A storage device capable of remotely deleting data and its use method
A storage device and data deletion technology, which is applied in digital data authentication, electronic digital data processing, computer security devices, etc., can solve the problems of inability to guarantee the safety of storage devices, failure to retrieve U disks, loss of storage devices, etc., to prevent Effects of data theft, increased likelihood, ease of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be further described below in conjunction with the accompanying drawings, but this should not be used as a limitation to the protection scope of the claims of the present invention.
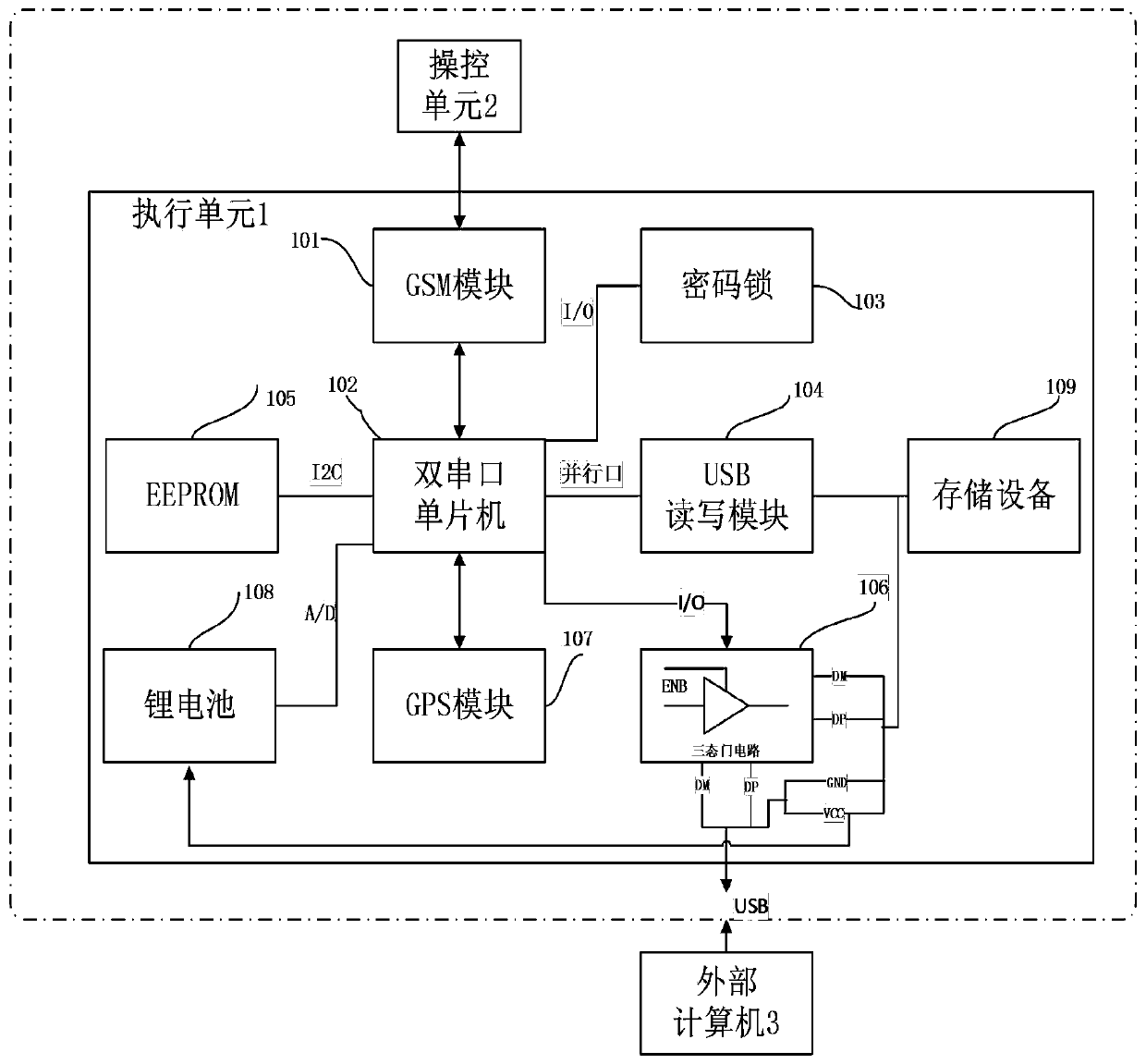
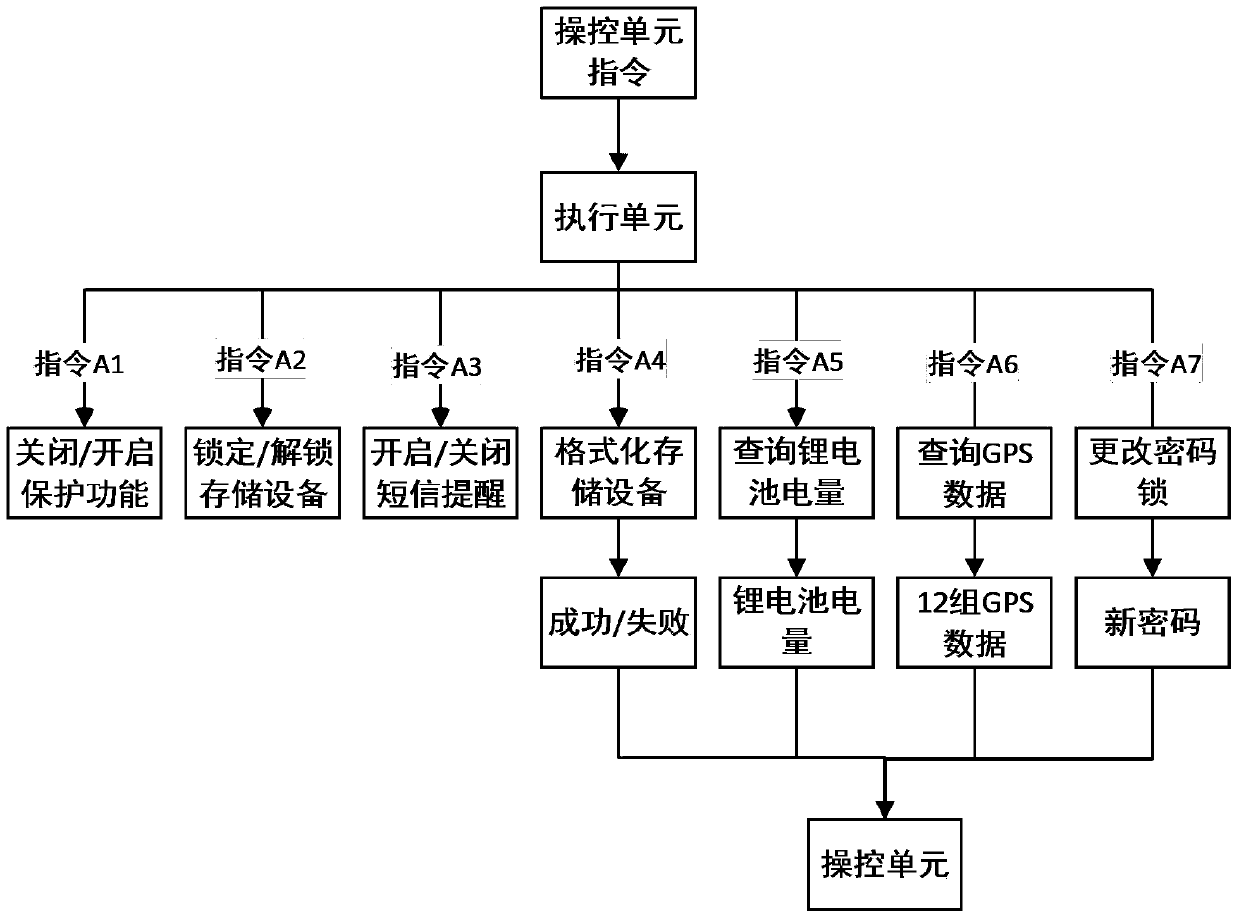
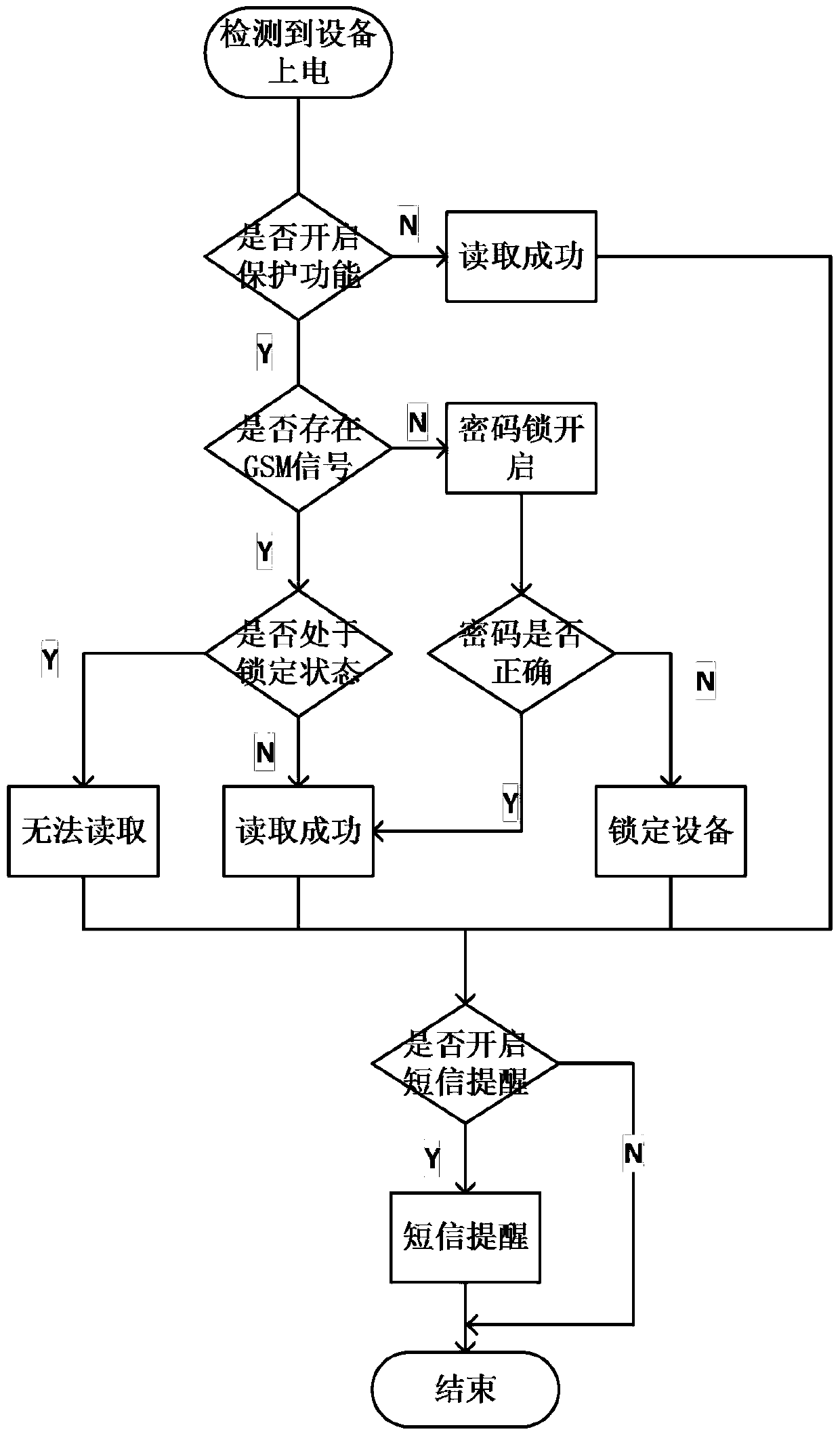
[0020] figure 1 The example shown shows that, figure 1 Inside the middle dotted line frame is the storage device (abbreviated as the storage device) of the present invention that can delete data remotely, including the control unit 2 and the execution unit 1, the control unit 2 is a preset mobile phone that communicates with the execution unit 1, and the execution unit 1. Receive the command sent by the control unit 2; the execution unit 1 includes a dual-serial single-chip microcomputer 102, a GSM module 101, a GPS module 107, a USB read-write module 104, a storage device 109, and an EEPROM (Electrically Erasable Programmable Read-Only Memory) 105 , lithium battery 108, password lock 103 and tri-state gate circuit 106; described dual serial port single-chip mic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com