Portable terminal, methods, programs and storage media for managing application start
a portable terminal and application start technology, applied in the field of portable terminals, can solve the problems of compromising security and inability to ensure the security of downloaded applications, and achieve the effect of ensuring the information security of the portable terminal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
twelfth modification
4.12: Twelfth Modification
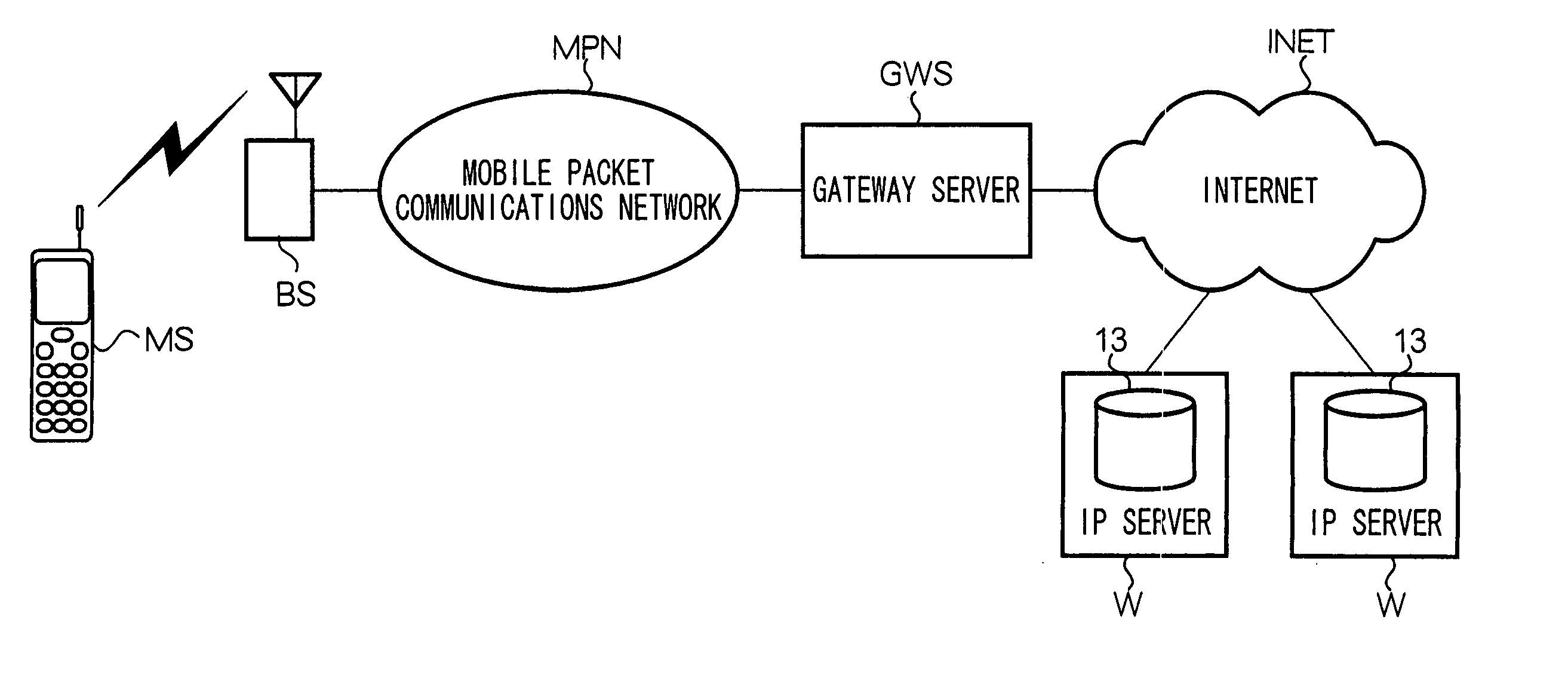
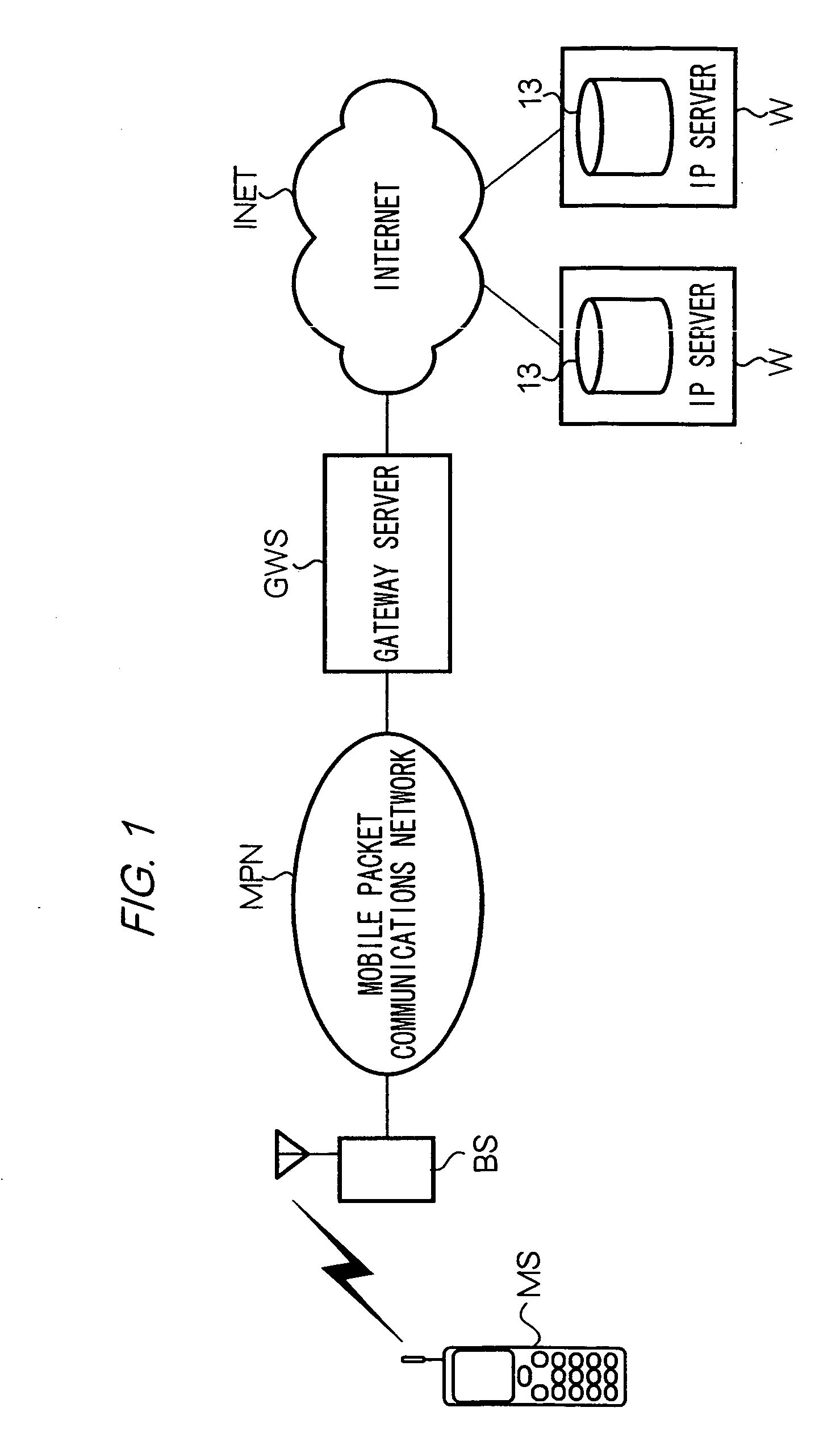
