Communication encryption verification method, device, computer equipment and storage medium
A verification method and computer technology, which are applied in the field of communication security, can solve the problems of judging the encryption status of the inability to communicate, and achieve the effect of accurate and reliable judgment results and encryption status judgment results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0028] In order to keep the communication process confidential, some R&D personnel try to encrypt the communication process by means of national secrets, so as to ensure the security and reliability of the communication process. When studying the use of national secrets to encrypt the communication process, not only the encryption method must be studied, but also the encryption must be verified. At present, the research and development personnel indirectly check the terminal encryption status through the protocol version number, but because there is no There are public standards, and there may be misjudgments in judging only by this method.
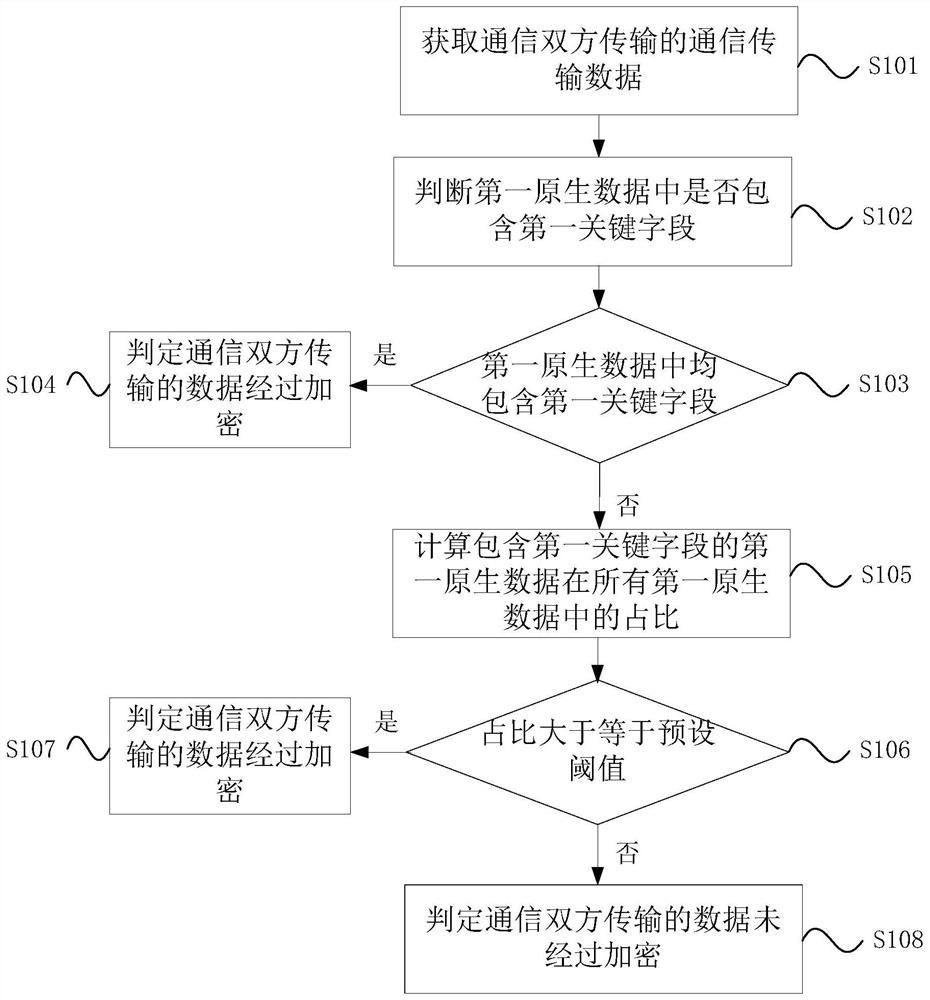
[0029] An embodiment of the present invention provides a verification method for communication encryption, such as figure 1 shown, including:
[0030] Step S101: Obtain the communication transmission data transmitted by the communication parties, where the communication transmission data is the first original data transmitted after the c...
Embodiment 2
[0061] This embodiment provides a verification device for communication encryption, such as Figure 9 shown, including:
[0062] The communication transmission data acquisition module 110 is used to acquire the communication transmission data transmitted by the communication parties. The communication transmission data is the first original data transmitted after the communication is established by the communication parties. For a detailed description, see the description of step S101 in the above-mentioned embodiment 1.
[0063] The judging module 120 is configured to judge whether the first raw data contains the first key field. For a detailed description, refer to the description of step S102 in the first embodiment above.
[0064] Encryption determination module 130, if all the first original data contains the first key field, the encryption determination module 130 is used to determine that the data transmitted by the communication parties is encrypted. For detailed descr...
Embodiment 3
[0067] An embodiment of the present invention provides a computer device, such as Figure 10 As shown, the computer device mainly includes one or more processors 31 and memory 32, Figure 10 A processor 31 is taken as an example.
[0068] The computer device may also include: an input device 33 and an output device 34 .
[0069] Processor 31, memory 32, input device 33 and output device 34 can be connected by bus or other methods, image 3 Take connection via bus as an example.
[0070]The processor 31 may be a central processing unit (Central Processing Unit, CPU). Processor 31 can also be other general processors, digital signal processor (Digital Signal Processor, DSP), application specific integrated circuit (Application Specific Integrated Circuit, ASIC), field programmable gate array (Field-Programmable Gate Array, FPGA) or Other chips such as programmable logic devices, discrete gate or transistor logic devices, discrete hardware components, or combinations of the a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com