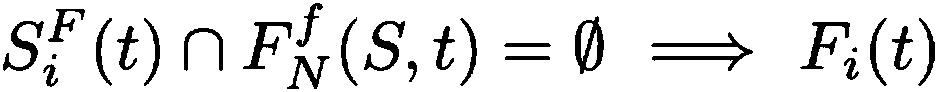Attack detection and identification method for sensors in presence of transient fault
A technology of attack detection and identification method, which is applied in the field of CPS system, can solve the problems of not considering transient faults, ignoring sensor error measurement, etc., and achieve the effect of good detection and identification performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
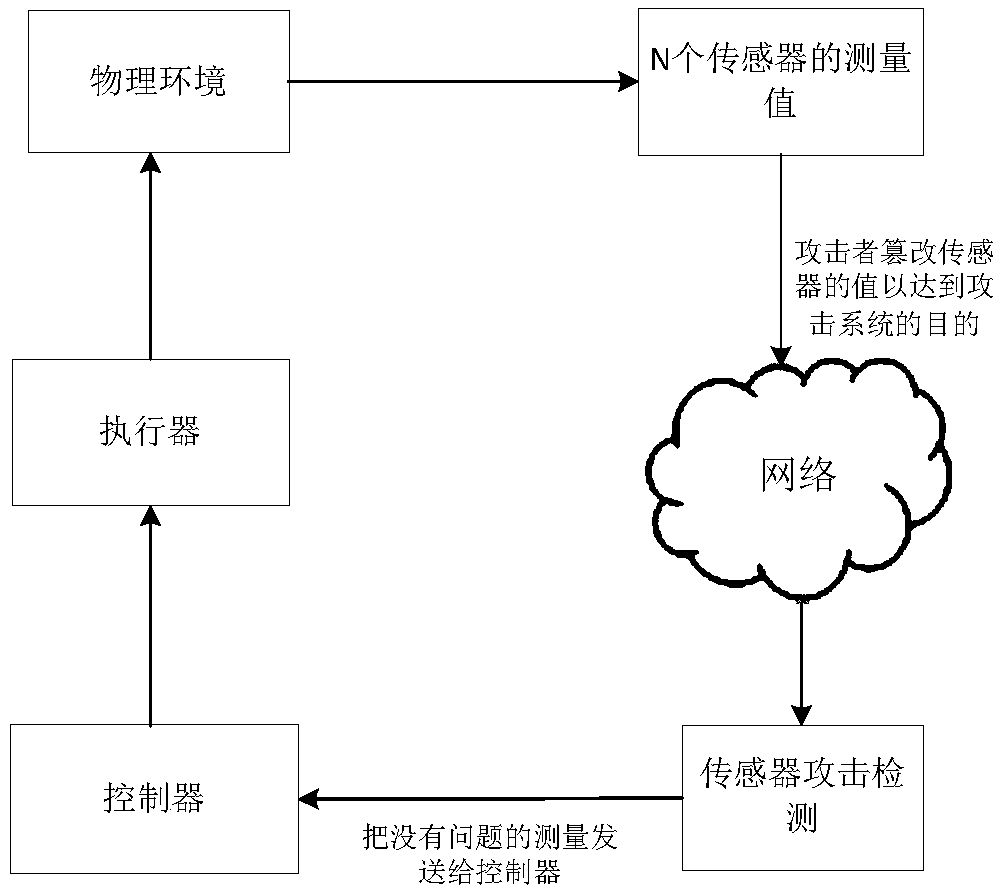
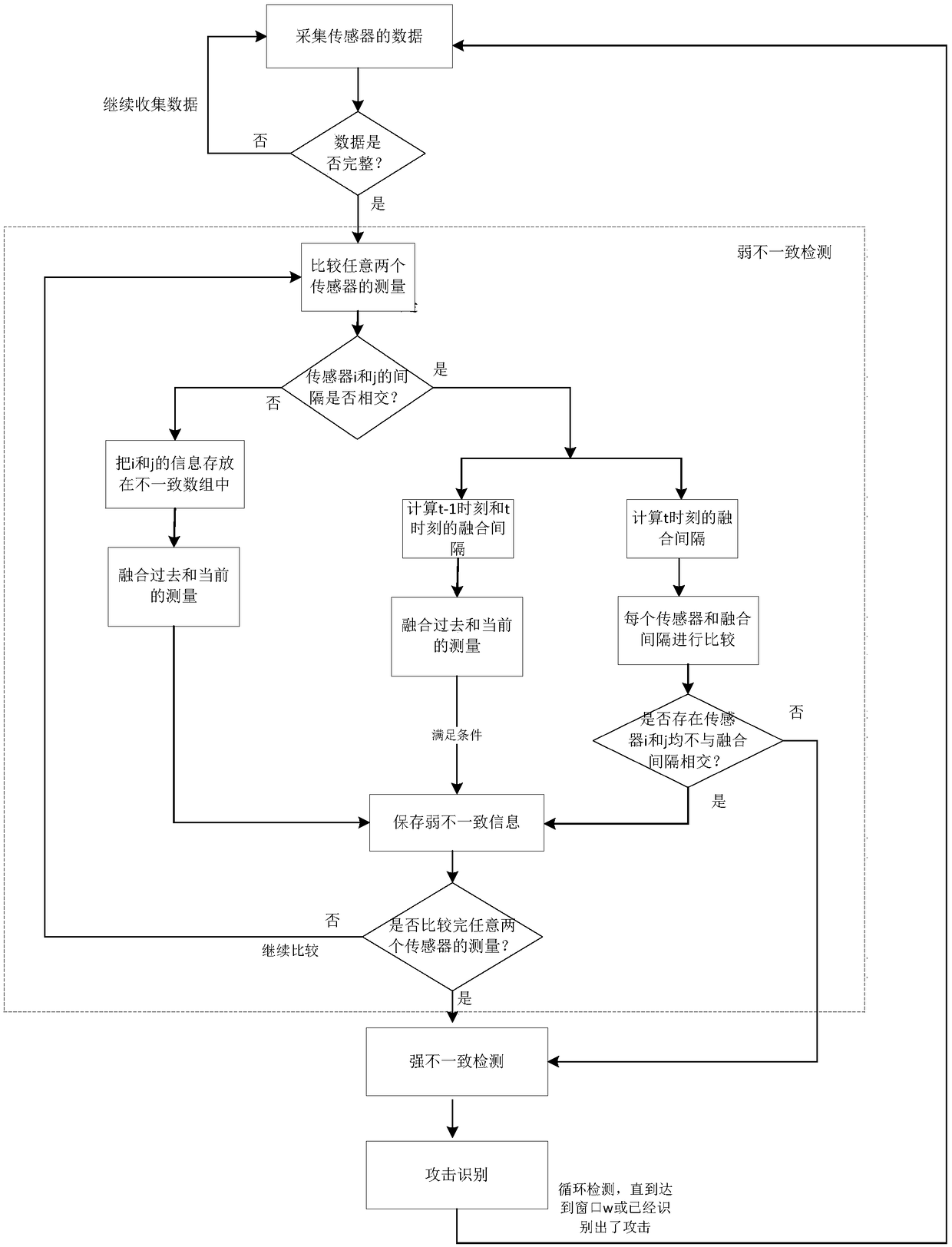
[0039] The invention relates to a sensor attack detection and identification method in the presence of transient faults, combining the fusion interval to further judge the detection of faults when two sensor intervals intersect, and considering the system dynamics model, using historical measurements to improve the accuracy of sensor attack detection and identification Performance; Set forth in detail below with embodiment.
[0040] (1) Hardware device:
[0041] The present invention uses a ground vehicle named EV3 as an experimental platform to test the performance of the attack detection and identification method. EV3 is the third MINDSTORMS robot developed by Lego in 2013. It is equipped with ultrasonic sensors, color sensors, touch sensors, motors, etc. The present invention uses an ultrasonic sensor and two left and right...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap