User behavior abnormity detection method and device, electronic equipment and readable storage medium
An anomaly detection and user technology, applied in the field of detection, can solve problems such as difficult verification, low efficiency of investigation, and difficulty in obtaining real feedback.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
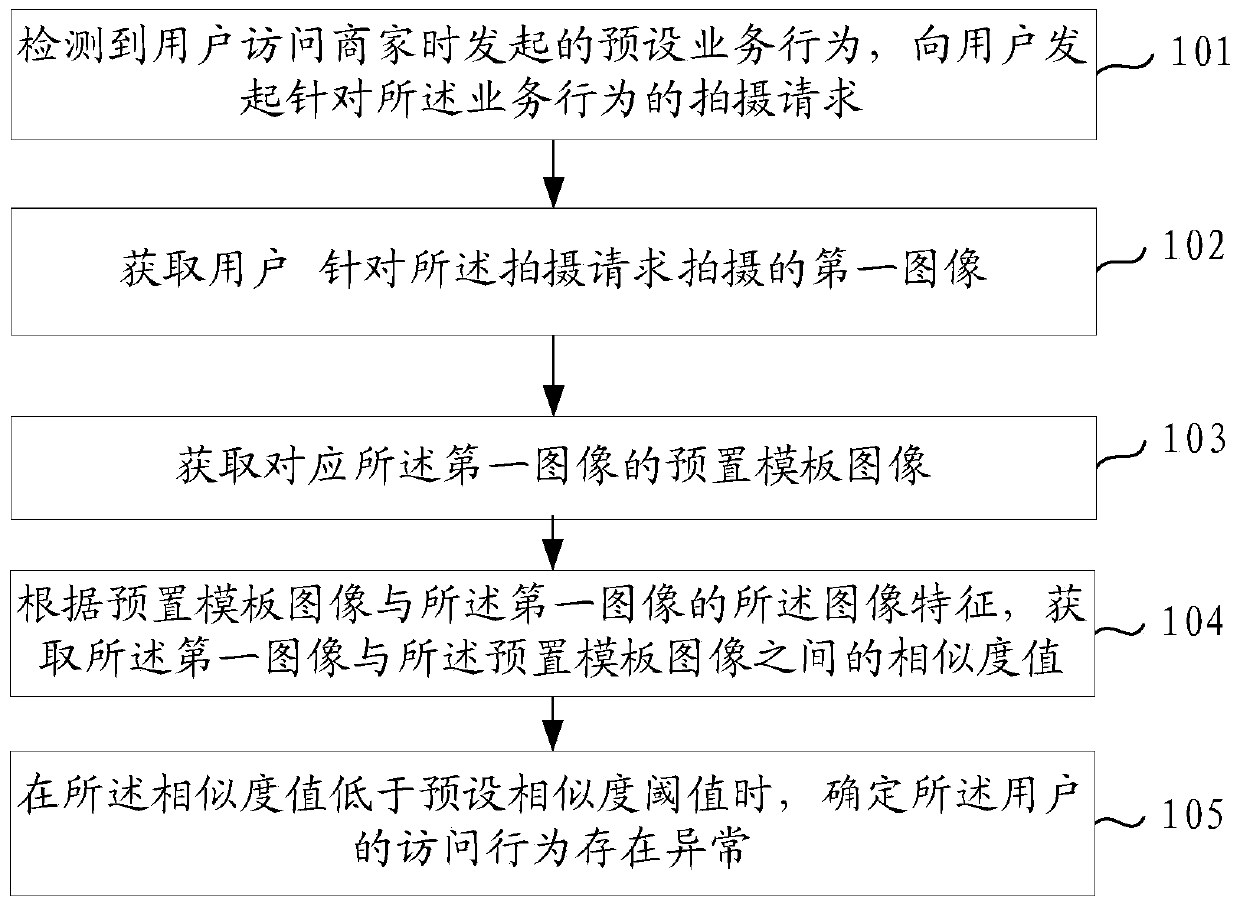
[0029] refer to figure 1 , which shows a flow chart of the steps of the method for detecting abnormal user behavior in one embodiment of the present disclosure, including:
[0030] Step 101: Detecting a preset business behavior initiated when a user visits a store, and initiating a photographing request for the business behavior to the user.
