Anti-theft method, mobile terminal and computer readable storage medium
A technology of mobile terminal and anti-theft method, which is applied in the protection of internal/peripheral computer components, telephone communication, digital data authentication, etc., and can solve the problems of increased difficulty in retrieving mobile terminals and failing to detect theft of mobile terminals in time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
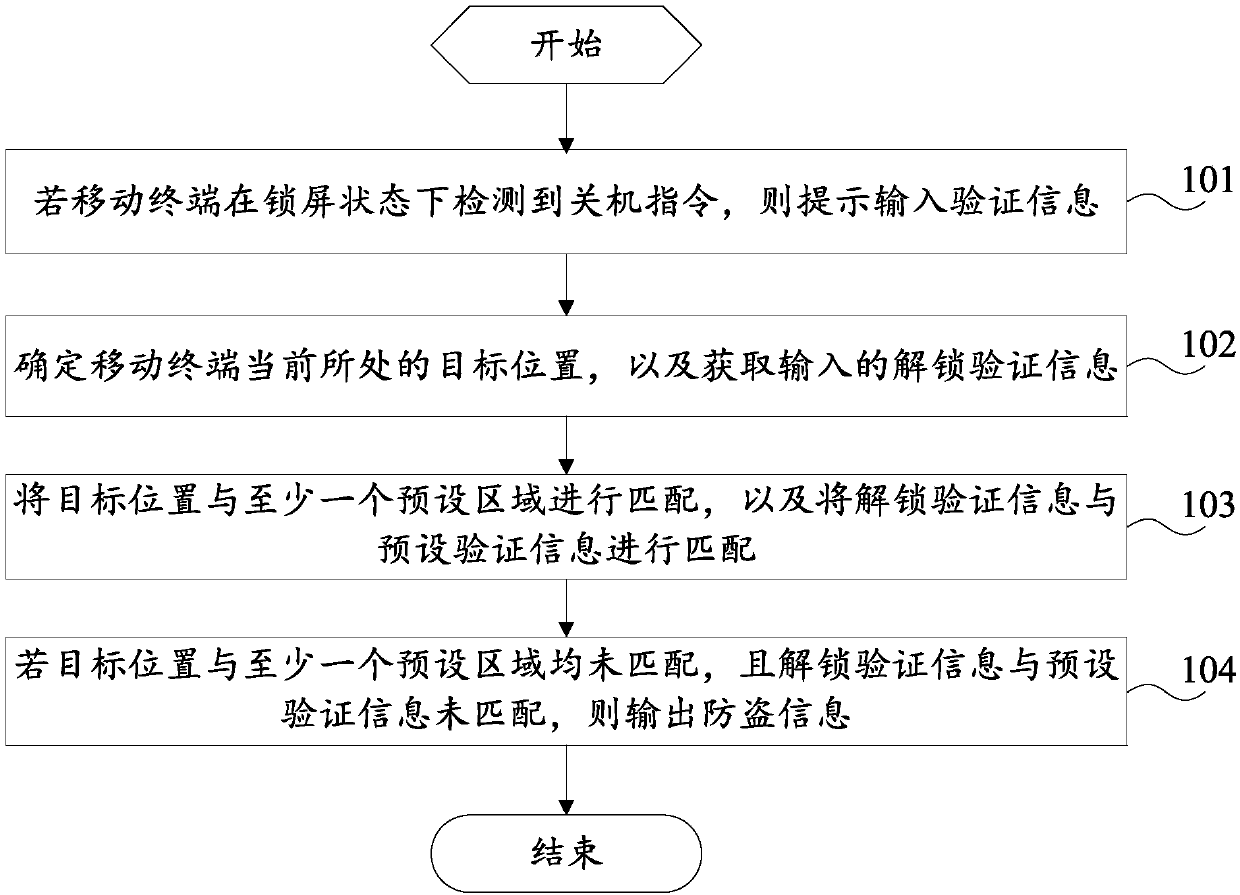
[0028] refer to figure 1 , which shows a flow chart of the anti-theft method in Embodiment 1 of the present invention, which may specifically include the following steps:
[0029] In step 101, if the mobile terminal detects a power-off command in the screen-locked state, it prompts to input verification information.