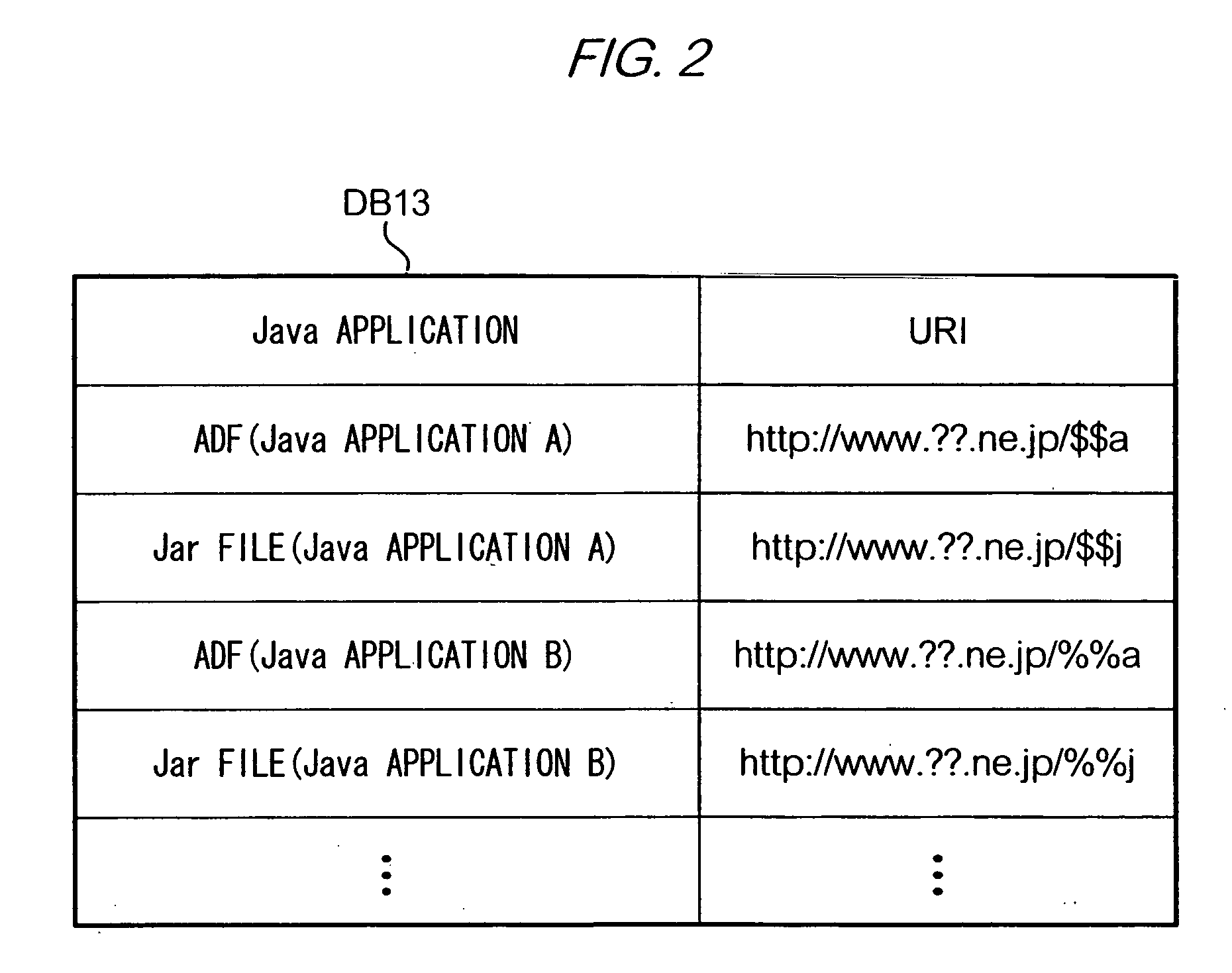
[0234] In a twelfth modification, in the ADF stored in mobile device MS, instead of trusted source data, untrusted source data is included; this data may include mail addresses or URIs that indicate untrusted data sources.
[0235] Mobile device MS decides, based on untrusted source data, whether to start another application following application specifiers included in e-mail or in HTML data, or startup instructions created by a Java application.
[0236] In other words, in the case where untrusted source data includes an e-mail transmission origin address, a HTML data transmission origin URI, or a URI of the download origin of a Java application that instructed to created startup instructions, mobile device MS does not start another Java application specified by this data.
[0237] With the twelfth modification, because the mobile device MS does perform startup of Java applications based on startup instructions or the like from sources with limited trustworthine...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com