Permission control method and device based on role and cloud function, equipment and medium
A technology of authority control and role, which is applied in the computer field, can solve problems such as limitations of authority control methods, and achieve the effect of flexible authority control methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
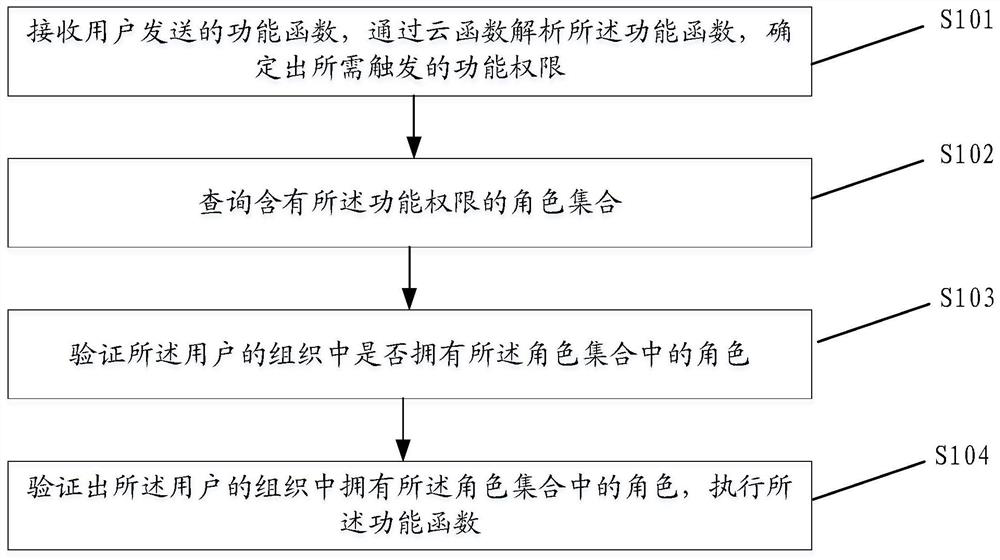
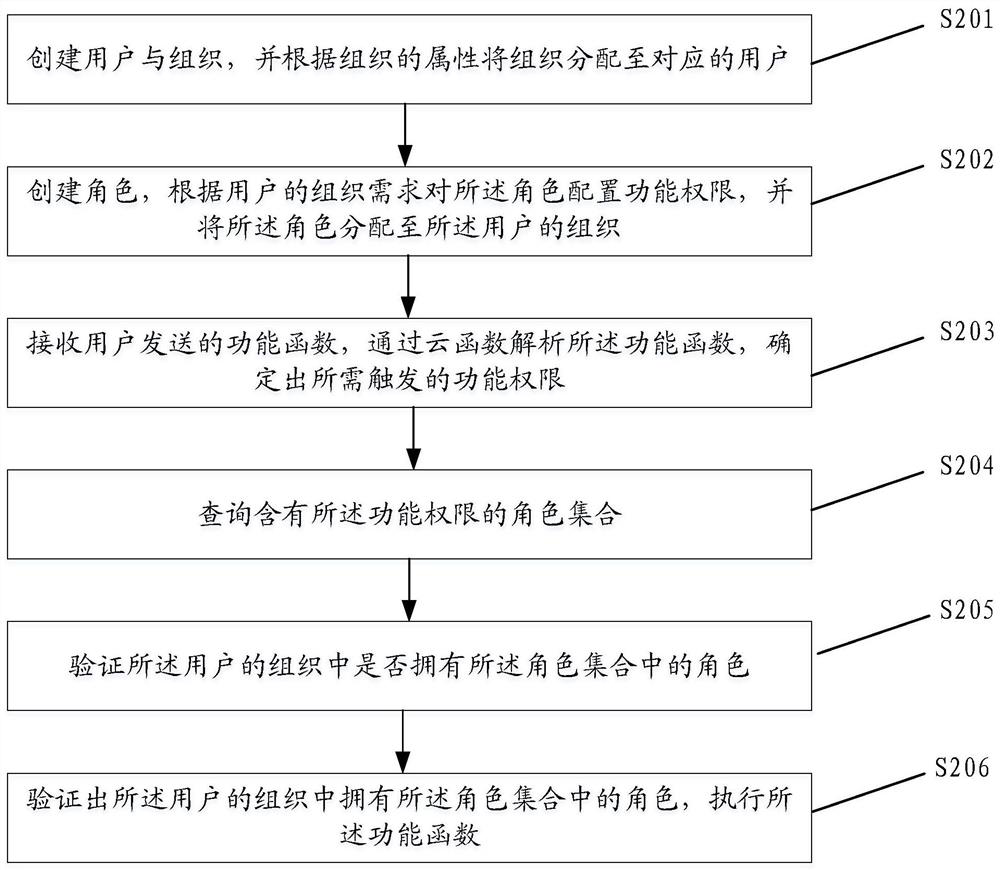
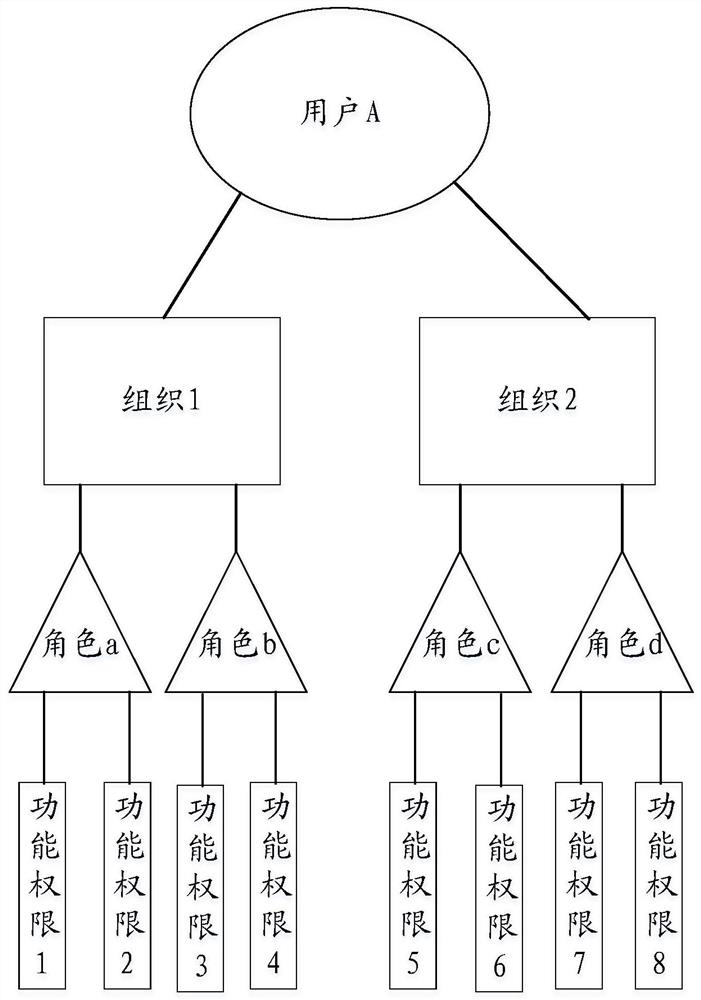
[0054] The relevant permissions of the enterprise resource planning system (ERP, Enterprise Resource Planning) are managed together with the launch of the project. Therefore, after the ERP system is launched, the control of the relevant permissions of the ERP system should be strictly formulated to ensure the security of relevant data access and Safe to operate. At the same time, different roles can be set for different corporate positions.
[0055] There are generally three types of access control methods in an enterprise environment:
[0056] 1. Autonomous access control is a control strategy that limits permissions on the basis of confirming the identity of the subject and the group to which it belongs.
[0057] 2. Mandatory authority control means that the system forces the subject to obey the authority control policy formulated in advance.
[0058] 3. Role-based authority control, mainly by dividing users into roles consistent with their organizations, to reduce the com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com