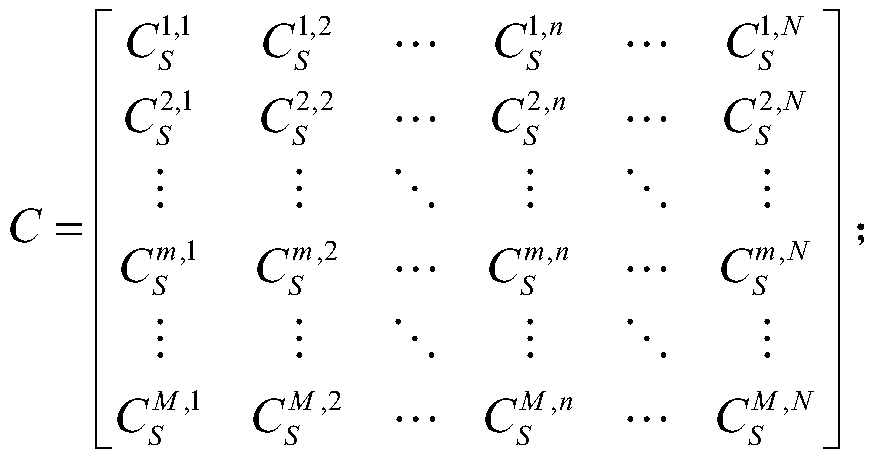
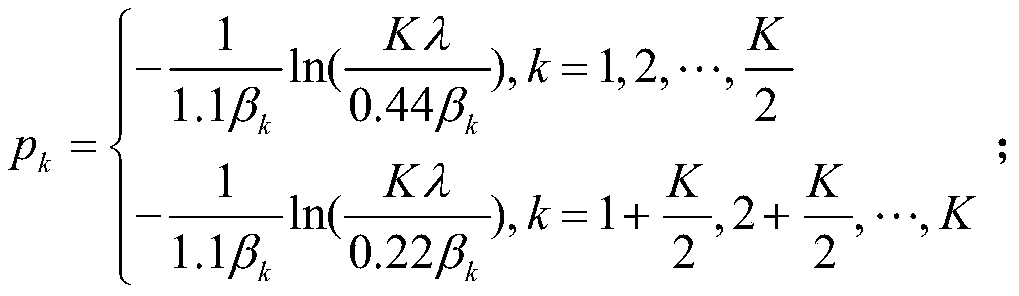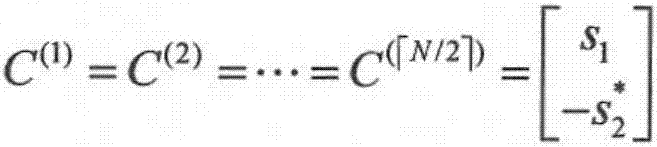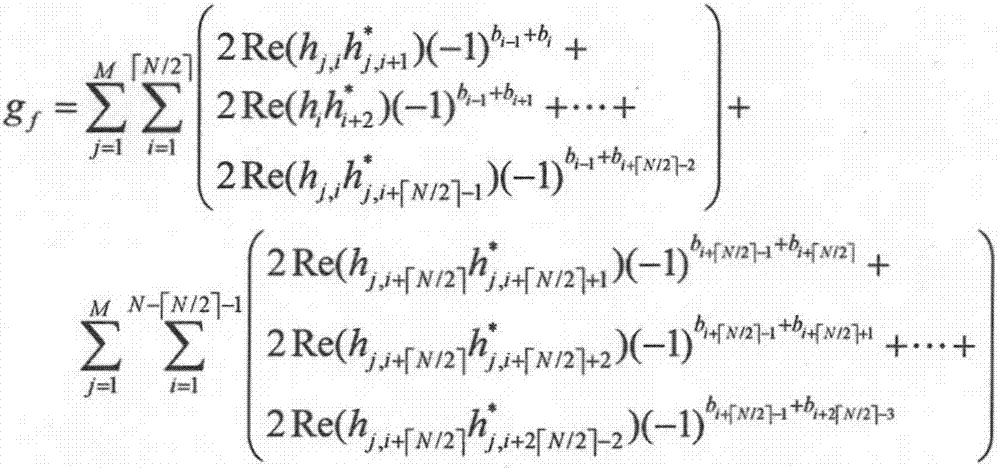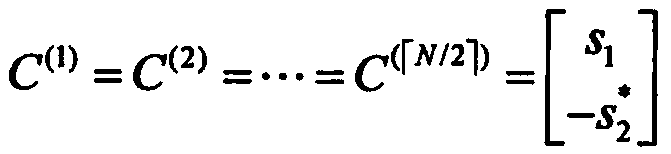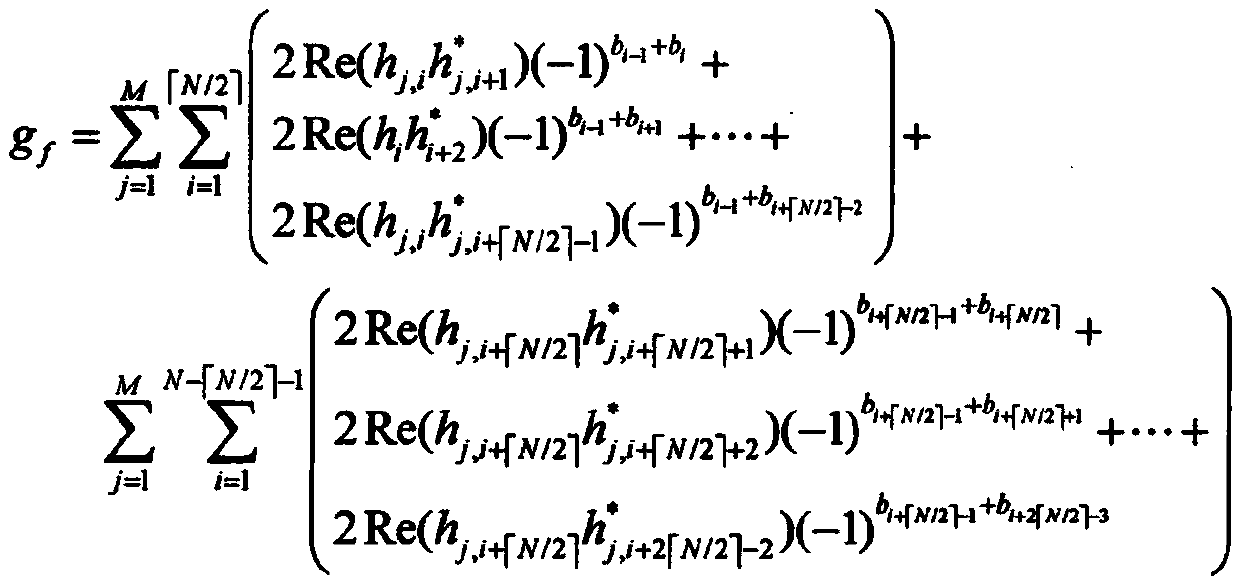Patents
Literature
42results about How to "Increase confidentiality capacity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
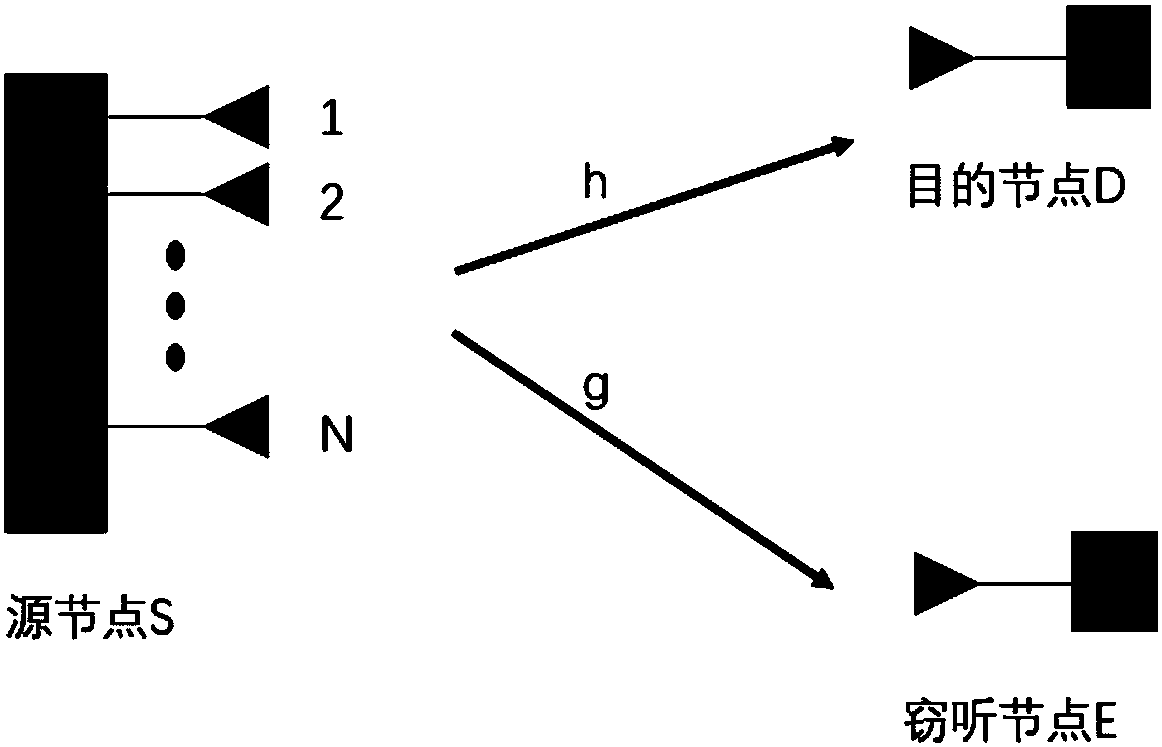
Multi-relay physical layer safety method based on known eavesdropping end channel information
InactiveCN104540124AIncrease freedomMaximize safe capacitySecurity arrangementHigh level techniquesInformation transmissionPhysical layer
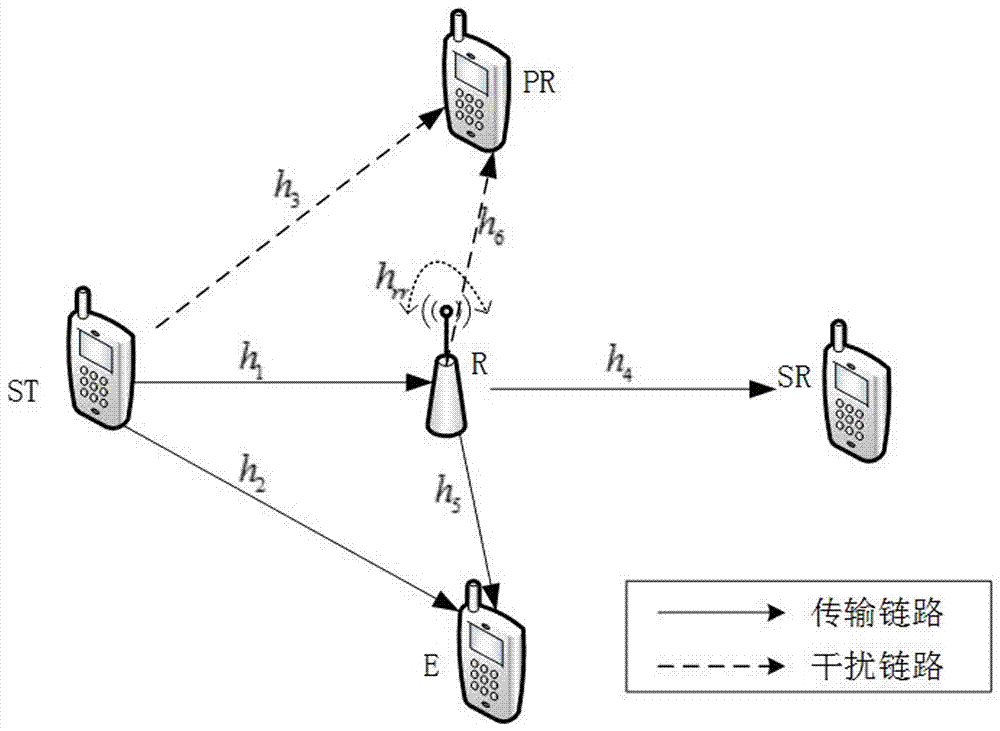
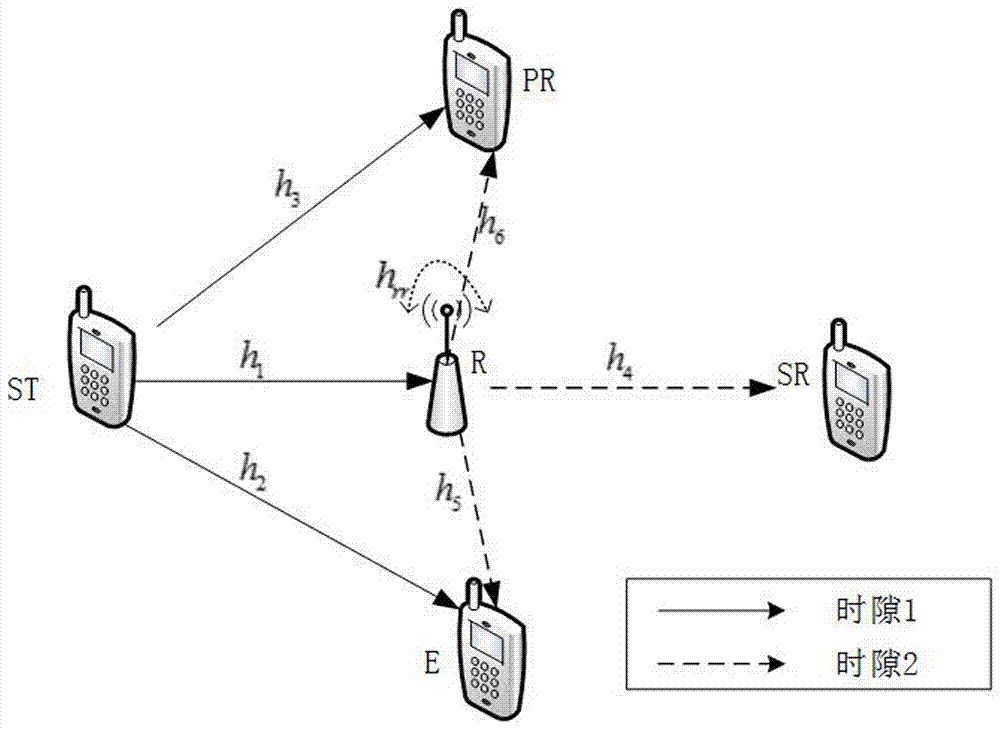
The invention discloses a multi-relay physical layer safety method based on known eavesdropping end channel information to achieve safety communication of a physical layer. Based on known eavesdropping end channel information, a relay group is divided into a relay forwarding group part and a relay interference group part, effectiveness and safe transmission of information are guaranteed for a first information transmission time slot by means of the beam forming technology and the artificial interference technology, and information is effectively prevented from being received by an eavesdropping end in a second time slot by means of the known eavesdropping end channel information and the beam forming technology. On the premise that relay power distribution is considered, the beam forming vector of the relay forwarding group part and the beam forming vector of the relay interference group part are optimized, and the maximum safe capacity of a system is obtained finally.
Owner:SHANDONG UNIV
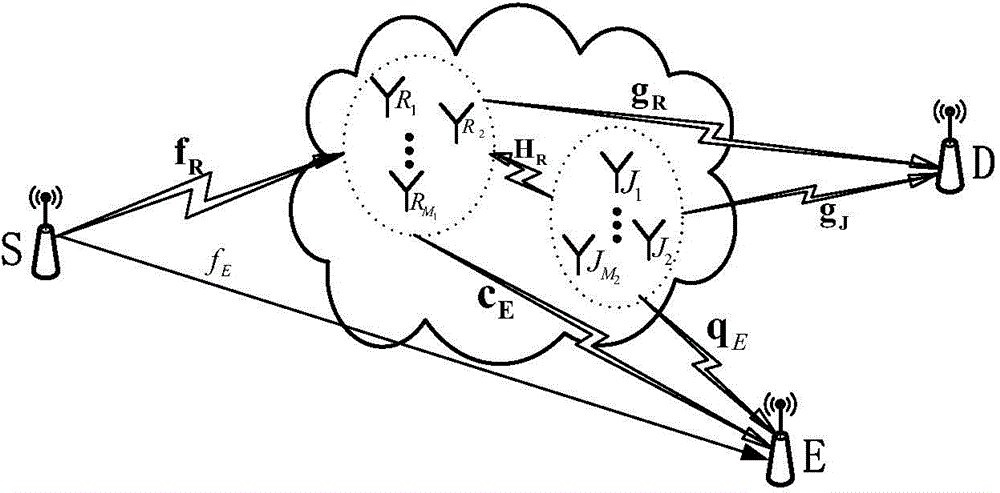
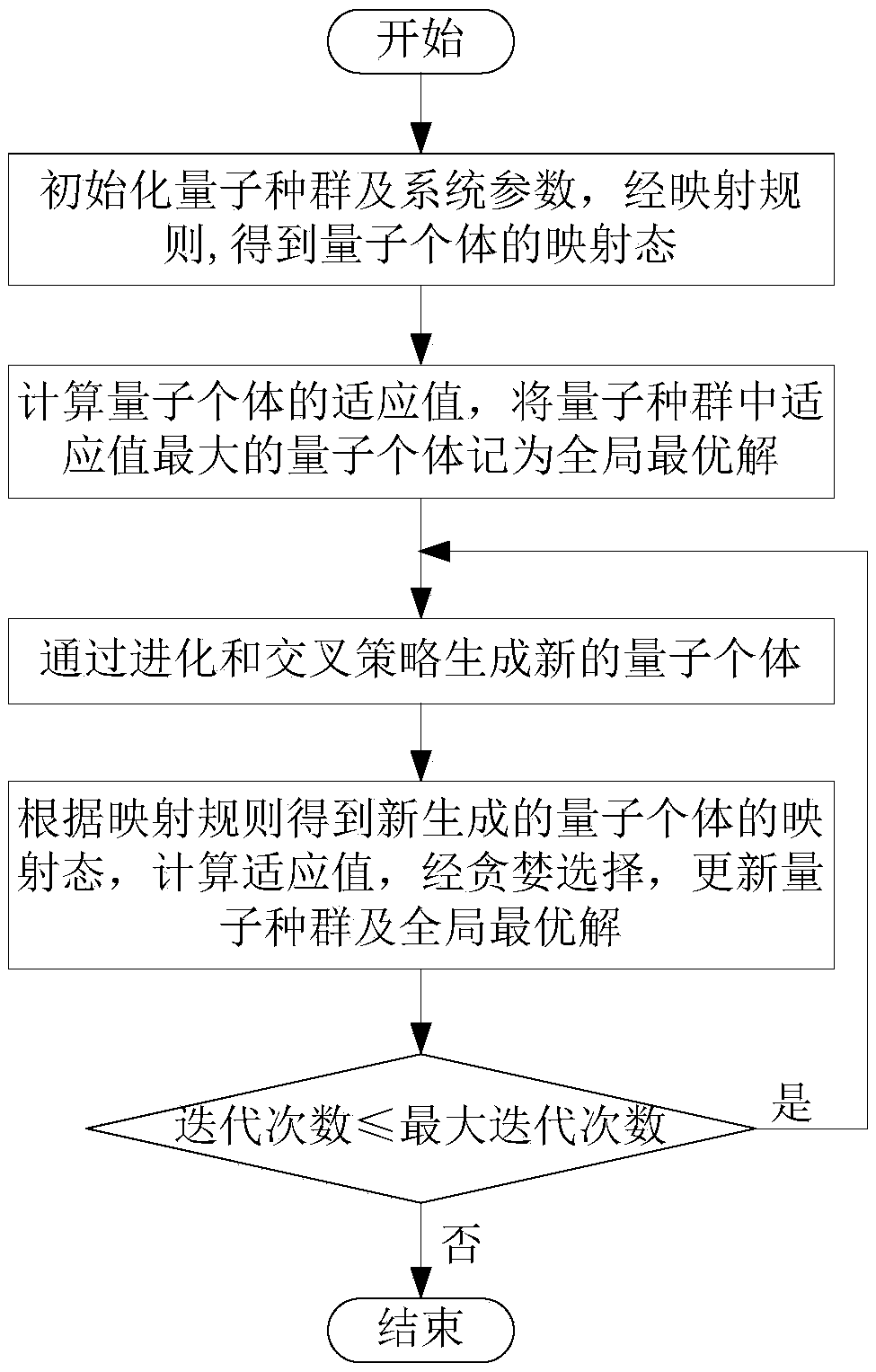
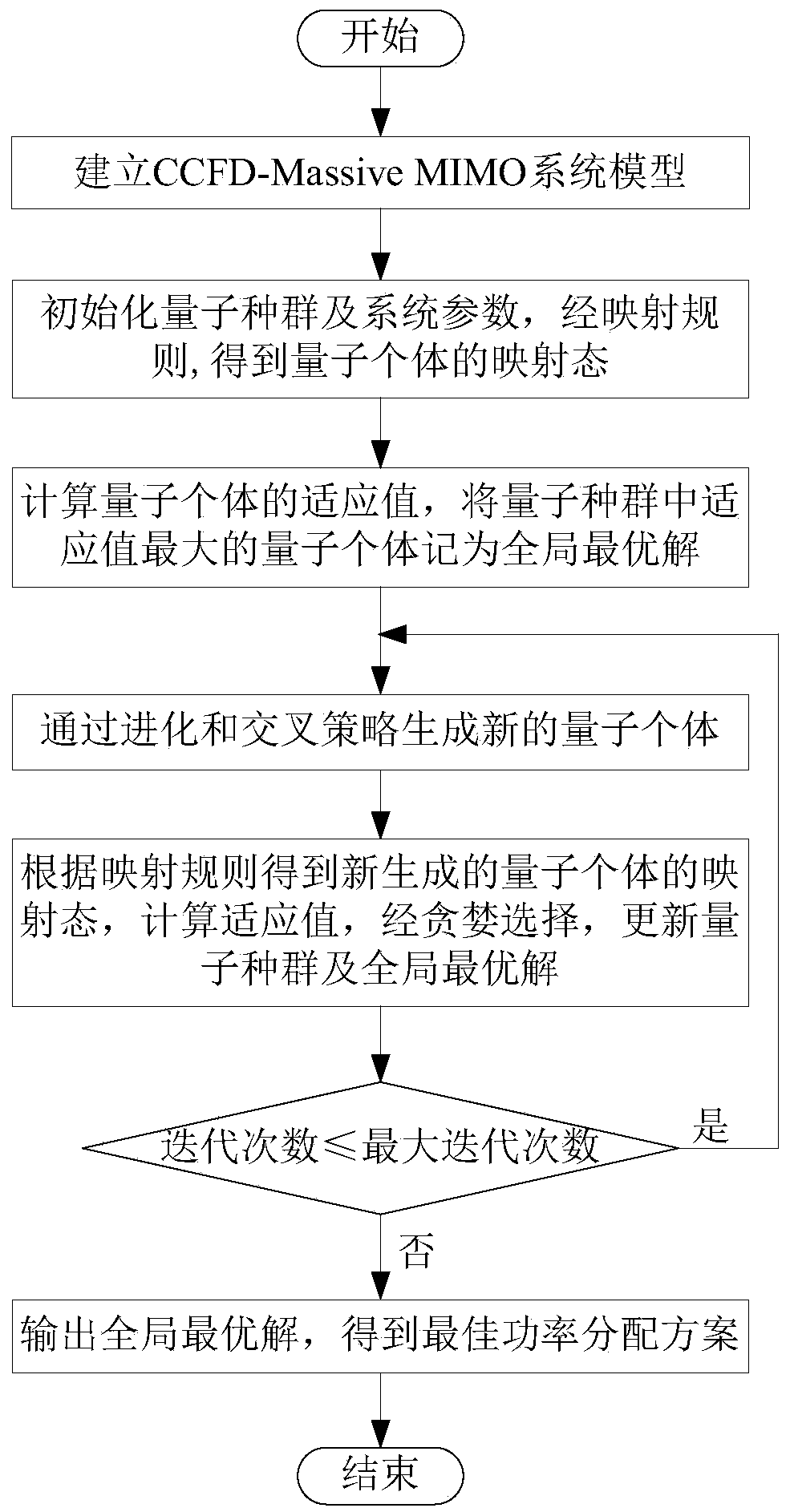
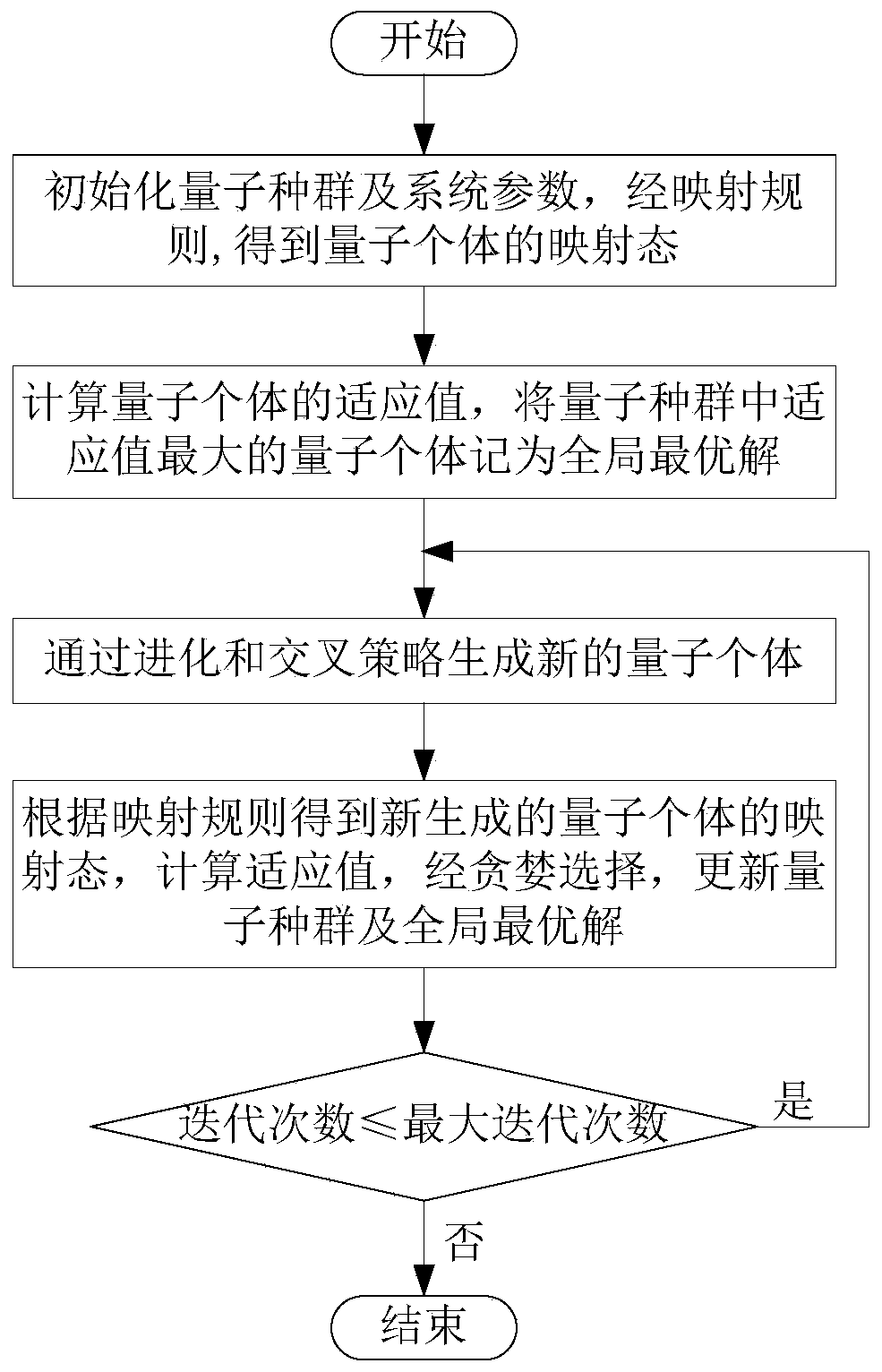
CCFD-Massive MIMO system power distribution method based on quantum backtracking search optimization
ActiveCN108880734AImprove spectrum utilizationImprove confidentialitySpatial transmit diversitySecret communicationSelf interferenceFrequency spectrum
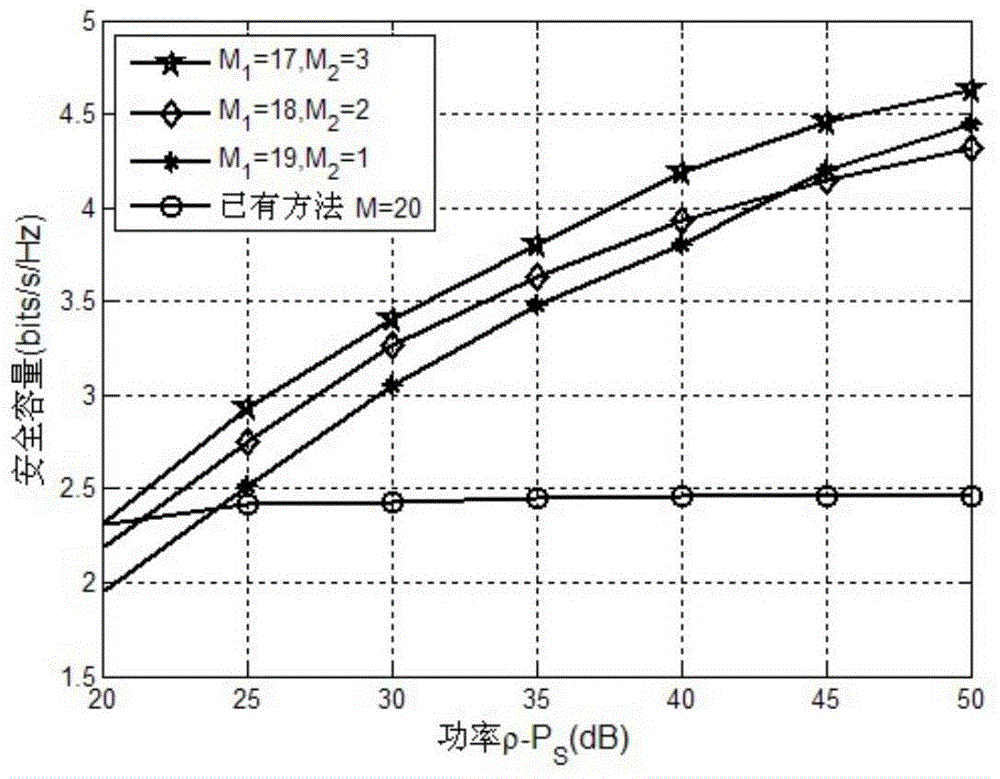
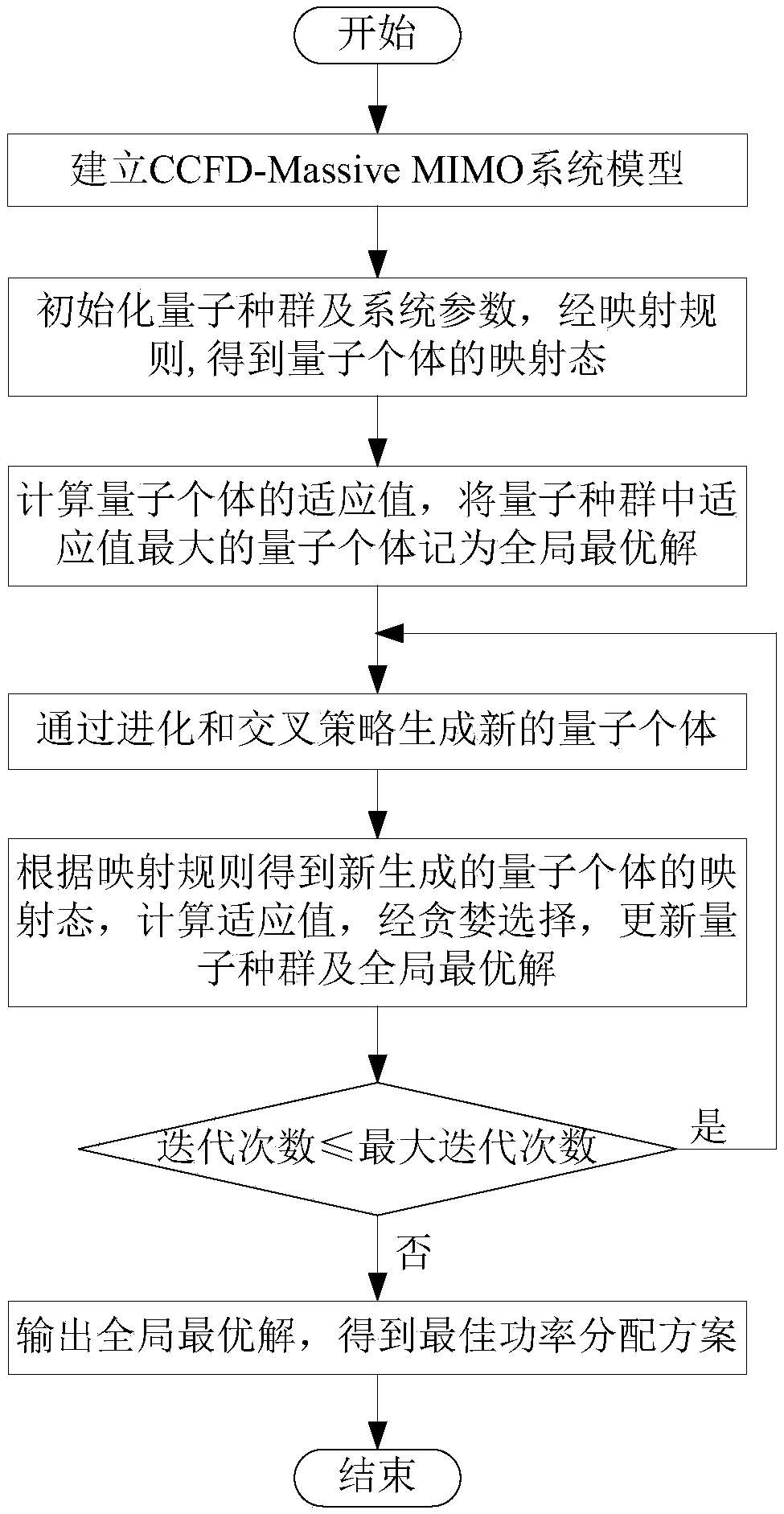
The invention provides a CCFD-Massive MIMO system power distribution method based on quantum backtracking search optimization. The CCFD-Massive MIMO system power distribution method based on quantum backtracking search optimization comprises the steps of: establishing a system model; initializing a quantum population and system parameters, so that mapping modes of quantum individuals are obtainedthrough a mapping rule; calculating adaptive values of the quantum individuals, and taking the quantum individual, the adaptive value of which is the maximum in the quantum population, as the globallyoptimal solution; generating new quantum individuals through evolution and crossover strategies; obtaining mapping modes of the new quantum individuals according to the mapping rule, calculating adaptive values, and updating the quantum population and the globally optimal solution through greedy selection; if the iteration time is less than the pre-set maximum iteration time, returning to the fourth step; and otherwise, ending iteration, and outputting the globally optimal solution, so that an optimal power distribution scheme is obtained. According to the CCFD-Massive MIMO system power distribution method based on quantum backtracking search optimization provided by the invention, the spectrum utilization rate is effectively increased; self-interference and mutual interference of base stations and users are sufficiently considered; the secrecy capacity of a system is increased to a great extent; and a new solution is provided for the power distribution problem of a complex system.
