Image reliability certification method based on quadtree
An authentication method and quadtree technology, which is applied in the field of image reliability authentication based on quadtree, can solve the problems of image use influence, inappropriate modification, etc., and achieve the effect of security guarantee and simple method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0017] 1. Information hiding:
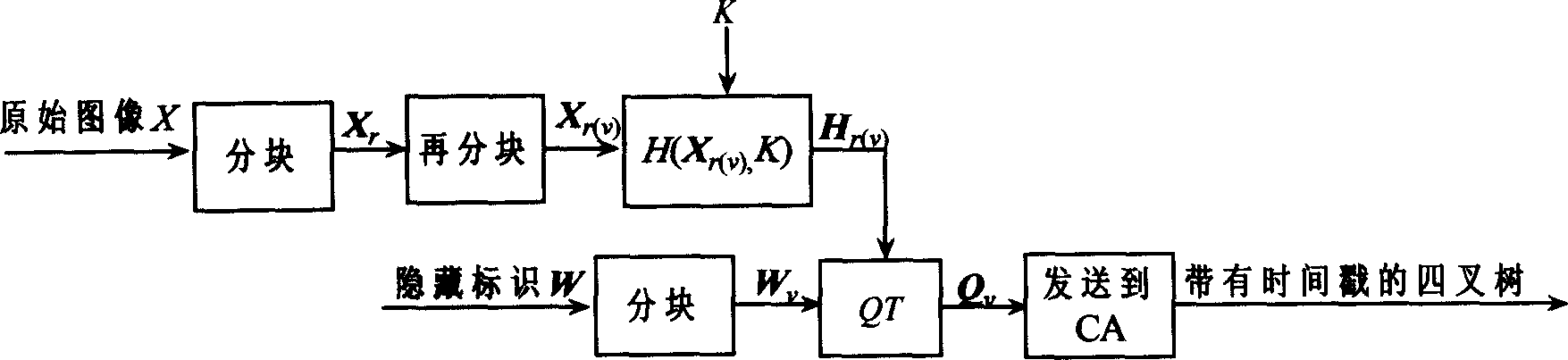
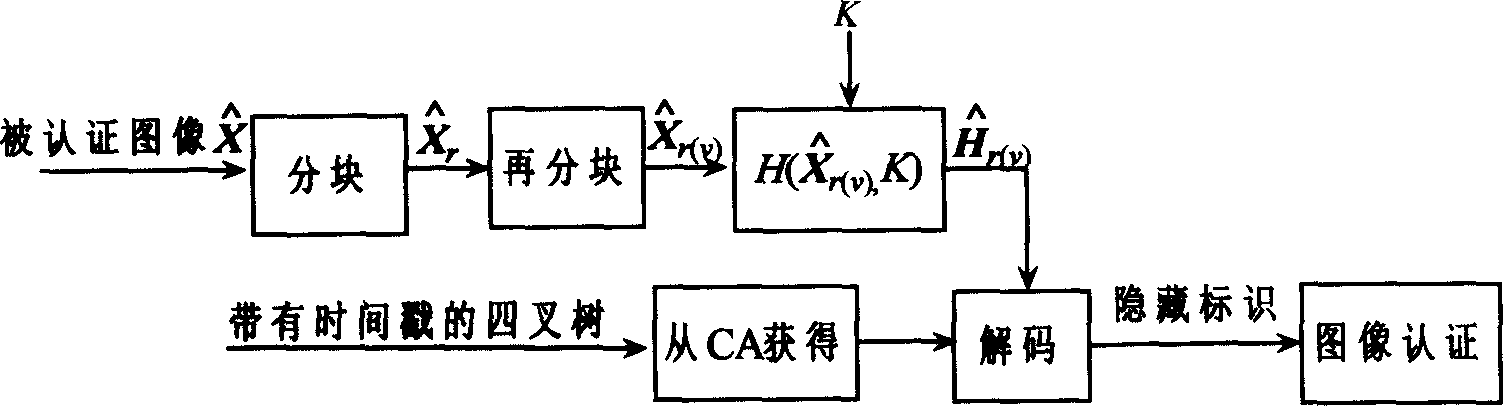
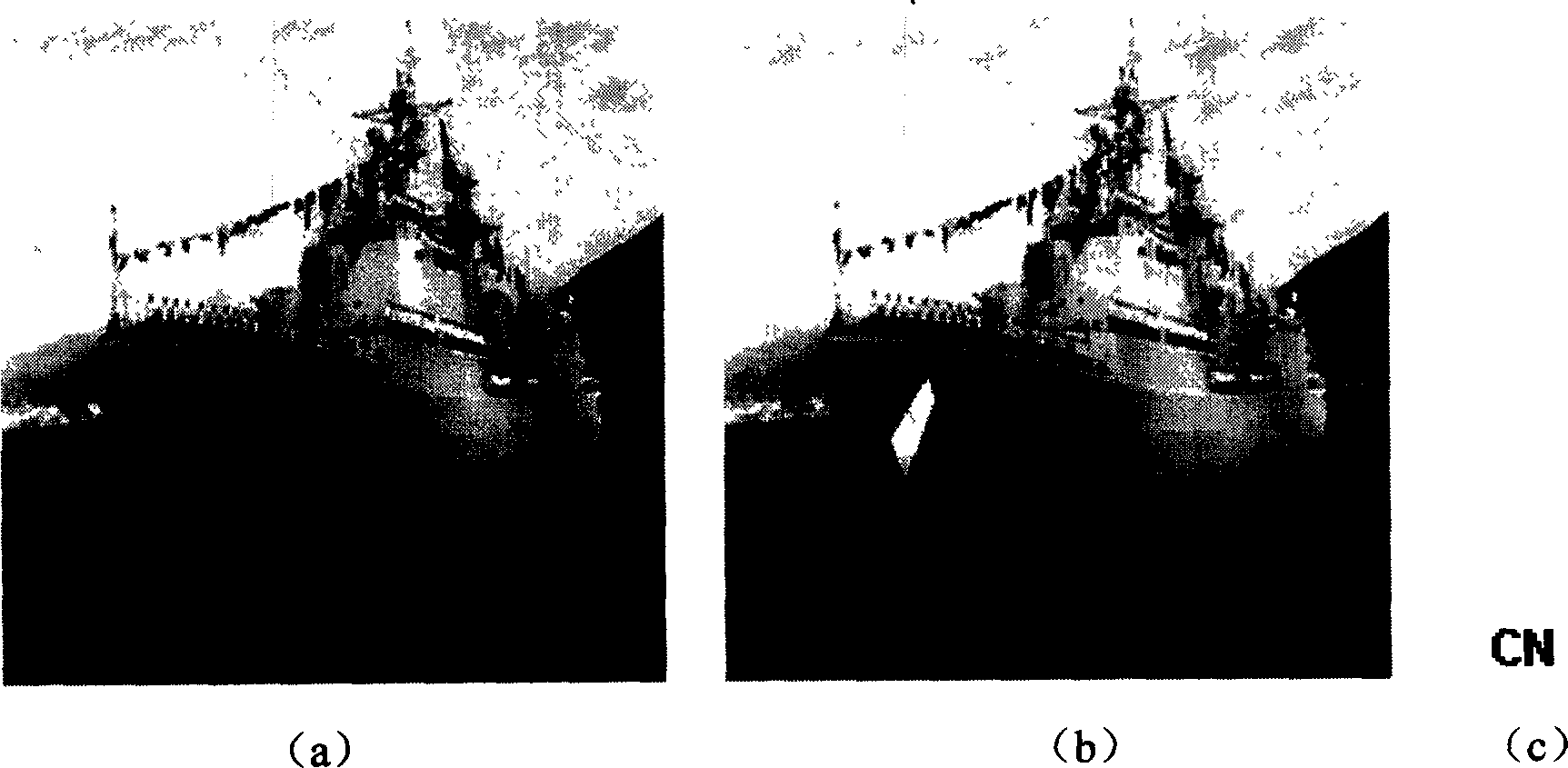
[0018] Such as figure 1 process for information hiding. Set the size to M 1 × M 2 The original image X is divided into many L 1 × L 2 (L 1 = 2 l , L 1 = 2 k , l, k=1, 2, ...) non-overlapping blocks X r (r=1, 2,..., n), the binary concealment mark W is divided into m non-overlapping blocks W v (v=1, 2, ..., m), each image block X r Divided into m smaller non-overlapping image blocks X r(v) . H( ) represents the Hash function on the password, and its output size is equal to each hidden identification block W v the size of. Calculate the Hash value of each smaller image block with the key K
[0019] h r(v) =H(X r(v) , K), (r=1,2,...,n; v=1,2,...,m)
[0020] In order to facilitate the description of the quadtree generation process, it is necessary to clarify the concept of the sim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com