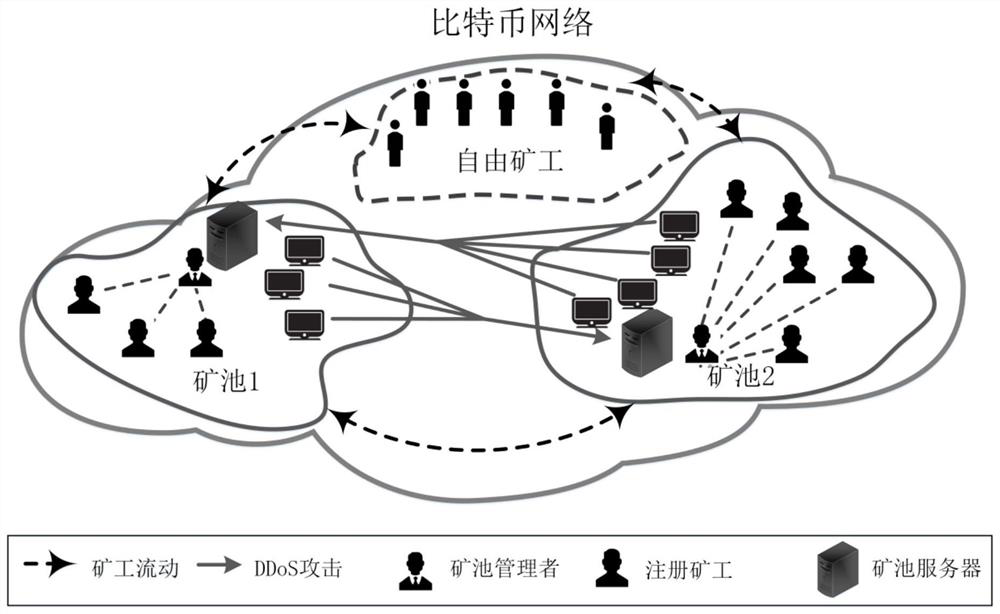
A Study Method of Bitcoin Mining Pool Attack Strategy Based on Stochastic Game Reinforcement Learning
A technology of enhanced learning and policy learning, applied in machine learning, digital transmission systems, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment specific Embodiment approach
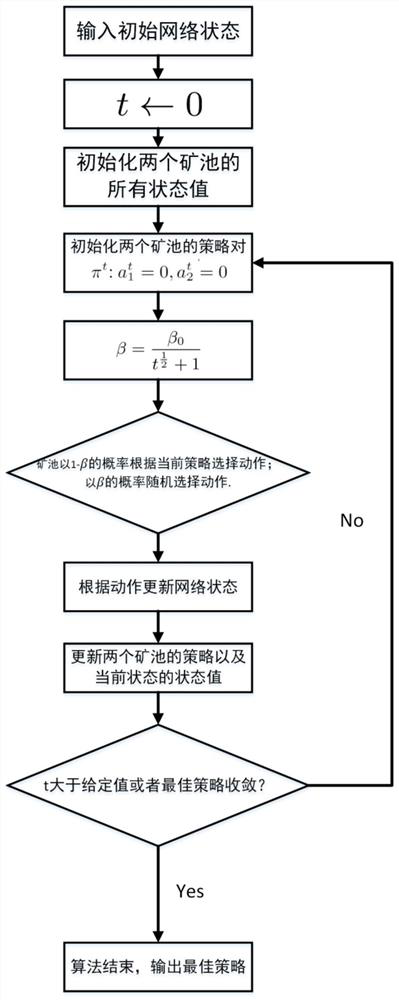
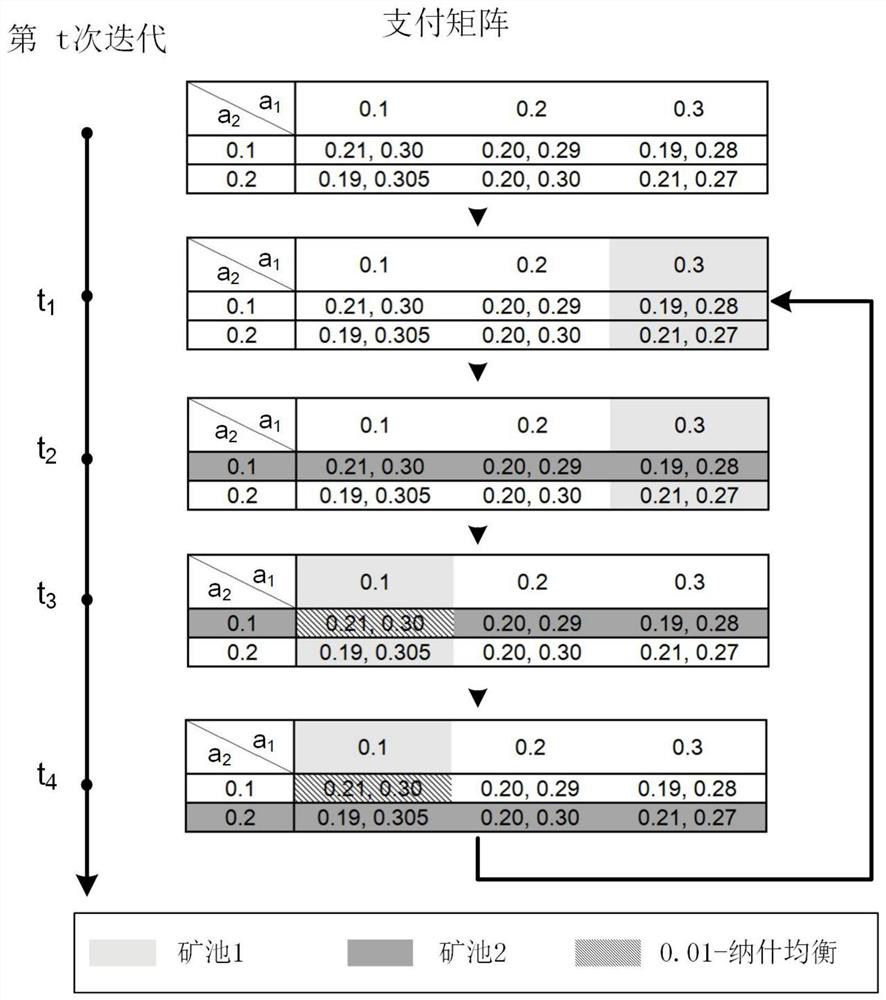
[0078] Figure 4 shows a simplified example of the process of finding an approximate Nash equilibrium to obtain an approximate optimal strategy pair for this iteration. The figure shows the payoff matrix when the two mining pools take different actions. Assuming ò = 0.01, then the approximate optimal action in state s eventually converges to last pair best policy pair in current state The action selection strategy is updated.
[0079] Step 6, according to Update the state value V of mining pool 1 in state s 1 t+1 (s); according to Update the state value of mining pool 2 in state s Where δ∈[0,1) is the learning rate of the mining pool, and in the tth iteration, the size is δ decreases as the number of iterations increases, which is helpful for the convergence of the algorithm in the later stage.
[0080] The concrete implementation process of embodiment is as follows:
[0081] The state value is the benefit in different states. Suppose the initial state of mini...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com