A detection method for obfuscated-openssh protocol traffic
A detection method and protocol technology, applied in instruments, computing, electrical components, etc., can solve the problem of inability to effectively identify the Obfuscated-Openssh protocol, achieve reliable detection results, and overcome the effect of high false alarm rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
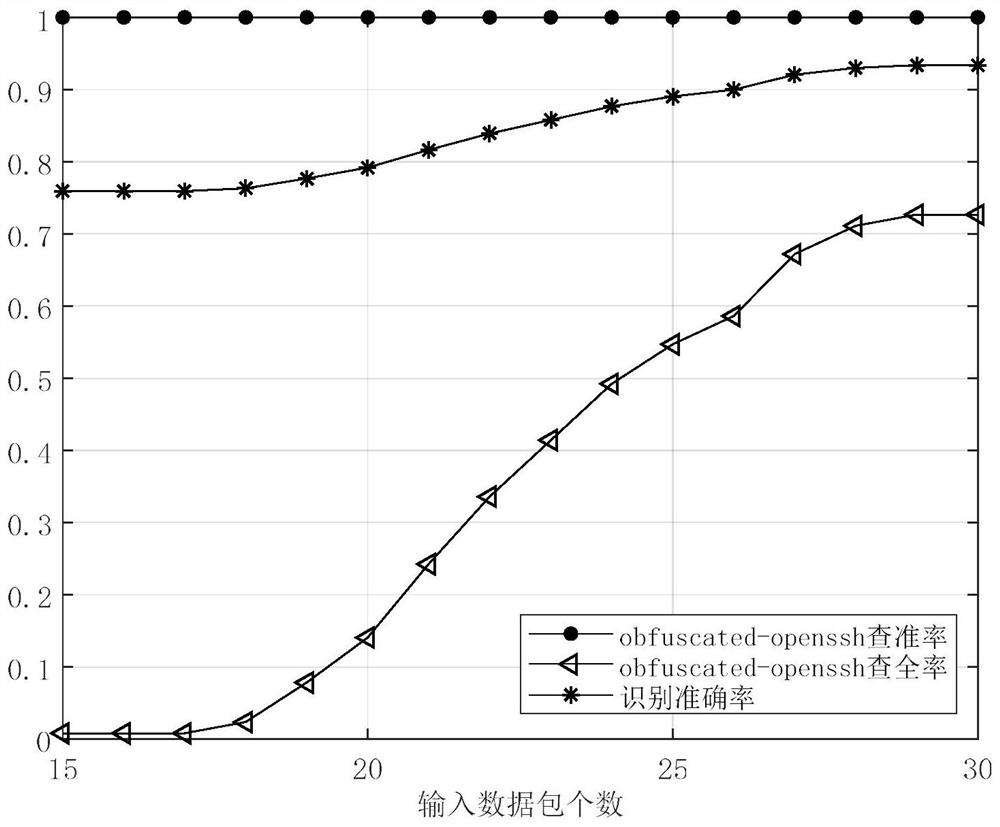
[0040] In order to verify the effectiveness of the solution of the present invention, the following simulation experiments are carried out.
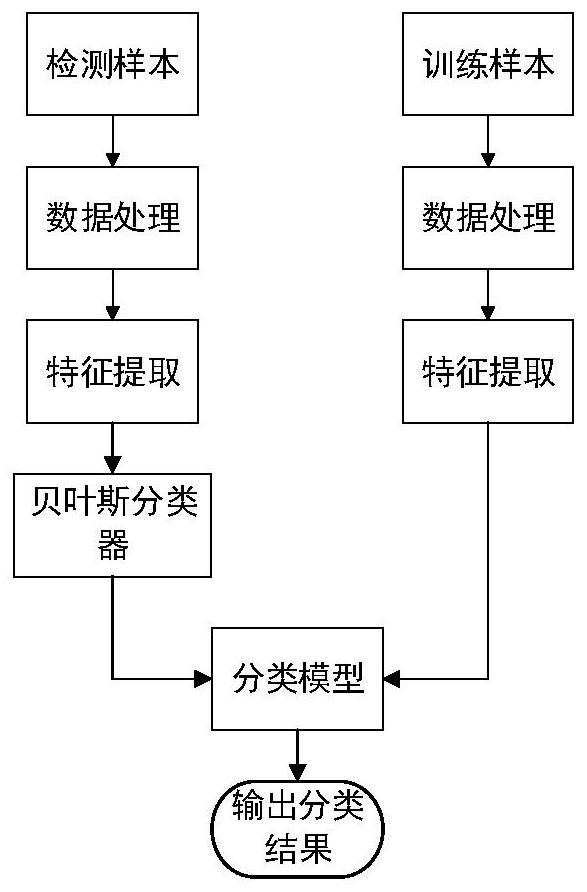
[0041] In this embodiment, for the detection method of the Obfuscated-Openssh protocol, at first capture the training sample flow and the sample flow to be tested, extract relevant features respectively, use the normal data as the training data, and the data to be tested as the test data input into the Bayesian classifier (wherein The processing process of training samples and samples to be tested is not in any order), the specific process is as follows:
[0042] Step 1: Capture Obfuscated-Openssh protocol traffic, capture non-Obfuscated-Openssh protocol traffic, and generate training sample data set S train ;
[0043] Step 2: Stream the training sample data set S according to the TCP quintuple train , and mark the training sample category according to the TCP data flow, mark the Obfuscated-Openssh protocol TCP data flow category as ob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com