Mechanism to provide customer vcn network encryption using customer-managed keys in network virtualization device
a virtualization device and customer technology, applied in the field of virtual cloud networks, can solve the problems of security, performance penalty, unauthorized parties not being able to view plaintext data,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028]In the following description, for the purposes of explanation, specific details are set forth in order to provide a thorough understanding of certain embodiments. However, it will be apparent that various embodiments may be practiced without these specific details. The figures and description are not intended to be restrictive. The word “exemplary” is used herein to mean “serving as an example, instance, or illustration.” Any embodiment or design described herein as “exemplary” is not necessarily to be construed as preferred or advantageous over other embodiments or designs.
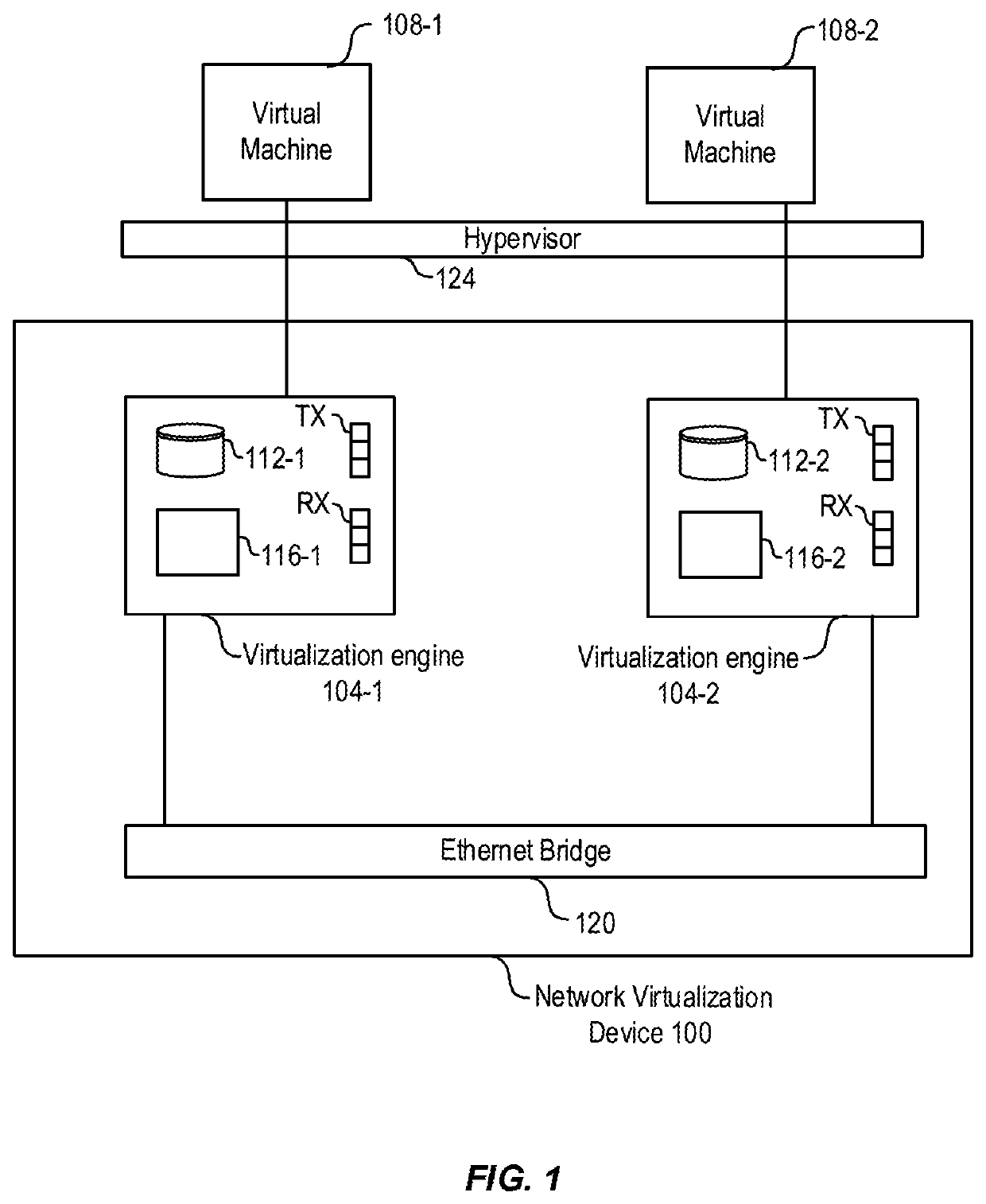
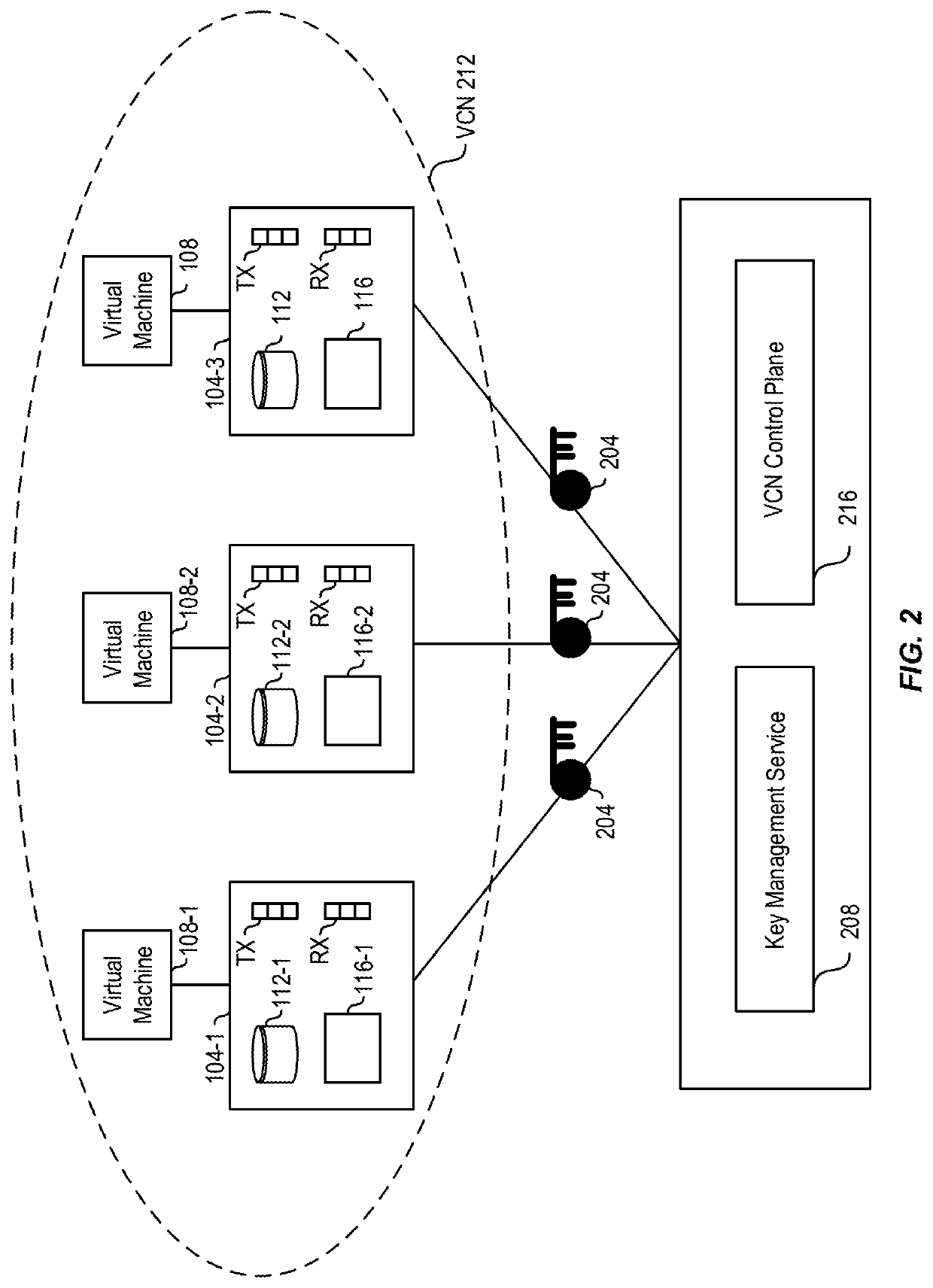
