A vehicle Ethernet information security protection method
An information security and Ethernet technology, applied in the field of Ethernet information security protection, can solve the problems that vehicle Ethernet information security cannot be guaranteed, system functions are easily affected, and communication messages are easy to leak.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
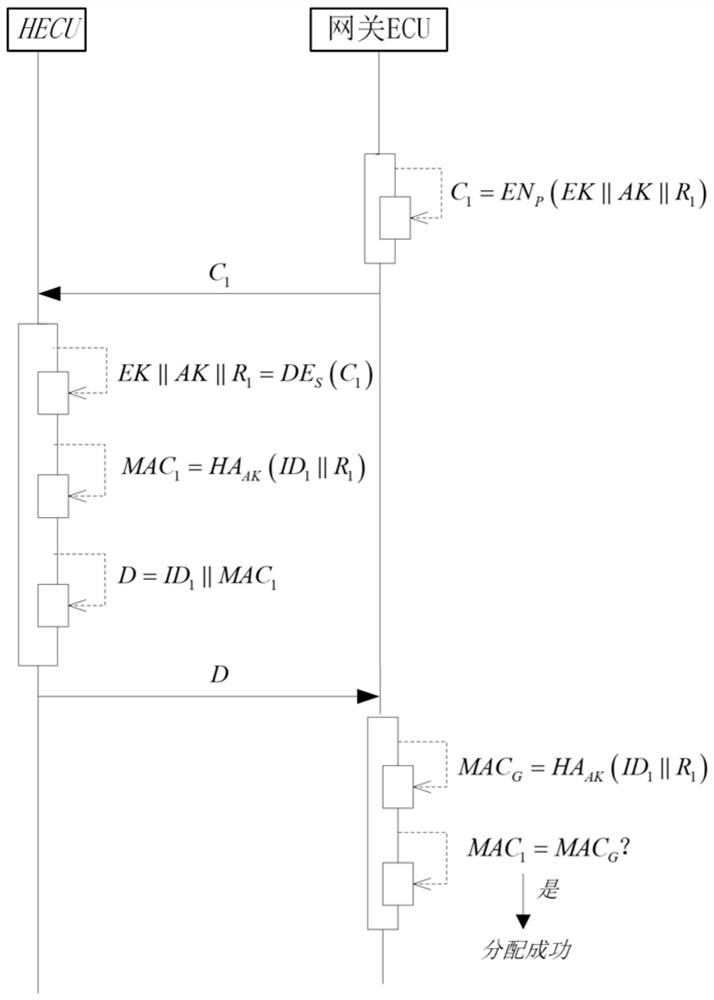
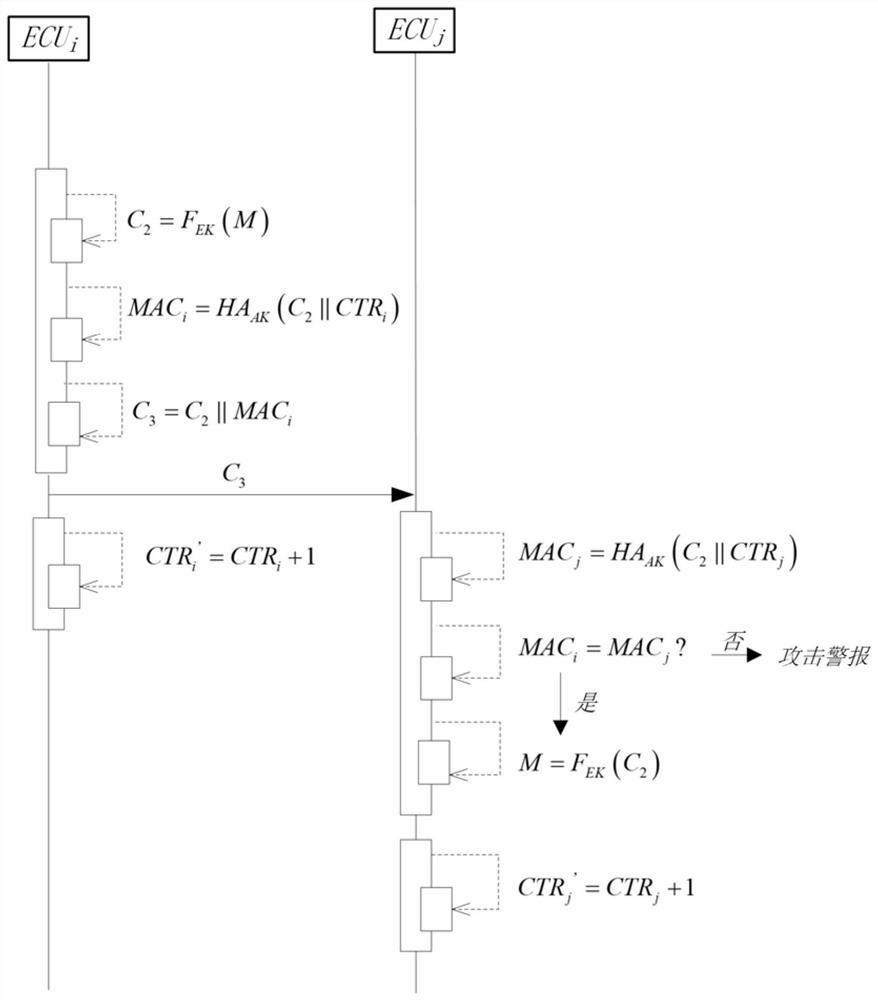
[0051] The technical scheme that the present invention adopts is, comprises the following parts:
[0052] The first part: key distribution, the gateway ECU has a set of digital certificates, which contains the identity, public key and private key of each legal ECU in the network, and at the same time, the gateway ECU has the encryption key EK and authentication key AK required for communication , in the startup phase, the gateway ECU distributes encryption keys and authentication keys to each legal ECU in the network in sequence;
[0053] The second part: secure communication, after the key distribution process in the start-up phase is completed, each legal ECU in the network already has an encryption key and an authentication key, so that the messages during the normal driving of the vehicle can be encrypted, decrypted and authenticated operate;
[0054] In the first part, the gateway ECU distributes keys for the HECU, and the HECU represents any legal ECU in the network, su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com