Owner:HARBIN ENG UNIV
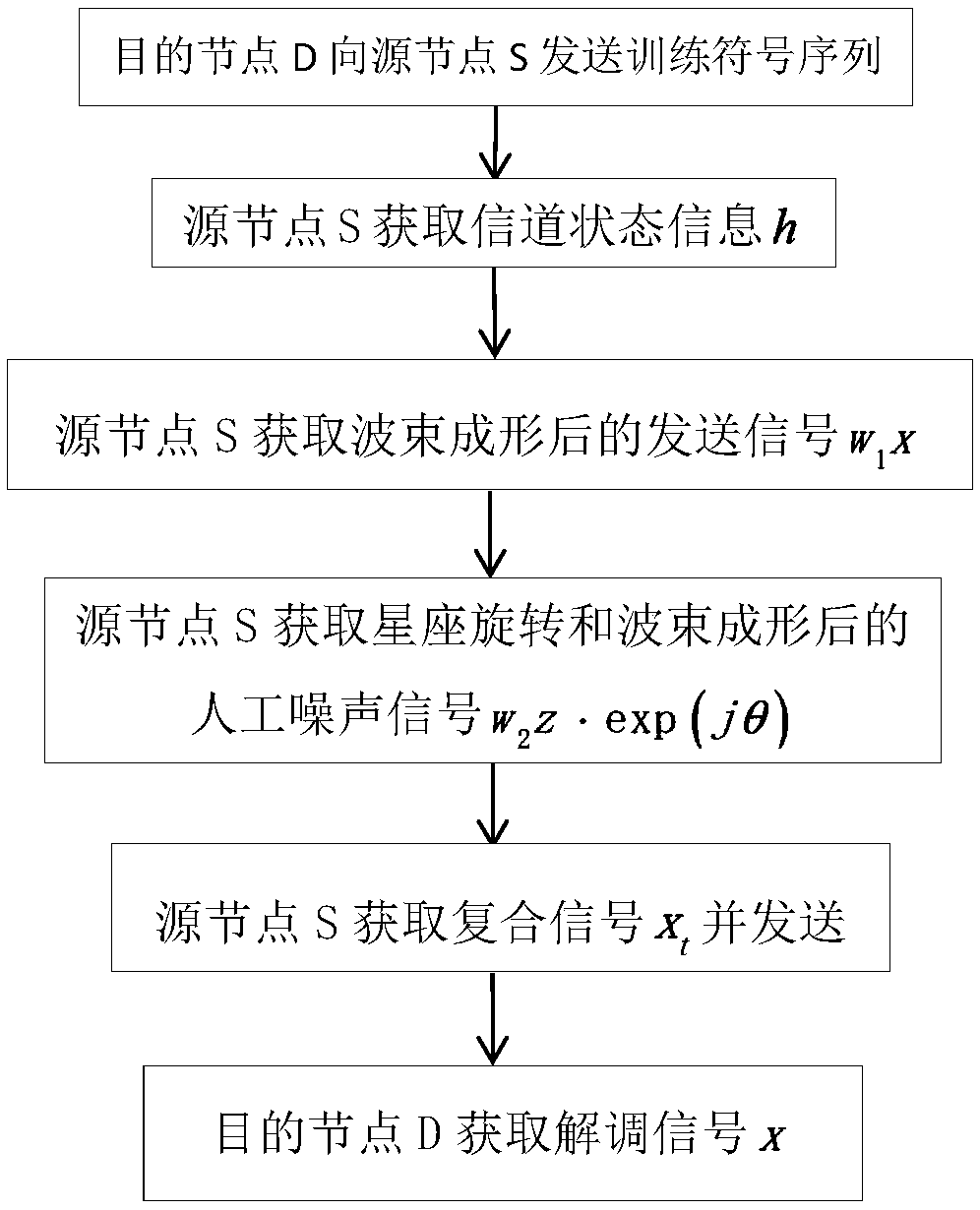
Physical layer safety transmission method of manual noise based on constellation rotation
ActiveCN108366026AImprove signal-to-noise ratioIncrease confidentiality capacitySpatial transmit diversitySecret communicationChannel state informationCommunications system
The invention provides a physical layer safety transmission method of manual noise based on constellation rotation. A technical problem that a wireless communication system is small in secrecy capacity in the prior art is solved. The realization step is as follows: a source node S acquires channel state information to a destination node D, produces a sending signal and performing beamforming on the sending signal, produces manual noise and performs the constellation rotation at the specified angle and the beamforming; the source node S overlaps the sending signal after beamforming and the manual noise after constellation rotation as a compound signal, and sends the compound signal; the destination node D receives the compound signal passing through a channel, and demodulates the same to acquire a demodulated signal. By performing the constellation rotation on the manual noise, the receiving signal signal-to-noise ratio of a sending end can be obviously improved, and the signal-to-noiseratio of an illegal eavesdropping terminal can be maintained at the low value level, thereby improving the secrecy capacity of the wireless communication system, and the security of the wireless communication system is effectively improved.
Owner:XIDIAN UNIV
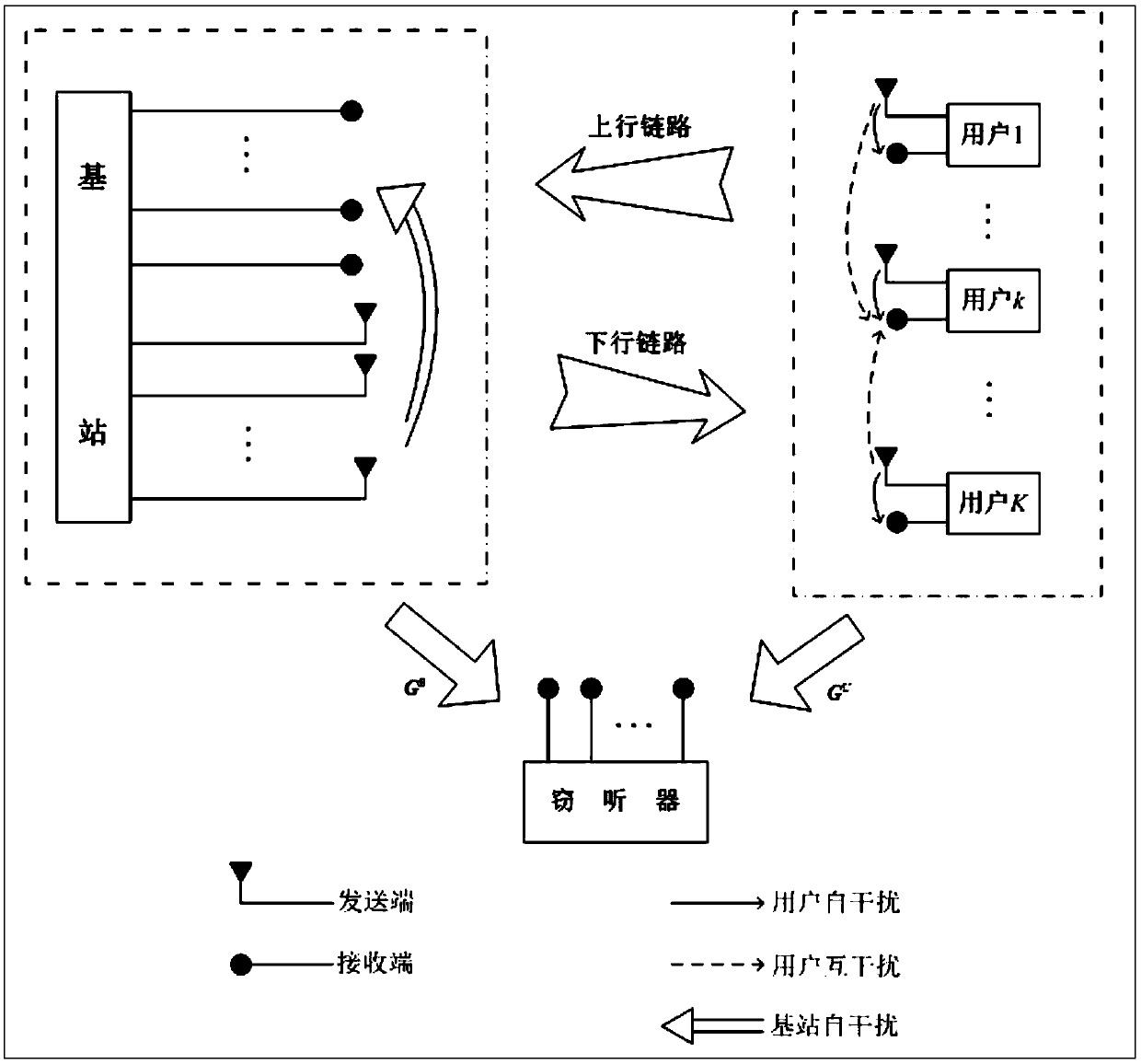
A combined multi-relay selection and time slot resource configuration method for a large-scale MIMO system
ActiveCN109861728ALow interception capabilityImprove energy utilizationRadio transmissionCommunication jammingCommunications systemInformation transmission
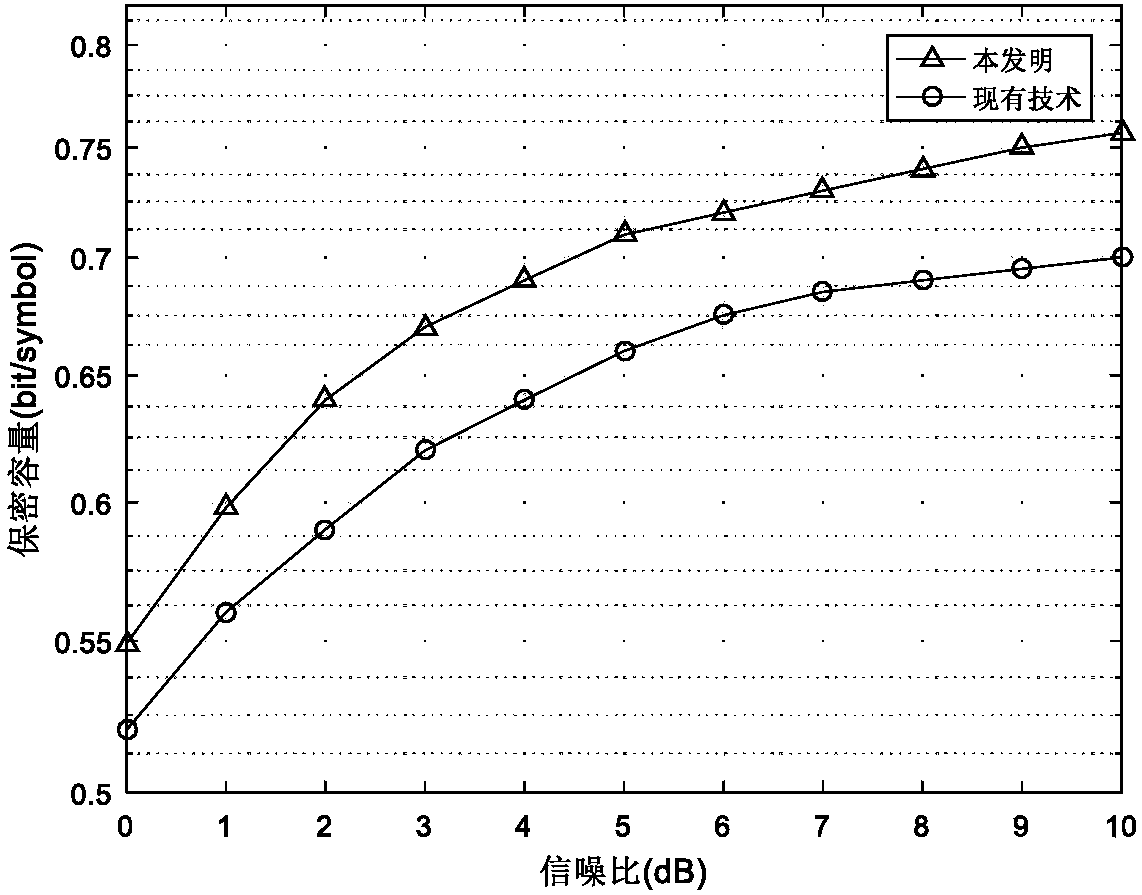
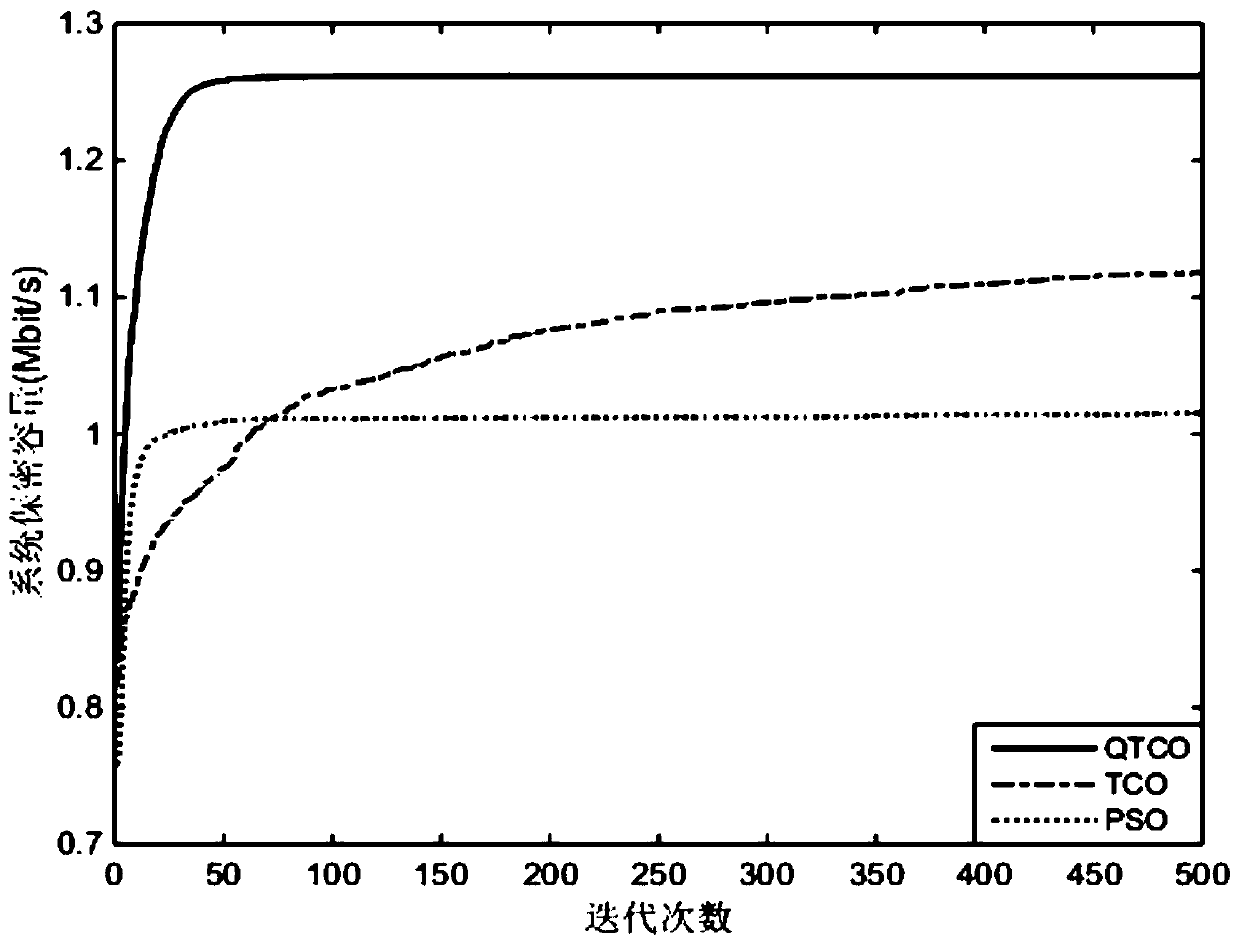
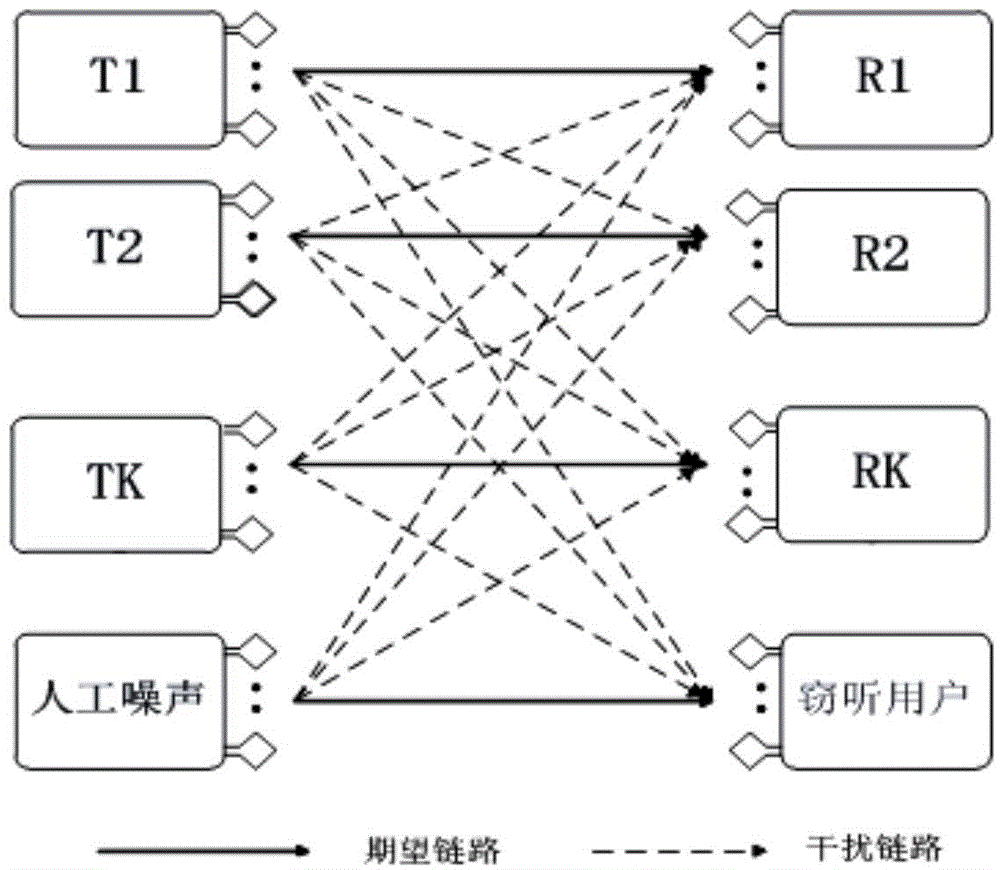
The invention relates to a combined multi-relay selection and time slot resource configuration method for a large-scale MIMO system. According to the method, the advantages of a quantum optimization mechanism and a termite swarm optimization mechanism are combined, the complex hybrid optimization problem of multi-relay selection and time slot resource configuration of the Massive MIMO system is solved by using the quantum termite swarm optimization method, and the method has the advantages of high search speed and high global search capability. According to the invention, a wireless energy collection technology is combined; the energy consumption in the information transmission process of the Massive MIMO cooperative communication system can be obviously reduced; The user terminal and theinterference relay respectively send the interference signal to the stealer to reduce the signal to interference plus noise ratio of the stealer, so that the confidentiality capacity of the Massive MIMO system can be effectively improved, and the safety and the reliability of the communication system are ensured.
