Covert communication detection method based on have message encoding in the process of bittorrent file sharing
A technology of message encoding and covert communication, applied in electrical components, transmission systems, etc., can solve the problems of the Have message covert communication detection method proposed in no open literature, achieve reliable detection results, and overcome the effect of high false alarm rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
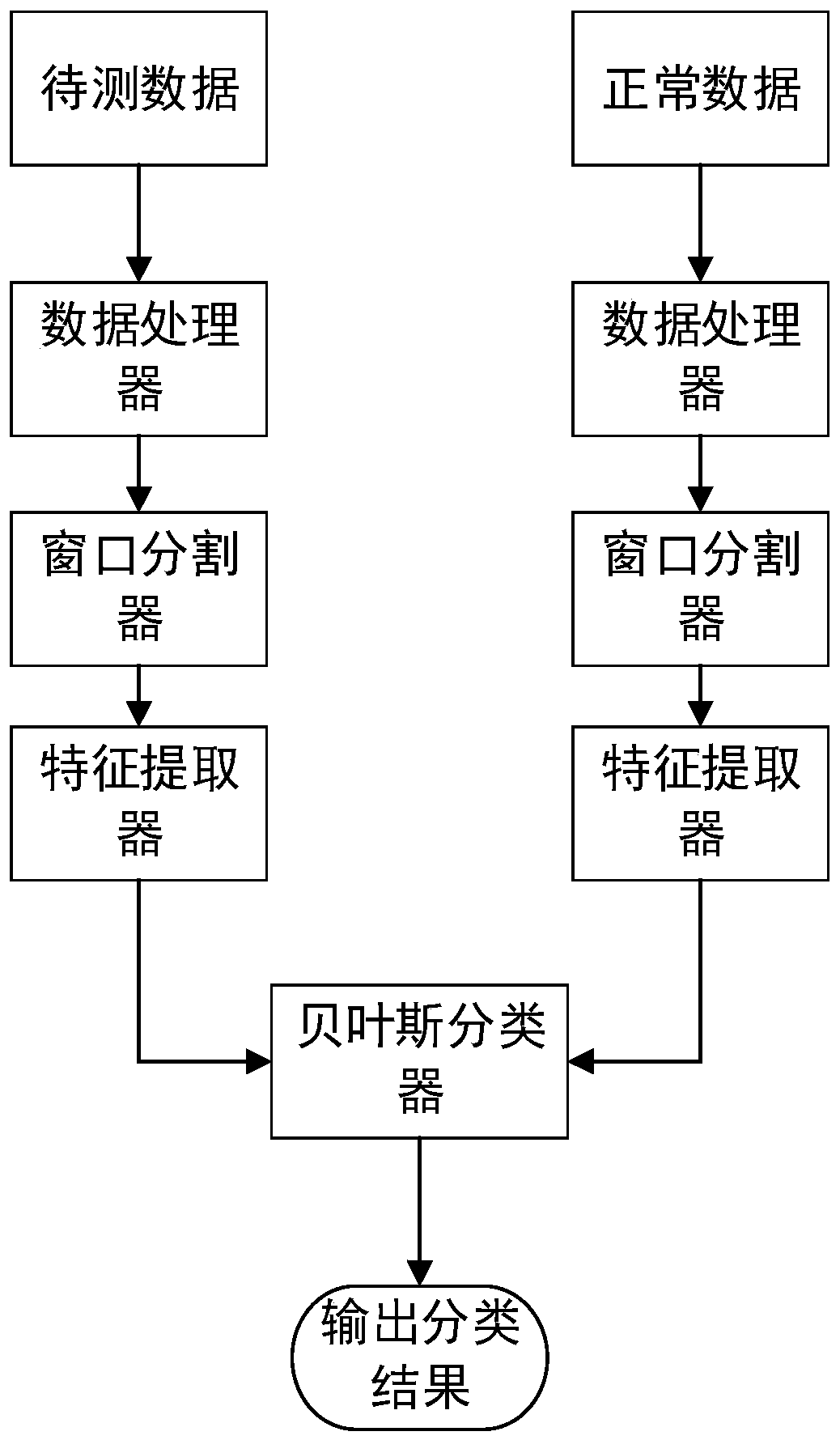
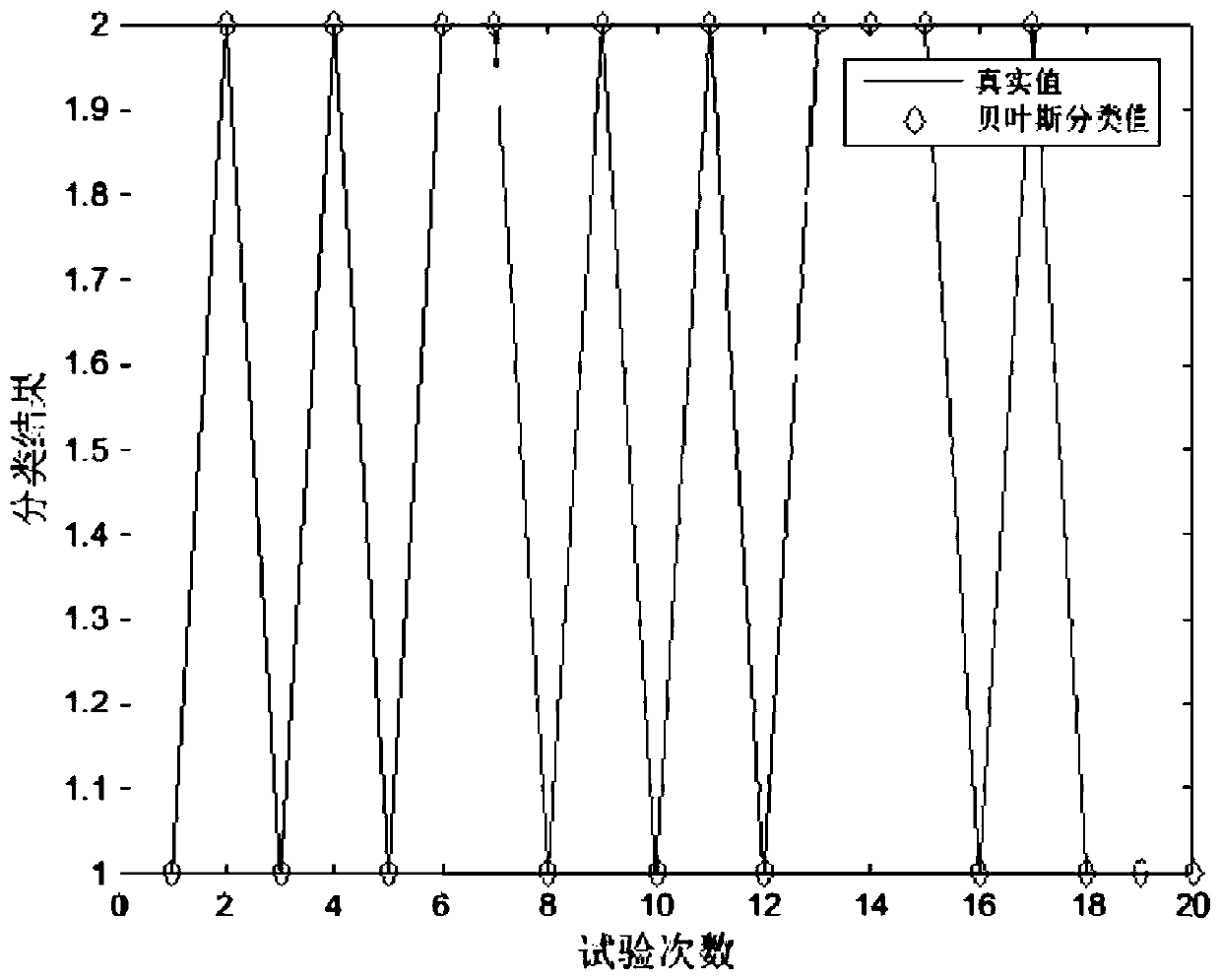
