Controlling method of business operations authority
A business operation and authority control technology, applied in the computer field, can solve problems such as large system modification workload and hidden dangers of system stability, and achieve the effect of enriching authority control strategies, meeting the needs of dynamic business changes, and ensuring stability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
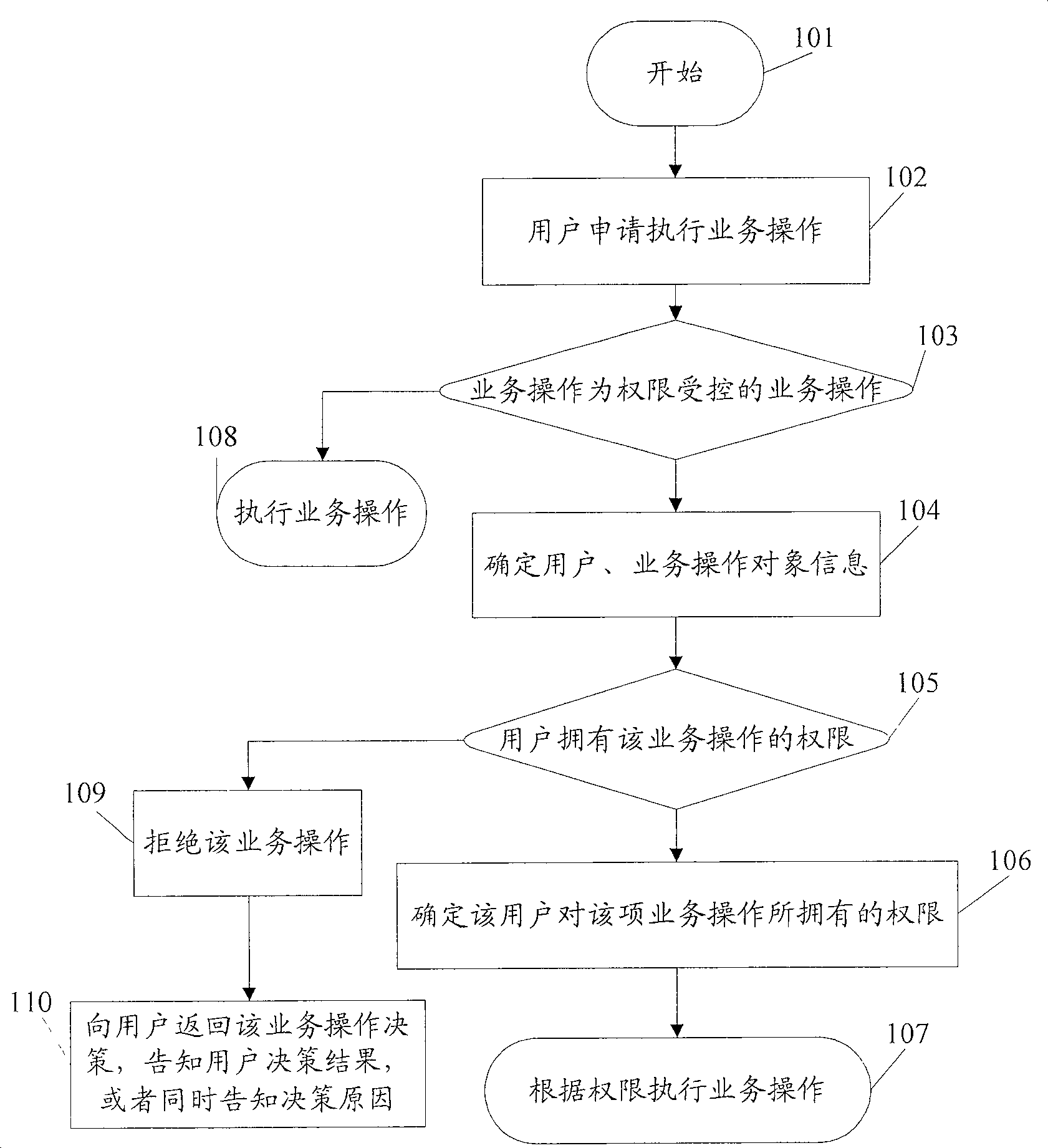
[0044] figure 1It is a schematic flow diagram of the business operation authority control method in this embodiment. As shown in the figure, this method is based on the authority in the relational database, the business operation object (corresponding function), and the subsystem, personnel and role where the business operation object is located. Corresponding relationship, carry out authority control, this method comprises the following steps:
[0045] Step 101: start.