[0031] In the embodiment of the present disclosure, in the scenario of authenticity detection of the user's visit to the store, when the user goes to the store to perform business operations, the store visit behavior verification task can be issued to the user through the application platform, and the verification task requests the user to take an image of a specified scene in the store Data, for example, when the user goes to the store to place an order, pay, and evaluate operations, a request is sent to the user to capture real image data corresponding to the order, payment, and evaluation object, and the user can take pictures accordi...
Embodiment 2
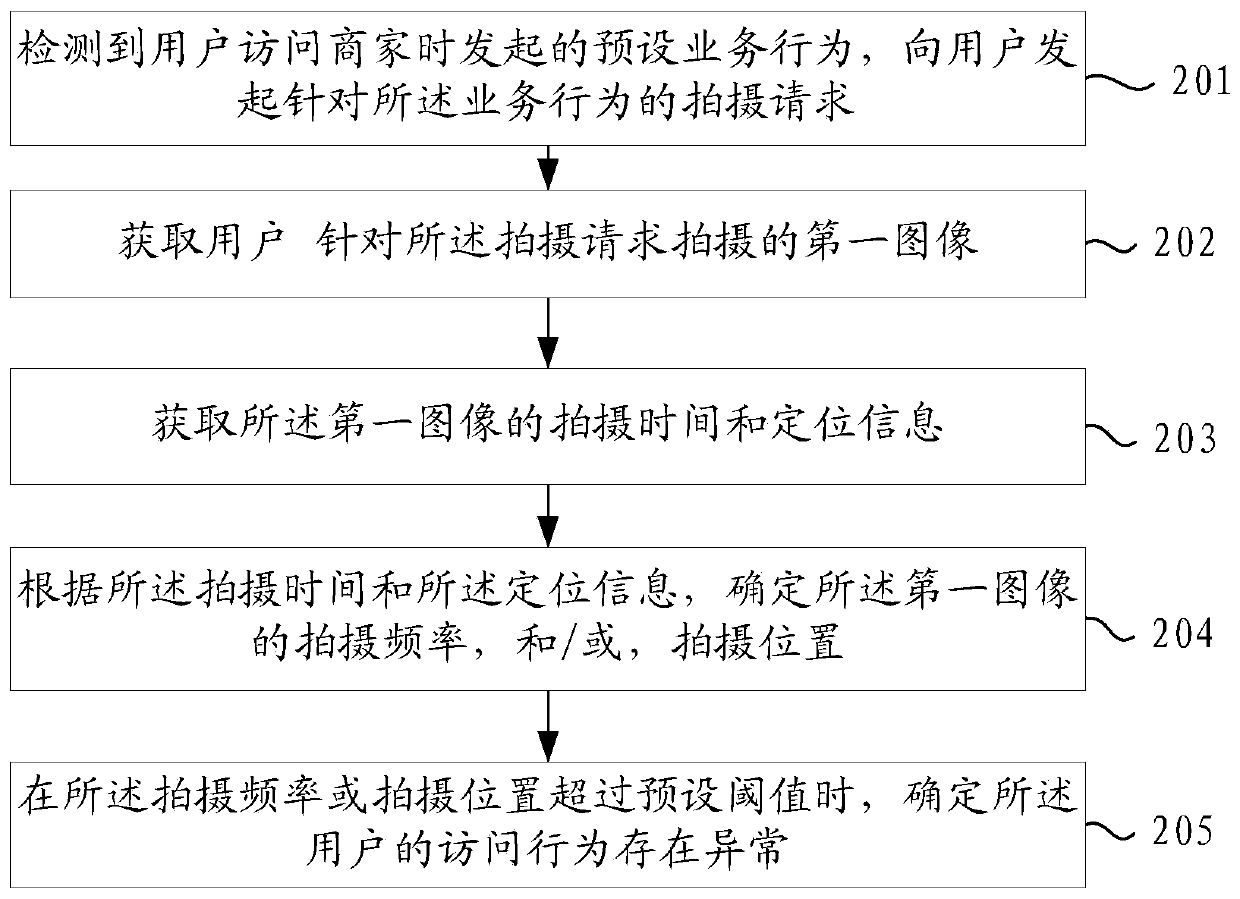
[0081] refer to figure 2 , which shows a flowchart of steps of a method for detecting abnormal user behavior in another embodiment of the present disclosure, specifically as follows.
[0082] Step 201, detecting the preset business behavior initiated by the user when visiting the merchant, and initiating a photographing request for the business behavior to the user;
[0083] This step is the same as step 101 and will not be described in detail here.
