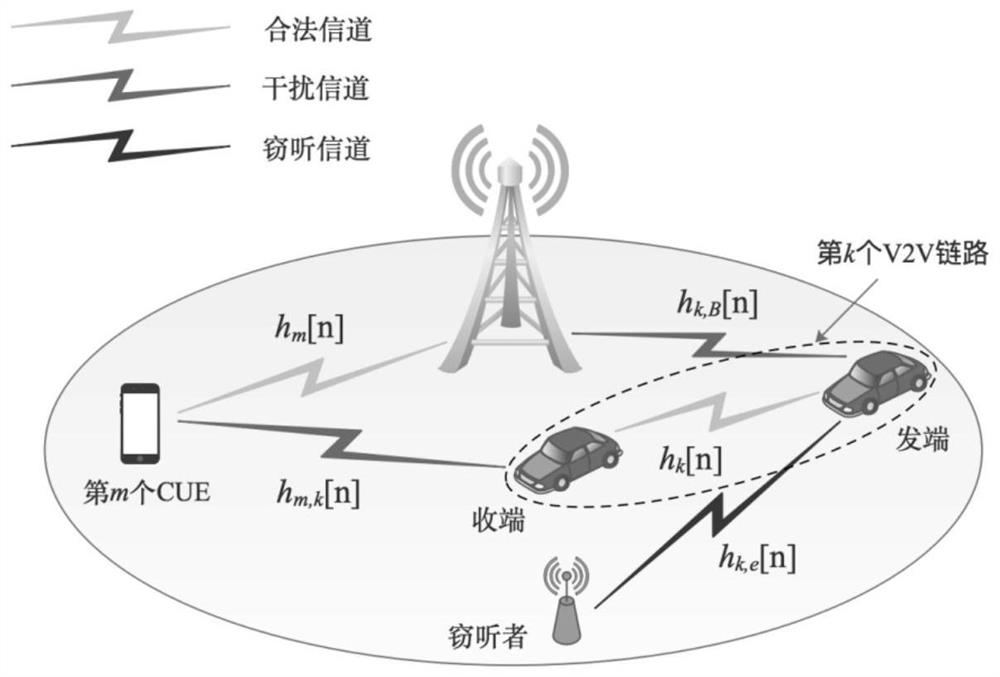
A physical layer security method and system based on resource allocation in v2v communication
A technology of physical layer security and resource allocation, applied in the field of physical layer security, can solve problems such as unoptimized confidentiality capacity and impact on system confidentiality performance, and achieve the effect of improving confidentiality capacity and ensuring security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0105] Example 1: This implementation mode is applied to scenario 1:
[0106] Scenario 1: Eve eavesdrops on all VUEs in the cellular network,
[0107] In scenario 1, when Eve eavesdrops on the confidential information of all VUEs in the network, the purpose of this embodiment is to maximize the sum confidentiality capacity of all VUEs, and the confidentiality capacity optimization problem is:
[0108]
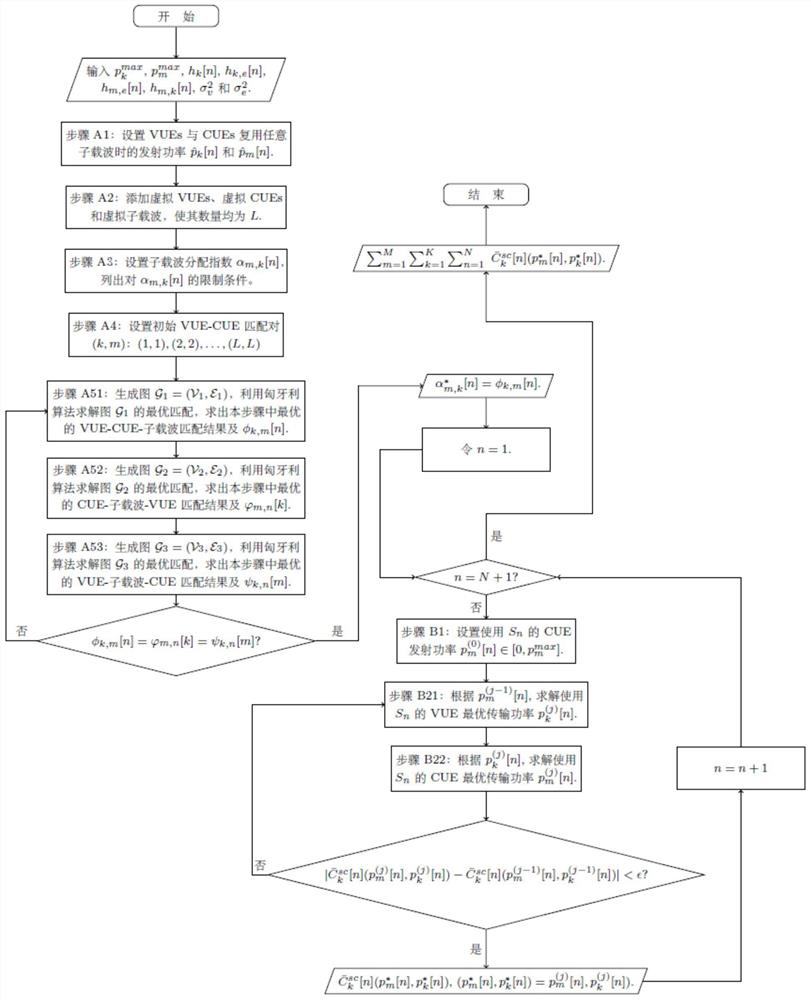
[0109] The flow chart of this embodiment to solve the optimization problem is as follows figure 2 shown.
[0110] Aiming at the issue of subcarrier allocation when VUE and CUE multiplex subcarriers, step A of this embodiment provides an iterative method for subcarrier allocation based on 3D matching when VUE and CUE multiplex subcarriers, including:
[0111] Step A1: Set the transmission power when any VUE and CUE multiplex any subcarrier, the method includes:
[0112] for any U k and R m , in order to ensure the fairness among users, use the user's channel power gain ...
Embodiment 2
[0189] Embodiment 2: This embodiment is applied to scenario 2:
[0190] Scenario 2: Eve eavesdrops on some VUEs in the cellular network,
[0191] In the second scenario, Eve only eavesdrops on the secret information of some VUEs in the cellular network. At this time, the purpose of the present invention is to maximize the sum of the secret capacity of the eavesdropped VUEs and the channel capacity of the VUEs not eavesdropped. Then the optimization objective function can be expressed as:
[0192]
[0193] Algorithm flow chart such as Figure 6 shown.
[0194] Aiming at the problem of subcarrier allocation when VUE and CUE multiplex subcarriers, step A of this embodiment provides an iterative method for subcarrier allocation based on 3D matching when VUE and CUE multiplex subcarriers, which is similar to the subcarrier allocation method in scenario 1. same, including:
[0195] Step A1:
[0196] Set U within cellular coverage k and R m use S n The transmit power whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com