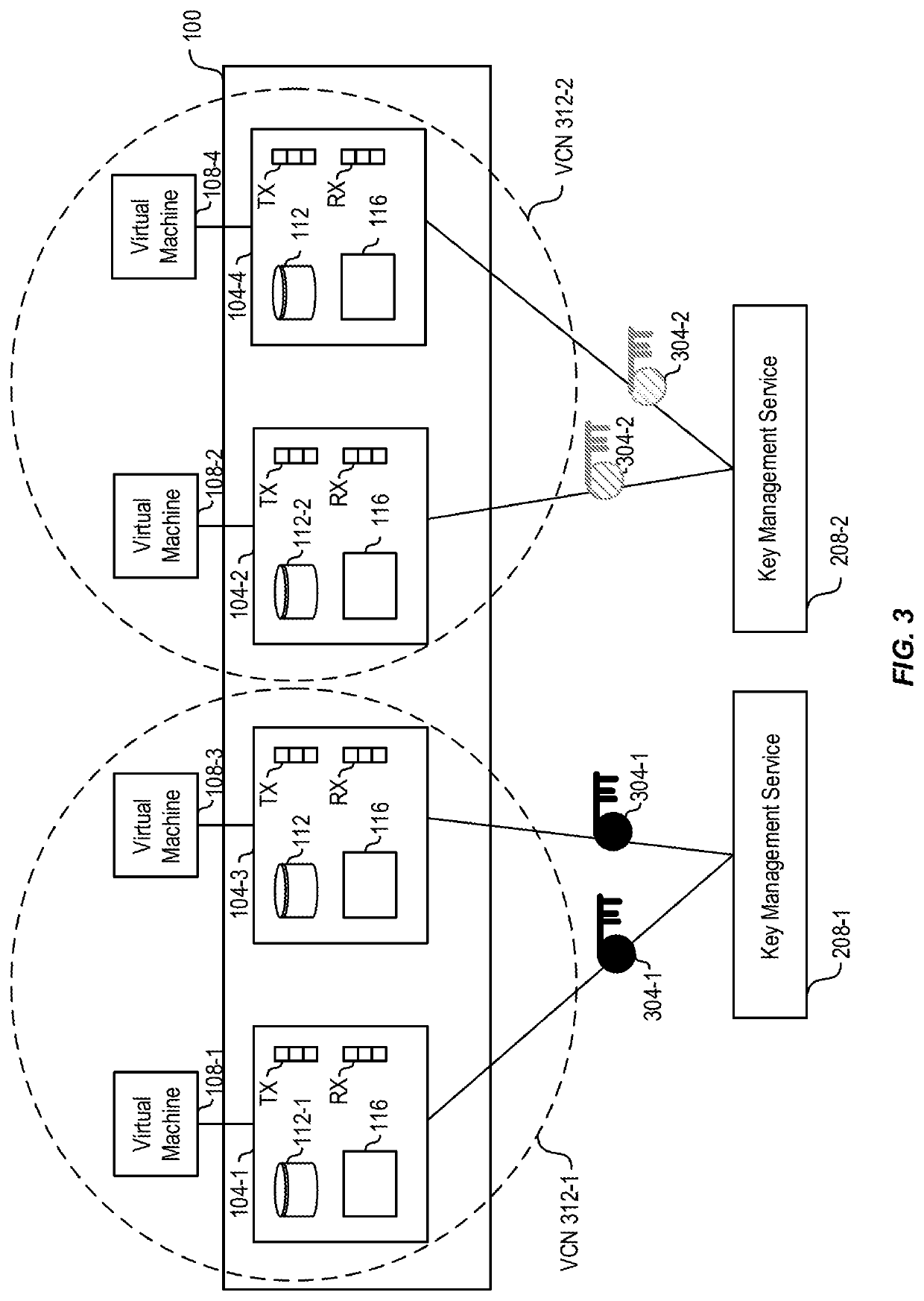
[0029]A virtual cloud network (VCN) is a customizable and private network. A host can provide computing hardware and / or software for a customer to set up a VCN. Typically, the host manages encryption, if any, for a VCN. A customer might not want the host to manage encryption because the customer could fear a data breach of the host could compromise customer data, or the customer might be concerned about how...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap