Multi-relay physical layer safety method based on known eavesdropping end channel information
A technology of physical layer security and channel information, which is applied in the field of multi-relay physical layer security, can solve the unrealistic problems of installing multiple antennas, and achieve the effect of maximizing the security capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
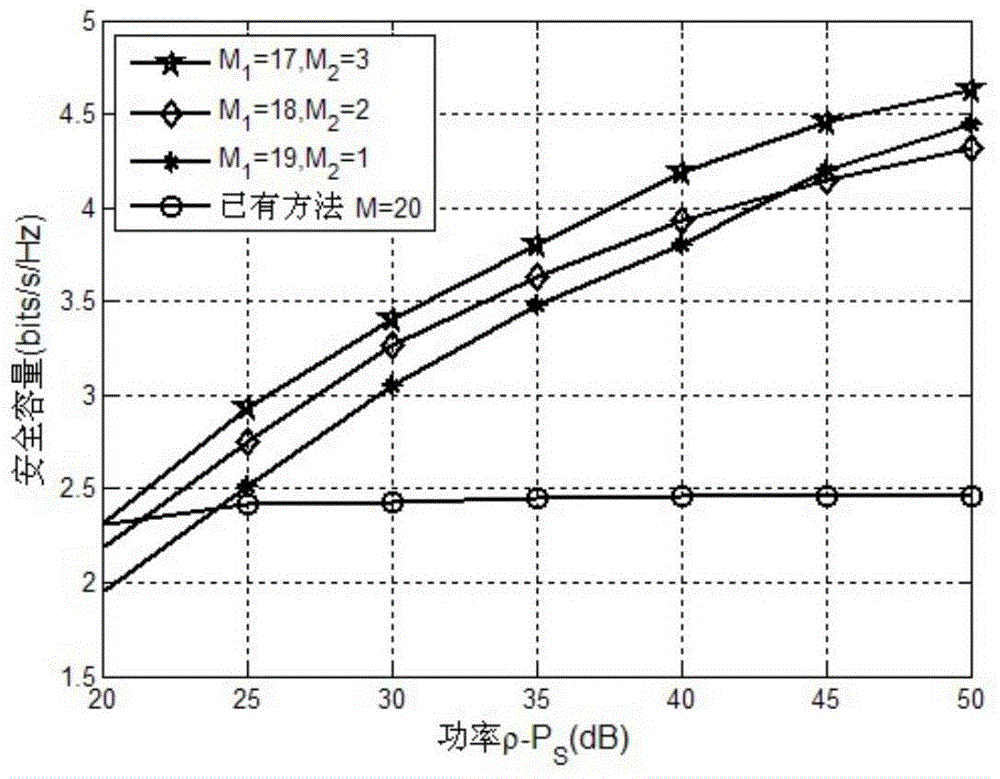
[0019] Based on the research on the security problem of the physical layer, the present invention proposes a physical layer security method based on a multi-relay multi-interference network with known eavesdropping terminal channel information. In this method, the relay node group is divided into a relay forwarding group and an interference group. On the premise of ensuring the maximum degree of freedom of the system, the beamforming vectors of the relay forwarding node group and the interference node group are optimized to maximize The secrecy capacity of the system. Then, the optimal relay power allocation scheme is calculated to maximize the system secrecy capacity.
[0020] The present invention will be further described below in conjunction with specific examples (but not limited to this example) and accompanying drawings.
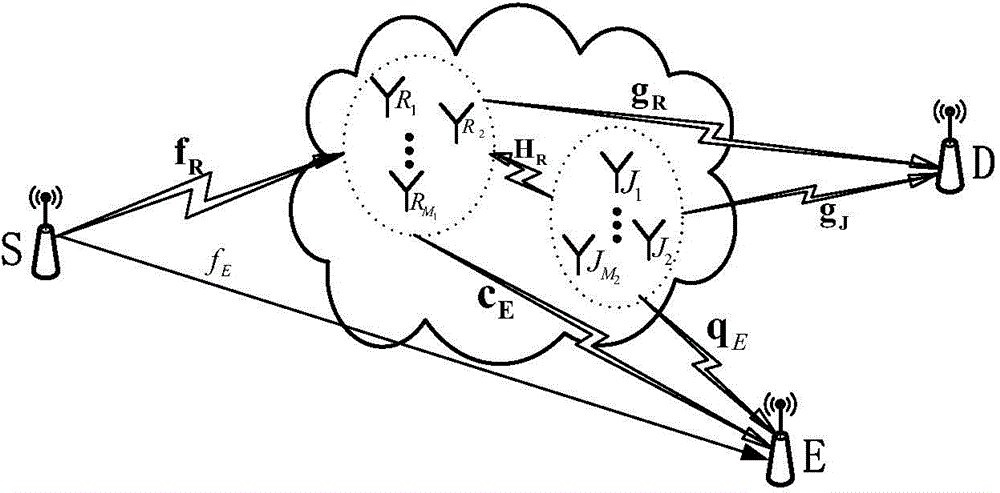
[0021] as attached figure 1 As shown, the system model is a eavesdropping network with multiple relays and multiple interferences. The network con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com