Owner:HARBIN ENG UNIV
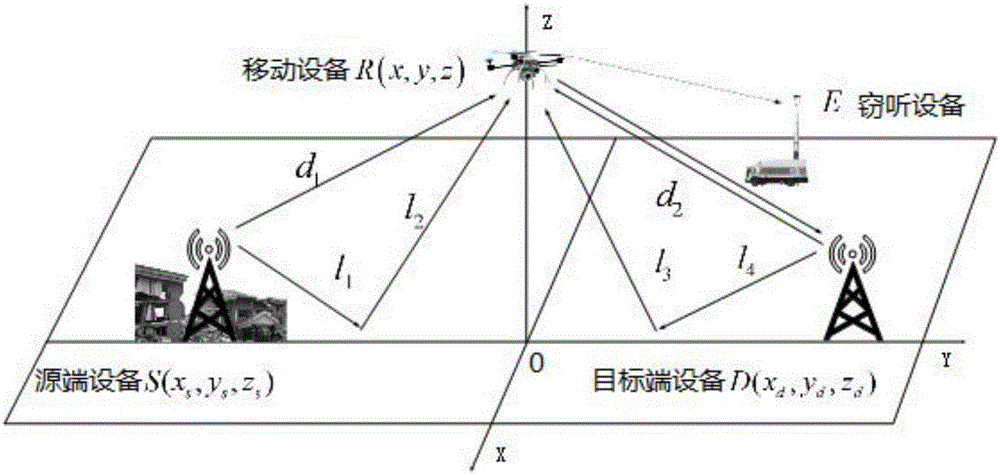
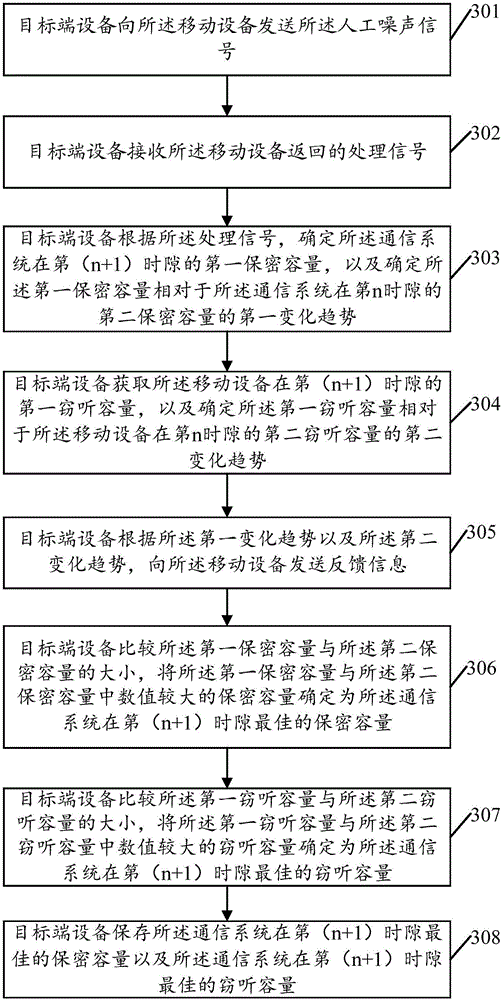
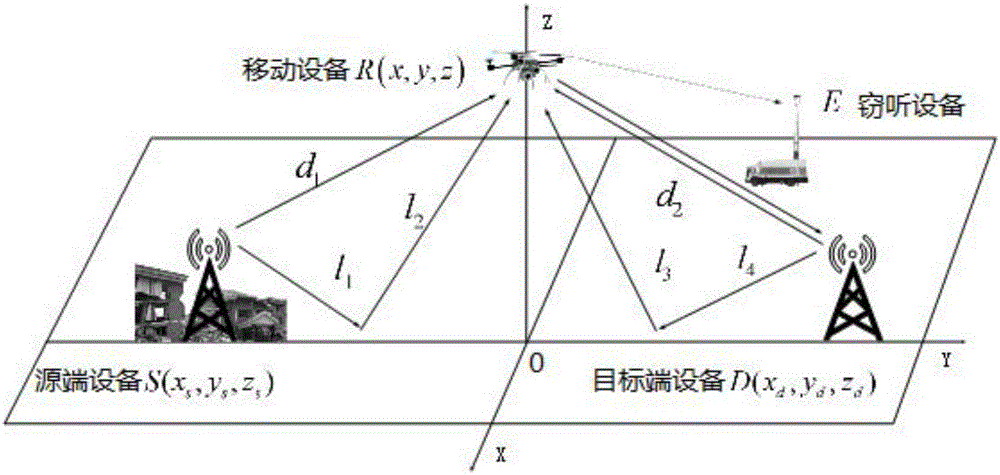
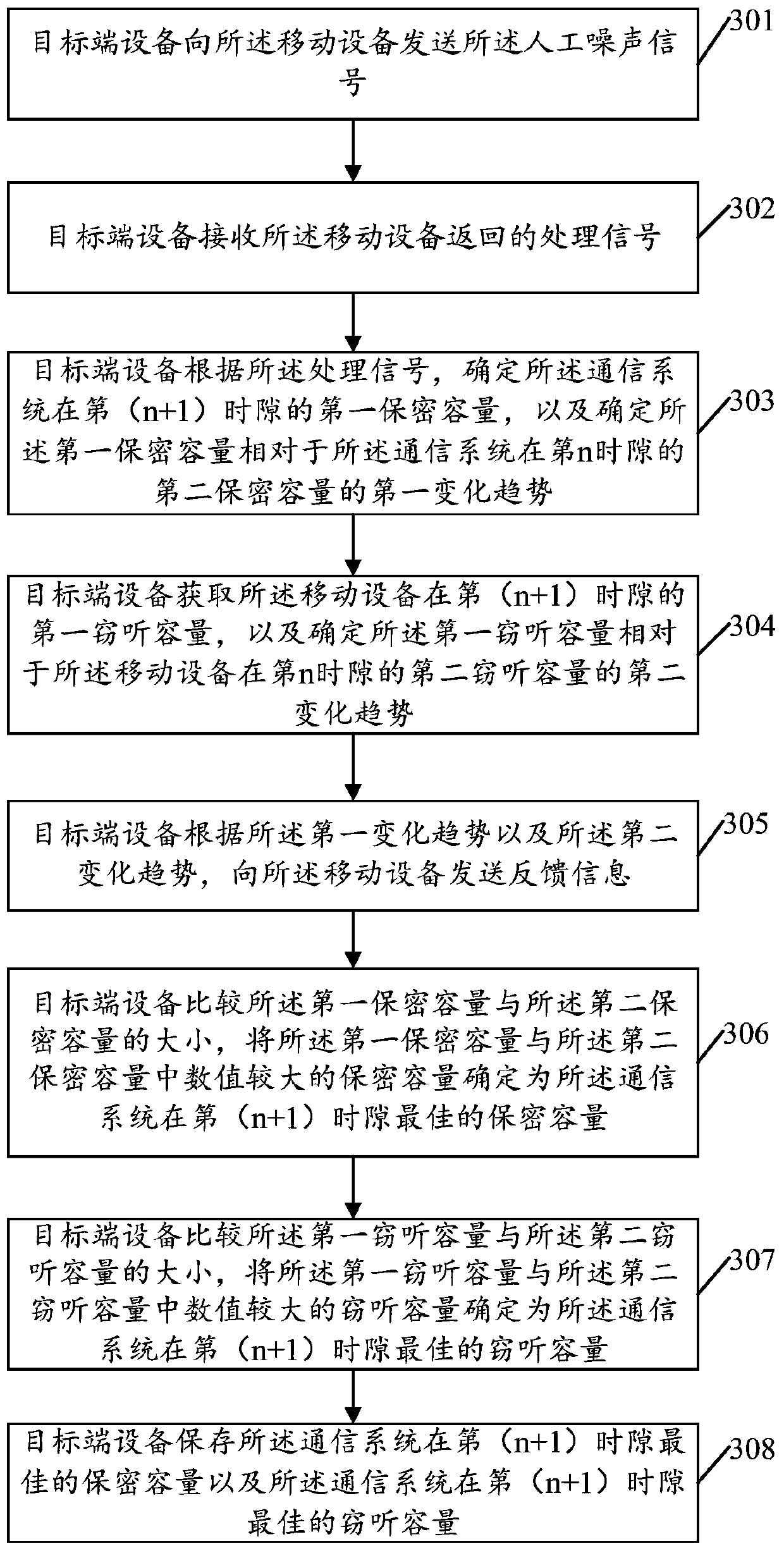
Mobile equipment position control method and device for dynamic noise based on signal-to-interference and noise ratio
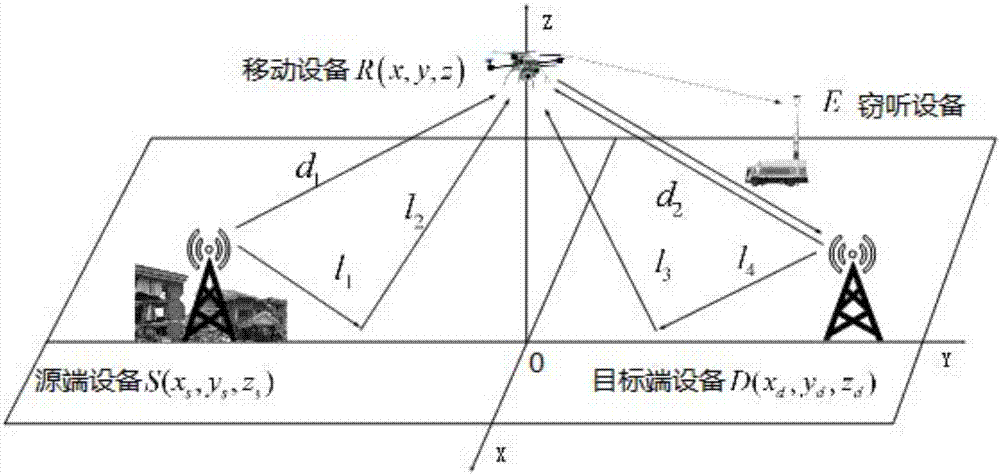
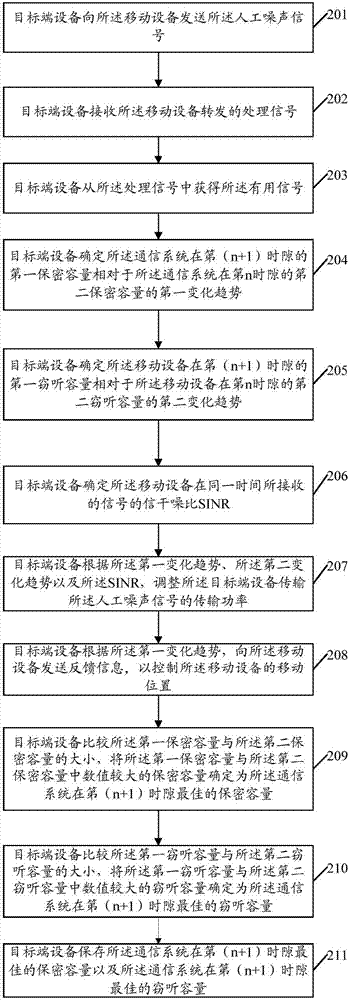
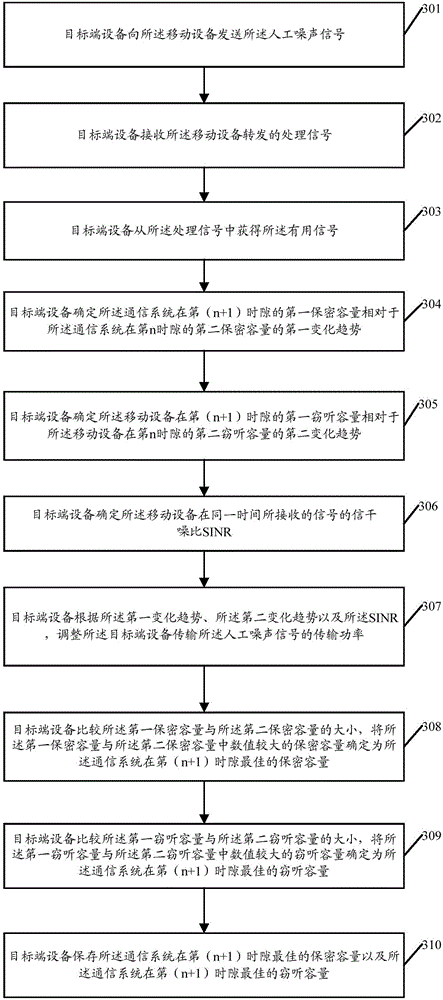
ActiveCN107360544AOptimize confidentiality capacityIncrease confidentiality capacityPower managementCommunication jammingVIT signalsSelf adaptive
The invention provides a mobile equipment position control method and device for dynamic noise based on signal-to-interference and noise ratio, and the method comprises the steps: determining a first change trend of a first secrecy capacity of a communication system in an (n+1)-th time slot relative to a second secrecy capacity of the communication system in an n-th time slot; determining a first change trend of a first interception capacity of mobile equipment in an (n+1)-th time slot relative to a second interception capacity of the mobile equipment in an n-th time slot; determining the SINR of a signal received by the mobile equipment in the same time period; adjusting the transmission power of target end equipment in transmitting a manual noise signal; and transmitting the feedback information to the mobile terminal according to the first change trend. According to the embodiment of the invention, the method can achieve the control of the movement position of the mobile equipment according to the feedback information, achieves the further optimization of the secrecy capacity of the communication system through the adaptive adjustment of the manual noise signal, and enables the safe communication to be carried out continuously.
Owner:SHENZHEN UNIV
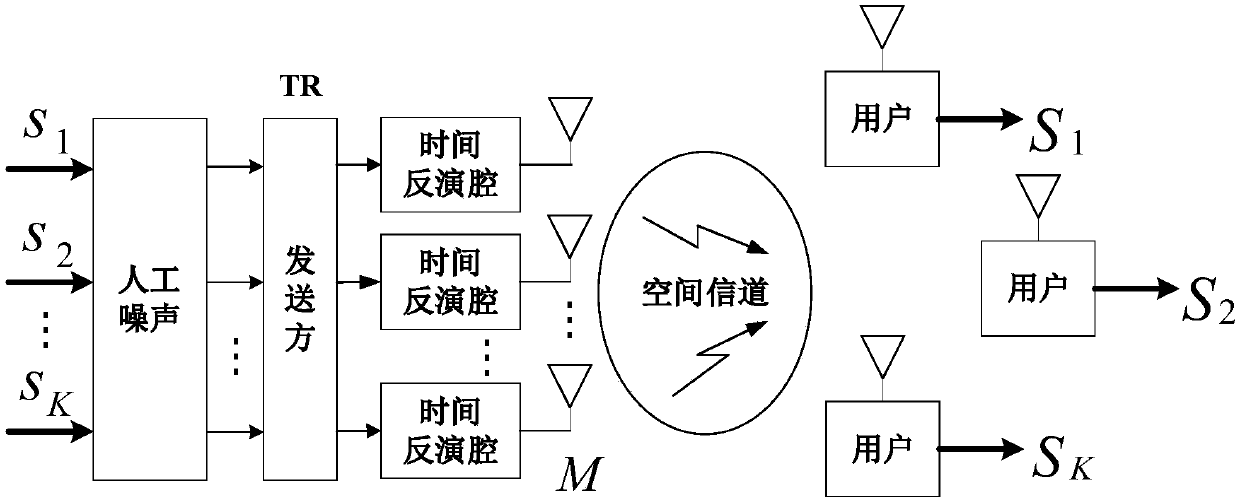
Downlink secure transmission policy based on time reversal technology
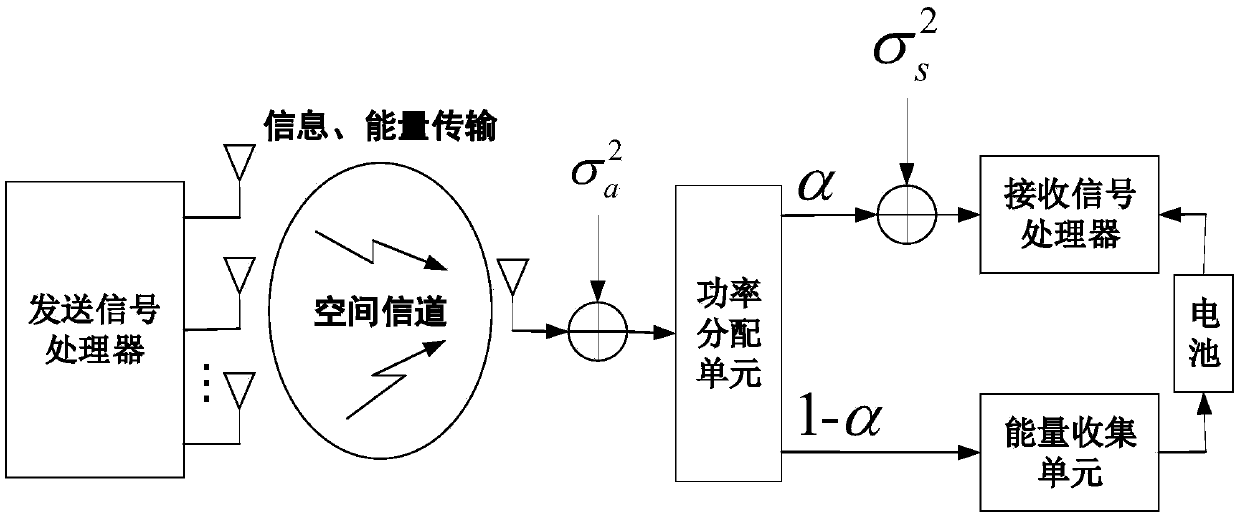
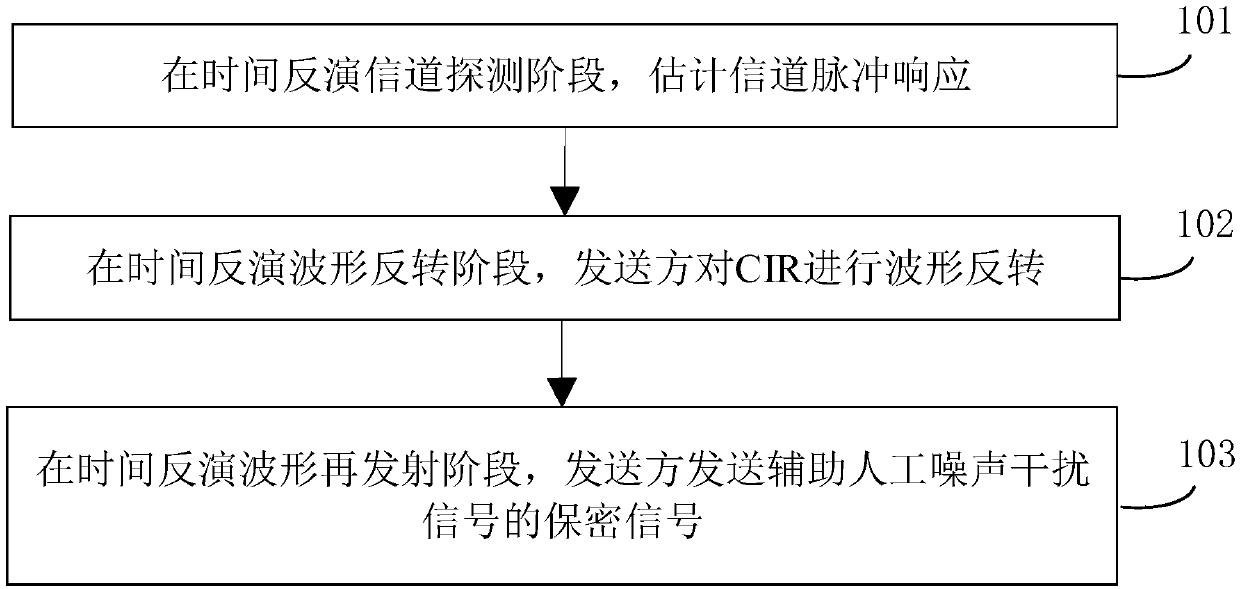
InactiveCN109660553AReduce leakageIncrease confidentiality capacityBaseband system detailsRadio transmissionTransmission policyEnergy transfer
According to a secure transmission policy employing artificial noise, secrecy of a system can be greatly improved, while, energy is additionally consumed, and a life cycle of a whole wireless communication system is likely to be influenced. For a secure communication problem in a multiuser multiple input single output downlink system, the invention discloses a downlink secure transmission policy based on a time reversal technology. The time reversal technology is employed in the multiuser multiple input single output (MISO) downlink system. The secrecy performance of the system is improved through utilization of space-time focusing. The fact that secrecy signals of auxiliary artificial noise interference signals consume the energy additionally is taken into consideration, so an energy consumption problem is effectively solved through importing of an SWIET (simultaneous wireless information and energy transfer) technology, and system security performance is improved. Theoretical analysis and simulation results show that the provide policy is relatively high in secrecy capacity and is relatively low in information leakage quantity.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method for improving MIMO safety capacity based on weighting matrix
InactiveCN104901730AAnd increased capacityConstant tapping capacitySpatial transmit diversityHigh level techniquesSystem matrixDecomposition
The present invention discloses a method for improving MIMO safety capacity based on a weighting matrix. The method includes: (1) adding a weighting matrix Dk at a transmitting terminal to decrease the matrix dimensions of the system matrix such that a zero space is available; (2) calculating a precoding matrix Fk of each user at the transmitting terminal to obtain an equivalent channel matrix DkHkFk, wherein Hk represents the channel matrix of the kth user; (3) performing SVD decomposition of the equivalent channel matrix and water injection power distribution for each user; (4) adding a weighting matrix Wk at a receiving terminal, and calculating sum capacity of each user; and (5) calculating a weighting matrix We and wiretapping capacity at a wiretapping terminal, and calculating the difference between the sum capacity and the wiretapping capacity to obtain confidential capacity. According to the method, only one matrix is required to be added at the receiving end, so that the implementation is easy, and the safety capacity of the user system is greatly increased.
Owner:NANJING UNIV OF POSTS & TELECOMM
Multicast method and device based on physical layer security transmission
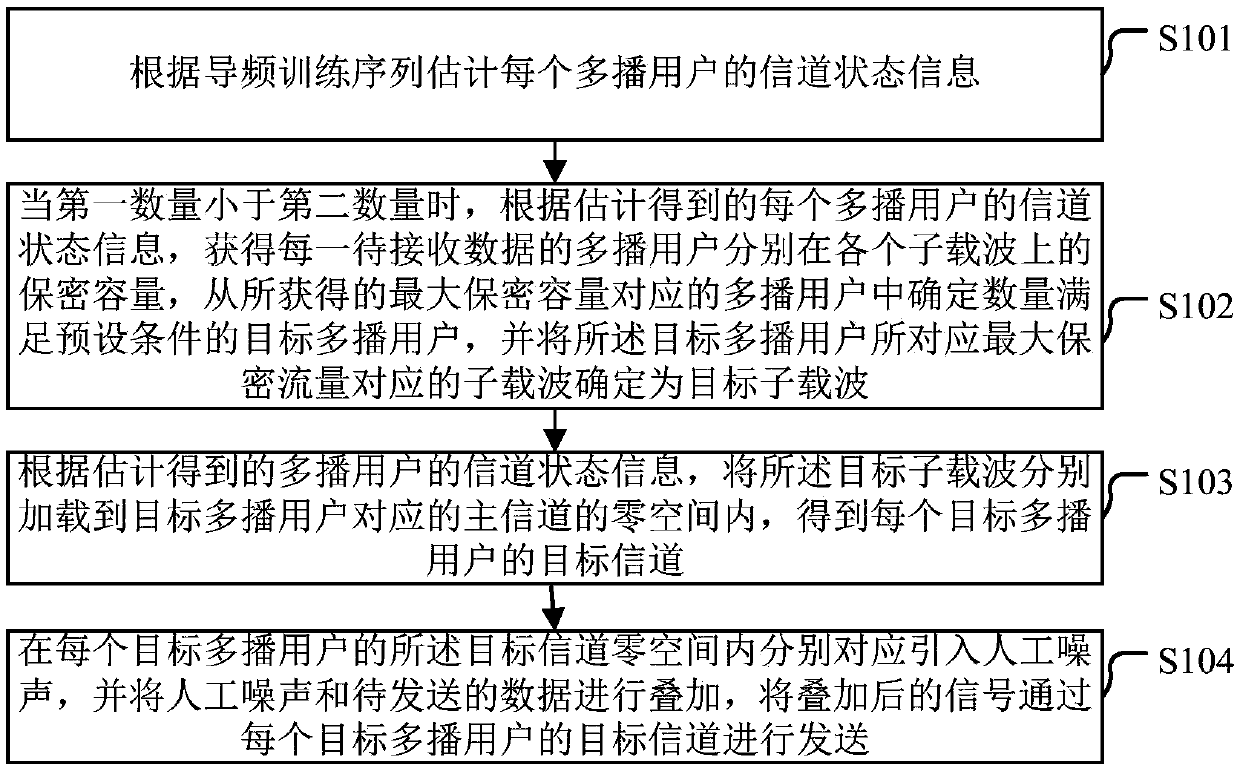
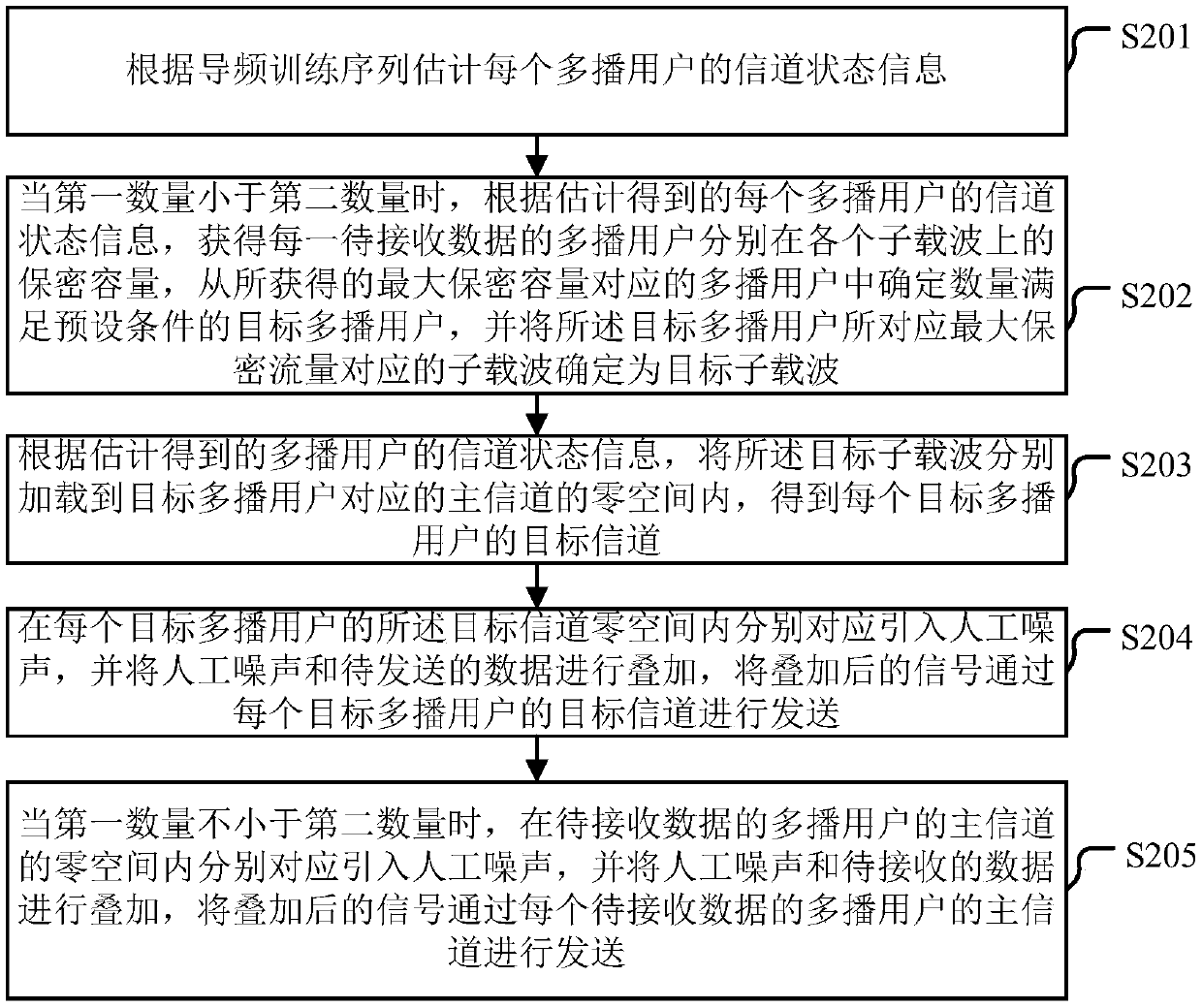
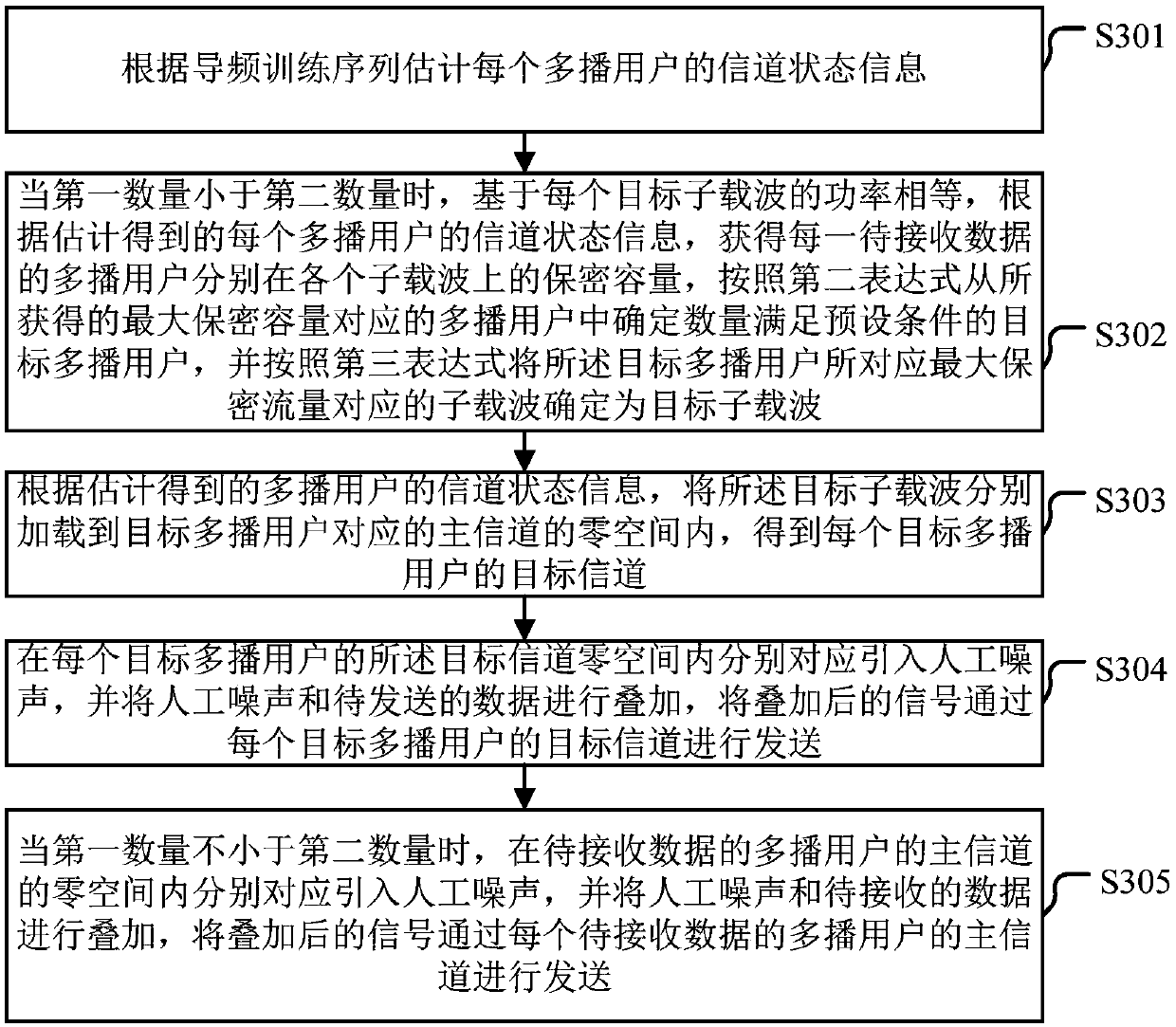
InactiveCN108738133ATransmission is safe and correctIncrease confidentiality capacityBaseband system detailsSecurity arrangementChannel state informationCarrier signal
Embodiments of the invention provide a multicast method and device based on physical layer security transmission. The method comprises the following steps of estimating channel state information of each multicast user according to a pilot frequency training sequence; when the first number is smaller than the second number, acquiring secrecy capacity according to the estimated channel state information, determining a target multicast user from the multicast user corresponding to the acquired maximum secrecy capacity, and determining sub-carriers corresponding to the maximum secrecy capacity astarget sub-carriers; respectively loading the target sub-carriers into a null space of a main channel corresponding to the target multicast user according to the estimated channel state information inorder to obtain a target channel; and correspondingly introducing artificial noise into each zero space, superposing the artificial noise and data to be sent, and sending the superposed signal through the target channel of each target multicast user. According to the scheme provided by the embodiments of the invention, when different secret QoS requirements of each user in a multicast group are ensured, the correctness of the data can be guaranteed.
Owner:CHINA CRIMINAL POLICE UNIV
Mixed duplex transmission method for improving physical layer security in cognitive relay network
ActiveCN107171775AIncrease safety capacity situationDetrimental effects of weakening transmission capacity performanceAllocation timingSecurity arrangementSelf interferencePhysical layer
The invention discloses a mixed duplex transmission method for improving physical layer security in a cognitive relay network. The mixed duplex transmission method comprises the steps of, by a pair of unauthorized users, sharing a frequency band resource with an authorized user in the cognitive relay network with an illegal eavesdropper under the assistance of a cooperative relay and under the interference limitation to a main user; and by the relay, playing a role of confusing the illegal eavesdropper through adding man-made noise while assisting to decode and forward information. One relay transmission frame is divided into two equal time slots during half-duplex transmission. The relay transmission frame is not subjected to time slot division during the full-duplex transmission. When the full-duplex self-interference power is lower than a threshold value, the full-duplex transmission is adopted; otherwise, the half-duplex transmission is adopted. Switching between the half-duplex transmission and full-duplex transmission is realized based on the full-duplex self-interference power, respective advantages of the half-duplex mode and the full-duplex mode are utilized, and the physical layer security of the cognitive relay network is finally improved by increasing the total transmission capacity of the cognitive relay network.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Eavesdropping preventing method and device
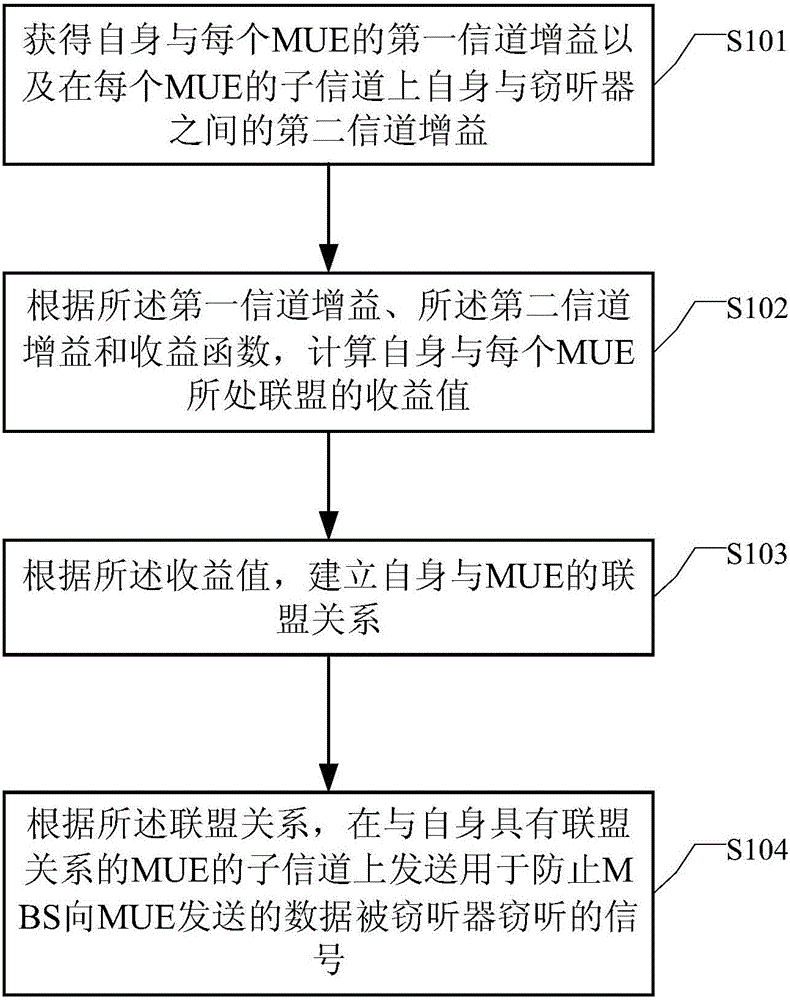
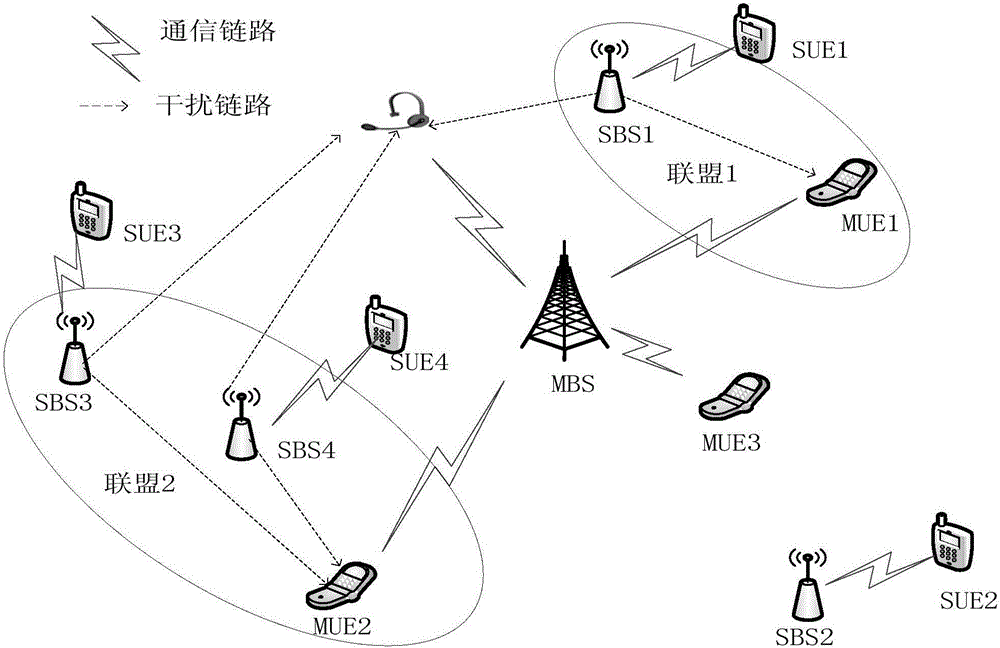
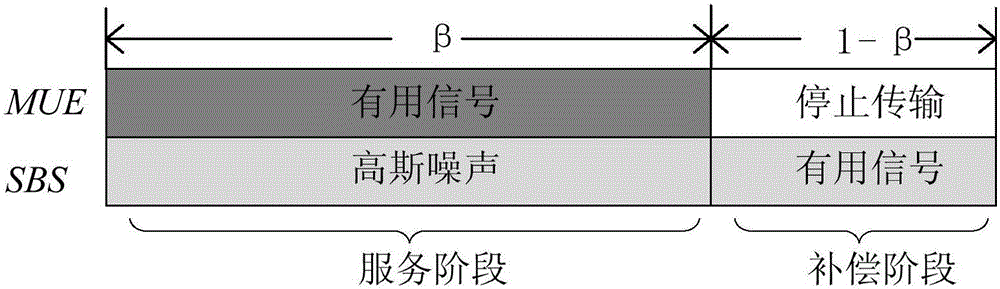
ActiveCN105873037AIncrease confidentiality capacityReduce performance lossSecurity arrangementEngineeringEavesdropping
The embodiment of the invention discloses an eavesdropping preventing method and device. The eavesdropping preventing method and device are applied to an SBS in a heterogeneous cellular network. The method includes the steps that a first channel gain between the device and each piece of MUE and a second channel gain between the device and an interceptor on a subchannel of each piece of MUE are acquired; according to the first channel gains, the second channel gains and a revenue function, gain values of allies where the device and each piece of MUE are located are calculated; according to the gain values, the ally relationship between the device and each piece of MUE is established; according to the ally relationships, signals for preventing data sent by an MBS to the MUE from being eavesdropped by the interceptor are sent on the subchannels of the MUE with the ally relationships with the device, wherein the signals are part of effective information sent by the SBS to SUE. By means of the method and device, the data sent by the MBS to the MUE is prevented from being eavesdropped by the interceptor, and the performance losses of the SBS are reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Physical layer security resource allocation method in ICV network
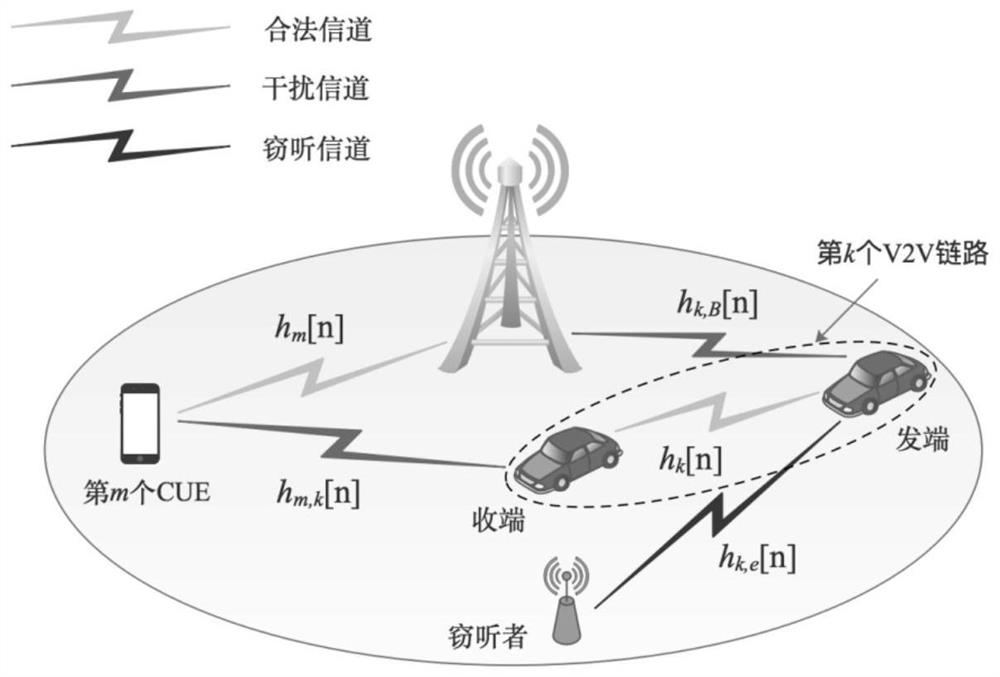
ActiveCN112153744AIncrease confidentiality capacityRealize automatic spectrum accessParticular environment based servicesVehicle-to-vehicle communicationInterference (communication)Transmitted power
Owner:HARBIN INST OF TECH
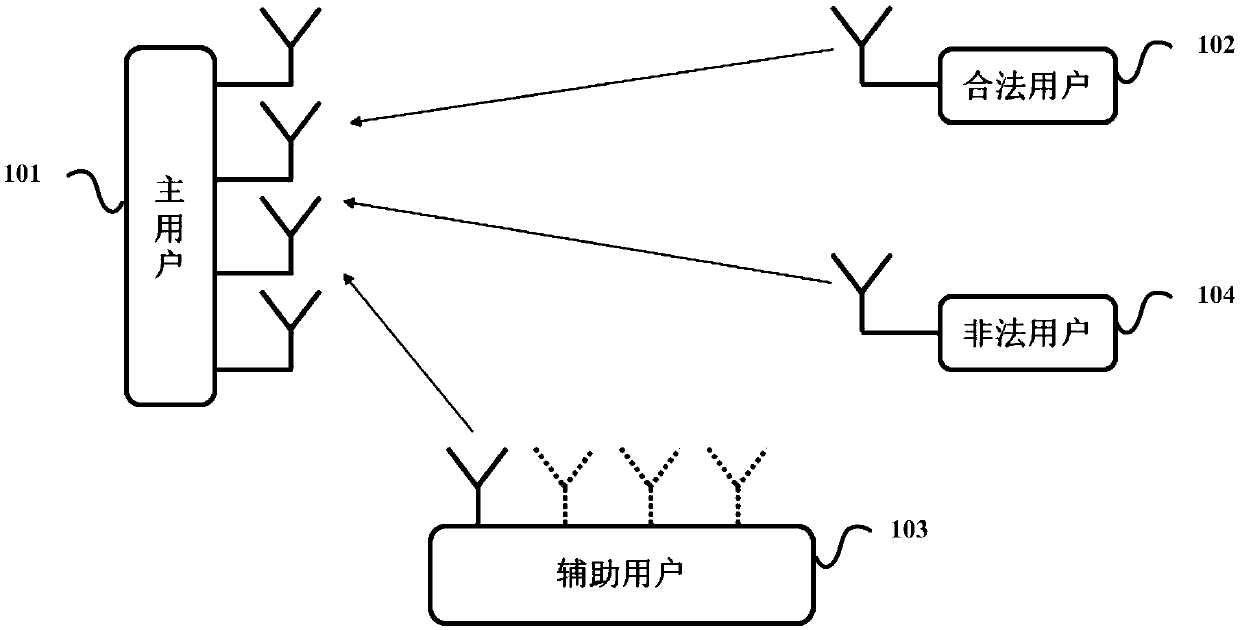
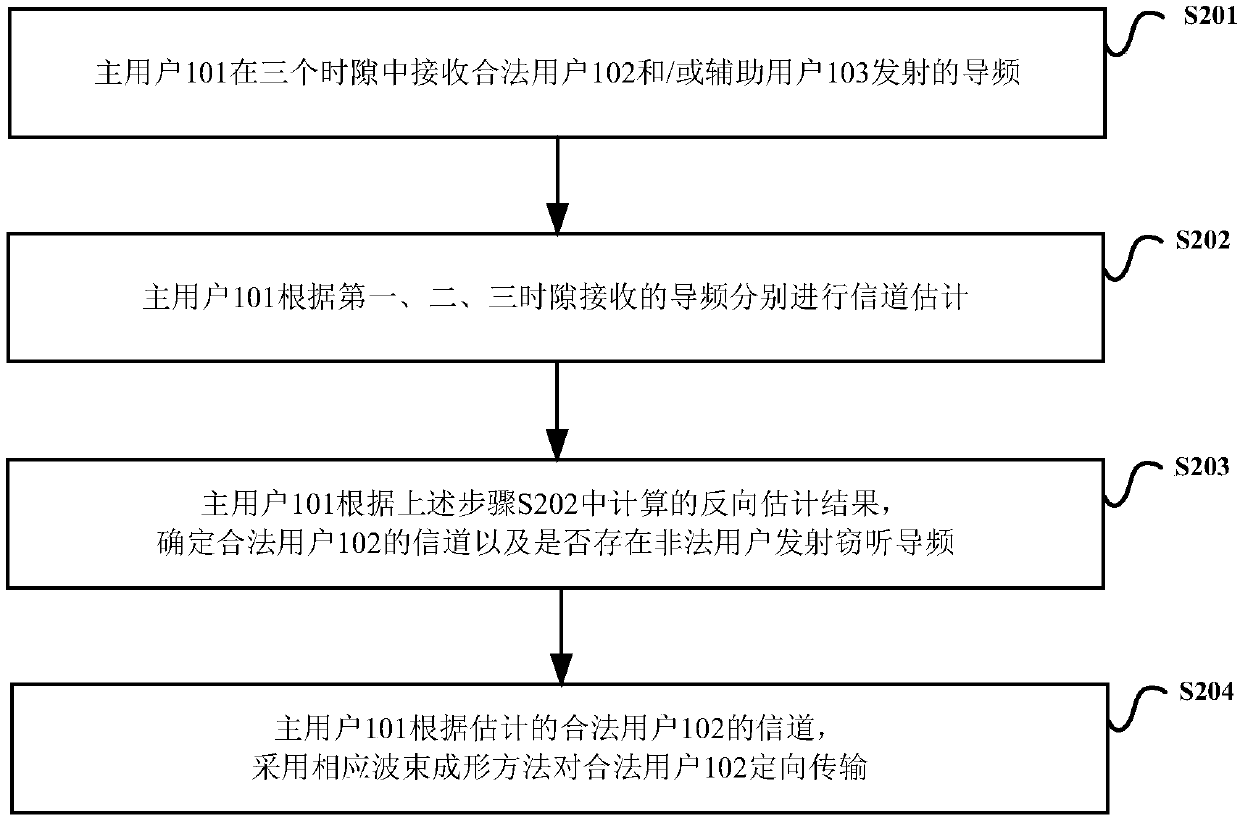
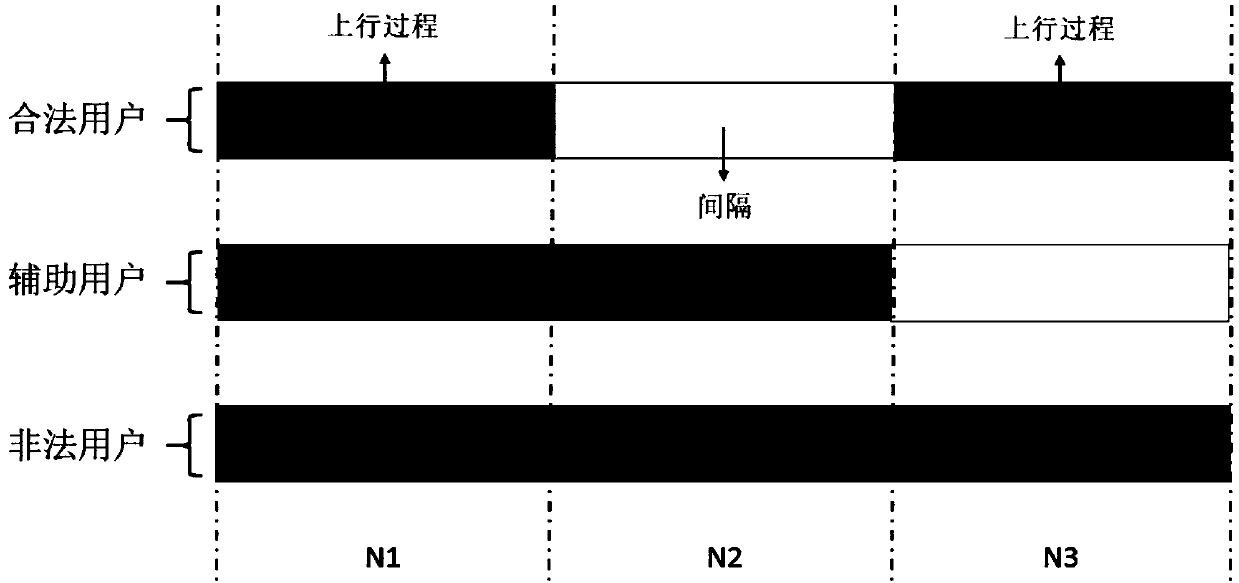
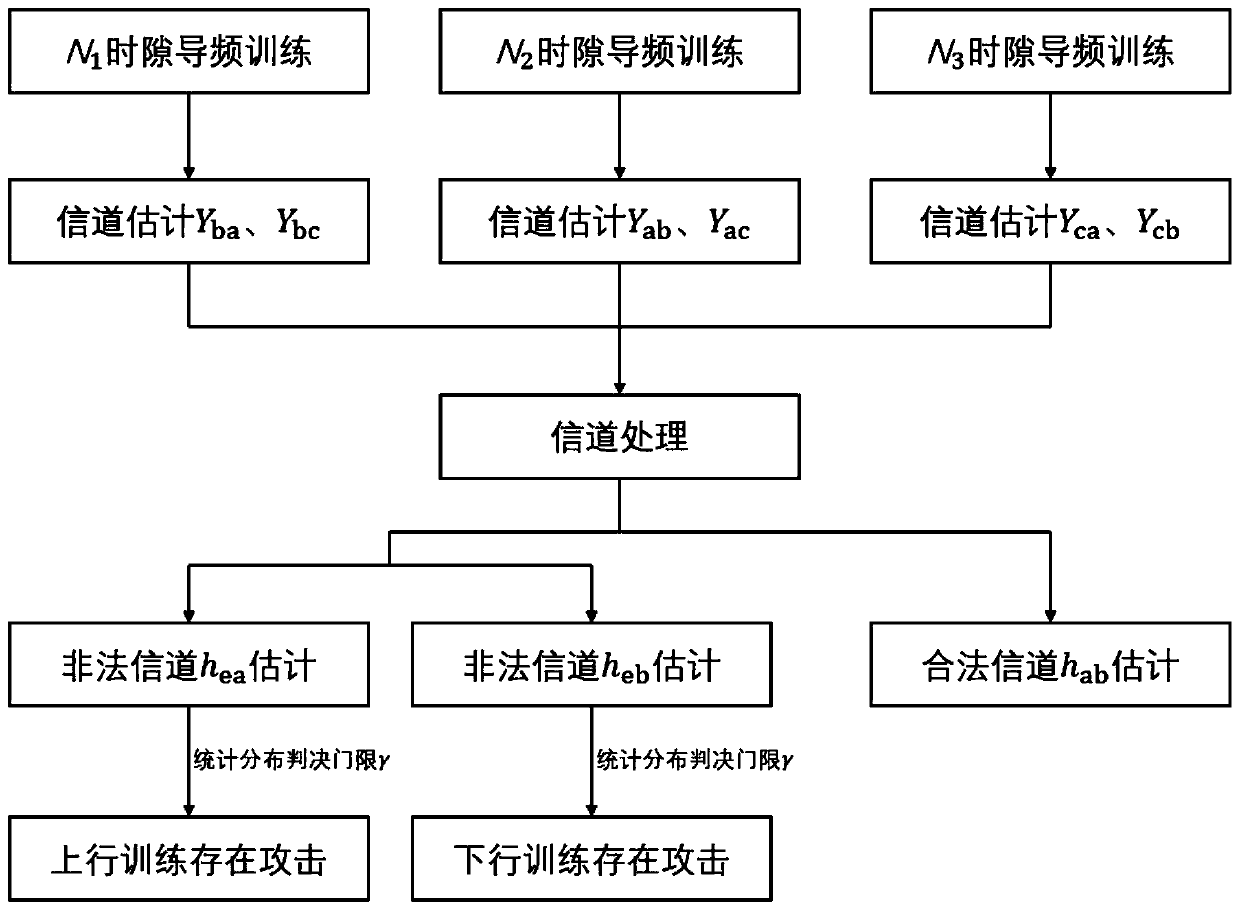
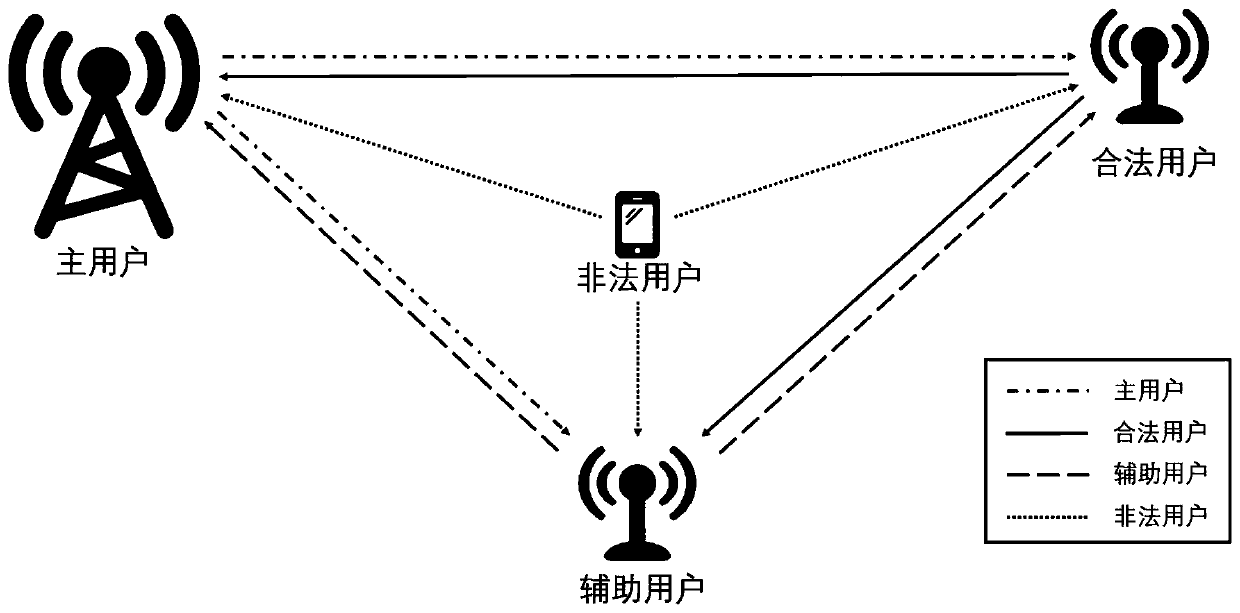
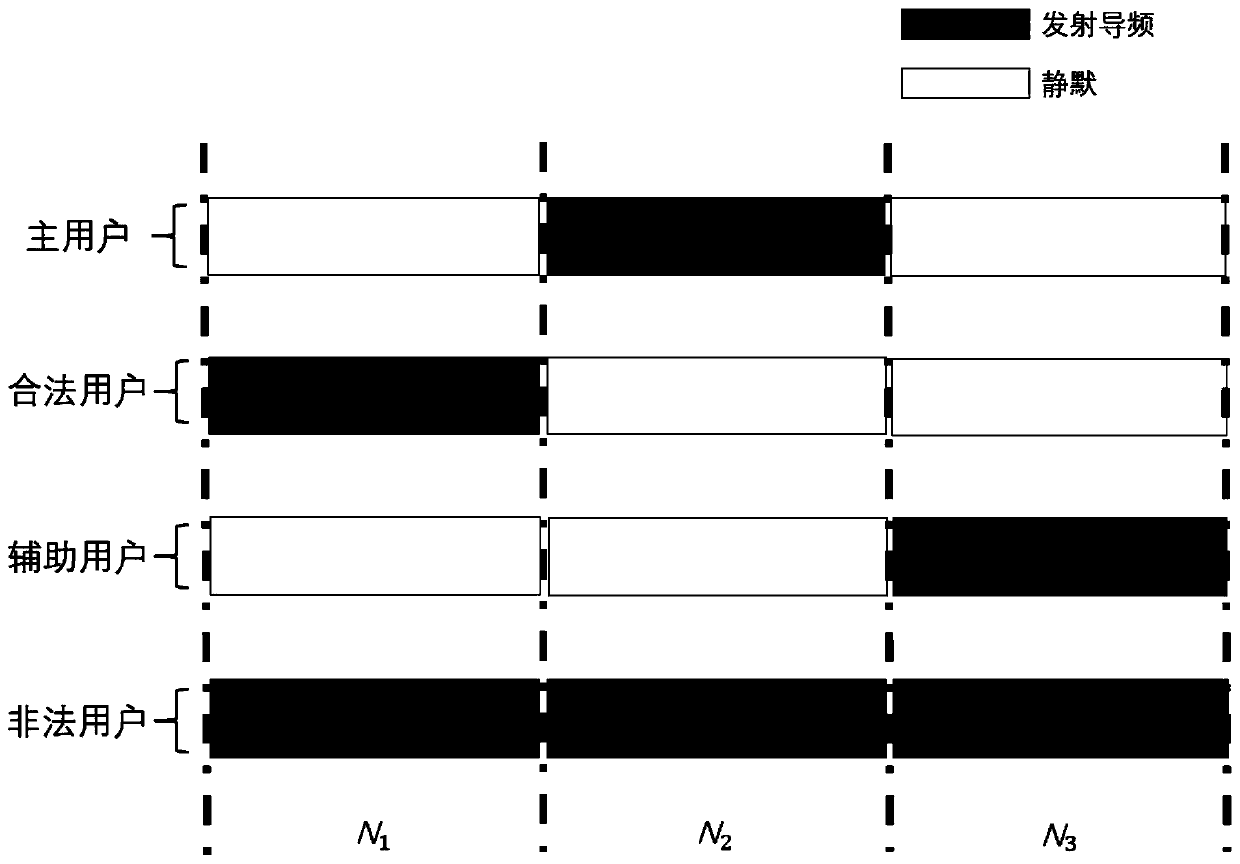
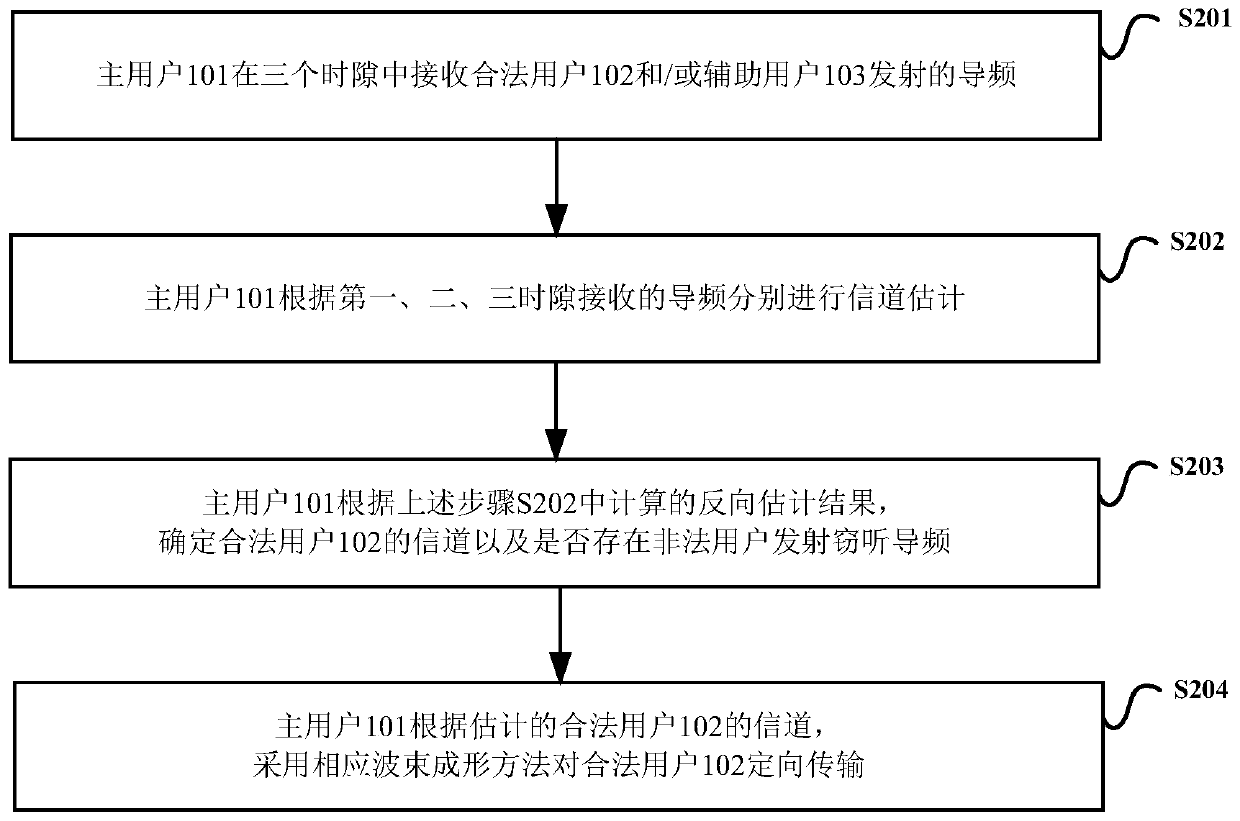
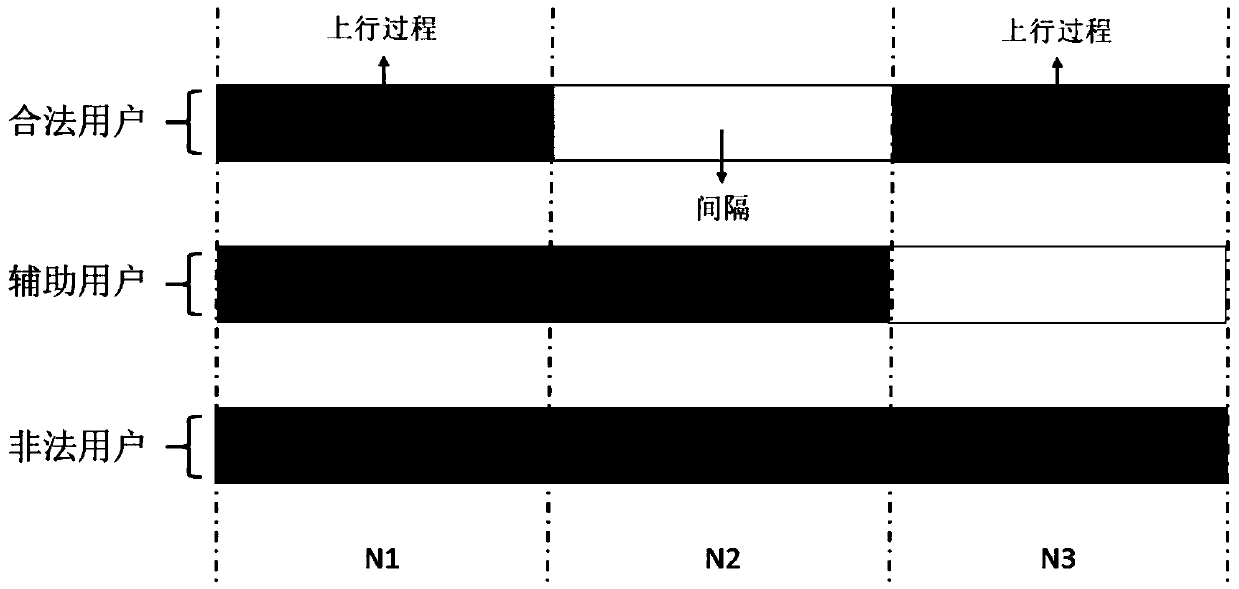
Method, system and device for detecting wiretapping pilot signal sent by illegal user
ActiveCN108768901AAvoid the risk of secondary fraudIncrease confidentiality capacityBaseband system detailsSecret communicationInformation securityComputer science
The invention discloses a method, system and device for detecting a wiretapping pilot signal sent by an illegal user. The method comprises the following steps: receiving pilot signals sent by a legaluser and an auxiliary user in a first time slot, receiving a pilot signal sent by the legal user in a second time slot, and receiving a pilot signal sent by the auxiliary user in a third time slot; respectively calculating reverse channel estimation results according to the pilot signals received in the first, the second and the third time slots; and according to the calculated reverse channel estimation results, determining a channel of the legal user and whether the illegal user sends the wiretapping pilot signal or not. The method, system and device provided by the invention has the advantages that the deceitful pilot signal and the illegal user can be detected, so that wiretapping of the illegal user can be prevented, and high information security of the legal user can be guaranteed.
Owner:BEIJING UNIV OF POSTS & TELECOMM
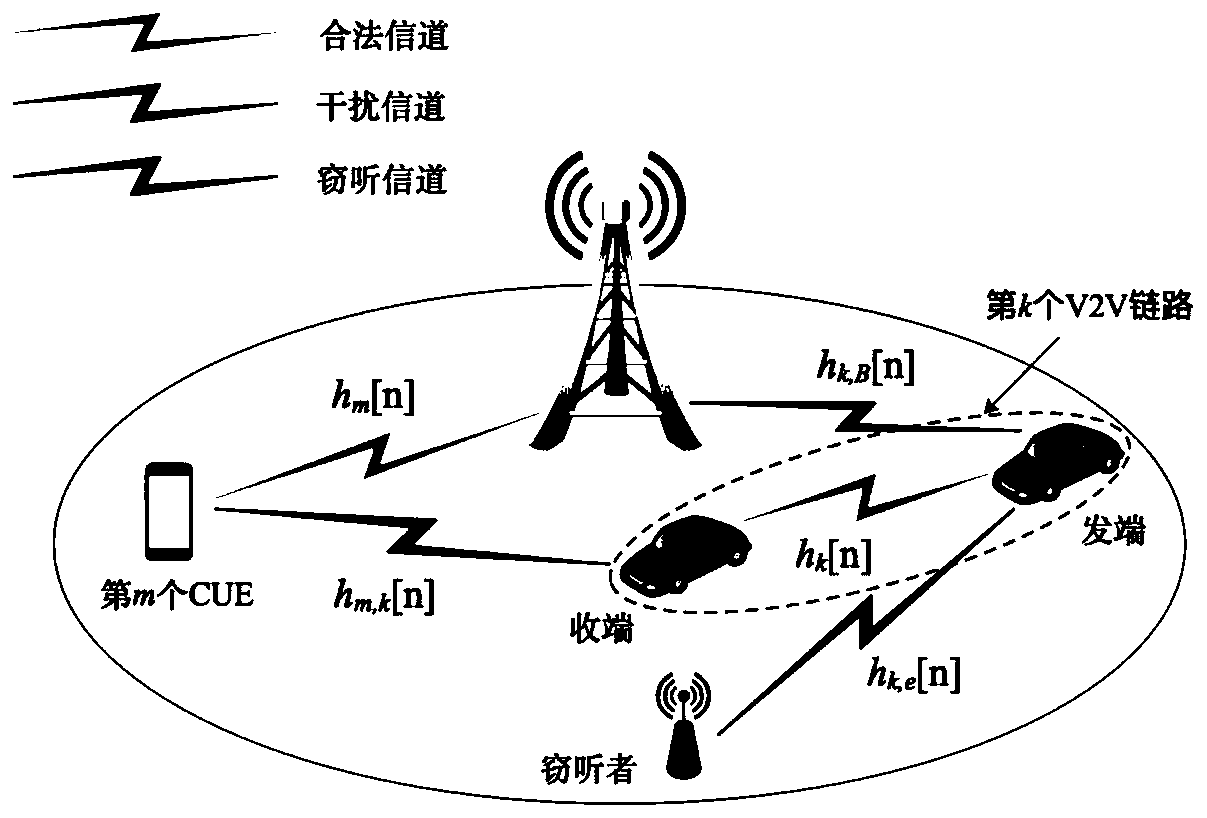
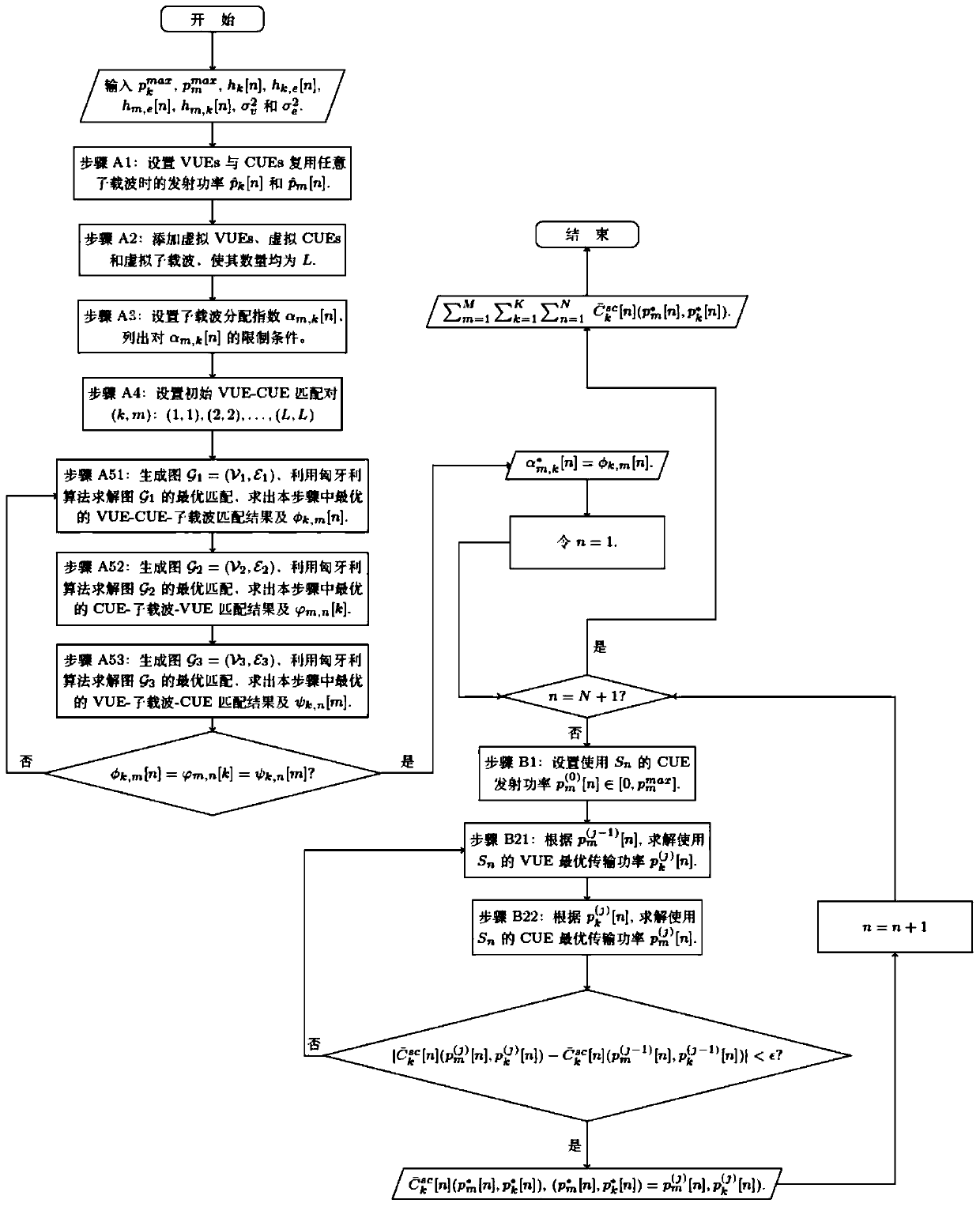
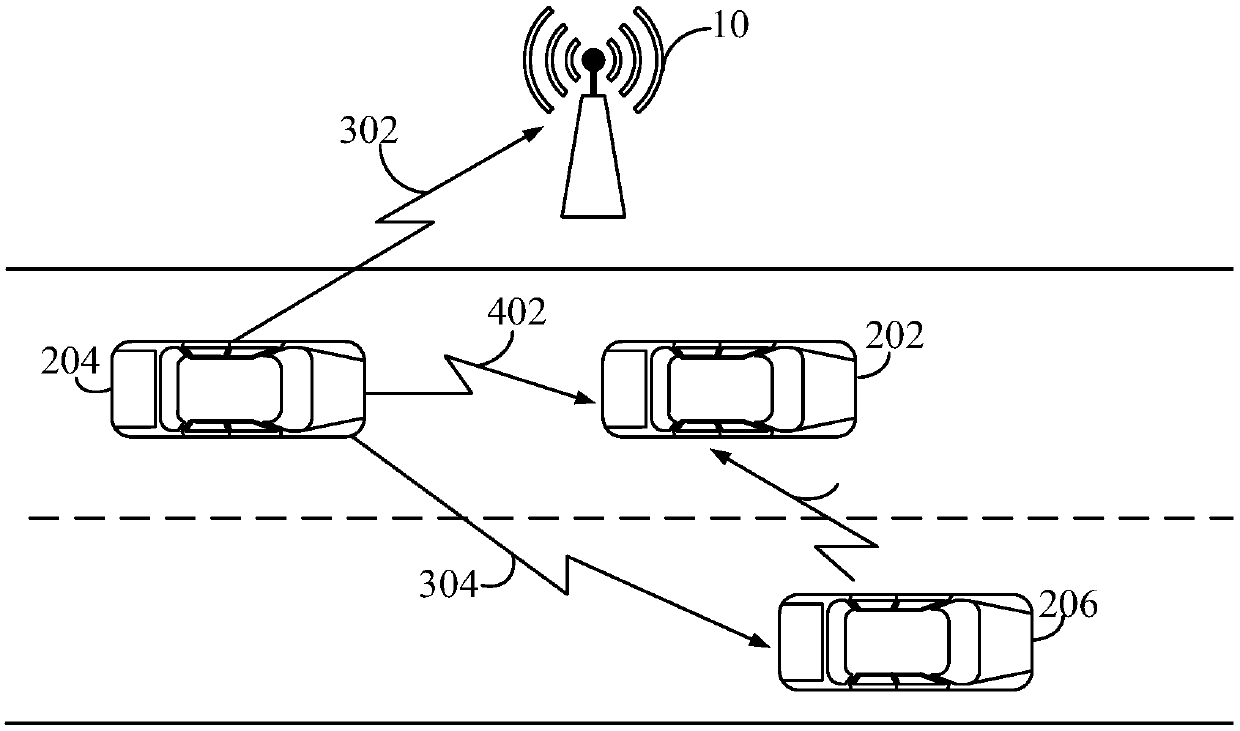
A physical layer security method and system based on resource allocation in V2V communication
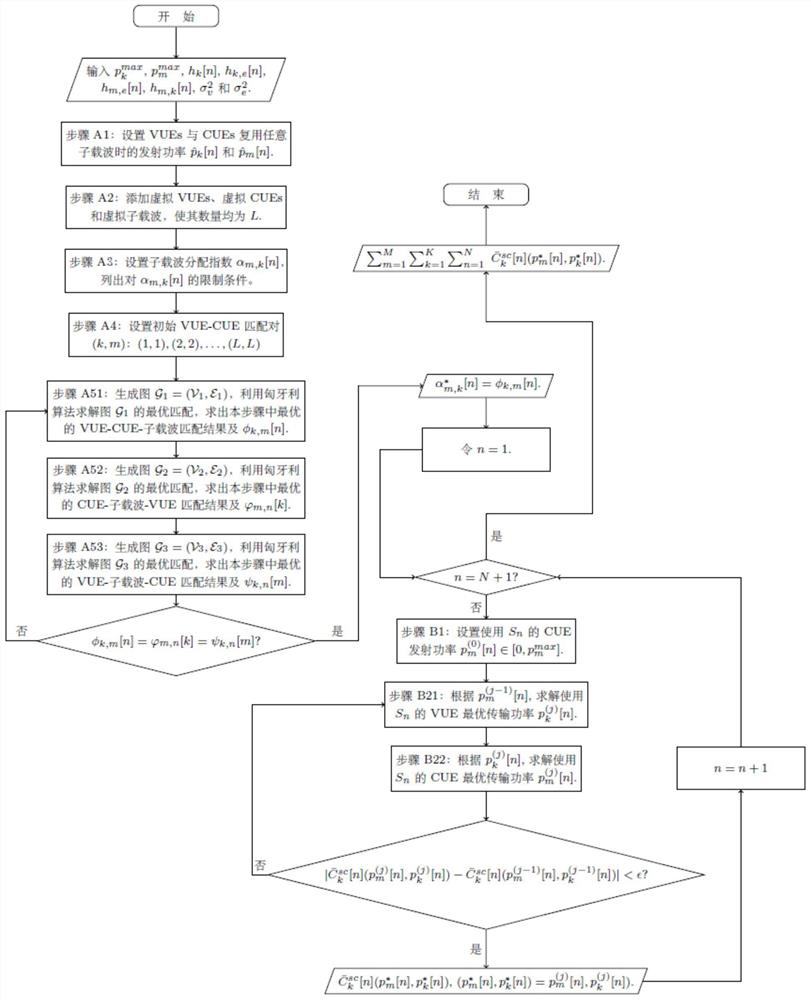
ActiveCN109714732AIncrease confidentiality capacityConfidential Capacity GuaranteeParticular environment based servicesVehicle-to-vehicle communicationConfidentialityPhysical layer
The invention discloses a physical layer security method and system based on resource allocation in V2V communication, which can improve the confidentiality of the system, and belongs to the technicalfield of wireless communication. The method comprises: S1, when a wiretaker wiretaps confidential information of all vehicle user equipment VUEs in a cellular network, the purpose of maximizing the sum confidentiality capacity of all the vehicle user equipment VUEs is achieved, multiplexed subcarriers are distributed to the vehicle user equipment VUEs and cellular user equipment CUEs, and the VUEs and the CUEs have the same priority; When the eavesdropper only eavesdrops confidential information of part of the VUEs in the cellular network to enable the sum of the confidential capacity of theeavesdropped VUEs and the channel capacity of the VUEs which are not eavesdropped to be maximum, multiplexing subcarriers are distributed to the VUEs and the CUEs, and the VUEs and the CUEs have the same priority; And S2, the transmission power of the VUE and the CUE multiplexing the corresponding subcarriers is solved according to the subcarrier distribution result in the step S1.
