System and method of determining memory ownership on cache line basis for detecting self-modifying code including code with instruction that overlaps cache line boundaries
a cache line and memory ownership technology, applied in the field of system and memory ownership, can solve the problems of dcache, improper or unintended operation, smc subsequently modified,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
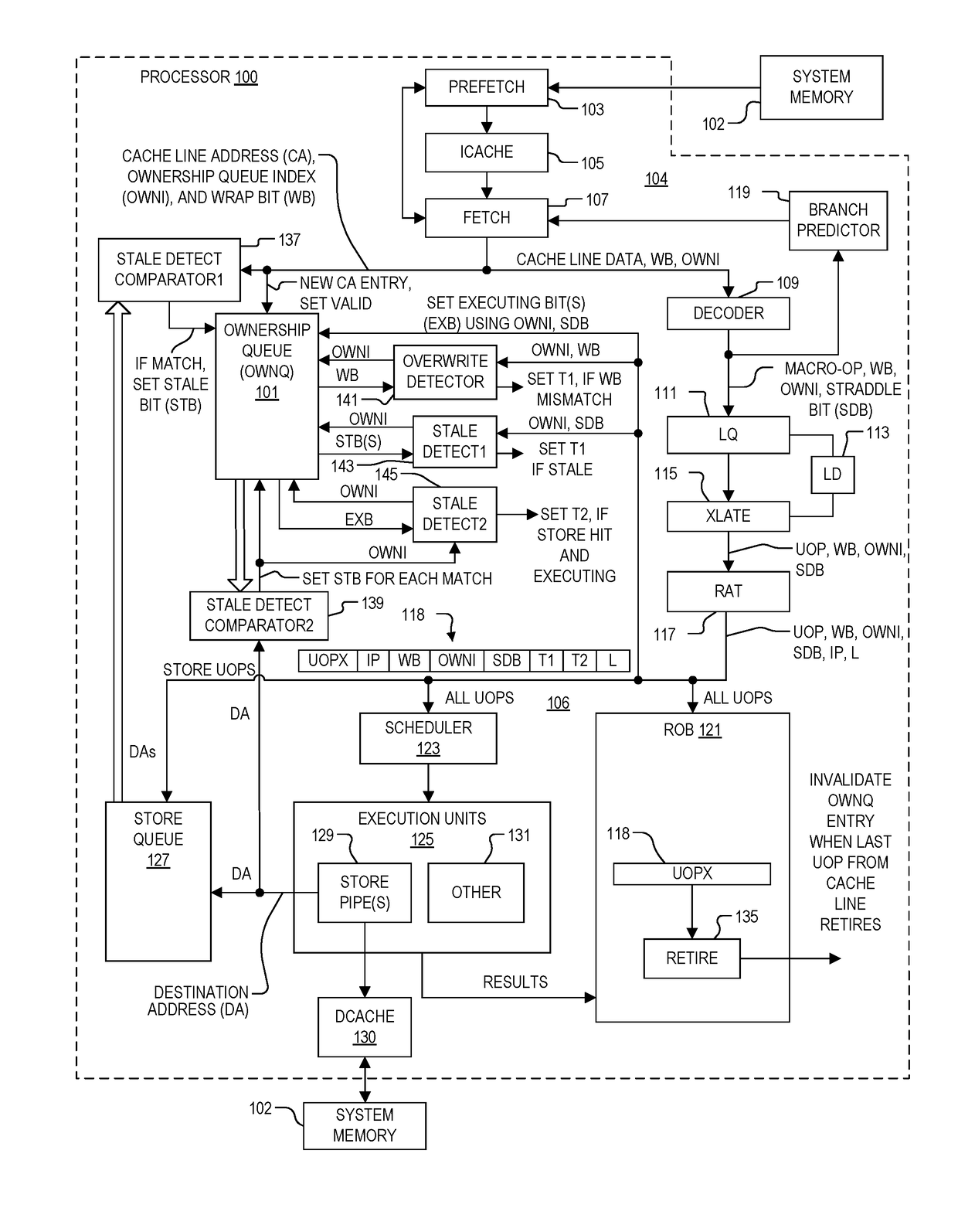
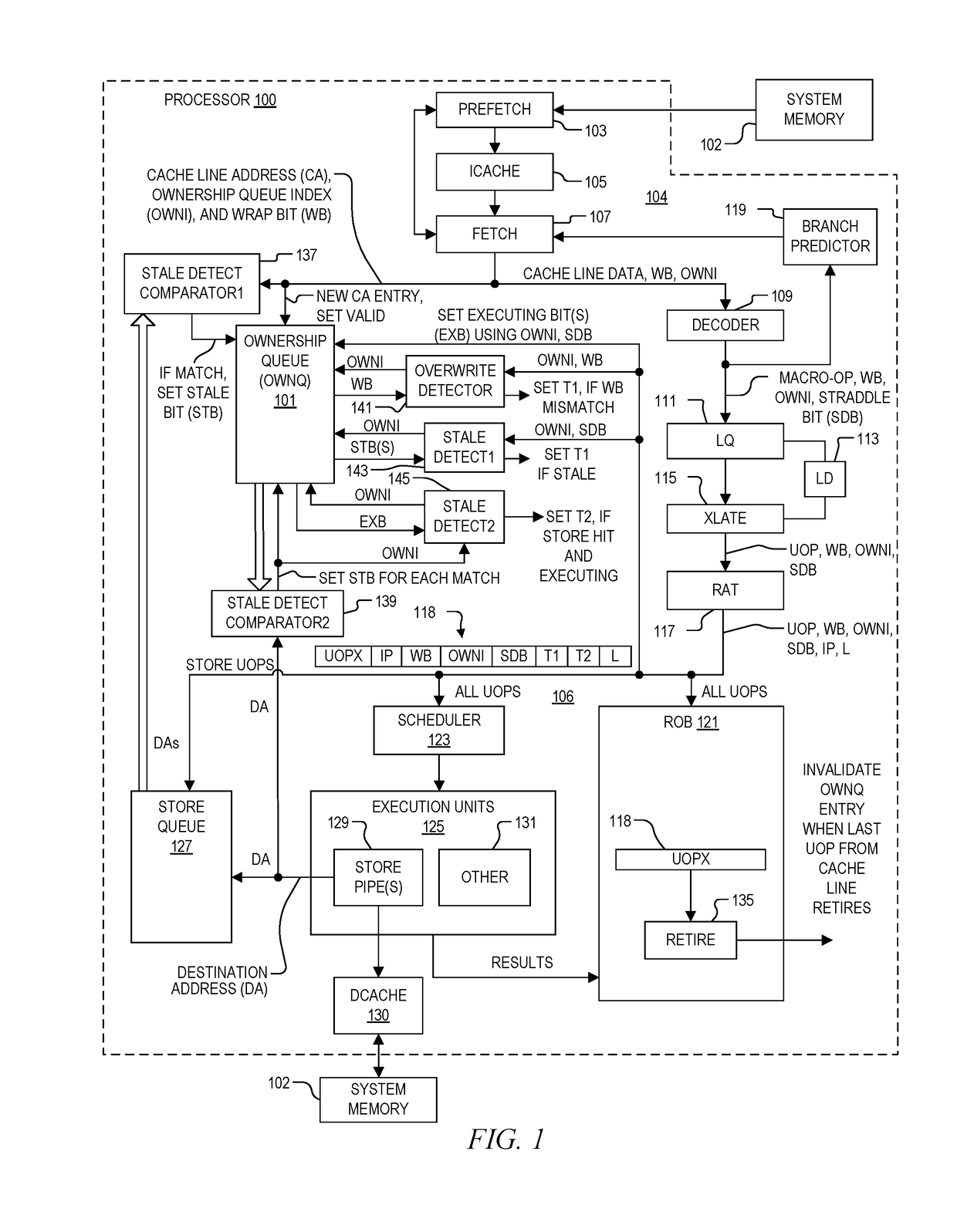
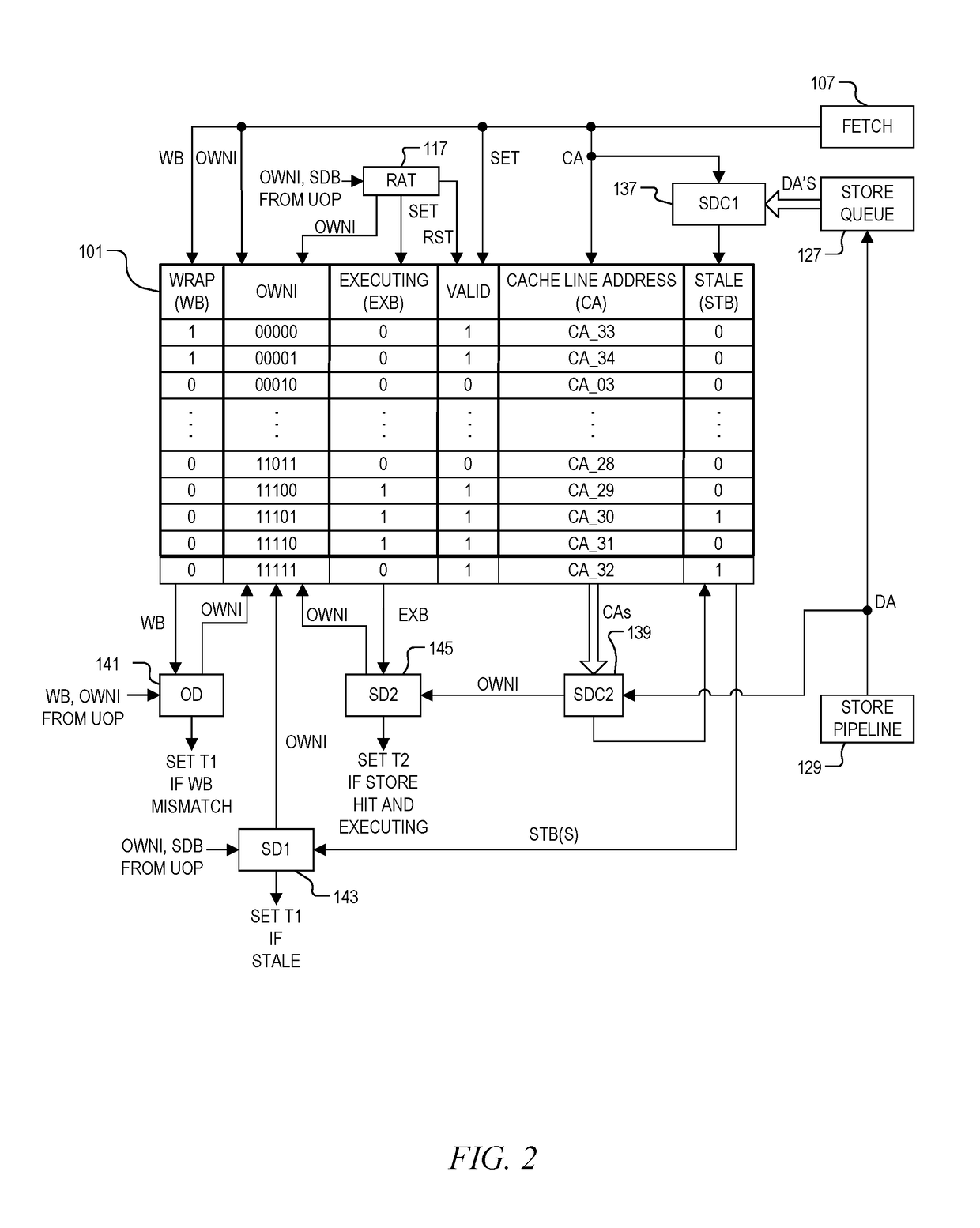
[0027]The inventors have recognized the problems of memory ownership in view of self-modifying code (SMC). They have therefore developed a system and method of establishing memory ownership on a cache line basis using an ownership queue which may be used for detecting SMC including code with one or more instructions that overlap cache line boundaries. An ownership index is determined for each cache line entered into the ownership queue. A processing front end sets a straddle bit for each instruction that was derived from cache line data that overlapped two cache lines in the ownership queue. The ownership index and straddle bit are included with each instruction issued for processing from a processor front end. A stale detection system sets a stale bit of an entry of the ownership queue that collides with a store instruction, and marks an issued instruction with a first exception when a stale bit of the corresponding entry in the ownership queue is set, or when a straddle bit of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com