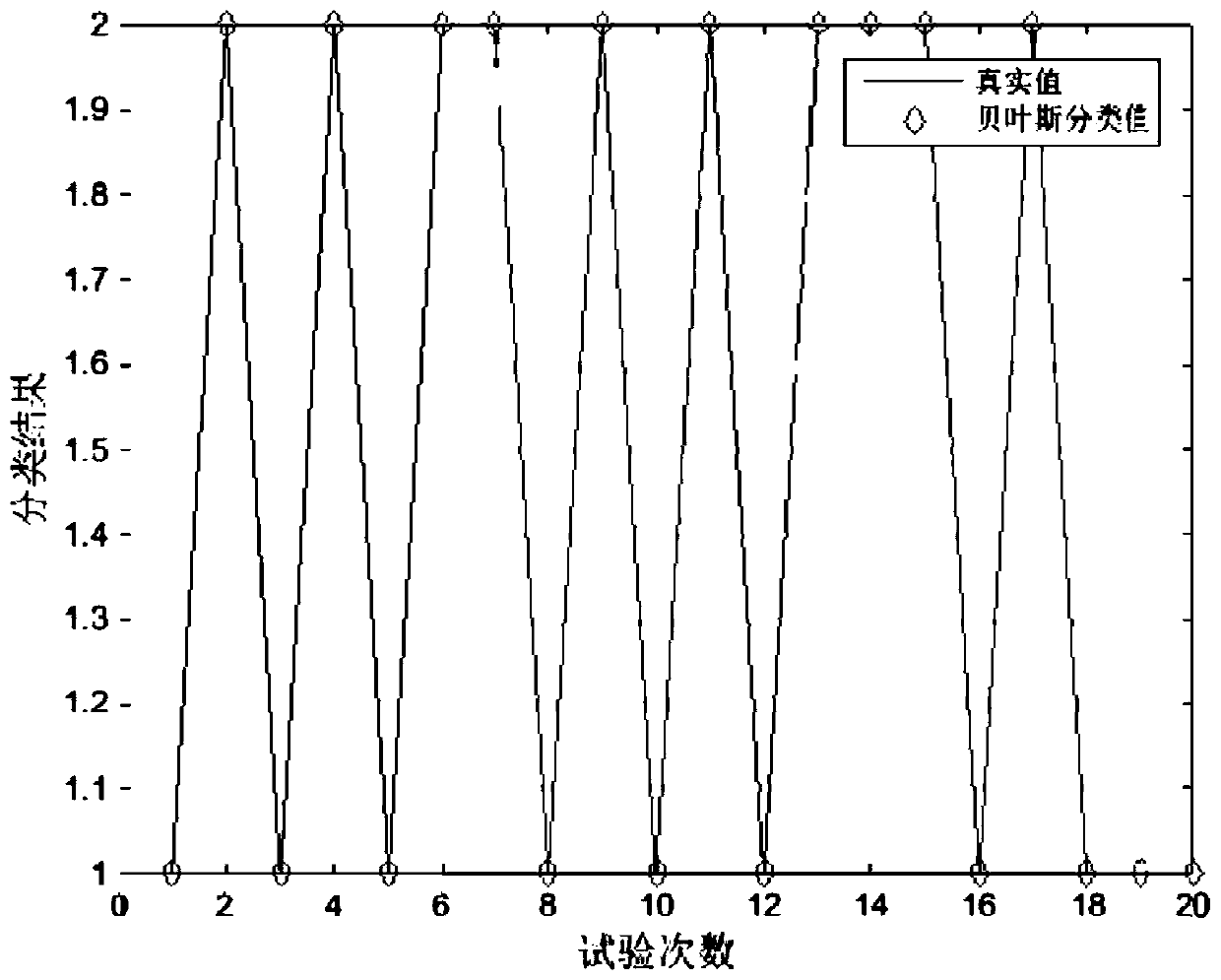
[0037] figure 1 It is a schematic diagram of the detection process based on the Bayesian classifier. In this embodiment, for the covert communication detection method based on Have message encoding in the BitTorrent file sharing process, first capture the normal data and the data to be tested, and extract the normal data and the data to be tested respectively. The three characteristics of information entropy, ε similarity and variance, using normal data as training data, and testing data as testing data, input Bayesian classifier (wherein the normal data and testing data are processed in no particular order); the specific process as follows:
[0038] Step 1: Set up the data capturer, use the data capturer to capture normal data, and filter out the Have messages.
[0039] Step 2: Set up the data processor, use the data processor to extract the load in each normal data Have message (the load in the message is a positive integer, and it shows a rising trend), and calculate the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com