Power service secure transmission method and system based on edge calculation
An edge computing and power business technology, applied in transmission systems, transmission monitoring, information technology support systems, etc., can solve problems such as low data security, optimize computing and communication resources, and improve confidentiality capacity and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
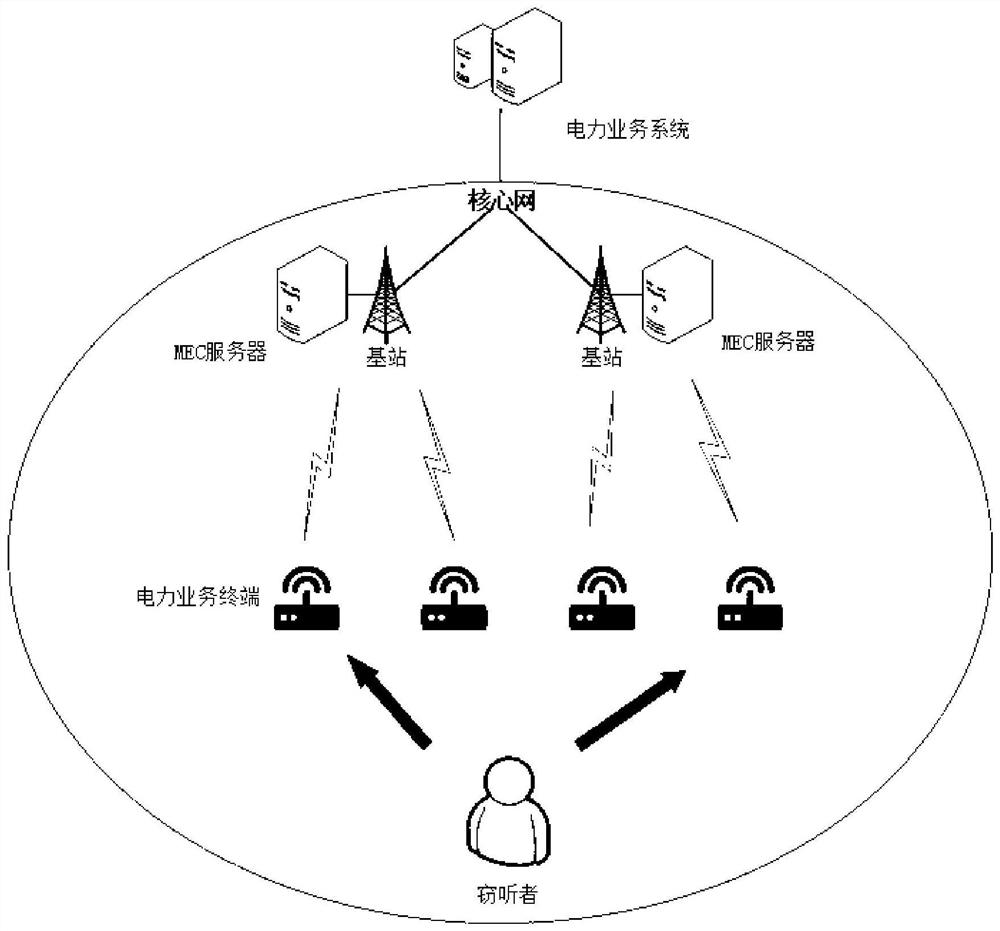
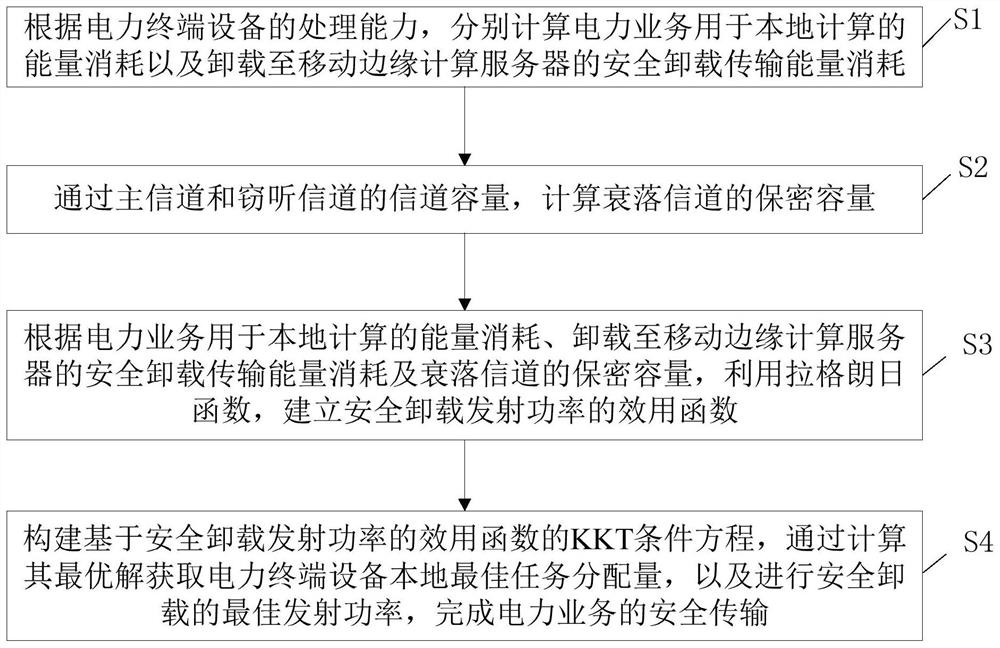
[0050]An edge computing-based secure power service transmission method provided by an embodiment of the present invention is suitable for 5G communication networks, such as figure 1 As shown, the method is based on the physical layer security policy system model of power Internet of Things edge computing, which consists of a business system layer, a base station equipped with a mobile edge computing server, multiple power terminal devices, and an eavesdropper. Such as figure 2 shown, including the following steps:
[0051] Step S1: According to the processing capability of the power terminal equipment, calculate the energy consumption of the power service for local computing and the energy consumption of safe offloading transmission offloaded to the mobile edge computing server.
[0052] In the embodiment of the present invention, each power terminal device needs to perform at least one task within a period of time, and its task can be represented by a binary parameter A=(I,...
Embodiment 2
[0092] An embodiment of the present invention provides a power service security transmission system based on edge computing. The system is based on a physical layer security policy system model of power Internet of Things edge computing. It consists of a business system layer, a base station equipped with a mobile edge computing server, and multiple A power terminal device and an eavesdropper, such as Figure 5 As shown, the system includes:
[0093] The energy consumption calculation module 1 is used to separately calculate the energy consumption of the power service for local calculation and the energy consumption of safe offloading transmission offloaded to the mobile edge computing server according to the processing capability of the power terminal equipment; this module executes the steps in Embodiment 1 The method described in S1 will not be repeated here.
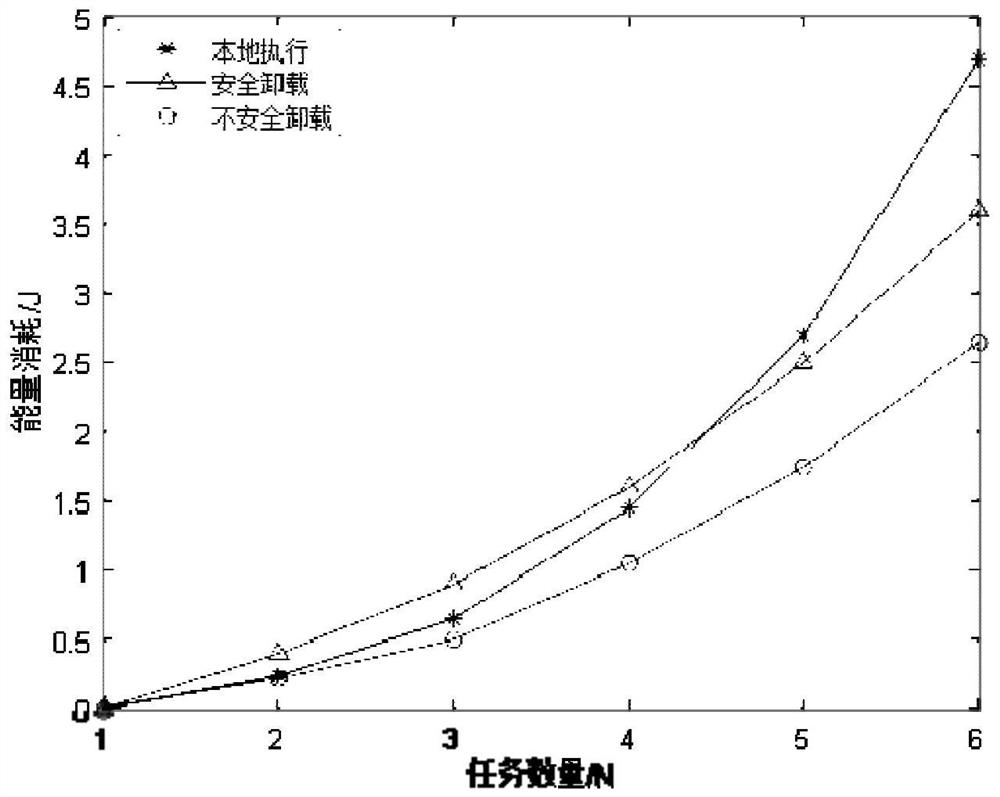
[0094] The secrecy capacity calculation module 2 is used to calculate the secrecy capacity of the fading channel ...
Embodiment 3
[0099] An embodiment of the present invention provides a terminal, such as Image 6 As shown, it includes: at least one processor 401 , such as a CPU (Central Processing Unit, central processing unit), at least one communication interface 403 , memory 404 , and at least one communication bus 402 . Wherein, the communication bus 402 is used to realize connection and communication between these components. Wherein, the communication interface 403 may include a display screen (Display) and a keyboard (Keyboard), and the optional communication interface 403 may also include a standard wired interface and a wireless interface. The memory 404 may be a high-speed RAM memory (Random Access Memory, volatile random access memory), or a non-volatile memory (non-volatile memory), such as at least one disk memory. Optionally, the memory 404 may also be at least one storage device located away from the aforementioned processor 401 . The processor 401 may execute the edge computing-based s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com