A program defense method and system based on digital certificate
A digital certificate, defense system technology, applied in the direction of platform integrity maintenance, can solve problems such as zero-day attacks, and achieve the effect of blocking malware and spam
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
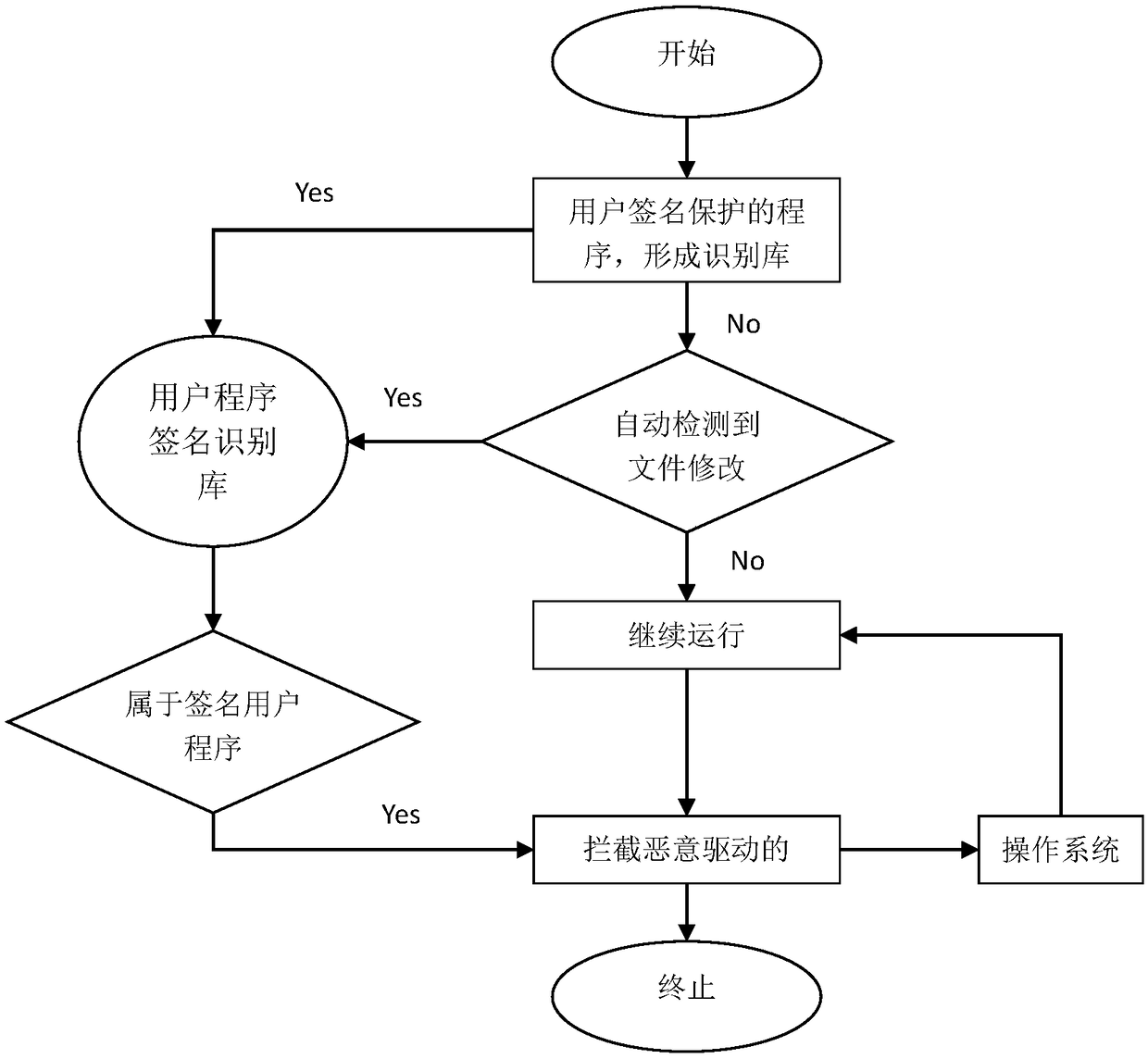
[0026] Such as figure 1 As shown, a digital certificate-based program defense method of the embodiment includes steps:
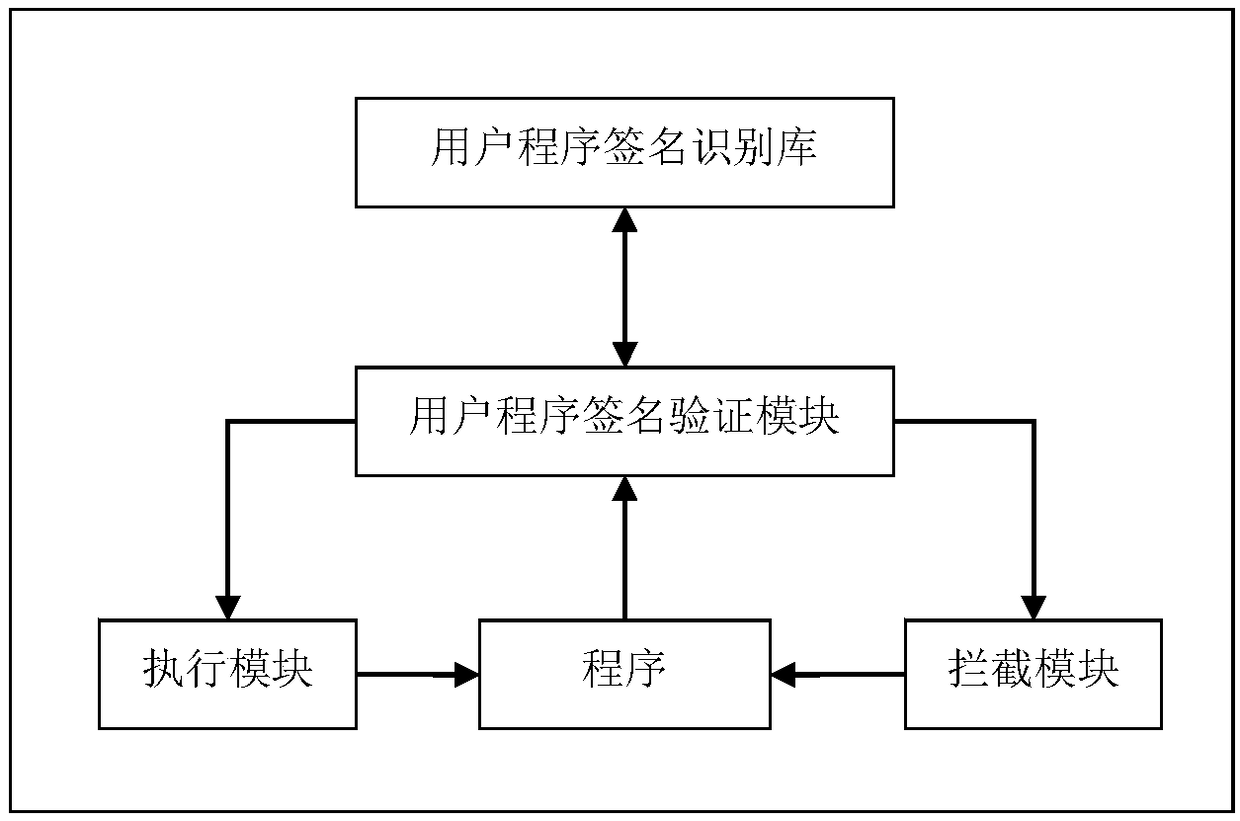
[0027] The user program signature identification library is established. The specific operations of this embodiment include collecting protection programs that require user signatures to form a user program signature identification library.
[0028] Detect whether the digital signature of the program is legal; in this embodiment, judge whether the digital signature of the program is legal by judging whether the digital signature of the program is in the user program signature identification library. The specific operations include, when it is detected that the user program is running or modified, verifying the digital certificate signature information of the program with the information stored in the user program signature identifica...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap