A real-time detection system and method for cloud security incidents based on machine learning
A security event and machine learning technology, applied in the field of cross-cloud resource sharing, can solve problems such as undetectable attack types, easy means and easy hiding, etc., to facilitate log analysis, improve system analysis efficiency and analysis accuracy, and improve storage. The effect of efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
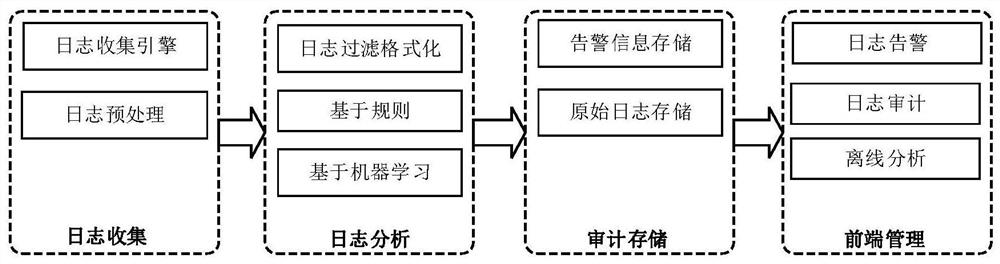
[0047] This embodiment provides a real-time detection system for cloud security events based on machine learning, including a log collection module, a log analysis module, an audit storage module and a front-end management module;
[0048] The log collection module collects logs in all cloud platforms through a log collection engine, and after log preprocessing, sends all logs to the log analysis module for unified analysis;
[0049] The log analysis module analyzes the received log data, and generates a log analysis result;
[0050] The audit storage module stores logs with large amounts of data in the distributed file system, and stores log analysis results with small amounts of data and important logs in the database;
[0051] The front-end management module displays system operation status and security events that occur.
Embodiment 2
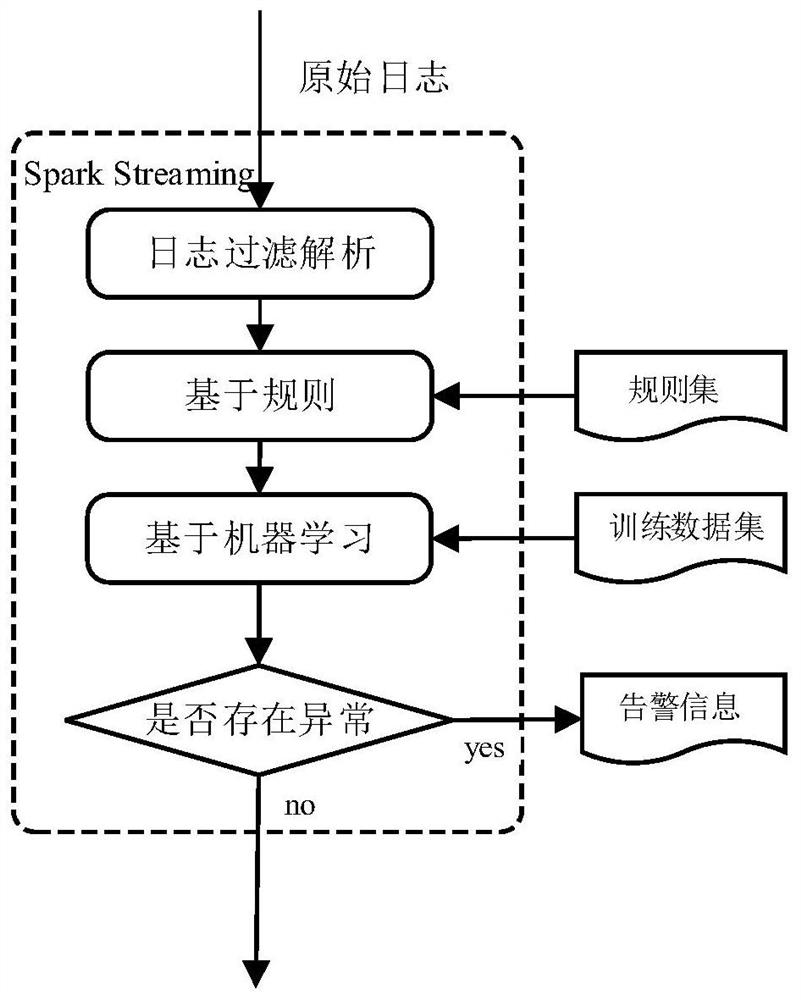
[0053] This embodiment provides a method for real-time detection of cloud security events based on machine learning, including the following steps:
[0054] S1. The log collection module sends all logs to the log analysis module for unified analysis;
[0055] S2. The log analysis module analyzes the received log data and generates a log analysis result;
[0056] S3. The audit storage module stores logs with a large amount of data in the distributed file system, and stores log analysis results with small amounts of data and important logs in the database;
[0057] S4. The front-end management module displays system operation status and security events that occur.
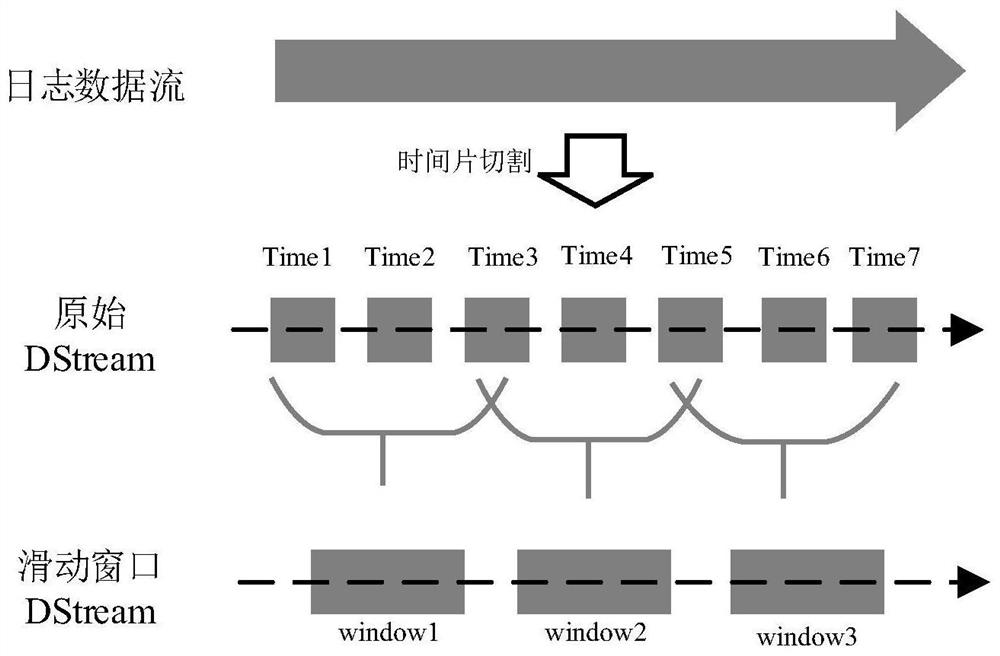
[0058] There are many types of log files in the cloud environment. First, determine which log files to collect. The log files collected by this method include instance logs, physical machine logs, system logs, audit logs, and cloud platform logs, and send these logs to a unified Log analysis module. The log collec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com