Self-protection method and device for CA terminal
A protection device and terminal technology, applied in the direction of internal/peripheral computer component protection, etc., can solve problems such as terminal loss, achieve the effect of reducing value, increasing possibility, and strengthening security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
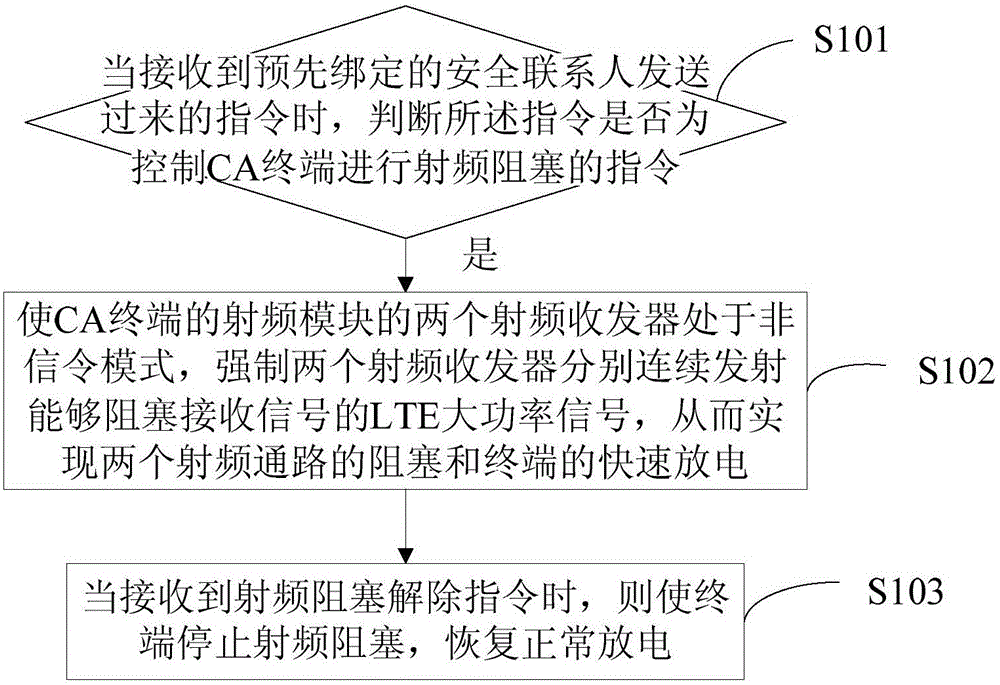
[0030] Embodiment 1 of the present invention provides a self-protection method for a CA (CarrierAggregation, carrier aggregation) terminal, which is aimed at a terminal supporting uplink carrier aggregation, regardless of whether it is a CA of China Unicom Telecom or a CA of China Mobile. The present embodiment will be described in detail below in conjunction with the accompanying drawings. figure 1 It is a flow chart of the method of Embodiment 1 of the present invention, please refer to figure 1 , the method of the embodiment of the present invention includes the following steps:
[0031] Step S101, when receiving an instruction sent by a pre-bound security contact, determine whether the instruction is an instruction to control the CA terminal to block radio frequency;
[0032] Specifically, in the setting of the CA terminal, a security contact may be preset. After the setting is complete, you need to bind with the security contact to complete the relevant security interac...
Embodiment 2
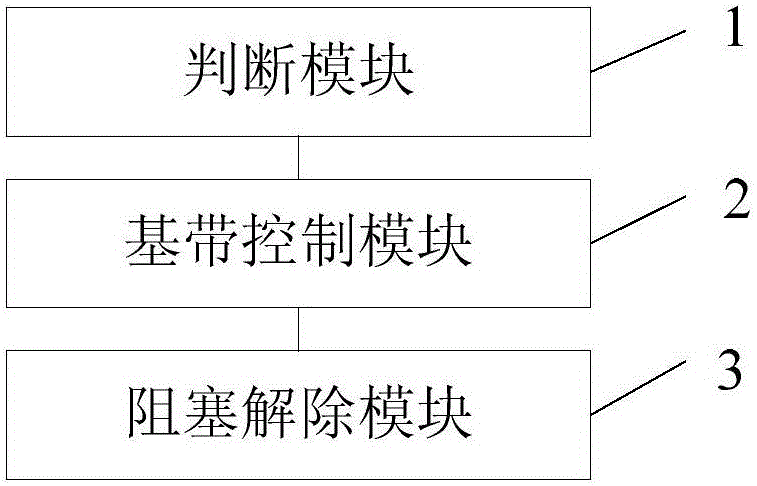
[0047] Embodiment 2 of the present invention provides a self-protection device for a CA terminal, please refer to figure 2 , the device according to the embodiment of the present invention includes a judging module 1, a baseband control module 2 and a blocking unblocking module 3, and the principles of the above modules will be described in detail below.
[0048] The judging module 1 is configured to, when receiving an instruction sent by a pre-bound security contact, judge whether the instruction is an instruction to control the radio frequency blocking of the CA terminal.
[0049] Specifically, in the setting of the CA terminal, a security contact may be preset. After the setting is complete, you need to bind with the security contact to complete the relevant security interaction.
[0050] When the CA terminal is stolen or lost, the user can send a short message to the CA terminal through the pre-bound security contact, and at this time, the judging module 1 will judge and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com