Encryption method for program
A program and application technology, applied in the direction of instruments, electrical digital data processing, digital data processing components, etc., can solve the problems of not being able to guarantee that it will not be stolen, wasting money and time, and losing the rights of designers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
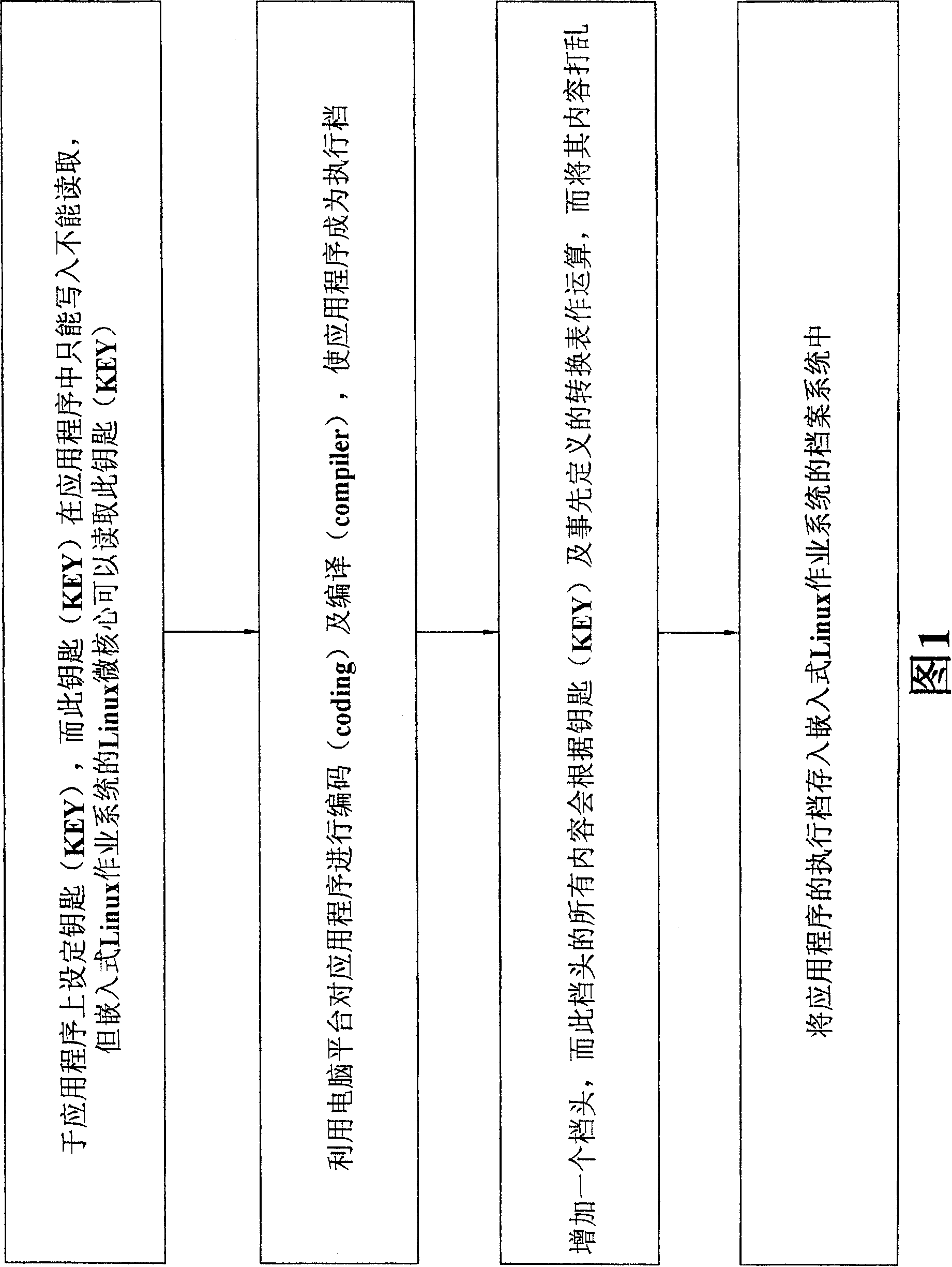
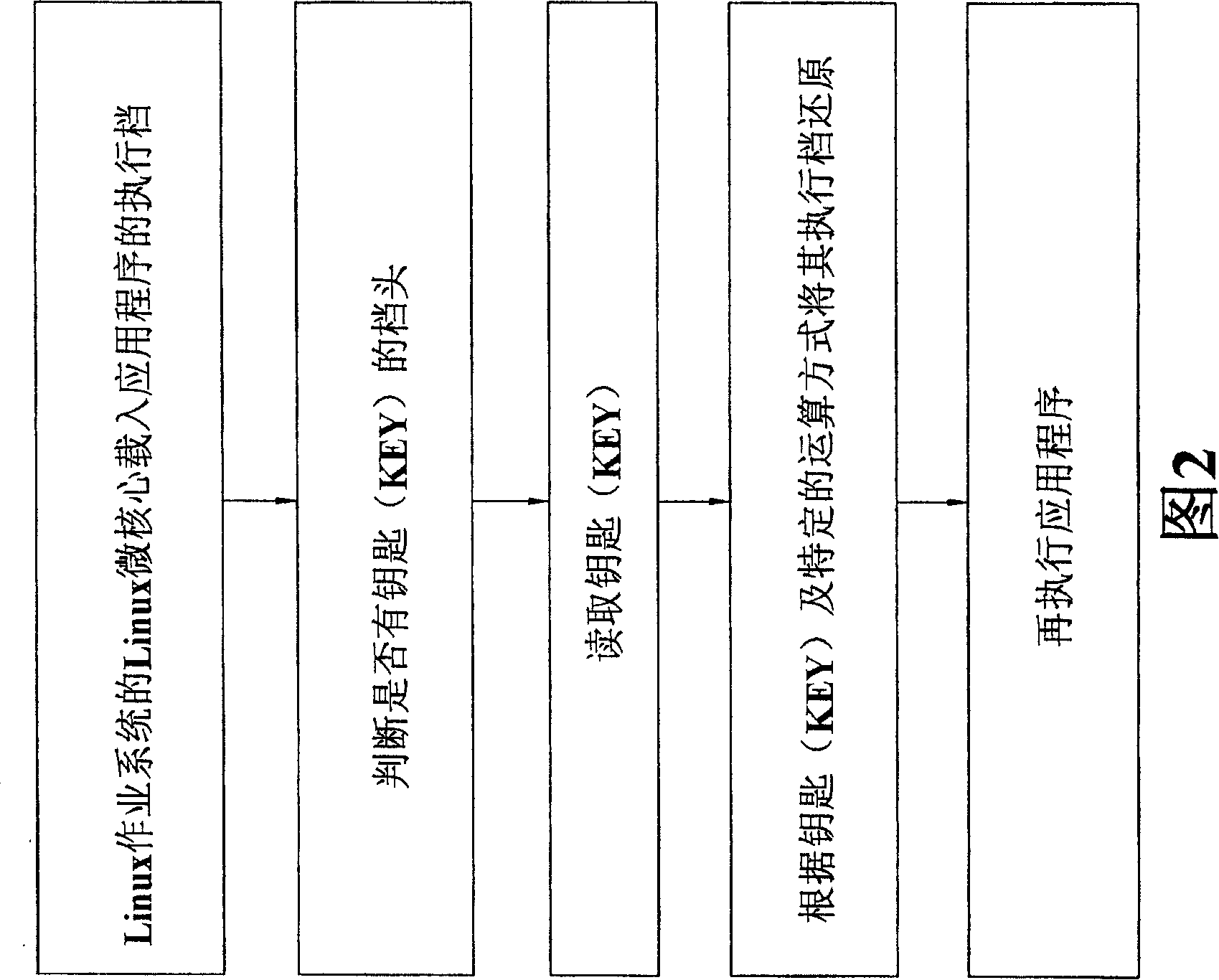
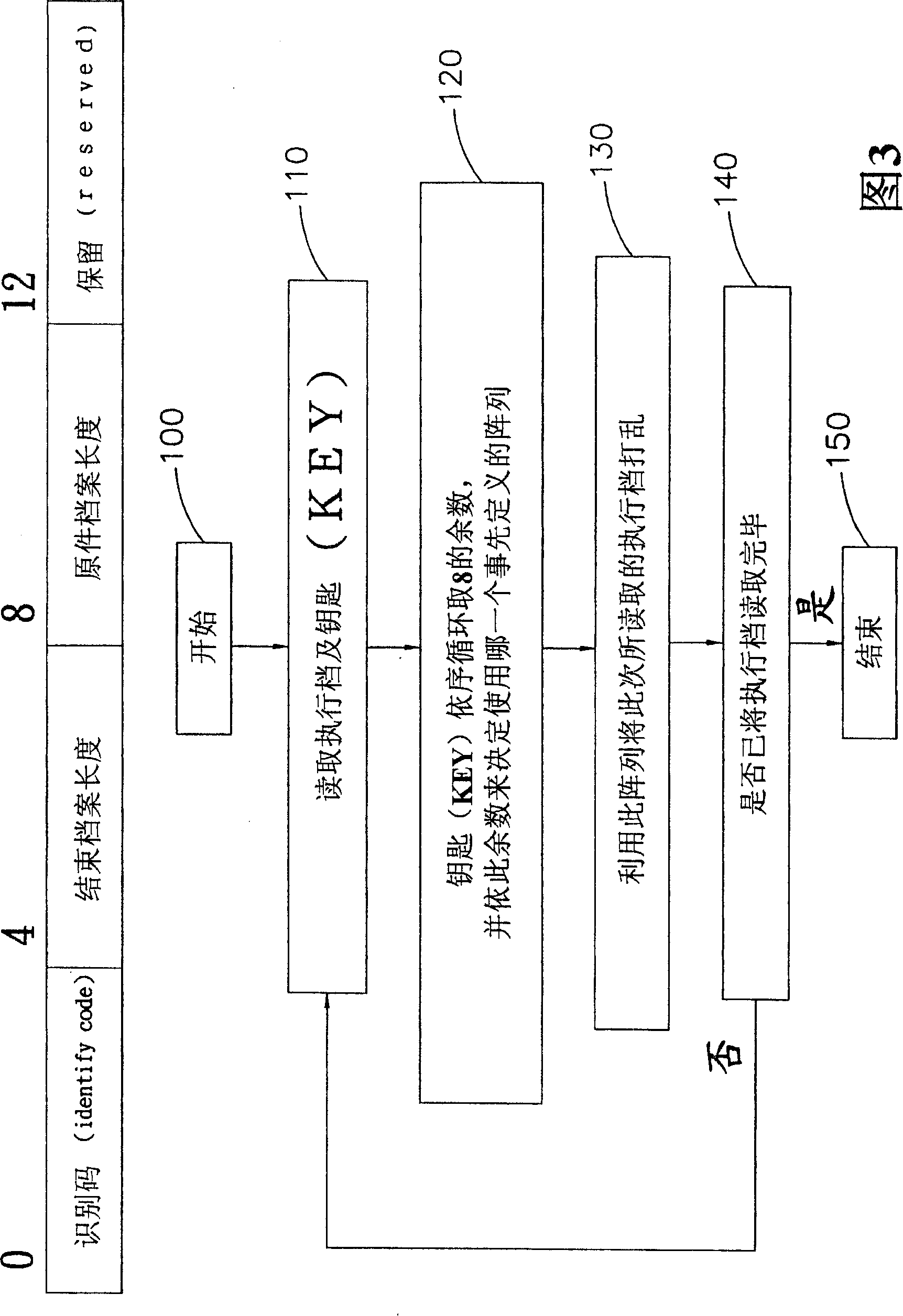
[0026] Please refer to shown in Fig. 1, it is the action flowchart of the present invention in use, can clearly find out from the figure, the present invention utilizes embedded Linux operating system (Embedded Linux System) as design platform, on the designed application program , set the key (KEY), and this key (KEY) can only be written and cannot be read in the application program, but the Linux microkernel (Kernel) of the embedded Linux operating system (EmbeddedLinux System) can read this key (KEY) ), and then use the computer platform to encode the application program (Coding: convert the input message sequence into a code sequence) and compile (Compiler: translate the original program into an executable program), so that the application program becomes an executable file, and continue the application software Add another file header to the execution file, and all the content of this file header will be calculated according to the key (KEY) and the conversion table define...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com