[0084] Step 202, acquiring the first image taken by the user according to the shooting request;
[0085] This step is the same as step 102 and will not be described in detail here.
[0086] Step 203, acquiring the shooting time and location information of the first image.
[0087] In the embodiment of the present disclosure, the geographic location where the first image is shot is determined through the positioning information in the image meta information, and secondly, the shooting time information in the image meta informa...
Embodiment 3
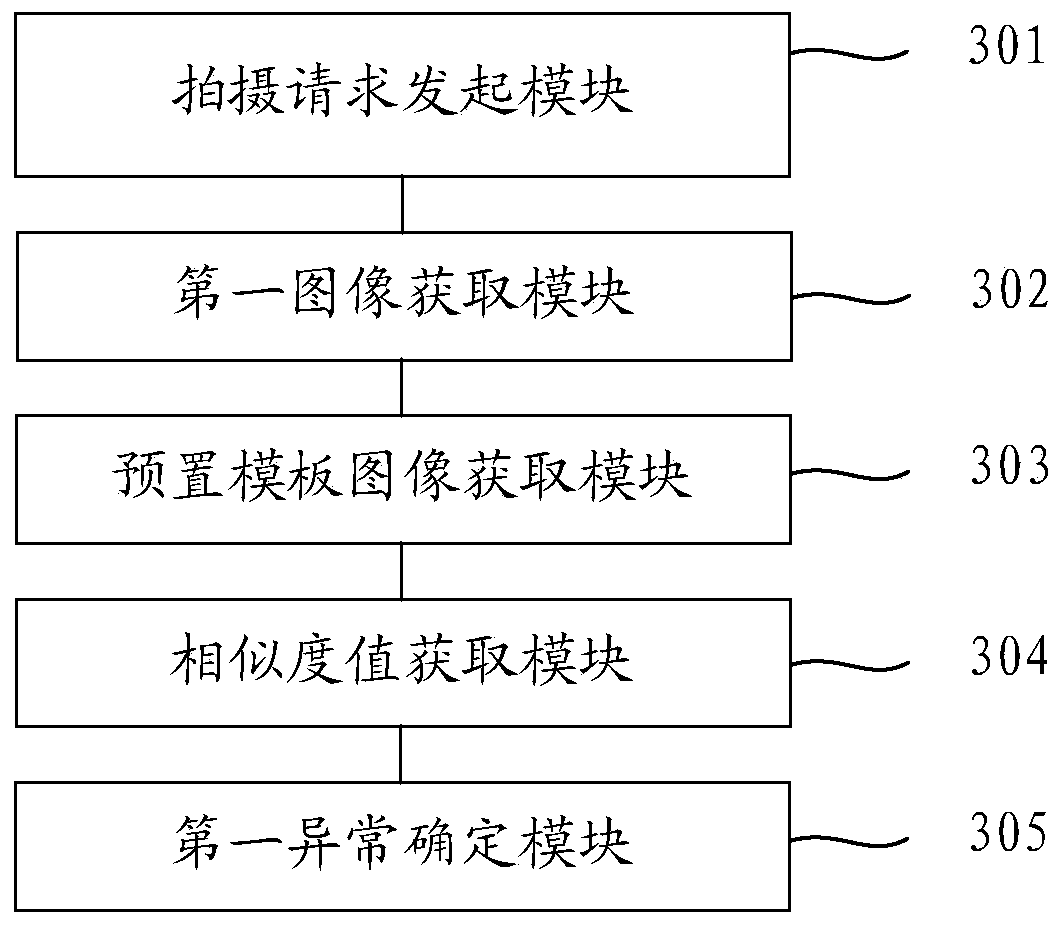
[0121] refer to image 3 , which shows a structural diagram of an apparatus for detecting abnormal user behavior in an embodiment of the present disclosure, specifically as follows.
[0122] A shooting request initiating module 301, configured to detect a preset business behavior initiated when a user visits a merchant, and initiate a shooting request for the business behavior to the user;
[0123] A first image acquisition module 302, configured to acquire a first image captured by the user according to the shooting request;
[0124] A preset template image acquisition module 303, configured to acquire a preset template image corresponding to the first image;
[0125] A similarity value acquisition module 304, configured to acquire a similarity value between the first image and the preset template image according to the image features of the preset template image and the first image;
[0126] Preferably, the similarity value acquisition module 304 includes:
[0127] The fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com