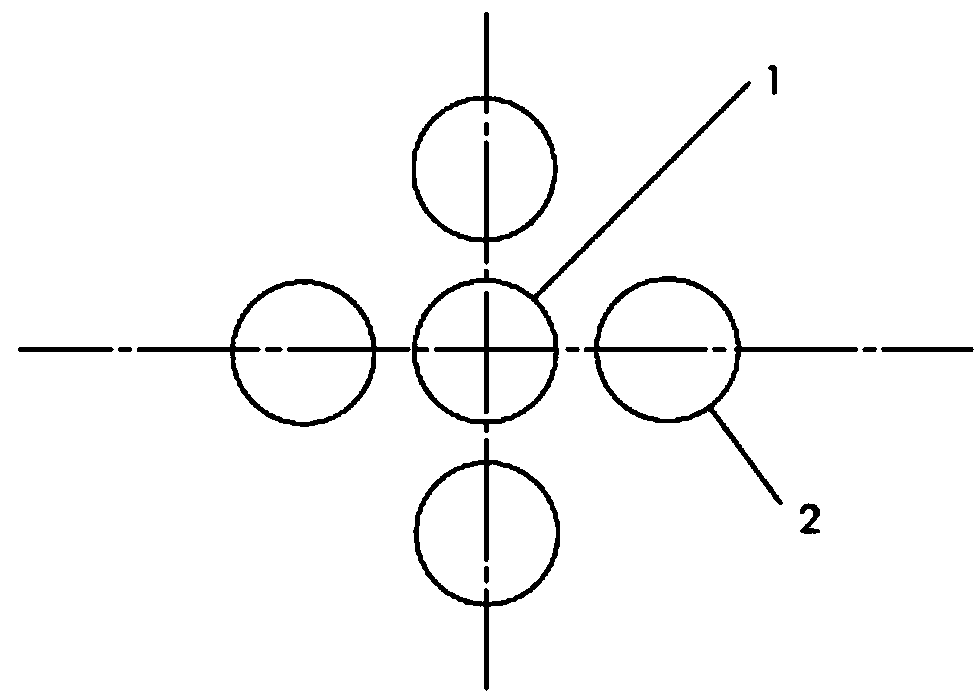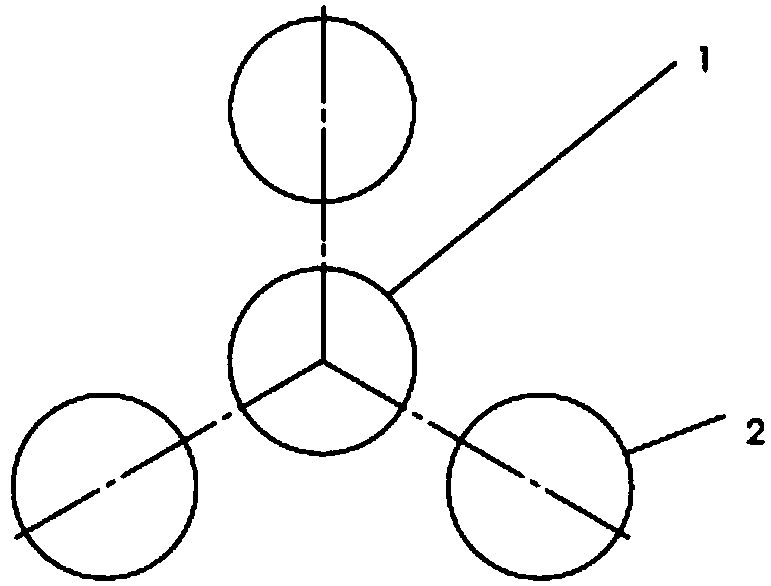Multi-touch key false triggering prevention method and structure
A multi-touch and button technology, which is applied in the direction of instruments, electrical digital data processing, and input/output process of data processing, etc., can solve problems such as equipment malfunction, no good solution, and easy triggering of touch buttons by mistake, so as to reduce Effect of False Trigger Probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0012] Embodiment one: if figure 1 The central position of the center is the "lock / unlock" button (1), and 4 common function buttons (2) are evenly distributed around it. From the area covered by these four function buttons (2), any object (including Human body) will trigger the surrounding function buttons (2) first, and then the "Lock / Unlock" button (1), but a touch vertically approaching from the upper part of the "Lock / Unlock" button can produce a normal touch effect.
[0013] The identification and processing method of the key is as mentioned above, only when the "lock / unlock" is touched and the other keys are not touched, the touch is considered to be a valid touch, and then the timing is started, only if the touch remains for more than the set time (such as 2.5 Seconds), the touch is considered to be valid. If there are other key inputs or if the touch hold time exceeds the maximum allowable value (such as 10 seconds), it is considered to be a false trigger and re-enter...
Embodiment 2
[0016] Embodiment two: figure 2 The central position of the lock is the "lock / unlock" button (1), and 3 common function buttons (2) are evenly distributed around the periphery.
[0017] Other implementation measures are the same as in Embodiment 1.
[0018] Since the three circular buttons surround the "lock / unlock" button with a large air gap, the circular buttons can be arranged in an oval shape, reducing the probability of false triggering.
[0019] The advantage of this solution is that fewer keys are required, but there are more leaky areas around it than the first option, and approaching from the leaky area may cause false triggering, and the preventive effect is slightly inferior to the first option.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com