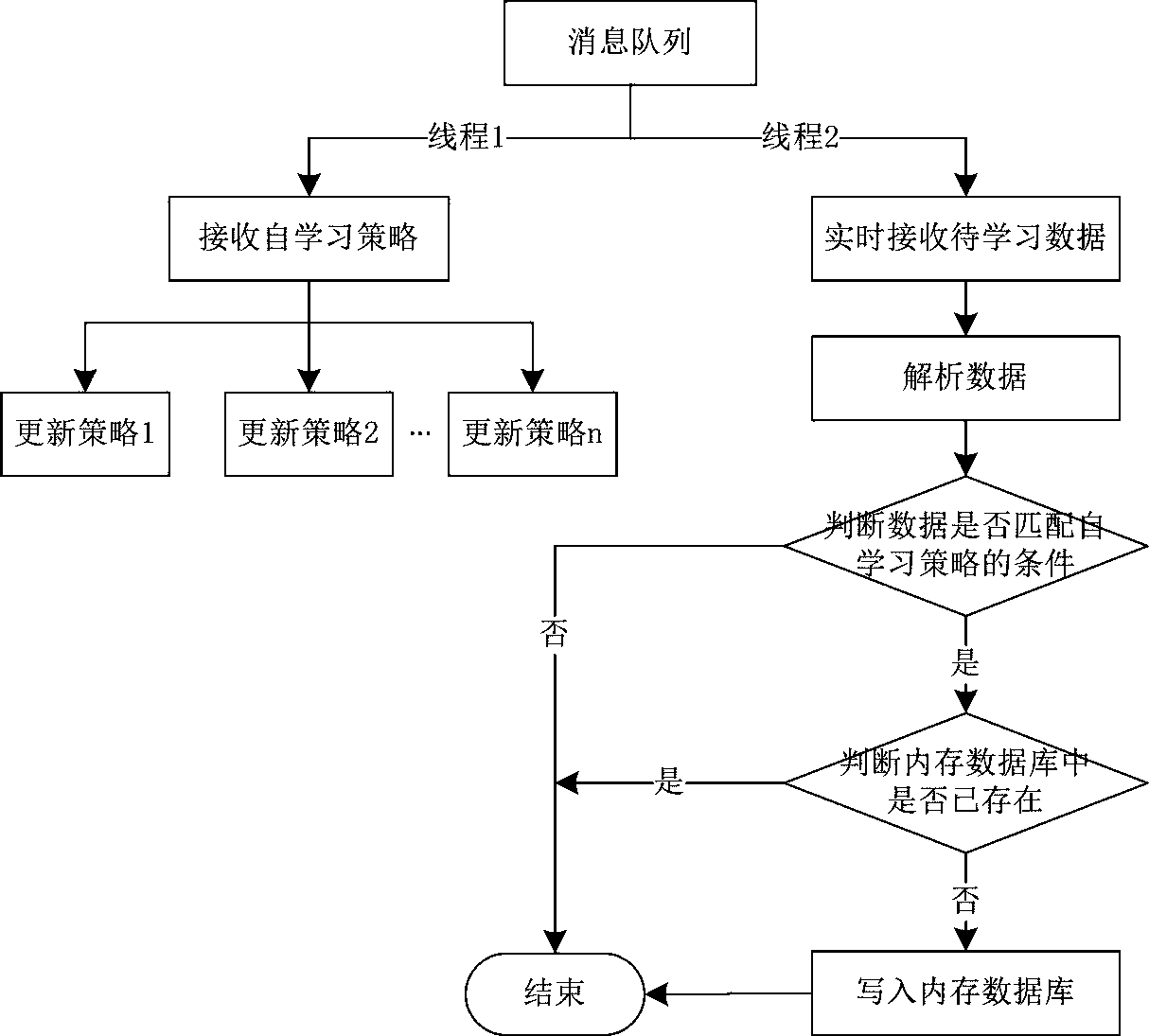
[0024] URL self-learning is to summarize the normal model of the site protection object by learning the data information of the user's normal traffic to the protected site, and generate the corresponding whitelist policy, which is loaded into the whitelist rule engine to detect and protect abnormal traffic .
[0025] Such as figure 1 As shown, based on the URL self-learning Web protection method, URL self-learning and Web security protection are carried out simultaneously in real time, that is, to determine whether the requested URL exists in the memory database; if it exists, transfer the request to the Web server for response; It exists, loads and executes the self-learning strategy, and updates it to the memory database; at the same time, when the requested URL triggers the white list of the web protection, the corresponding preset action is executed.
[0026] Specifically, first configure the information of the site that needs security protection through the interface, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com