Information security protection method, device, electronic equipment and storage medium
A technology for information security and protection devices, applied in computer security devices, digital data protection, platform integrity maintenance, etc., can solve problems such as easy cracking of credit granting methods, reduce the risk of cracking, improve security levels, and protect information security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
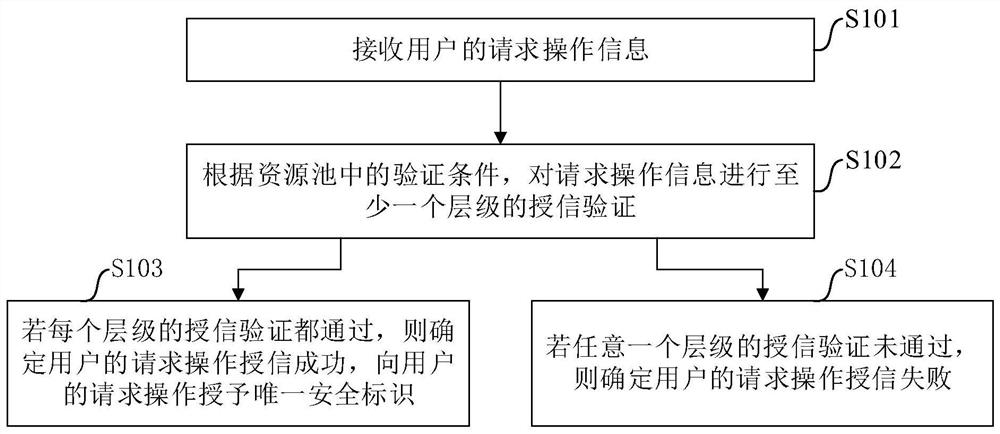
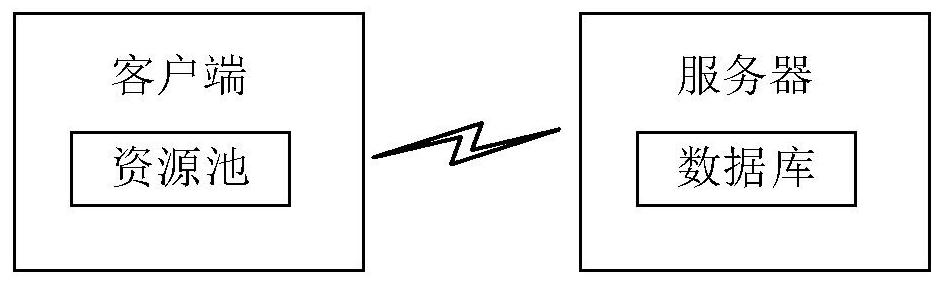
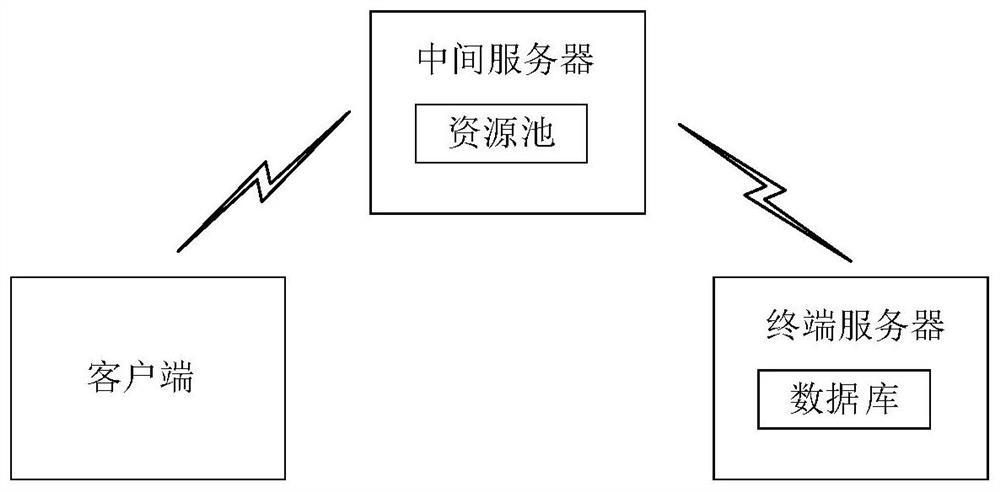
[0028] The present application is described in detail below, and examples of embodiments of the present application are shown in the drawings, wherein the same or similar reference numerals denote the same or similar components or components having the same or similar functions throughout. Also, detailed descriptions of known technologies will be omitted if they are not necessary to illustrate the features of the present application. The embodiments described below by referring to the figures are exemplary only for explaining the present application, and are not construed as limiting the present application.
[0029] Those skilled in the art can understand that, unless otherwise defined, all terms (including technical terms and scientific terms) used herein have the same meanings as commonly understood by those of ordinary skill in the art to which this application belongs. It should also be understood that terms, such as those defined in commonly used dictionaries, should be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com