Owner:HARBIN INST OF TECH
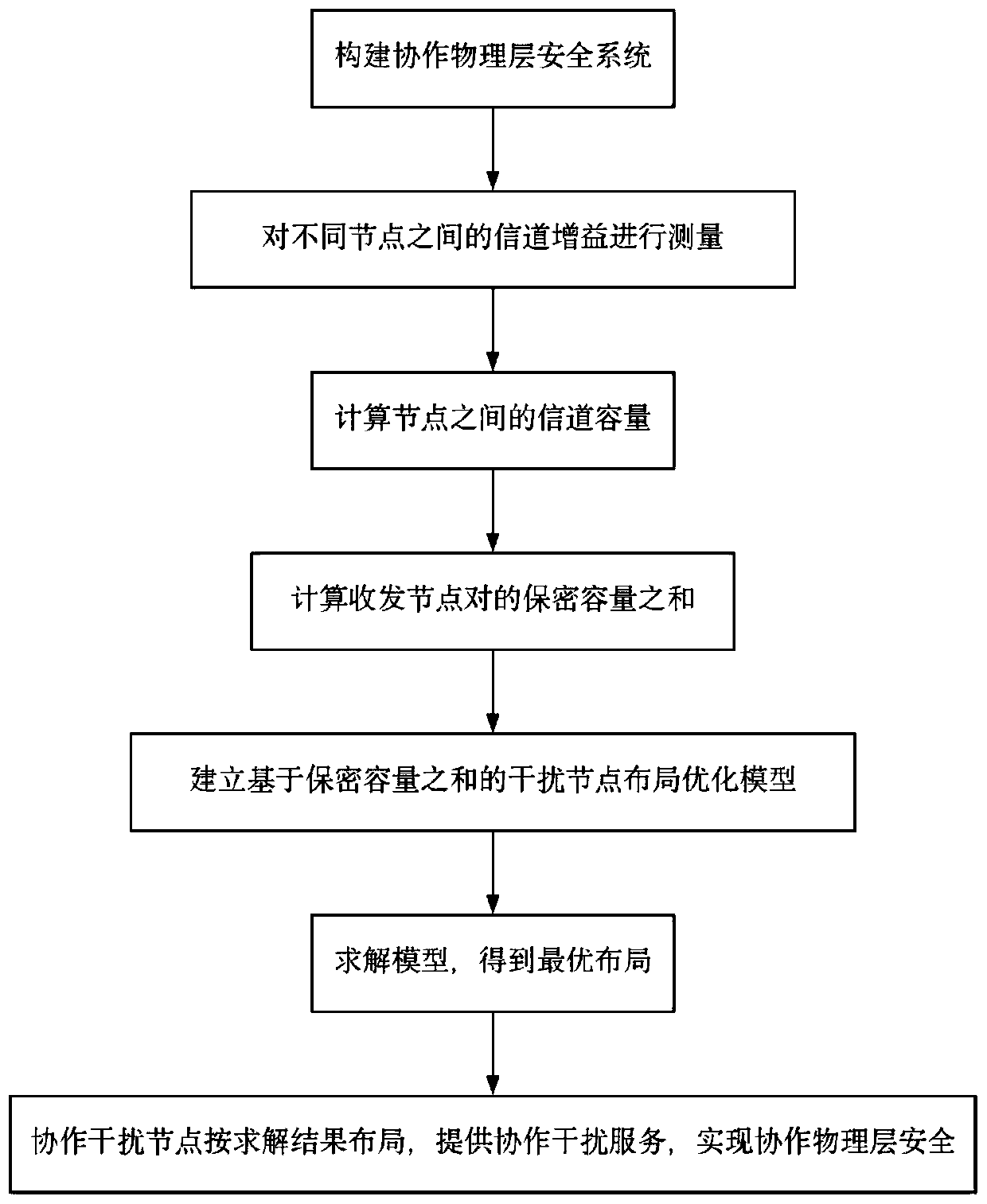
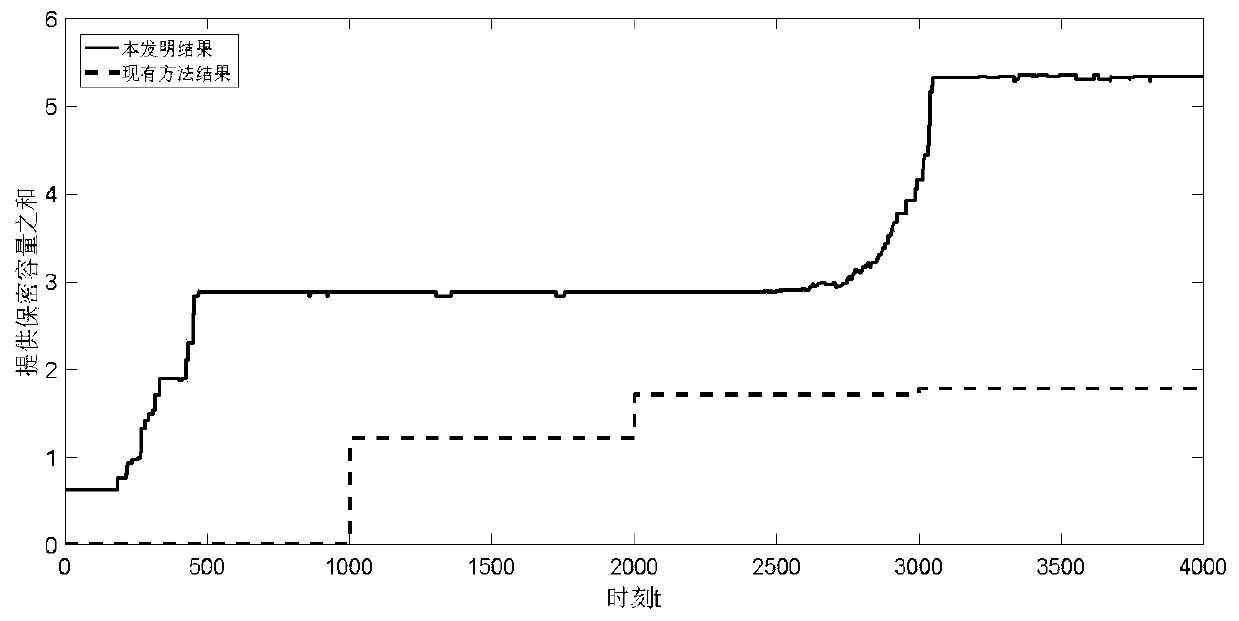
Cooperative physical layer security implementation method based on interference node optimization layout
ActiveCN110572826ABreak through the constraints of channel conditionsImprove securityNetwork traffic/resource managementSecurity arrangementCommunications securityComputer architecture
The invention provides a cooperative physical layer security implementation method based on interference node optimization layout, which is used for solving the technical problem of small confidentialcapacity acquired by transceiving node pairs in the prior art, and comprises the following implementation steps of: constructing a cooperative physical layer security system; measuring the channel gain between different nodes; calculating the channel capacity between the nodes; calculating the sum of confidential capacities provided by the cooperative interference nodes; establishing a cooperative interference node layout optimization model based on the sum of confidential capacities, and solving the cooperative interference node layout optimization model; and arranging the cooperative interference nodes and providing cooperative interference service according to a solving result, so as to achieve cooperative physical layer security. The method can be applied to different fields of wireless communication security, cooperative interference, secret communication and the like.
Owner:XIDIAN UNIV +1
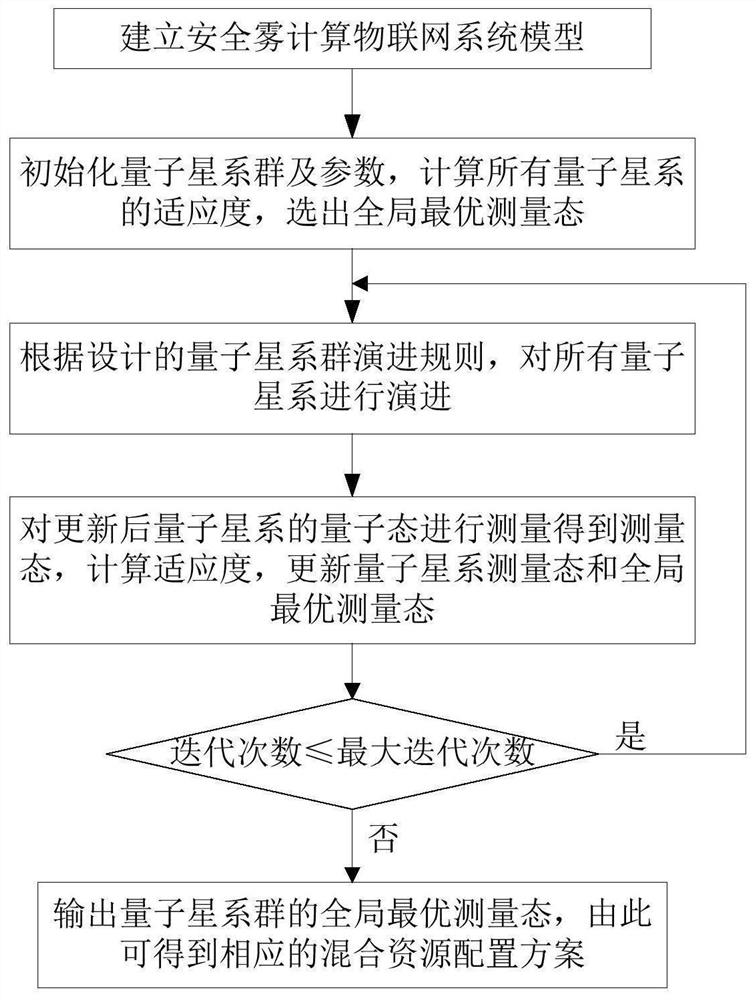
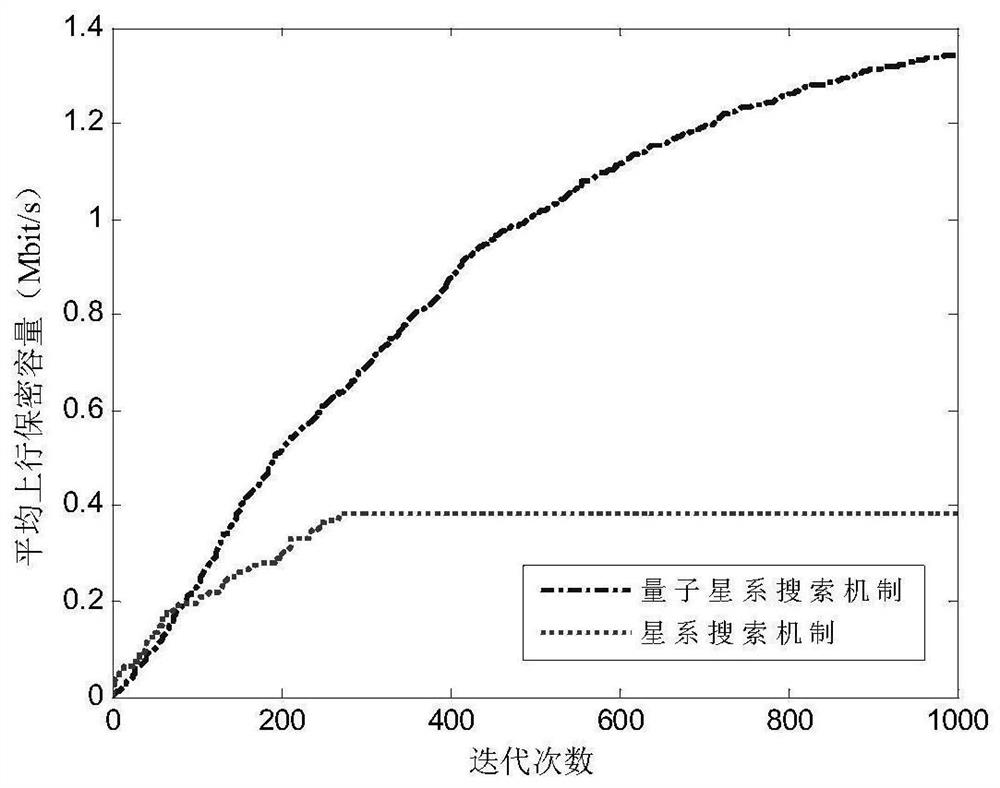
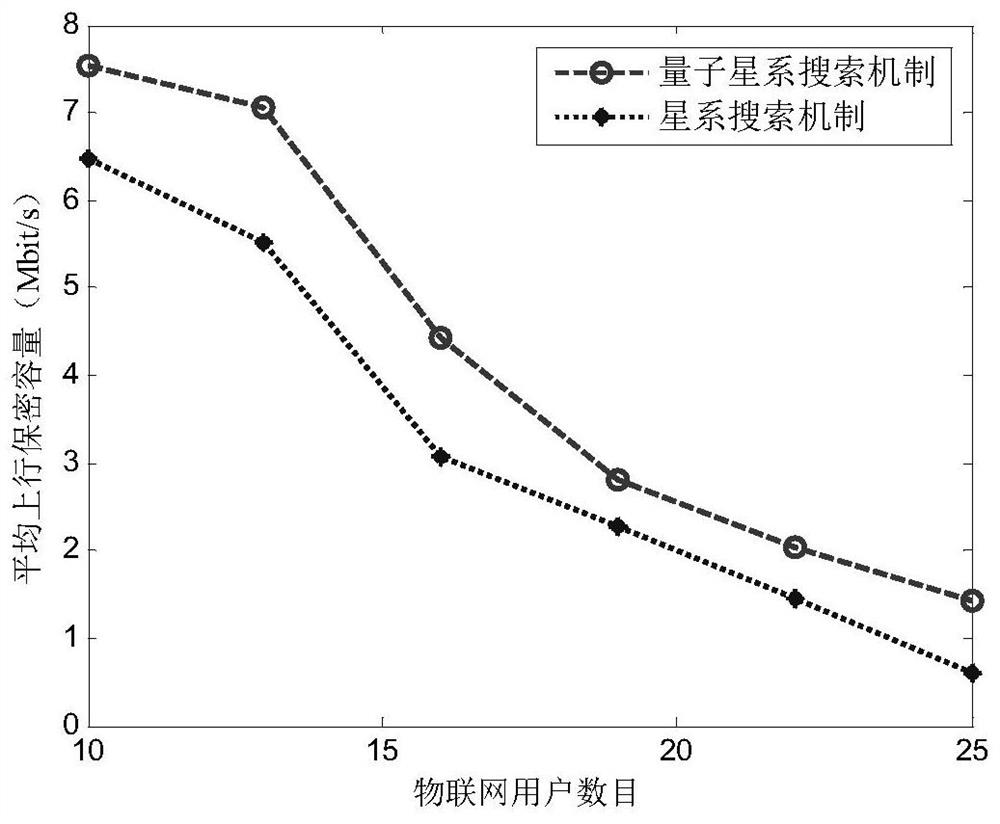
Hybrid resource configuration method for fog computing Internet-of-Things physical layer security
ActiveCN112787811AImprove securityReduce leakageKey distribution for secure communicationData switching networksData breachEngineering
The invention provides a hybrid resource configuration method for fog computing Internet-of-Things physical layer security. The method comprises the following steps: establishing a secure fog computing Internet-of-Things system model; initializing a quantum galaxy group and parameters; according to a designed quantum galaxy group evolution rule, evolving all quantum galaxes; measuring the quantum states of the updated quantum galaces to obtain the measurement states of all the updated quantum galaces, calculating the fitness of the measurement states, and updating the measurement states of all the quantum galaces and the global optimal measurement state of the quantum galaces according to the fitness value; and judging whether a termination condition is met. If the algebra of the current evolution is smaller than the set maximum number of iterations, i is made to be equal to i+1, and the third step is executed; otherwise, the evolution is terminated, and the global optimal measurement state of the quantum galaxy group is output, thereby obtaining a corresponding hybrid resource configuration scheme. According to the invention, the uplink secrecy capacity of the whole Internet-of-Things system is greatly improved, network data leakage is reduced, and the Internet-of-Things user is prevented from eavesdropping useful information by a malicious eavesdropper.
Owner:HARBIN ENG UNIV
Physical layer security algorithm based on subcarrier power allocation solution
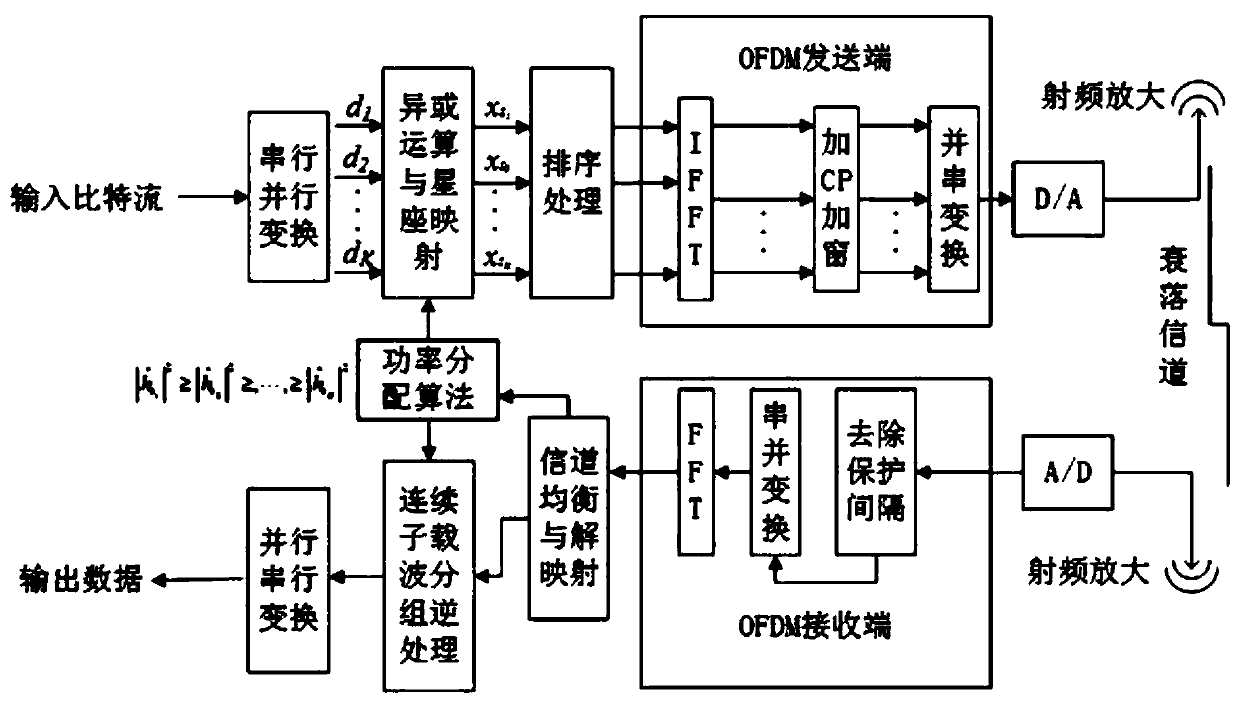
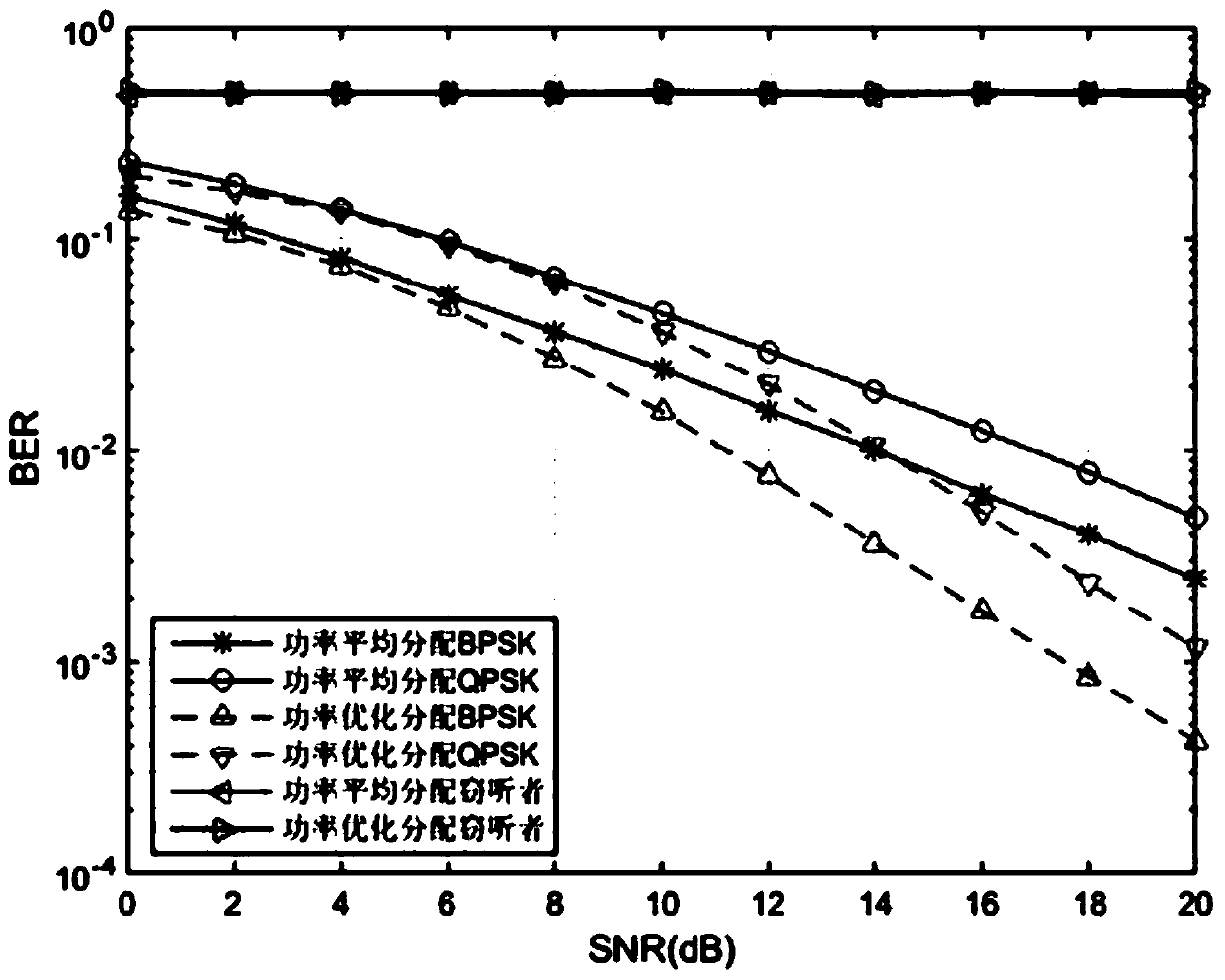
InactiveCN111224764AIncrease confidentiality capacityGuaranteed normal transmissionSignal allocationMulti-frequency code systemsAlgorithmPower optimization
The invention belongs to the technical field of wireless communication physical layer security, and particularly relates to a physical layer security algorithm based on a subcarrier power distributionsolution, which is suitable for a multicarrier communication network combining the characteristics of an OFDM system. According to the algorithm, a power distribution mode of a bit error rate optimization criterion is used for carrying out power distribution on subcarriers to optimize the bit error rate performance of a system, an empirical function power distribution scheme based on the power optimization distribution mode and applied to the algorithm provided by the invention is provided, and a power distribution coefficient closed solution is obtained. An algorithm simulation result showsthat a legal receiver can reliably decode, the error rate of an eavesdropper is close to 0.5, and a power optimization allocation algorithm simulation result shows that under the condition of a low signal-to-noise ratio, the bit error rate performance is optimized by 10%-20%; under the condition of 20dB, the bit error rate performance is improved by one order of magnitude.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +1
Resource allocation method for improving wireless transmission safety performance of Internet of Vehicles
ActiveCN109996218AImprove securityIncrease confidentiality capacityParticular environment based servicesVehicle wireless communication serviceWireless transmissionResource block
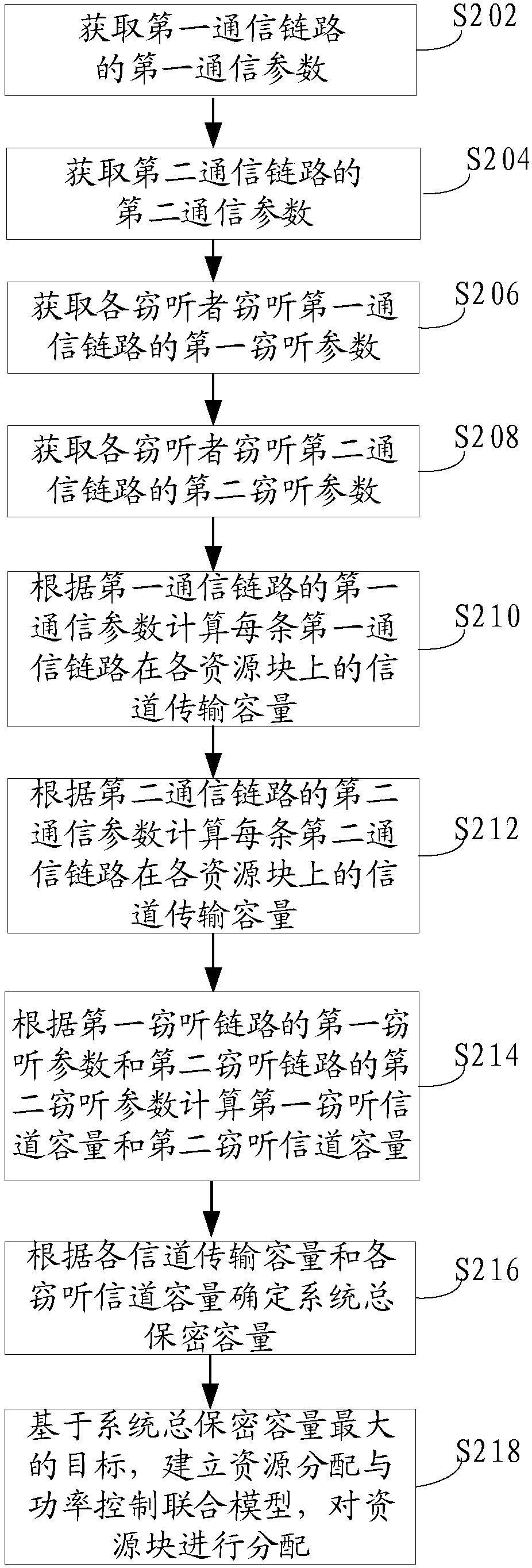
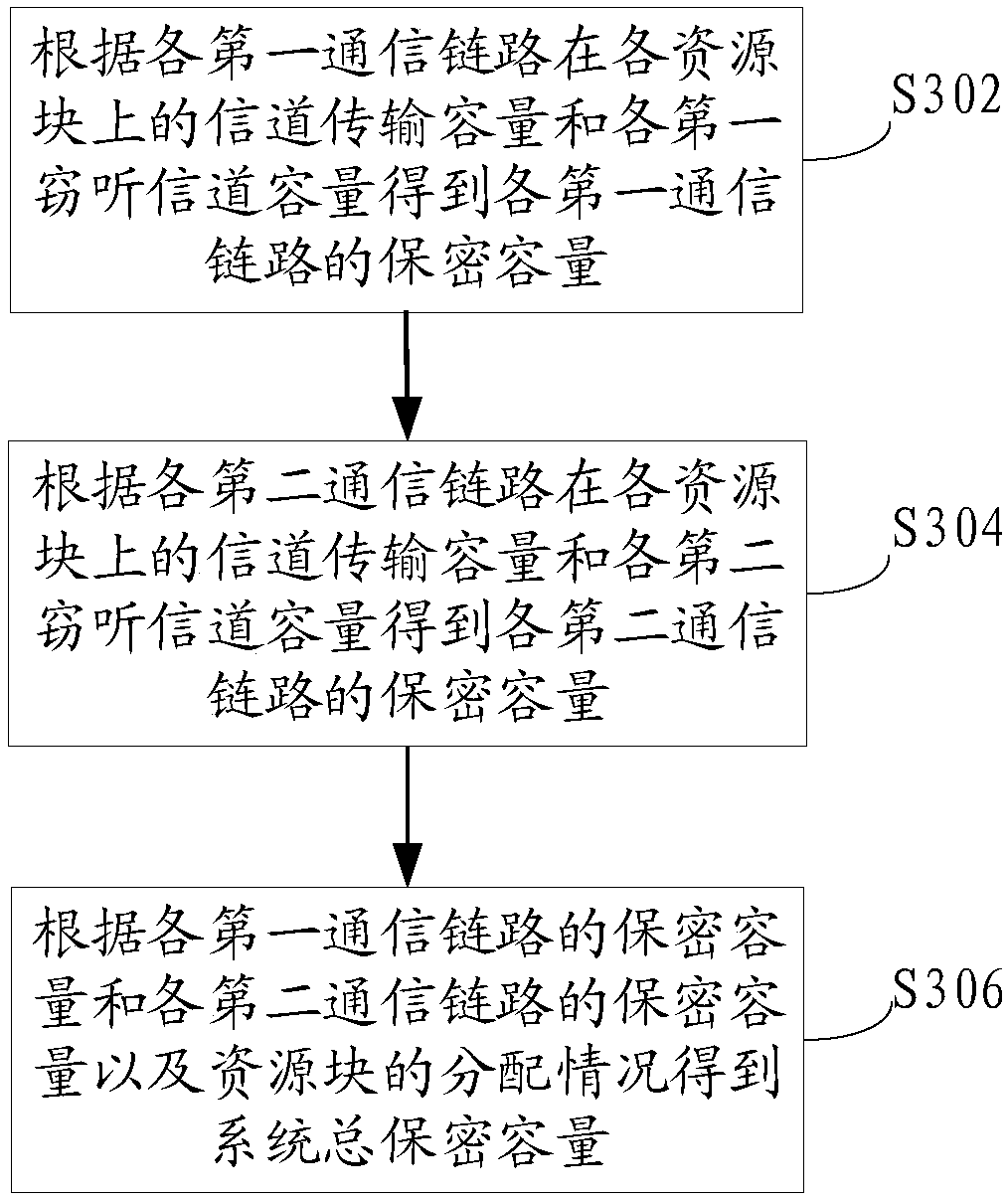
