A tamper-proof timing data confidential transmission method based on blockchain smart contract
A technology of smart contracts and data confidentiality, applied in the field of blockchain, it can solve the problems of inability to deal with replacement attacks and excessive deposit of the middleman
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further explained below in conjunction with accompanying drawing and specific embodiment:
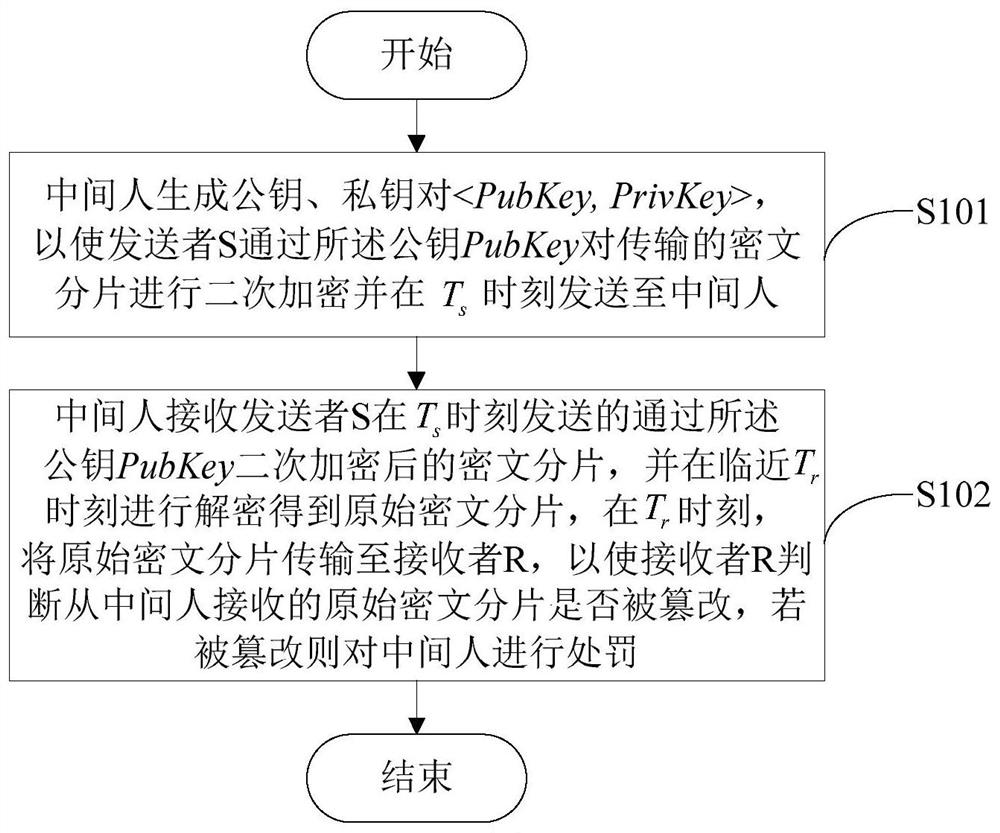
[0049] Such as figure 1 As shown, a tamper-proof timing data confidential transmission method based on blockchain smart contracts includes the following steps:
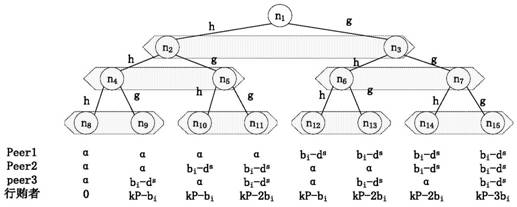
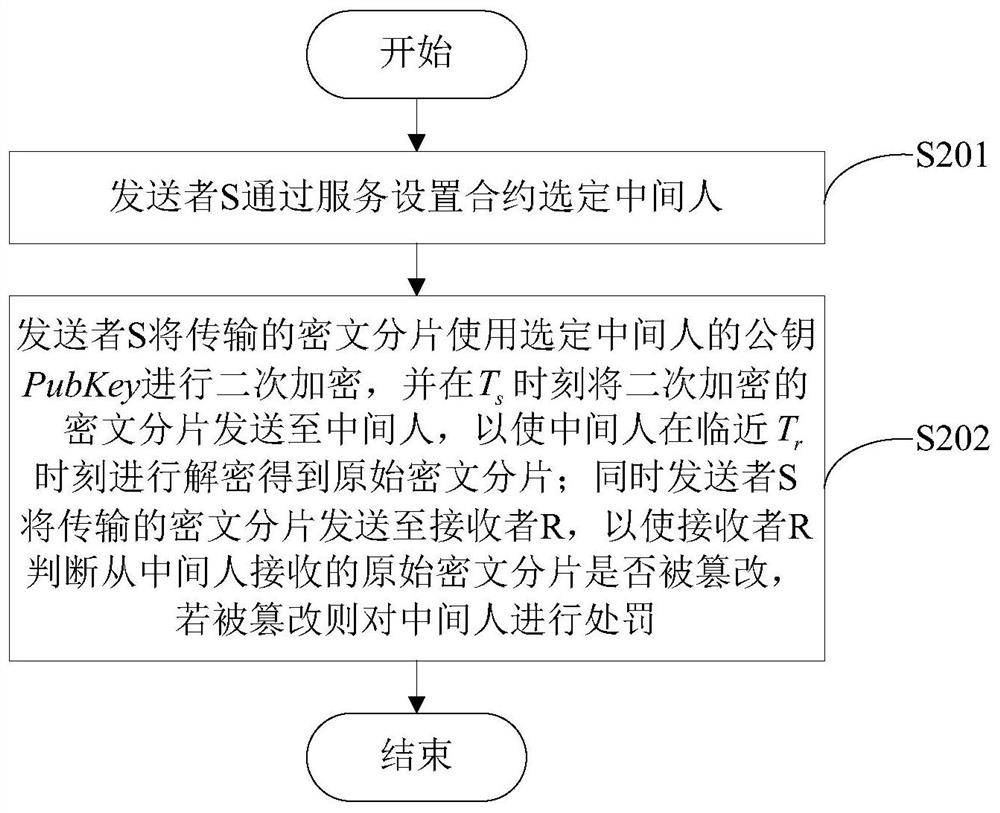
[0050] Step S101: The intermediary generates a public key and private key pair , so that the sender S uses the public key PubKey to perform secondary encryption on the transmitted ciphertext fragment and s It is sent to the intermediary at all times; the intermediary is generated by calling the intermediary registration contract registration on the network node on the public blockchain;
[0051] The intermediary registration contract enables any node in a public blockchain network to register as an intermediary. When a node registers as an intermediary, it needs to submit a part of funds as its own credit support, and this fund is recorded as d. At the same time, the intermediary needs to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com