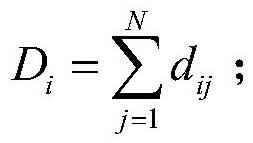A Network Intrusion Detection Method Based on Dynamic Adaptive Clustering Using Inflection Point Radius
A technology of network intrusion detection and dynamic self-adaptation, applied in the field of network security, can solve problems such as low detection accuracy and inability to accurately train intrusion detection models, achieve excellent detection ability and stability, ensure full coverage, and full inspection capabilities high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
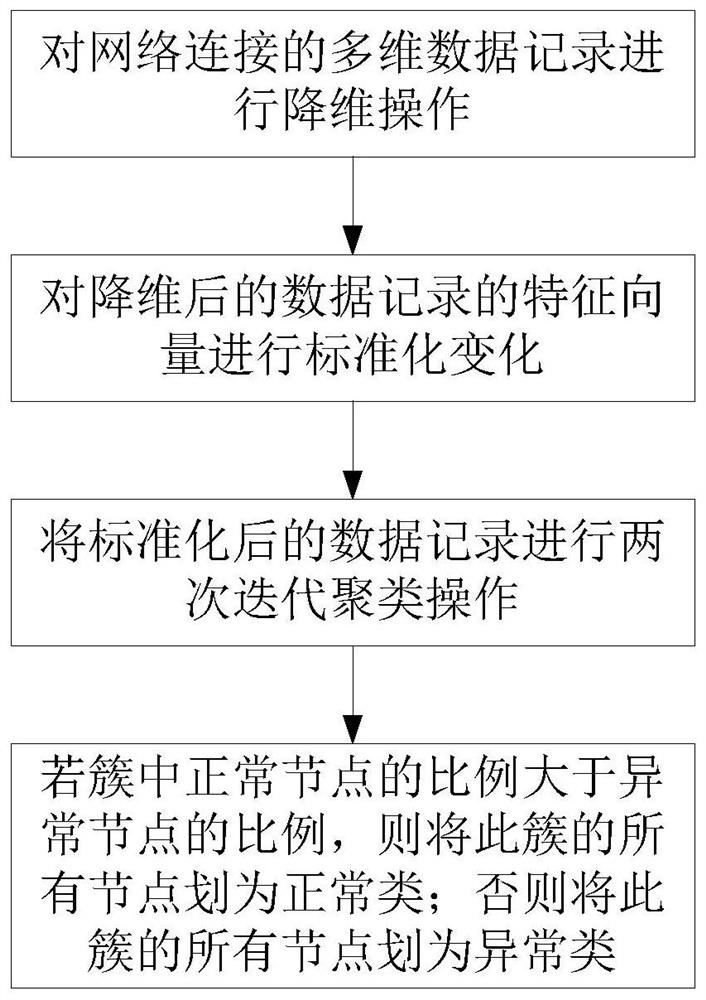
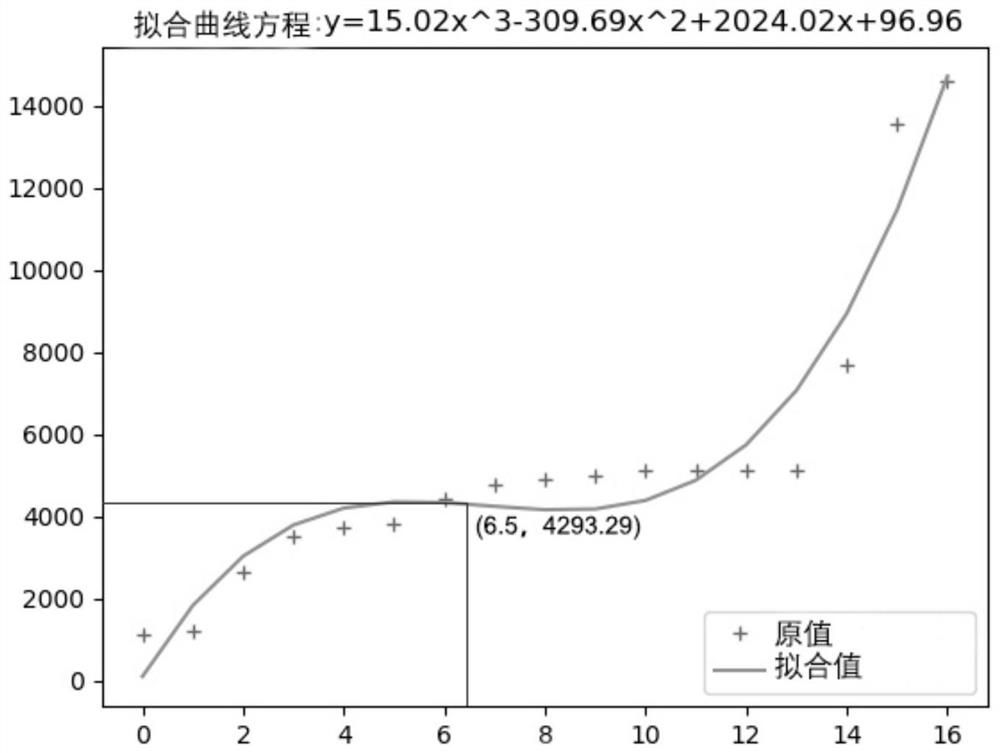
[0047] With the increasing frequency of network attacks, there are loopholes in traditional security protection products. Network intrusion detection, as an important protection method for information network security, can make up for the lack of firewalls and provide effective network security protection measures.
[0048]For the supervised algorithm, which relies heavily on the training data set, it has a strong ability to detect known intrusion behaviors, but it has a poor ability to detect unknown intrusion behaviors. Its application ability in actual intrusion detection is not comprehensive enough, and its applicability is not strong. For unsupervised algorithms, when they are applied to intrusion detection, in order to improve the detection rate and clustering accuracy, it is often necessary to remove outliers before performing empirical tuning (such as Kmeans algorithm and DBSCAN algorithm). It consumes a lot of cost in the optimization process of the clustering model, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com