The invention relates to a resource allocation method for improving the wireless transmission safety performance of the Internet of Vehicles. The method comprises the steps of obtaining a first communication parameter of each first communication link, a second communication parameter of each second communication link, a first eavesdropping parameter of a first eavesdropping link and a second eavesdropping parameter of a second eavesdropping link in the Internet of Vehicles, respectively calculating channel transmission capacities of each first communication link and each second communication link on each resource block according to the first communication parameter and the second communication parameter; respectively calculating a first eavesdropping channel capacity and a second eavesdropping channel capacity according to the first eavesdropping parameter and the second eavesdropping parameter, and determining the total confidentiality capacity of the system through the transmission capacity of each channel and the capacity of each eavesdropping channel, establishing a resource allocation and power control combined model based on the target of the maximum total confidentiality capacity of the system, allocating resource blocks, and improving the safety performance of the system in a manner of improving the confidentiality capacity of the system.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD
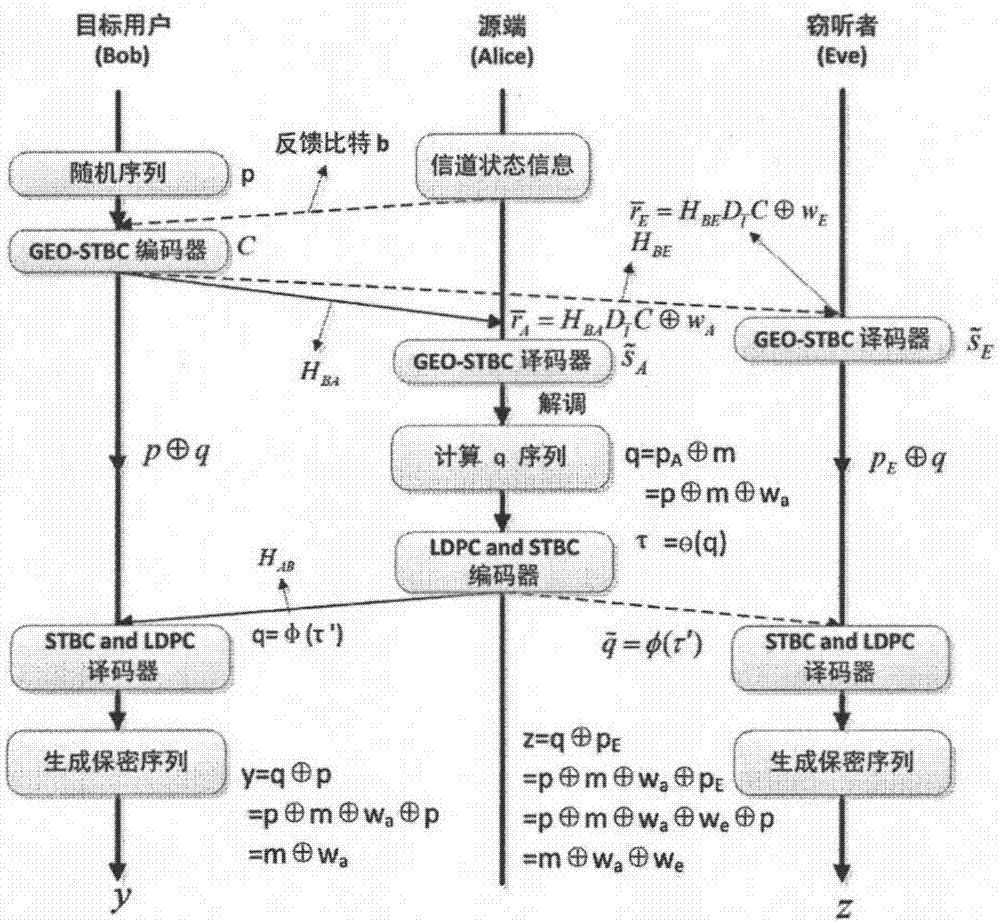
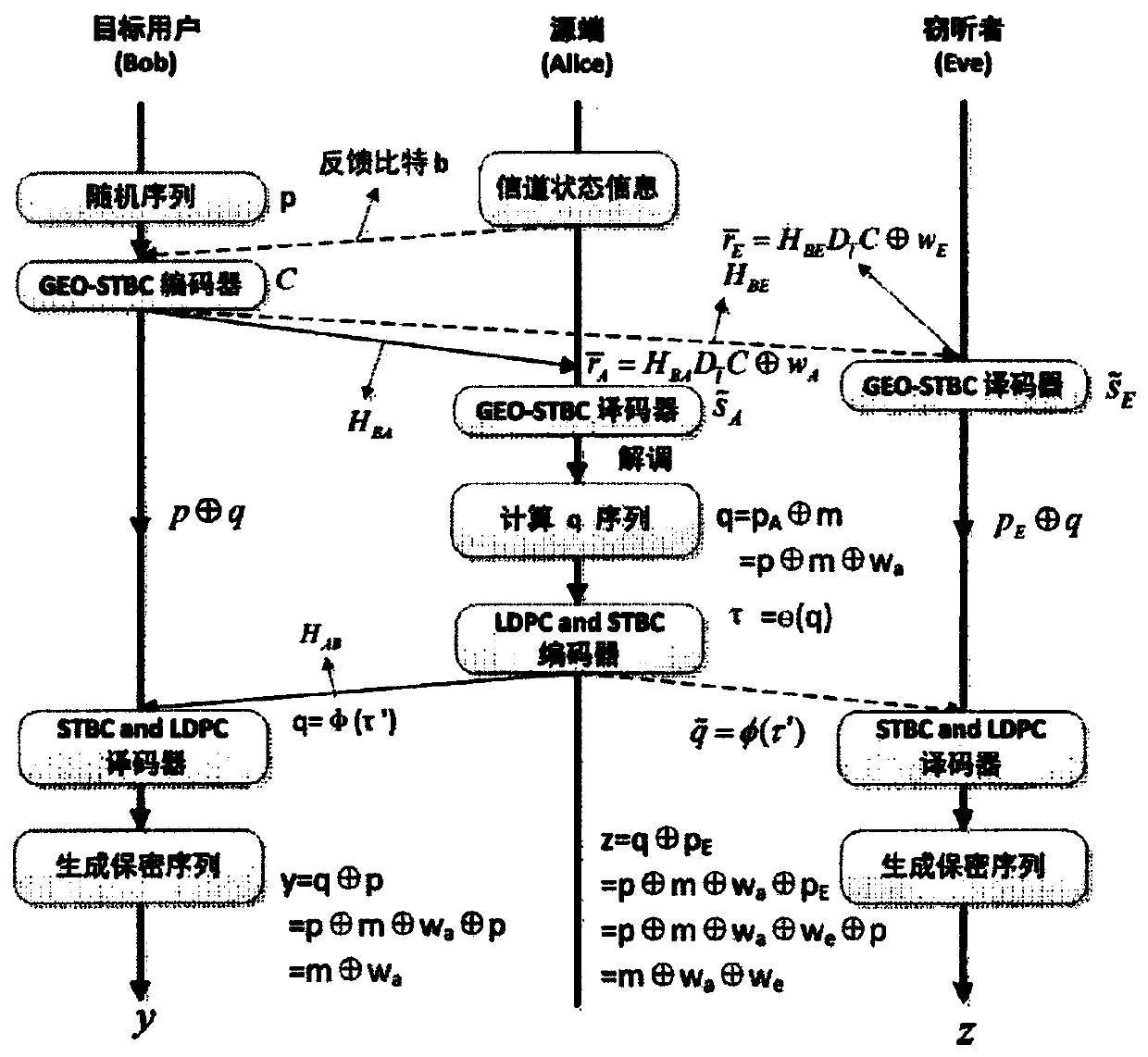
Secure communication method based on feedback under MIMO eavesdropping channel
ActiveCN106972912ALarge diversity gain and coding rateSimple linear processingError prevention/detection by diversity receptionSignal-to-noise ratio (imaging)Secure communication
The invention provides a secure communication method based on feedback under a MIMO eavesdropping channel. The secure communication between a target user possessing N transmitting antennas and a source end is realized, and the eavesdropping of an eavesdropper is prevented. The secure communication method is characterized in that the feedback performance gain of the source end as the receiving end is optimized, so that the receiving signal-to-noise ratio of the source end is higher than the eavesdropper. The secure capacity of the MIMO eavesdropping channel is improved, not only can be the receiving signal-to-noise ratio of the legal receiving end improved, but also can be the feedback performance gain of the MIMO eavesdropping channel enlarged. A theoretical simulation experiment shows that the feedback performance gain is in a linear increasing relation along the increasing of the signal-to-noise ratio; and meanwhile, the theoretical simulation shows that the security gap between the legal receiving end using the protocol and the eavesdropping end is increased along the increasing of the transmitting antenna number and / or signal-to-noise ratio.
Owner:DONGHUA UNIV
Method and device for detecting eavesdropping pilot frequency in channel training process
ActiveCN110034795AIncrease confidentiality capacityRadio transmissionChannel estimationTelecommunicationsEstimation result
The invention discloses a method for detecting eavesdropping pilot frequency in a channel training process, which is characterized by comprising the following steps of: setting a communication protocol; transmitting and receiving pilot frequency according to the communication protocol; calculating a channel reverse estimation result according to the pilot frequency received by each time slot to obtain a channel reverse estimation result; and estimating a channel of a legal user, an uplink communication channel of an illegal user and a downlink communication channel of the illegal user according to the channel reverse estimation result.
Owner:BEIJING UNIV OF POSTS & TELECOMM
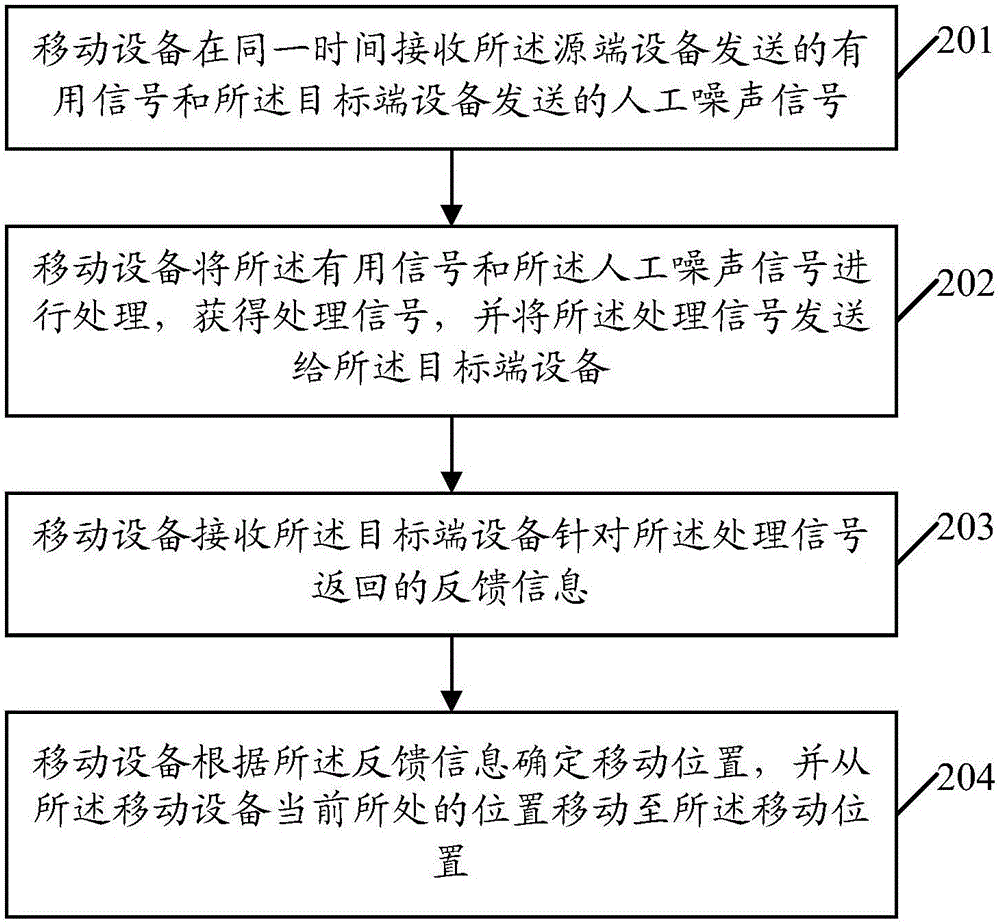
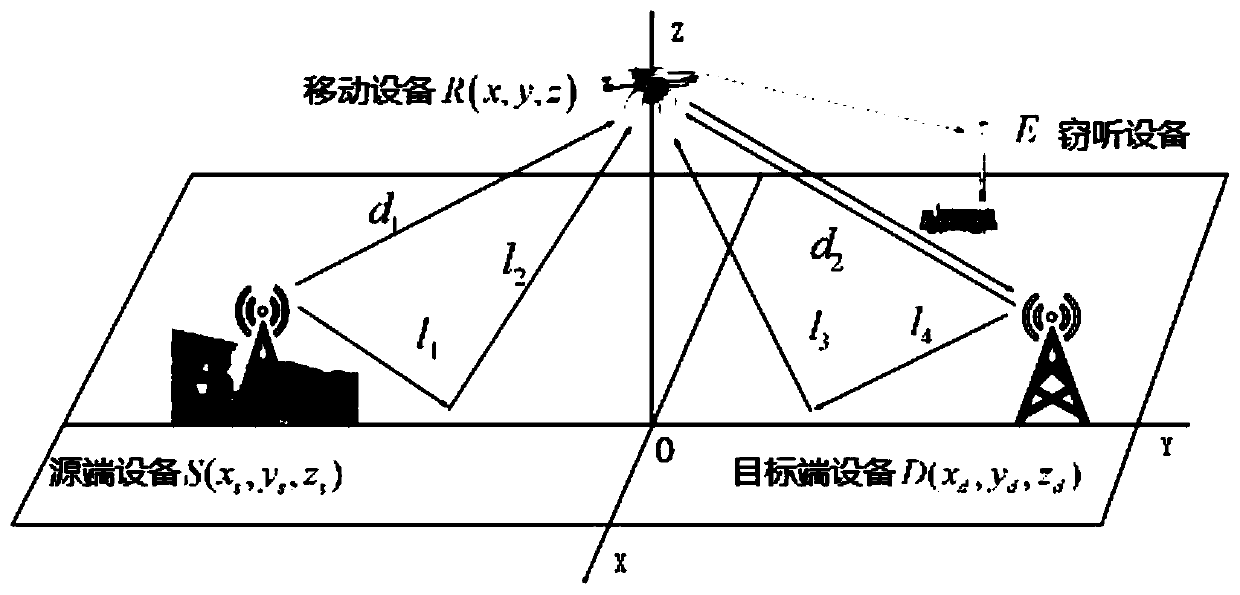
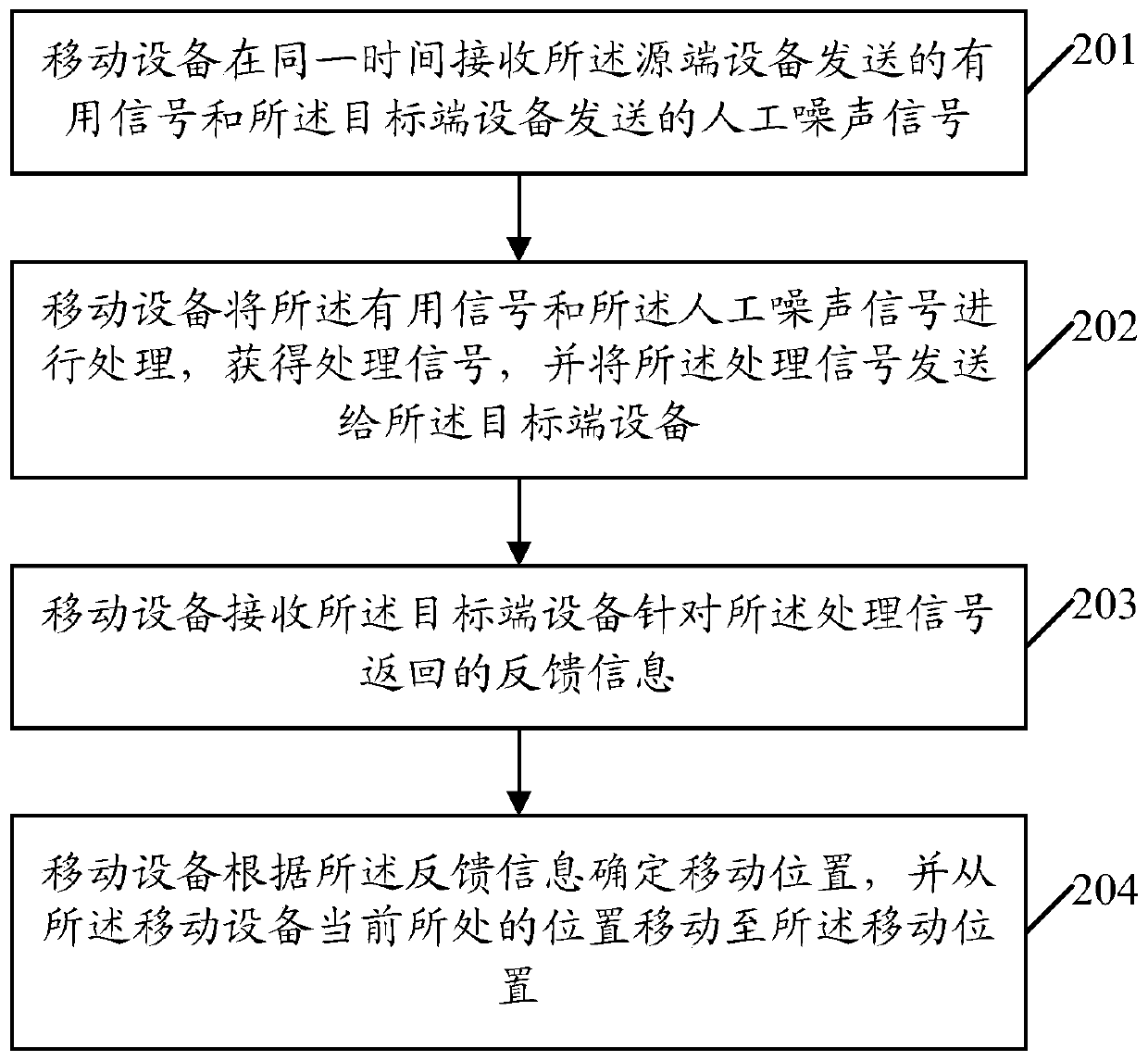
Mobile device position control method and device based on single bit feedback
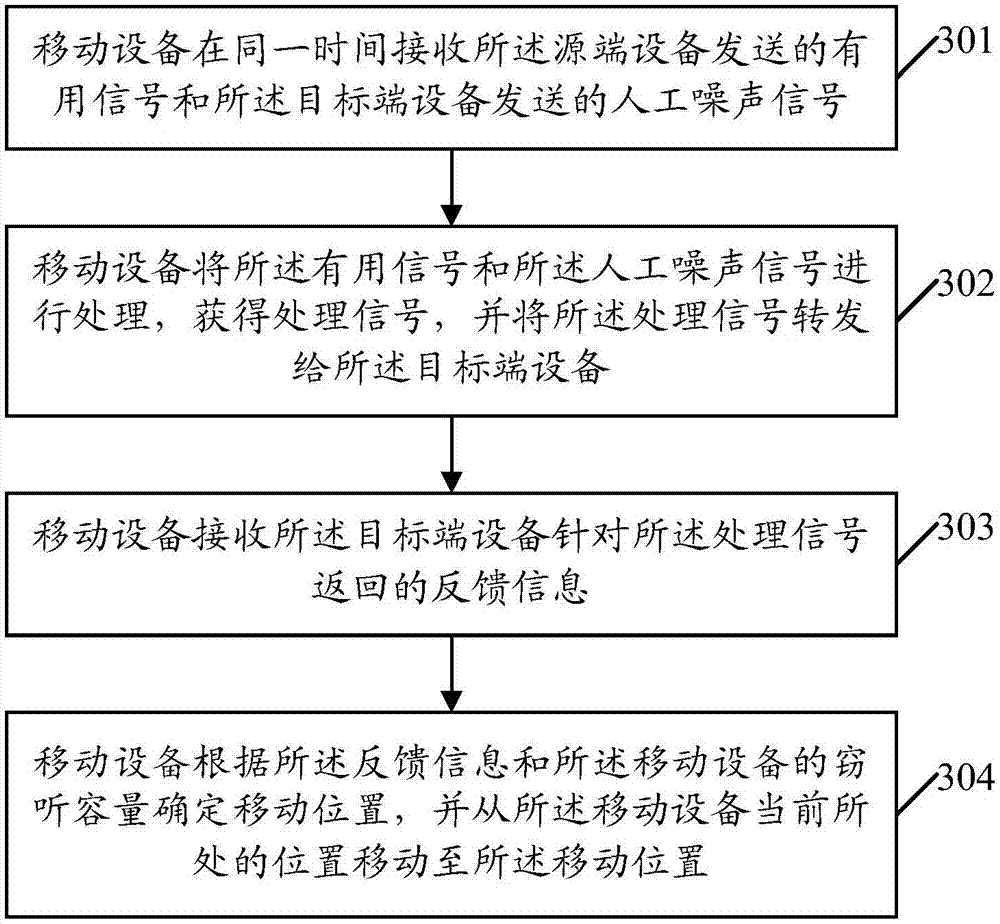
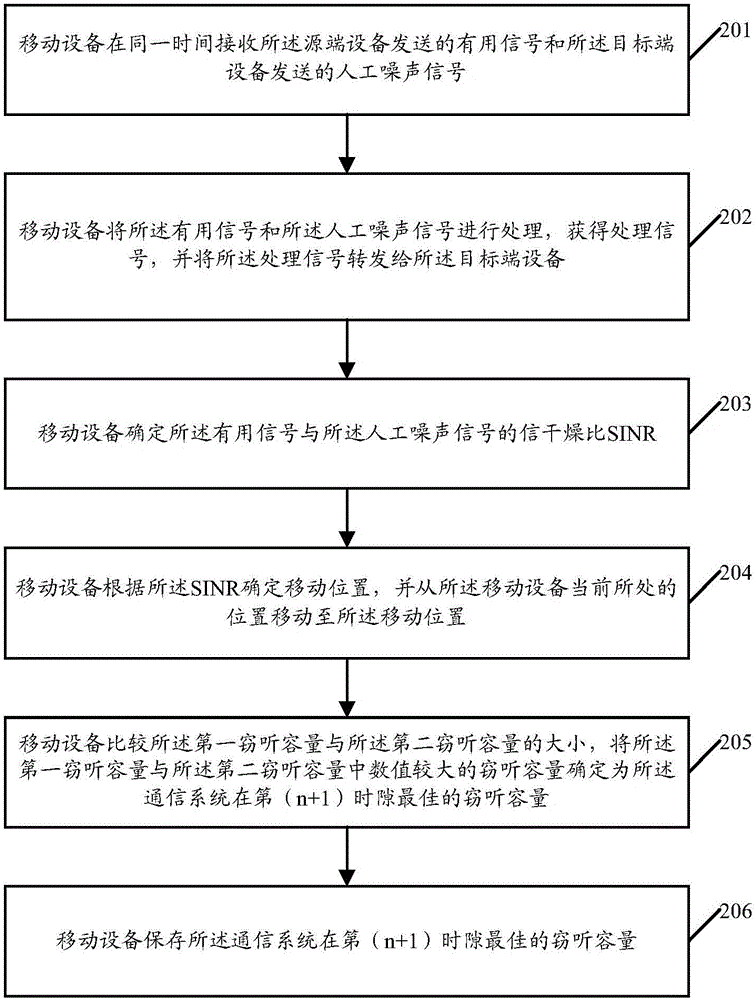
ActiveCN107436602AEavesdropping capacity boostIncrease confidentiality capacitySecret communicationRadio transmissionCommunications systemEavesdropping
The invention provides a mobile device position control method and a device based on single bit feedback. The method comprises steps: useful signals sent by a source-end device and artificial noise signals sent by a target-end device are received at the same time; the useful signals and the artificial noise signals are processed to acquire processed signals, and the processed signals are sent to the target-end device; feedback information returned for the processed signals by the target-end device is received, wherein the feedback information is used to indicate whether the secrecy capacity of the communication system is promoted simultaneously with the eavesdropping capacity of the mobile device; and according to the feedback information, a moving position is determined, and the current position of the mobile device is moved to the moving position. The embodiment of the invention can control the moving position of the mobile device, the secrecy capacity of the communication system is further optimized, and safety communication is ensured to be lasted.
