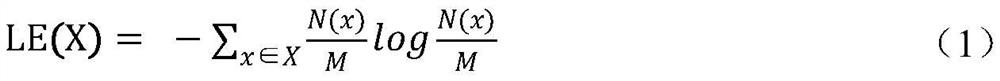A method for detecting HTTP obfuscated traffic based on suspiciousness evaluation
A technology of flow detection and suspiciousness, applied in transmission systems, electrical components, etc., can solve problems such as false alarms, confusion, and lack of versatility, and achieve the effect of overcoming high false alarm rates and good adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0053]In order to verify the effectiveness of the present invention, the following simulation experiment is performed with a certain university campus network.
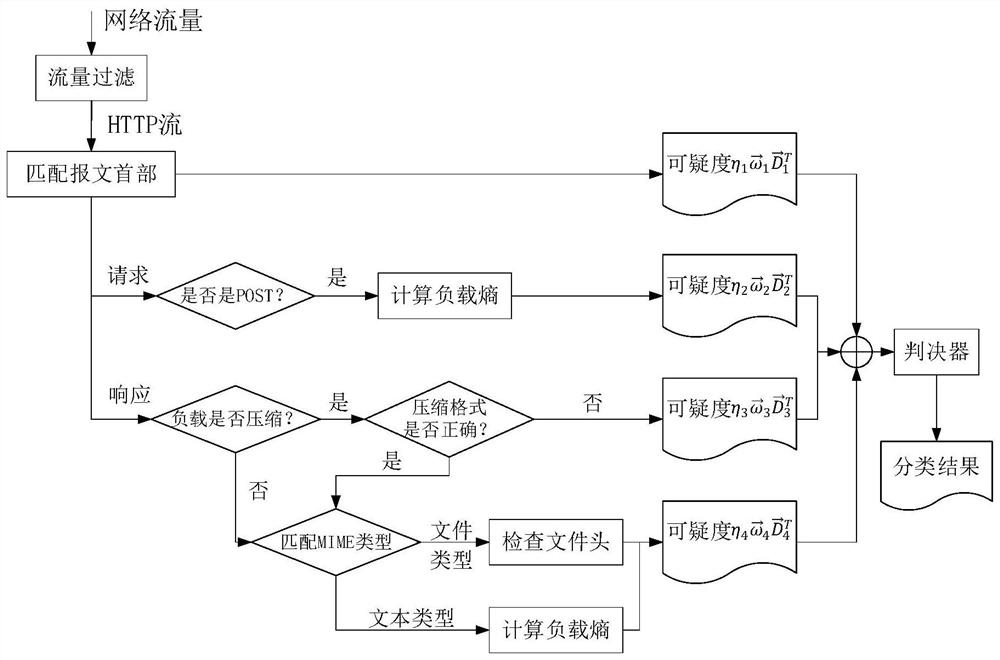
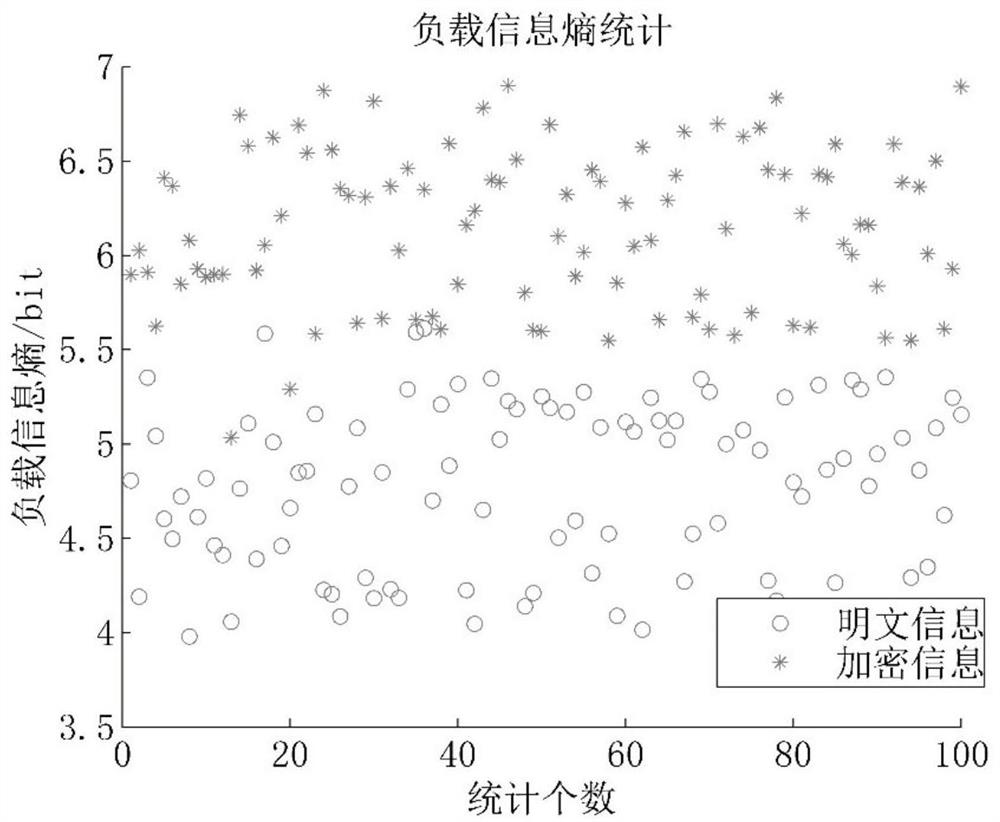
[0054]First filter network traffic, extract the data stream in the HTTP protocol, analyze the integrity of the protocol header information of the HTTP data stream, three characteristics of the content type ID, and load data type, using the doubts of the features, The weight of the doubts is used as the input of the decision, and the decision is determined by the decision data stream belonging to normal HTTP or confuses HTTP. The specific process is as follows:
[0055]Step 1: Set the data capture, use the data capture to capture network traffic data, and filter out the HTTP traffic, the screening rules apply to the regular expression "[A-ZA-Z] {3, 7}. * Http \ / 1 [0, 1] "and" HTTP \ / 1. [0, 1] [0-9] {0,3} ".
[0056]Step 2: Set the data processor, extract the TCP payload of each packet in the HTTP stream, and reorganize the full p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com