Video action recognition adversarial attack method insensitive to sampling
An action recognition and sensitive technology, applied in neural learning methods, character and pattern recognition, instruments, etc., can solve problems such as affecting attack effect, failure, loss of video timing context features, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
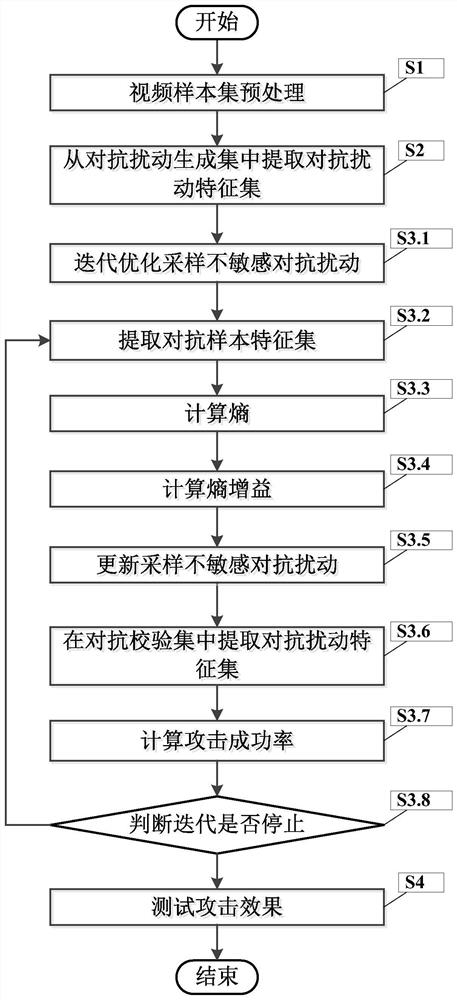
[0053] figure 1 It is a flow chart of the video action recognition confrontation attack method which is insensitive to sampling according to the present invention.
[0054] In this embodiment, as figure 1 As shown in the present invention, a sampling-insensitive video action recognition adversarial attack method includes the following steps:
[0055] S1, video sample set preprocessing
[0056] Manually divide the video sample set χ into the adversarial perturbation generation set χ 1 and the adversarial check set χ 2 , any video usually contains a large number of frames, and a few video frames are sampled to contain the patterns in the entire video, and the computational cost can be reduced. Therefore, the video needs to be sampled first, where the adversarial perturbation generation set is expressed as m 1 represents χ 1 The total number of video samples in the middle, the ith video sample X i ={x 1 ,x 2 ,…,x t ,...,x T}, x t Represents the t-th frame image, T is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com