Owner:SHENZHEN UNIV
Mobile device position control method and device based on adaptive noise feedback
ActiveCN107436601AIncrease confidentiality capacityRadio transmissionHigh level techniquesCommunications systemEngineering
The invention provides a mobile device position control method and a device based on adaptive noise feedback. The method comprises steps: useful signals sent by a source-end device and artificial noise signals sent by a target-end device are received at the same time; the signal to interference and noise ratio (SINR) of the signals received by the mobile device is determined; and according to the SINR, a moving position is determined, and the current position of the mobile device is moved to the moving position. According to the embodiment of the invention, the moving position of the mobile device can be determined according to the SINR, the secrecy capacity of the communication system is further optimized through adaptively adjusting the power of the artificial noise, and safety communication is ensured to be lasted.
Owner:SHENZHEN UNIV
A physical layer security method and system based on resource allocation in v2v communication
ActiveCN109714732BIncrease confidentiality capacityConfidential Capacity GuaranteeParticular environment based servicesVehicle-to-vehicle communicationMultiplexingResource assignment
Owner:HARBIN INST OF TECH
A multi-relay physical layer security method with known eavesdropping terminal channel information
InactiveCN104540124BIncrease confidentiality capacitySecurity arrangementHigh level techniquesSecure communicationChannel state information
The invention discloses a multi-relay physical layer safety method based on known eavesdropping end channel information to achieve safety communication of a physical layer. Based on known eavesdropping end channel information, a relay group is divided into a relay forwarding group part and a relay interference group part, effectiveness and safe transmission of information are guaranteed for a first information transmission time slot by means of the beam forming technology and the artificial interference technology, and information is effectively prevented from being received by an eavesdropping end in a second time slot by means of the known eavesdropping end channel information and the beam forming technology. On the premise that relay power distribution is considered, the beam forming vector of the relay forwarding group part and the beam forming vector of the relay interference group part are optimized, and the maximum safe capacity of a system is obtained finally.
Owner:SHANDONG UNIV
Method and device for position control of mobile equipment based on single-bit feedback
ActiveCN107436602BEavesdropping capacity boostIncrease confidentiality capacitySecret communicationRadio transmissionComputer hardwareSecure communication
The invention provides a mobile device position control method and a device based on single bit feedback. The method comprises steps: useful signals sent by a source-end device and artificial noise signals sent by a target-end device are received at the same time; the useful signals and the artificial noise signals are processed to acquire processed signals, and the processed signals are sent to the target-end device; feedback information returned for the processed signals by the target-end device is received, wherein the feedback information is used to indicate whether the secrecy capacity of the communication system is promoted simultaneously with the eavesdropping capacity of the mobile device; and according to the feedback information, a moving position is determined, and the current position of the mobile device is moved to the moving position. The embodiment of the invention can control the moving position of the mobile device, the secrecy capacity of the communication system is further optimized, and safety communication is ensured to be lasted.
Owner:SHENZHEN UNIV
A detection method, system and device for eavesdropping pilots transmitted by illegal users
ActiveCN108768901BAvoid the risk of secondary fraudIncrease confidentiality capacityBaseband system detailsSecret communicationTelecommunicationsEavesdropping
The invention discloses a method, system and device for detecting a wiretapping pilot signal sent by an illegal user. The method comprises the following steps: receiving pilot signals sent by a legaluser and an auxiliary user in a first time slot, receiving a pilot signal sent by the legal user in a second time slot, and receiving a pilot signal sent by the auxiliary user in a third time slot; respectively calculating reverse channel estimation results according to the pilot signals received in the first, the second and the third time slots; and according to the calculated reverse channel estimation results, determining a channel of the legal user and whether the illegal user sends the wiretapping pilot signal or not. The method, system and device provided by the invention has the advantages that the deceitful pilot signal and the illegal user can be detected, so that wiretapping of the illegal user can be prevented, and high information security of the legal user can be guaranteed.
Owner:BEIJING UNIV OF POSTS & TELECOMM
A Feedback-Based Secure Communication Method in MIMO Eavesdropping Channel
ActiveCN106972912BIncrease confidentiality capacityImprove bit error rate performanceError prevention/detection by diversity receptionSecure communicationEavesdropping
The invention provides a secure communication method based on feedback under a MIMO eavesdropping channel. The secure communication between a target user possessing N transmitting antennas and a source end is realized, and the eavesdropping of an eavesdropper is prevented. The secure communication method is characterized in that the feedback performance gain of the source end as the receiving end is optimized, so that the receiving signal-to-noise ratio of the source end is higher than the eavesdropper. The secure capacity of the MIMO eavesdropping channel is improved, not only can be the receiving signal-to-noise ratio of the legal receiving end improved, but also can be the feedback performance gain of the MIMO eavesdropping channel enlarged. A theoretical simulation experiment shows that the feedback performance gain is in a linear increasing relation along the increasing of the signal-to-noise ratio; and meanwhile, the theoretical simulation shows that the security gap between the legal receiving end using the protocol and the eavesdropping end is increased along the increasing of the transmitting antenna number and / or signal-to-noise ratio.
Owner:DONGHUA UNIV
Power allocation method for ccfd-massive MIMO system optimized by quantum backtracking search
ActiveCN108880734BImprove spectrum utilizationImprove confidentialitySpatial transmit diversitySecret communicationDistribution methodComplex system
Owner:HARBIN ENG UNIV
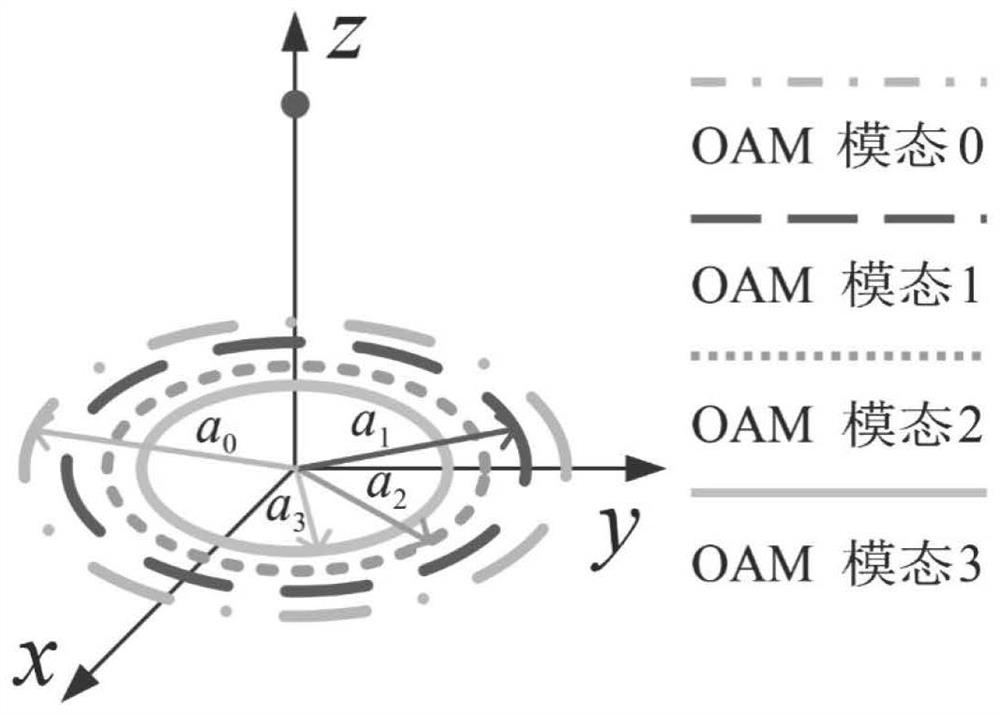
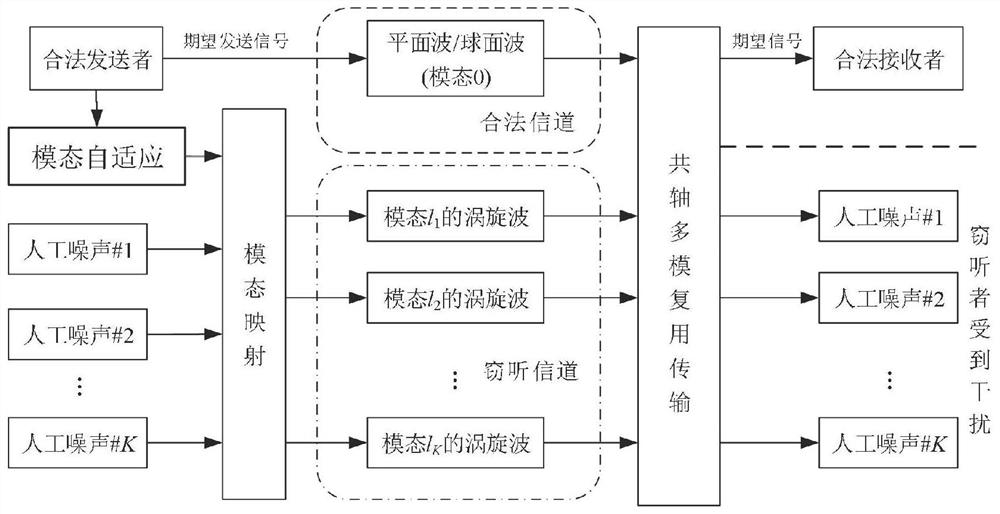
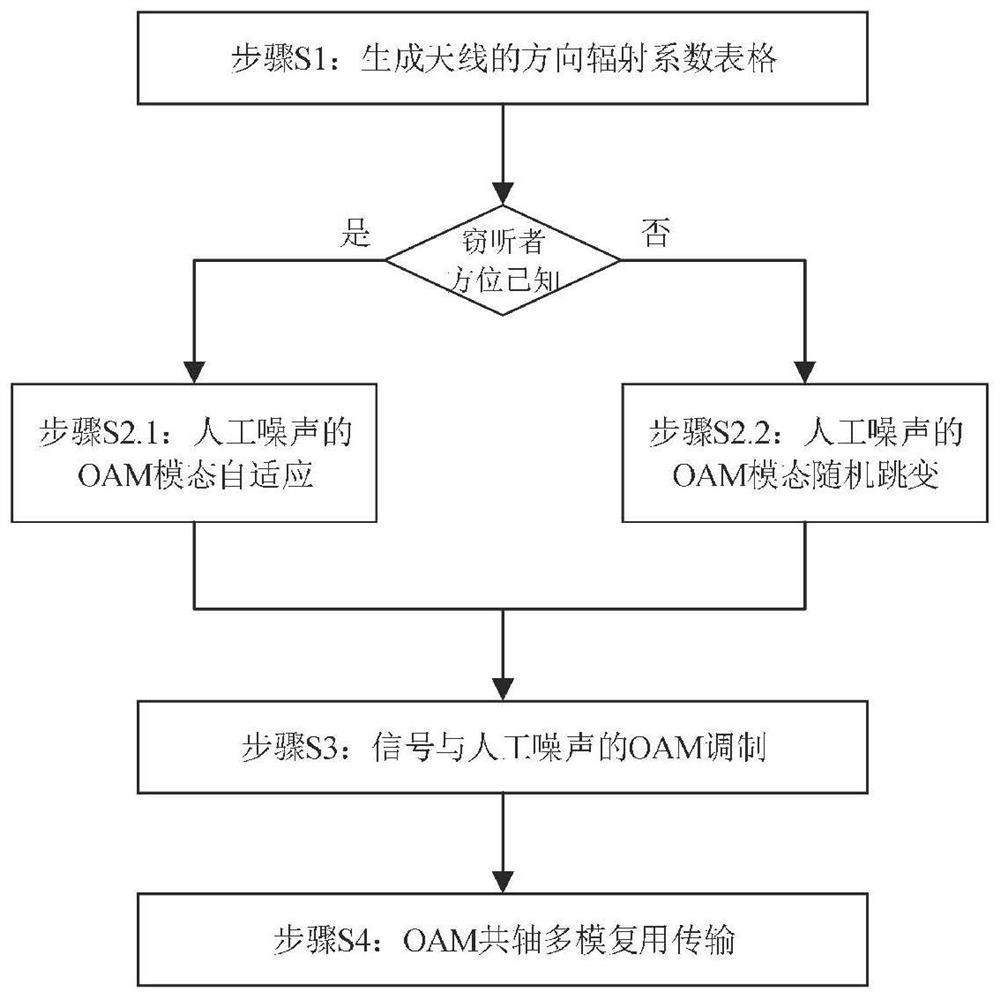
Self-adaptive safety communication device and method based on vortex electromagnetic waves
ActiveCN114189309AIncrease confidentiality capacityImprove anti-intercept performanceSecret communicationSecurity arrangementMultiplexingCarrier signal
The invention discloses a self-adaptive safety communication device and method based on vortex electromagnetic waves, and relates to the technical field of wireless communication. Generating a direction radiation coefficient table of the N-element uniform circular ring antenna array under a given carrier frequency; adaptively selecting an orbital angular momentum mode for sending the artificial noise; orbital angular momentum modulation of the sending signal and the artificial noise; the invention relates to coaxial multimode multiplexing transmission of orbital angular momentum. According to the invention, the secure wireless communication can be realized by using only one uniform circular ring antenna array. The artificial noise is multiplexed in a non-zero mode, so that legal users are not interfered, the channel capacity of eavesdroppers is reduced, and high-capacity secret communication is realized. Meanwhile, according to the direction angle information of the eavesdropper, the optimal mode of the artificial noise is adaptively selected, the eavesdropper is shielded to the maximum extent, and the secrecy performance of the system is improved. And when the direction of the eavesdropper is unknown, a mode of random hopping of an artificial noise mode is adopted to shield potential eavesdroppers in all directions, so that the secrecy capacity of the system is improved.
Owner:江苏集萃移动通信技术研究所有限公司
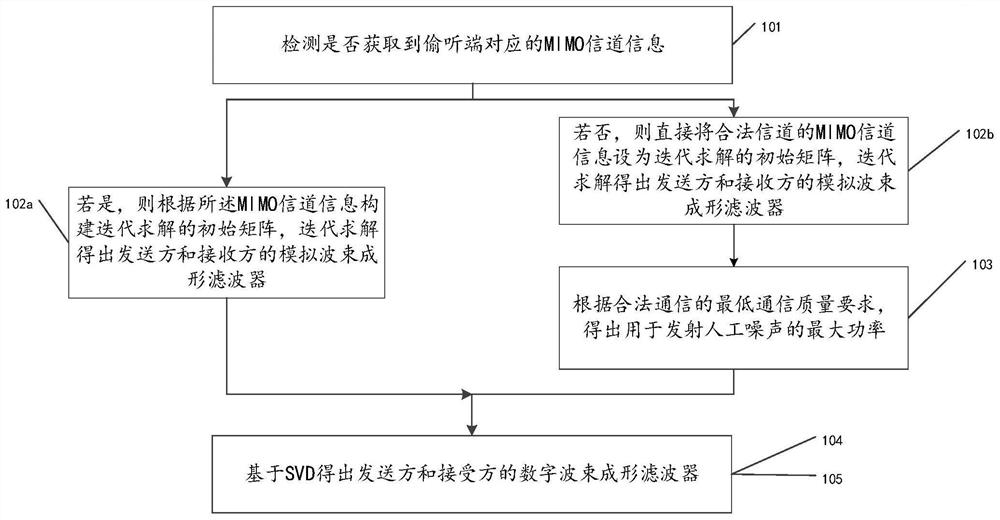
Design method and device of a hybrid beamforming filter based on millimeter wave mimo system security communication
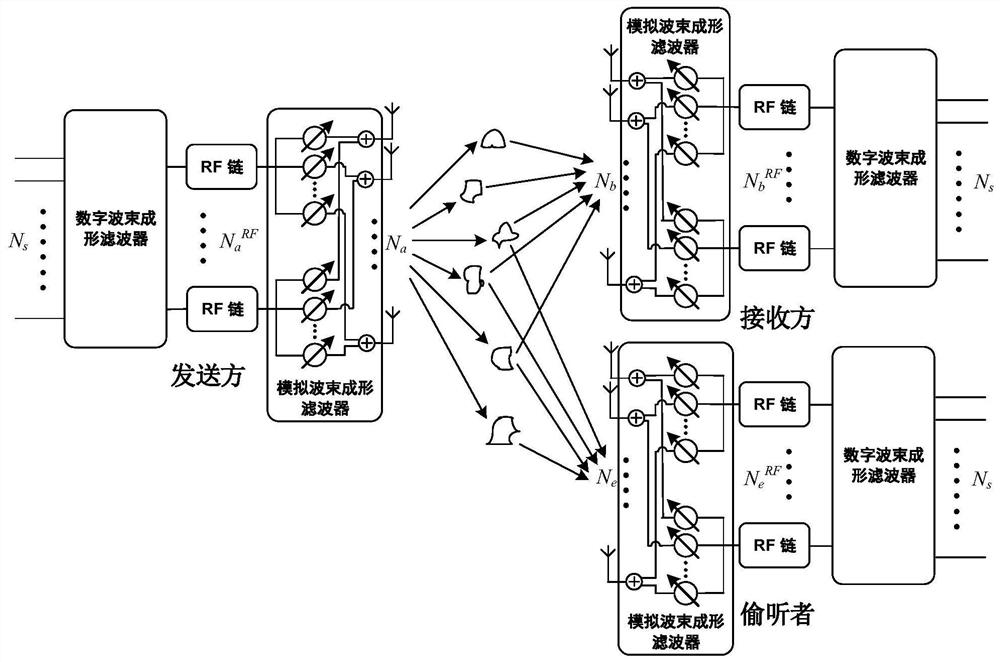
ActiveCN109004965BIncrease confidentiality capacitySpatial transmit diversityHybrid beamformingSecure communication
The invention discloses a design method and a device of a hybrid beamforming filter based on the safe communication of a millimeter wave MIMO system. The method includes: whether there is an eavesdropping channel is judged, if yes, analog beamforming filters are constructed according to the MIMO channel information corresponding to the eavesdropping end, otherwise the MIMO channel information ofthe legal channel is directly set as the initial matrix of iterative solution, and the analog beamforming filters are constructed. The digital beamforming filters obtained are all based on the SVD method. Based on the sparsity of millimeter wave channel and the limitations of analog filter design in millimeter wave system, considering the awareness of eavesdropping channel information, analog beamforming filter based on code-local joint selection of sender and receiver can improve the security capacity of MIMO system easily and efficiently, and make the mature physical layer security technology in traditional MIMO system, namely beamforming technology, be better transplanted to millimeter wave MIMO system.
Owner:DALIAN UNIV OF TECH
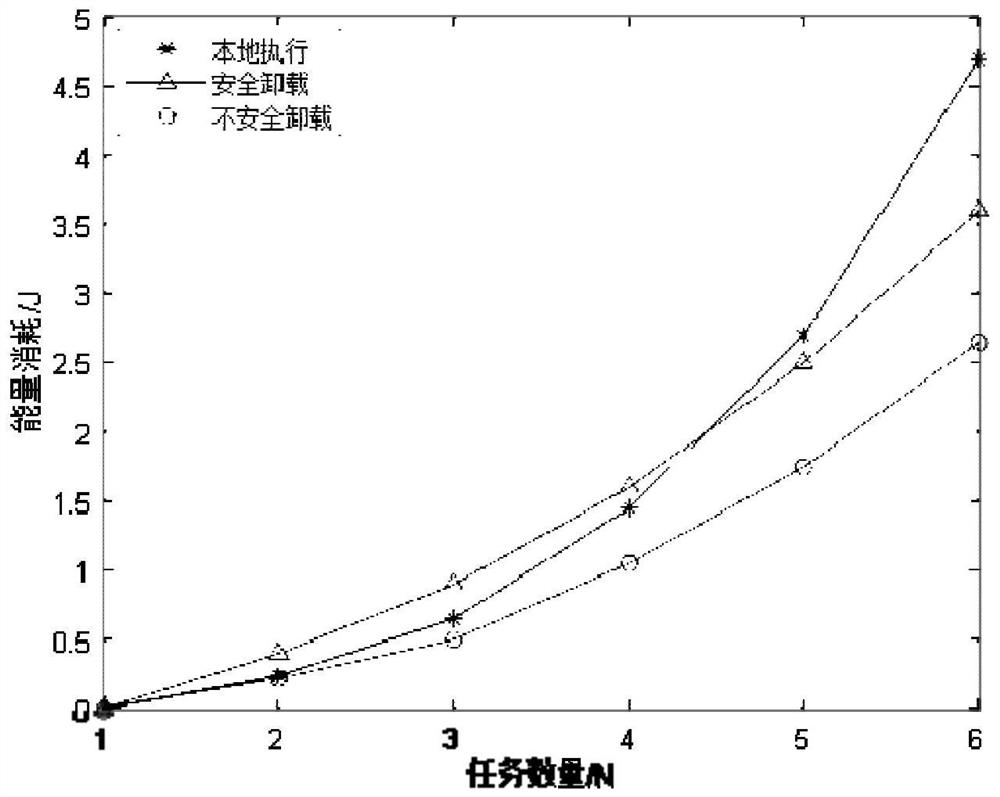
Power service secure transmission method and system based on edge calculation
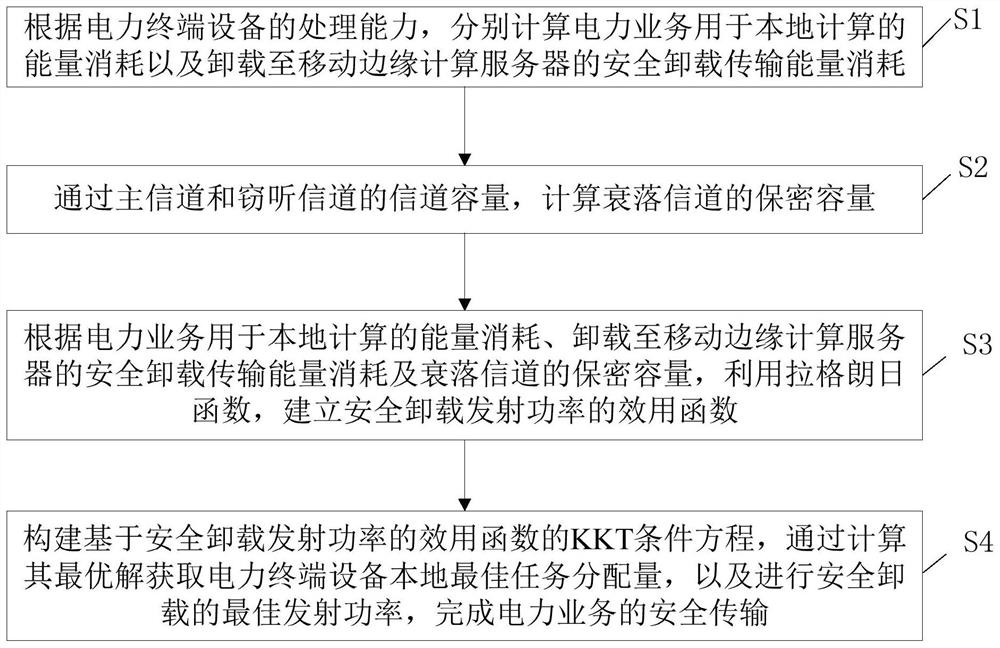
InactiveCN112995129AOptimize computing resourcesOptimize communication resourcesCircuit arrangementsTransmission monitoringPower utilityTransmitted power
The invention discloses a power service secure transmission method and system based on edge calculation. The method comprises the steps: taking the easy eavesdropping during data unloading and the limited processing resources of a power service terminal as consideration factors, According to the processing capability of power terminal equipment, carrying out the edge calculation; the method comprises the following steps: respectively calculating energy consumption of power service for local calculation and secure unloading transmission energy consumption unloaded to a mobile edge calculation server, introducing a Lagrange function based on a physical layer protection technology of main channel capacity and eavesdropping channel capacity, establishing a transmitting power utility function for secure unloading, introducing a KKT condition equation, and establishing a secure unloading transmission power utility function for secure unloading; by calculating the optimal solution, the local optimal task allocation quantity of the power terminal equipment and the optimal transmitting power for safe unloading are obtained, the safe transmission of the power service is completed, the calculation and communication resources of the power terminal equipment are optimized, and the secrecy capacity and the safety of the system are improved.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com