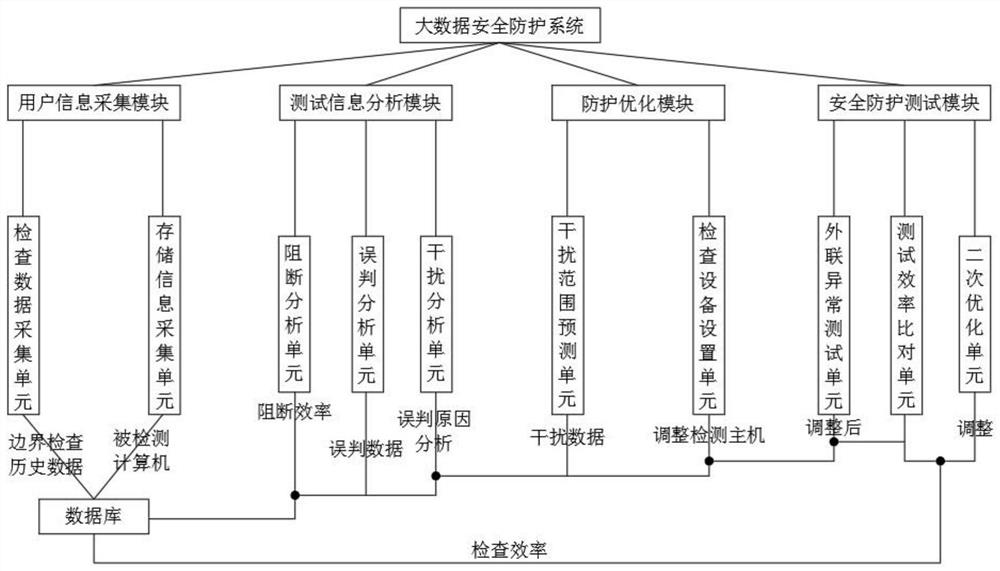
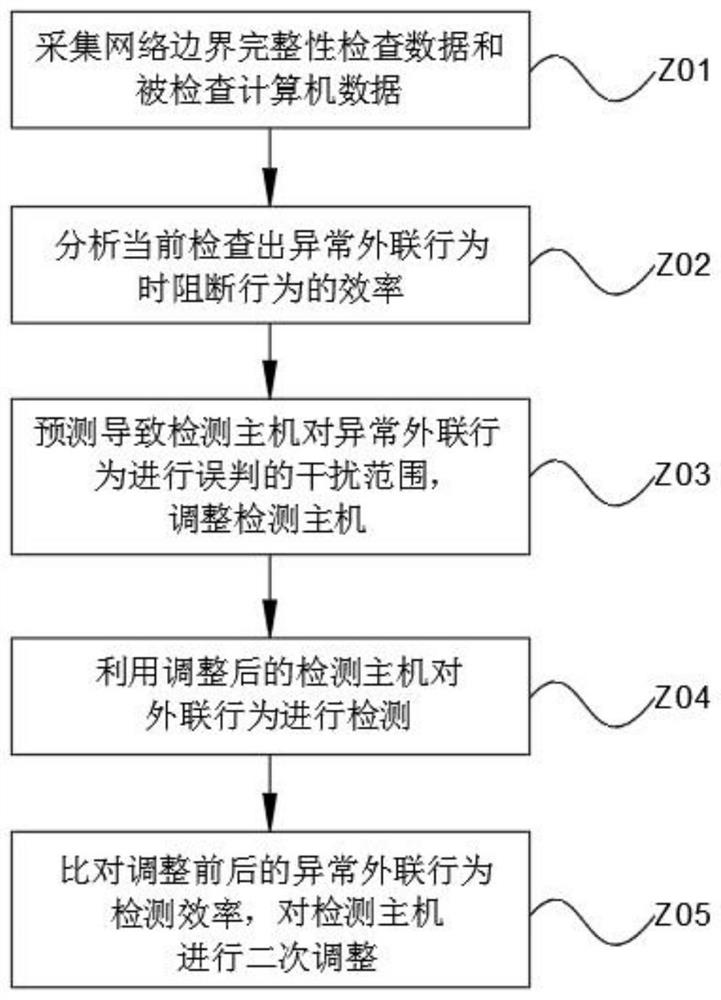
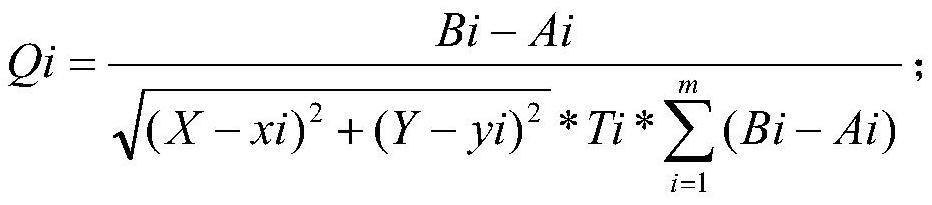Big data security protection system and method based on network security
A security protection and network security technology, applied in the field of network security, can solve problems such as the inability to improve the efficiency of detecting and blocking abnormal outreach behaviors, and misjudgment of outreach behaviors, so as to improve security protection efficiency, reduce misjudgments, and reduce interference Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0058] Example 1: Collect the IP address of the detection host, parse the IP address, model the boundary integrity check environment, and obtain the location coordinates of the detection host as (X, Y)=(20, 20). Detect the IP address of the computer, parse the IP address, and obtain the location coordinate set of the detected computer as (x, y)={(x1, y1), (x2, y2), (x3, y3)}={(6, 6 ), (10, 10), (15, 15)}, the set of times that the detected host detected abnormal outreach behavior of the detected computer in the intranet was obtained as B={B1, B2, B3}={6, 8 , 4}, the set of times the abnormal outreach behavior of the detected computer is blocked due to misjudgment is A={A1, A2, A3}={2, 3, 0}, and the abnormal outreach behavior of the detected computer is analyzed. The set of average duration of blocking is T={T1, T2, T3}={8, 6, 10}, according to the formula The total efficiency that the detection host detects and blocks the abnormal outreach behavior of the detected computer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com