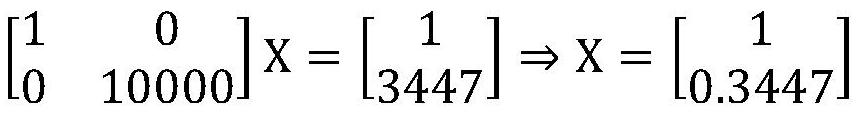A Fully Homomorphic Encryption Method Based on Random Unitary Matrix in Outsourced Computing
A fully homomorphic encryption and unitary matrix technology, applied in homomorphic encryption communication, secure communication devices, digital transmission systems, etc., can solve the problems of uncertain calculation results, no correct results, and loss of deterministic value of calculation results, etc., to achieve Effects of improving security and reducing calculation load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the implementation examples described here are only used to illustrate and explain the present invention, and are not intended to limit this invention.
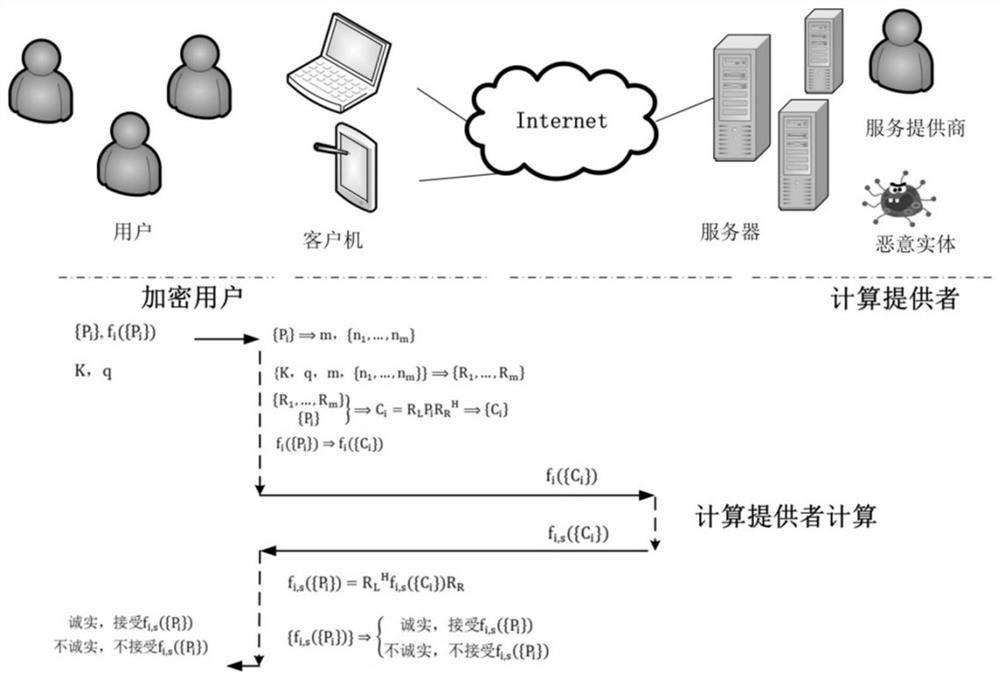
[0028] The application scenario of this embodiment is outsourcing computing, assuming that a certain user has a set of data {P i}={P 1(r×t) ,P 2(t×t) ,P 3(t×t) ,(P 4(t×t)}, a computational task f 1 ({P i}) = P 1 P 2 ÷(P 3 +P 4 ), where P i The subscript indicates the number of rows and columns of the matrix, such as P 1(r×t) , indicating that P 1 is an (r×t) matrix. The user gives a security goal G and a security parameter λ under the goal. Suppose the user chooses the Internet cloud server, such as figure 1 , a fully homomorphic encryption met...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com