Multi-strategy control method and device for shared access
A shared access, multi-strategy technology, applied in the field of communications, can solve the problems of inconsistent requirements for shared access, insufficient user monitoring, and inability to implement separate control of different access devices, so as to meet the needs of use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
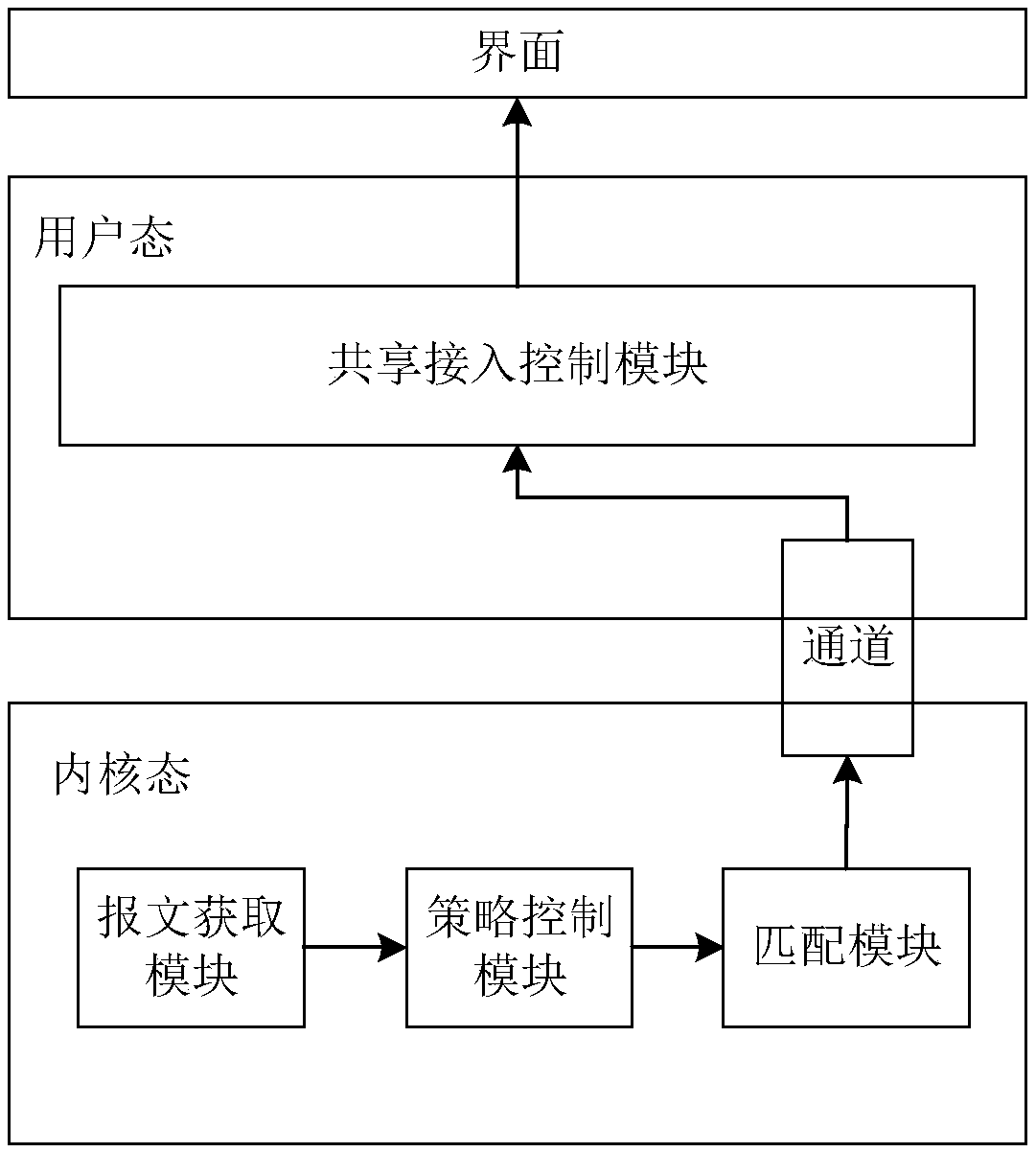
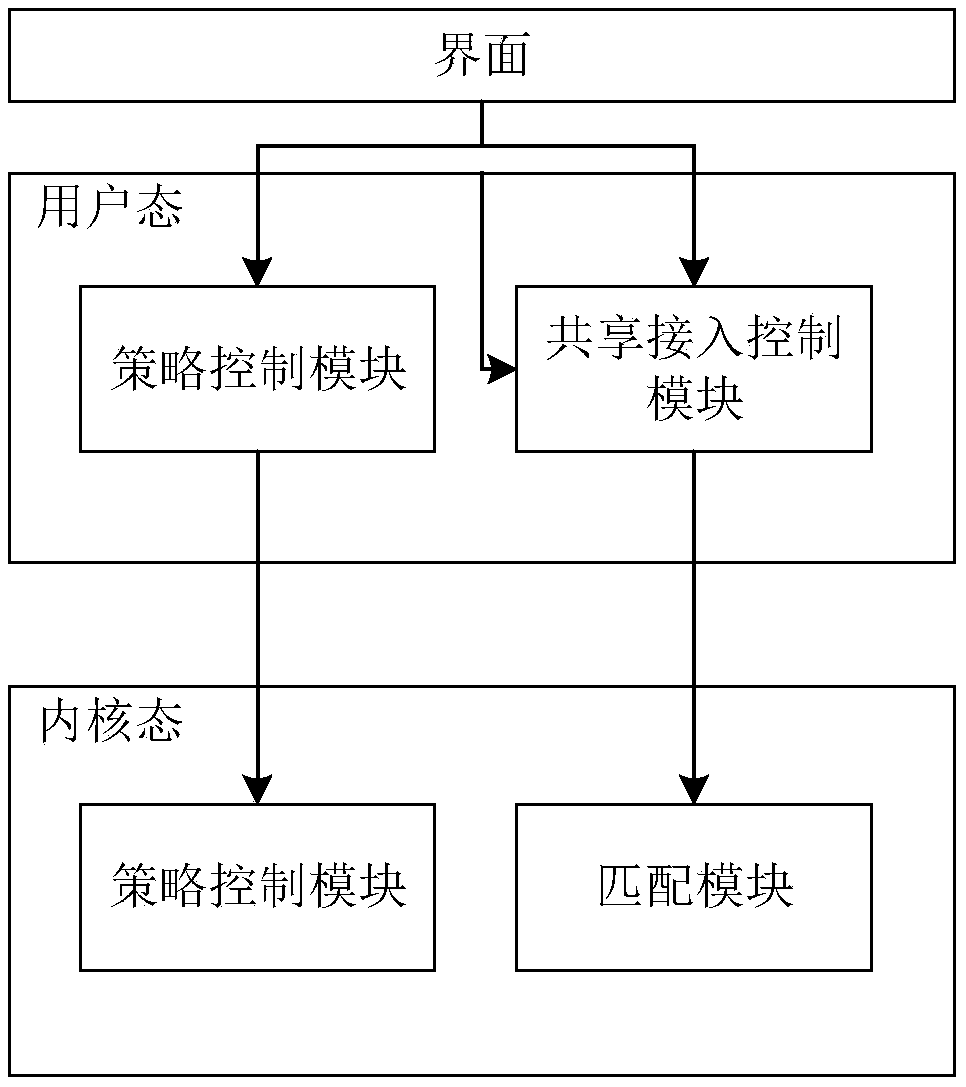
Image
Examples
Embodiment Construction
[0043] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
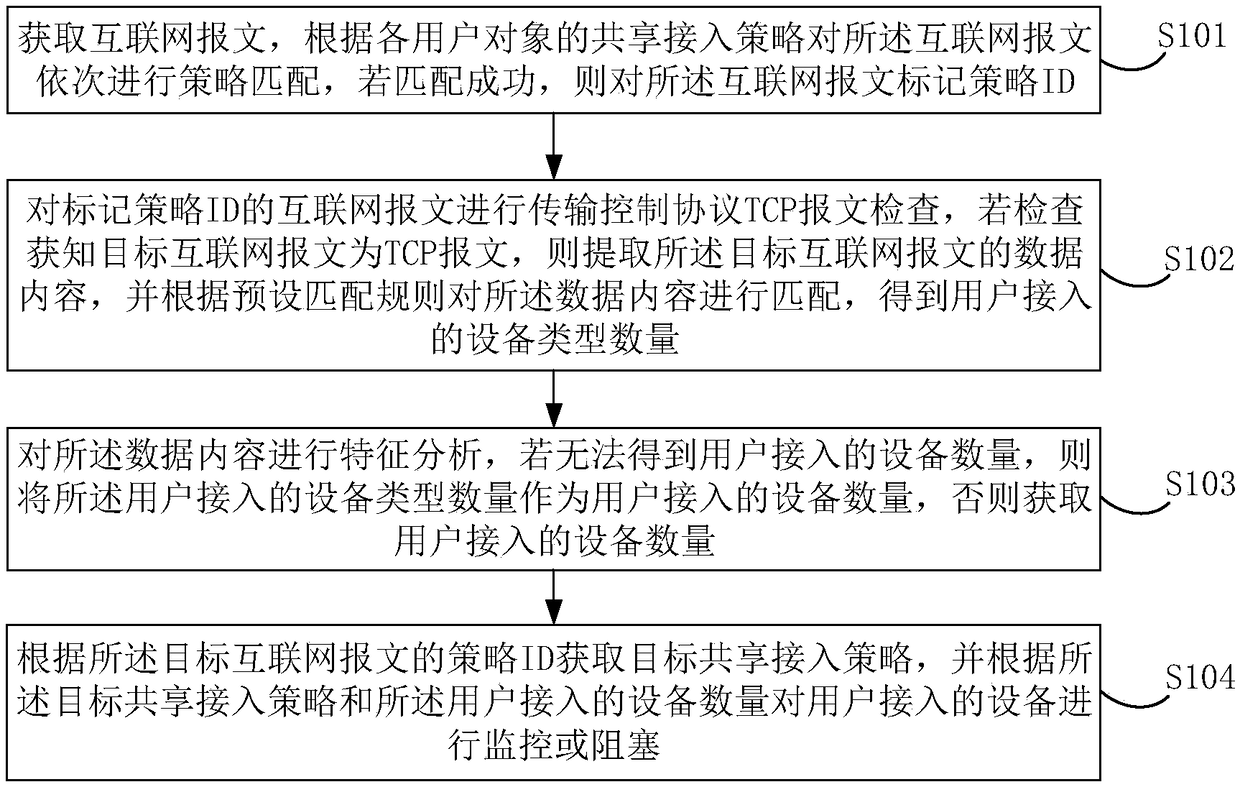
[0044] figure 1 It shows a schematic flowchart of a shared access multi-policy control method provided by this embodiment, including:
[0045] S101. Acquire Internet packets, perform policy matching on the Internet packets in sequence according to the shared access policies of each user object, and mark the Internet packets with a policy ID if the matching is successful.
[0046] Wherein, the user objects form different object sets according to different locations and times of the users, and each user object includes several users.
[0047]Specifically, the corresponding user objects are defined in the shared access policy, and each user object corresponds to multip...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com