Authorization management method and system
An authorization management and authorization code technology, applied in the field of embedded system development, can solve the problems of increasing management costs, static link libraries cannot guarantee legal permissions, and poor security, so as to avoid the increase of management costs and reduce the risk of being cracked.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
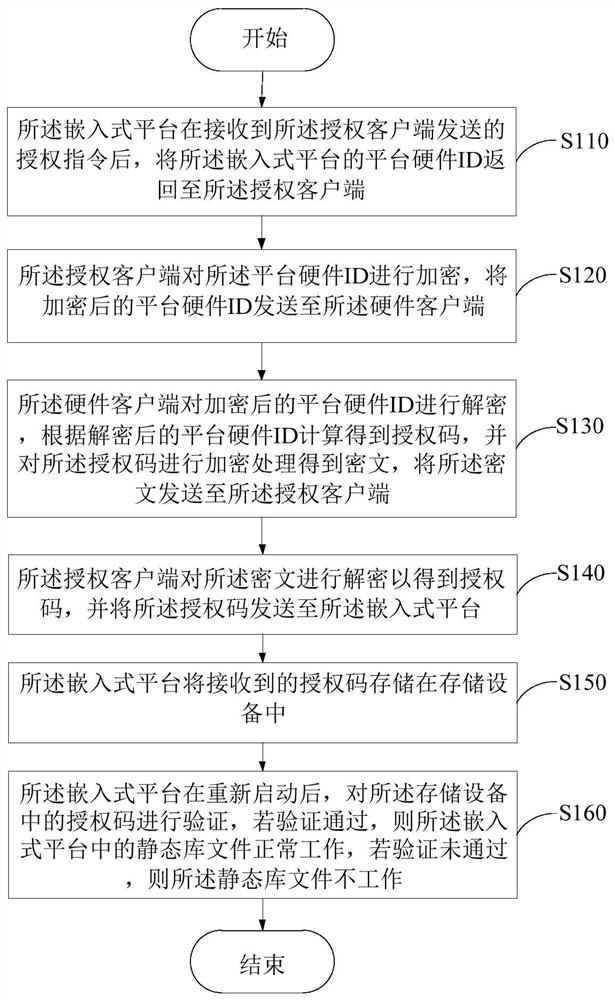
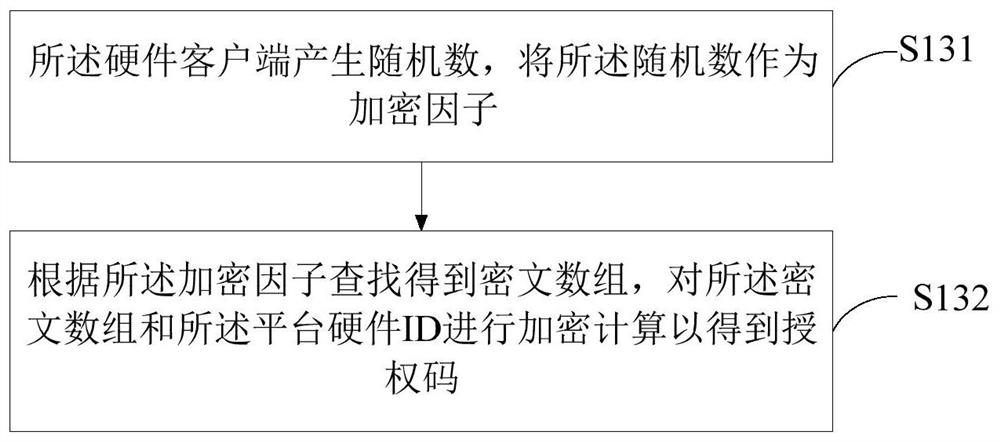
[0049] The inventors have found through research that the commonly used authorization methods for embedded systems in the prior art include using encryption ICs for authorization verification. However, this method requires an external IC, which increases the cost for the use of library files. At the same time, external ICs generally use random numbers for verification, but the generation of random numbers depends on the generation of the platform, and static library files cannot be fully controlled. After the platform redirects the random number generation function, it can generate a fixed value, and the code can be cracked. The encryption scheme, based on the above two points, is not suitable for the authorization of static library files.
[0050]In addition, in the prior art, the authorization client uses the hardware ID of the embedded platform to generate the authorization code Key1, and the embedded device receives the authorization code sent by the client for FLASH stora...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com