Method for Quantitatively Assessing Information Security Vulnerability of Scada System
A system information and quantitative evaluation technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of not considering the defense measures and the impact of the vulnerability of the SCADA system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
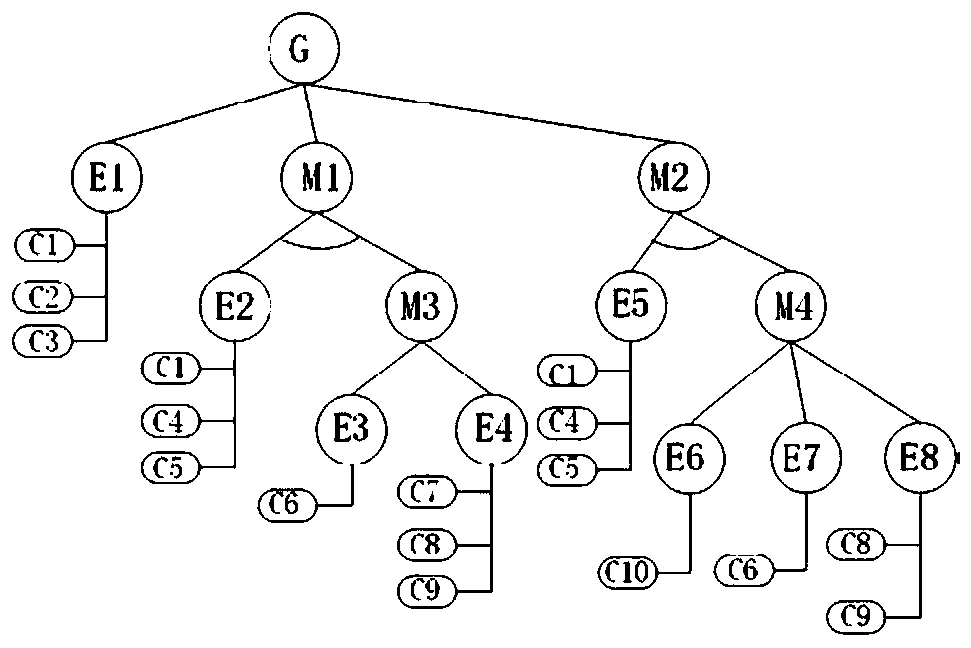
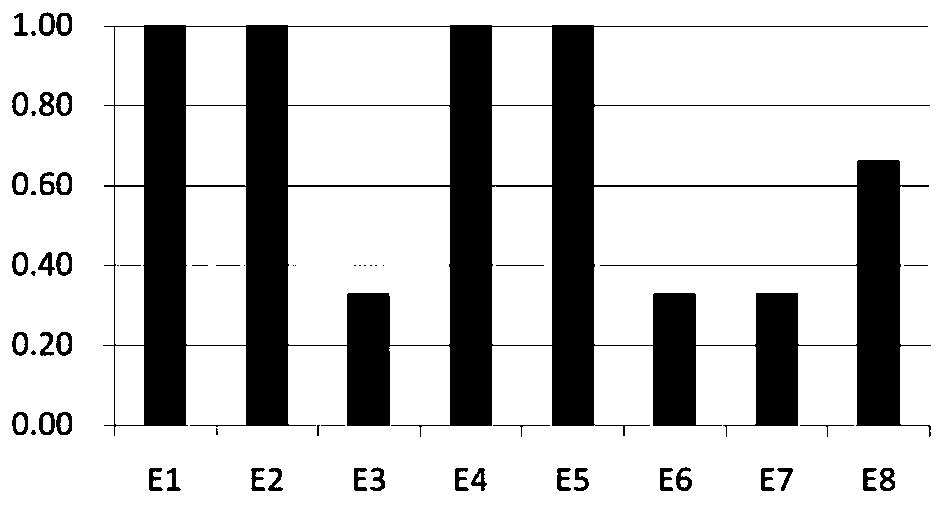
[0058] In this example, an example of an attack defense tree of a SCADA system is constructed, and the method of the present invention is applied to evaluate the vulnerability of its leaf nodes, attack sequences and the overall system.
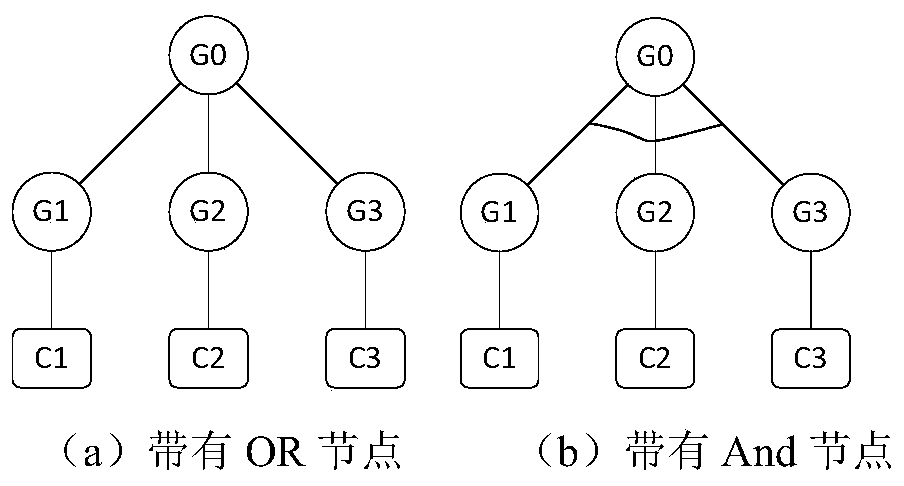
[0059] According to the definition and composition structure of SCADA system, its information security threats may come from three places, that is, from the master station, slave station and communication network. Through analysis, construct such as figure 2 An example of an attack defense tree is shown. The meanings of its root node, intermediate node, leaf node and defense node are shown in Table 1:
[0060] Table 1 Meaning of each node in the attack defense tree
[0061]
[0062] In practical applications, evaluators can establish corresponding scoring standards according to the actual situation, and then give the corresponding attribute score of each leaf node according to this standard. In this example, the scoring standard shown in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com