[0030] In the embodiment of the present invention, in order to protect privacy information, the user usually sets unlock verification information for the mobile terminal. After the mobile terminal is locked, the mobile terminal will unlock the screen only if the correct unlock verification information is input, and then the user can unlock the mobile terminal. Perform other operations on the mobile terminal interface. However, because criminals will directly shut down the mobile terminal after stealing it, and any remedial measures after shutting down will be useless, therefore, the mobile terminal must be guaranteed to be turned off in the screen unlocked state...
Embodiment 2
[0042] refer to figure 2 , which shows a flow chart of the anti-theft method in Embodiment 2 of the present invention, which may specifically include the following steps:
[0043] In step 201, if the mobile terminal detects a power-off command in the screen-locked state, it prompts to input verification information.
[0044] This step is similar to the implementation process of step 101 above, and will not be described in detail here.
[0045] For example, when the mobile terminal detects a power-off instruction in a locked screen state, a prompt window may be displayed to prompt the user to input verification information required for unlocking.
[0046] Step 202, determine the current target location of the mobile terminal.
[0047] In the embodiment of the present invention, when the mobile terminal detects a power-off instruction in a locked screen state, the current target location of the mobile terminal is available.
[0048] For example, the mobile terminal may deter...
Embodiment 3
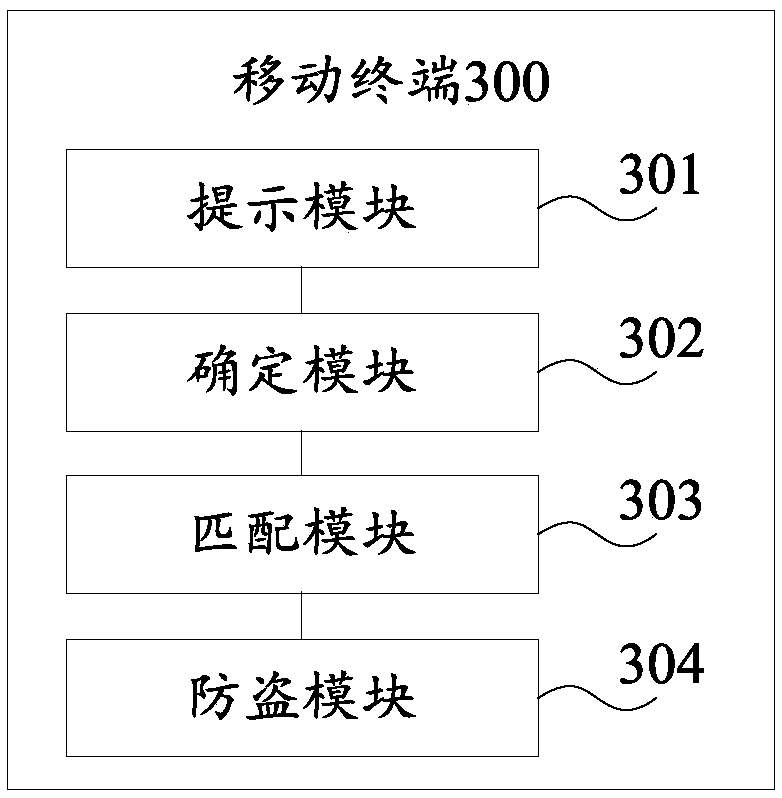
[0096] refer to image 3 , which shows a structural block diagram of a mobile terminal 300 according to Embodiment 3 of the present invention, which may specifically include:
[0097] A prompting module 301, configured to prompt input of verification information if the mobile terminal detects a power-off command in a screen-locked state;
[0098] A determining module 302, configured to determine the current target location of the mobile terminal, and acquire input unlock verification information;
[0099] A matching module 303, configured to match the target location with at least one preset area, and match the unlock verification information with preset verification information;
[0100] The anti-theft module 304 is configured to output anti-theft information if the target location does not match the at least one preset area, and the unlock verification information does not match the preset verification information.
[0101] optional, see Figure 4 , the anti-theft module ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com