Apt network attack detection method based on meta-path learning and subgraph sampling
A network attack and detection method technology, applied in the field of network security and machine learning, can solve the problems of complex system behavior, information loss, modeling, etc., and achieve the effect of overcoming latency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below in conjunction with the accompanying drawings.
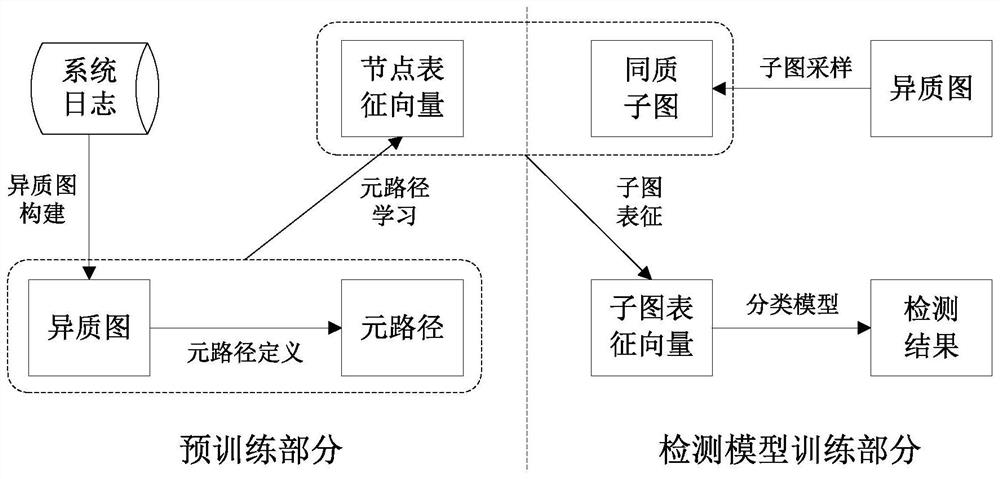
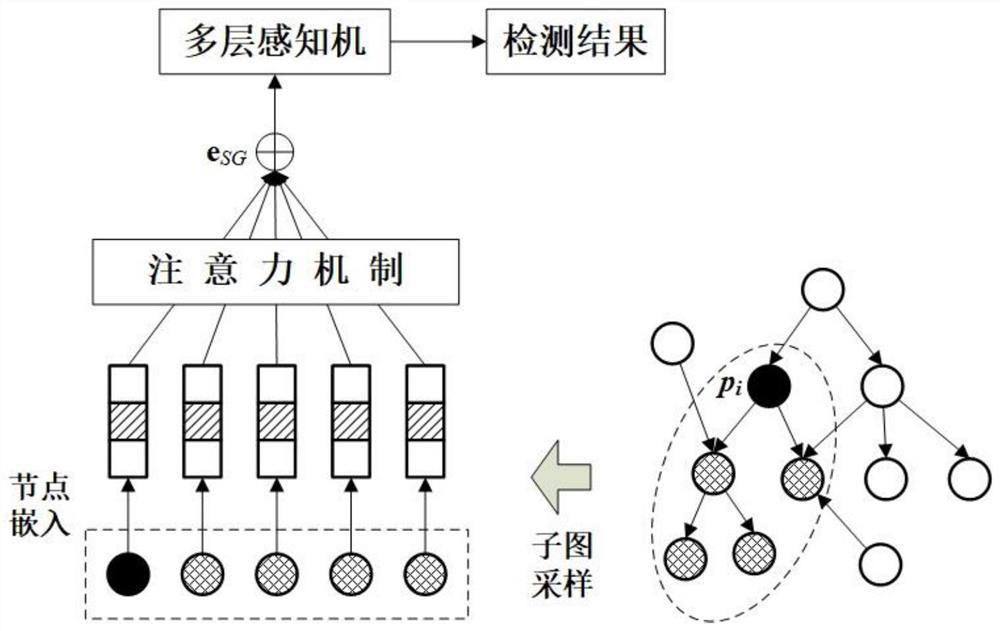
[0034] refer to Figure 1 ~ Figure 3 , an APT network attack detection method based on meta-path learning and subgraph sampling, comprising the following steps:
[0035] 1) Construction of heterogeneous graph based on log data: define system behavior involved in system log data, and build a heterogeneous graph representing system behavior on this basis;
[0036] In said step 1), the steps of building a heterogeneous graph based on log data are as follows:
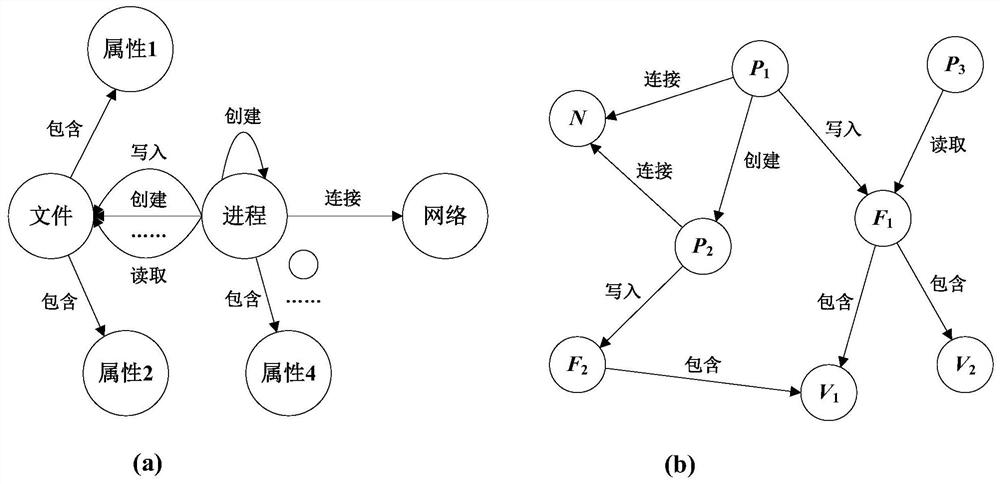
[0037] (1-1) Concept map definition: first, define node types according to the system behaviors involved in the log data, including processes, files, networks, node attributes, etc.; then, define relationship types according to the interactive behavior between nodes, including process and The derivation relationship between processes, the reading relationship between processes and files, the creation relationship ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com