Verification method based on secondary geographic location information
A geographic location information and secondary verification technology, applied in the field of verification based on secondary geographic location information, to achieve a safe and reliable verification method and prevent false passes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The content of the present invention will be described in detail below in conjunction with the accompanying drawings and embodiments of the description:
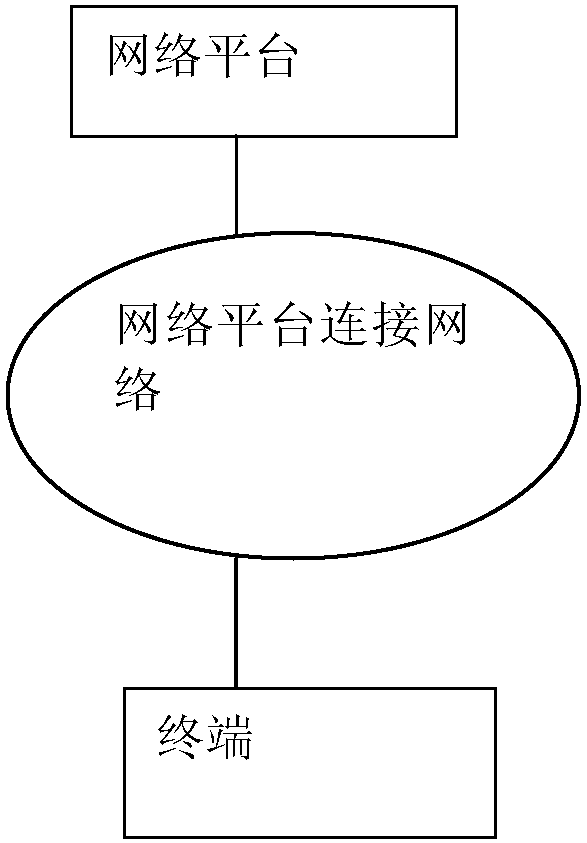
[0019] figure 1 It is a schematic diagram of the network connection of the current single-terminal verification mode. In this mode, the user's business confirmation work is performed on terminal A, and the network platform passes the user's business confirmation application after obtaining the correct verification information.
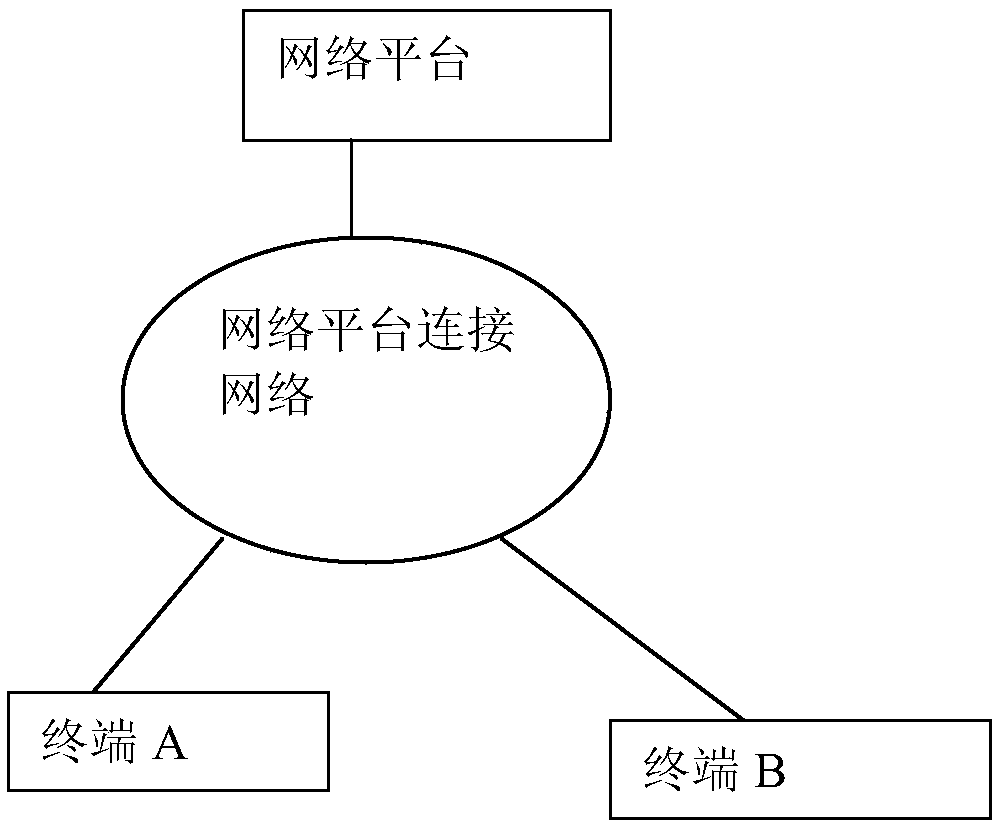
[0020] figure 2 It is the network connection schematic diagram of the current dual-terminal verification mode; in this mode, the user's business confirmation work is performed on terminal A, and the network platform obtains the correct verification information and sends it to terminal B for secondary verification After receiving the information, the terminal A confirms the application through the user's business.
[0021] Under the above two verification modes, with the cooperation of Troja...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com