[0046] The business system is in a waiting state, waiting for the user to input business operations.
[0047] Step 102: The user applies for executing a business operation.
[0048] The user submits a business operation application to the business system. The business operation can be the control of static objects such as menus, buttons, and interfaces, or data record-level operations such as querying, deleting, and updating business system data.
[0049] Step 103: Judging whether the business operation is...
Embodiment 2
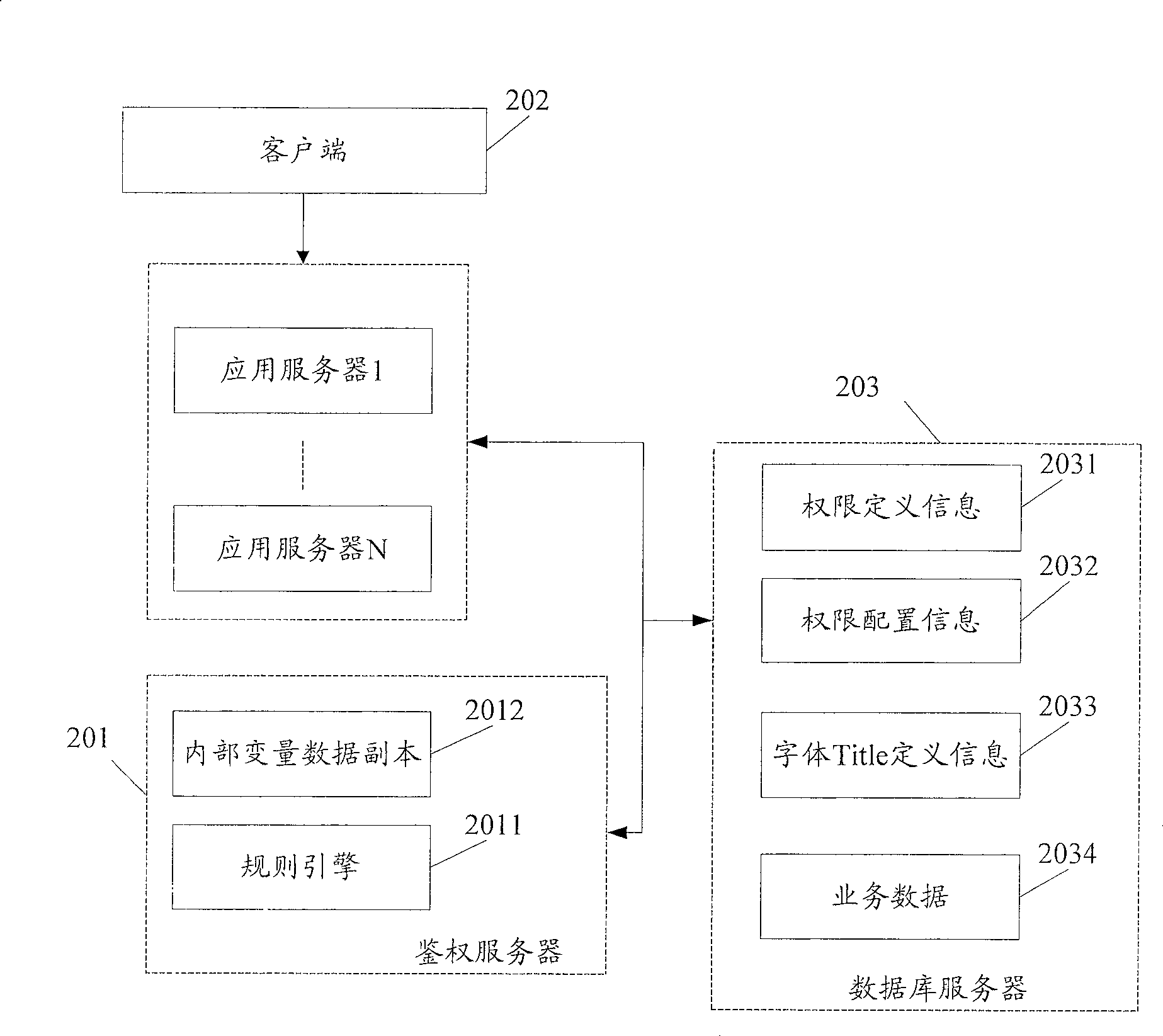
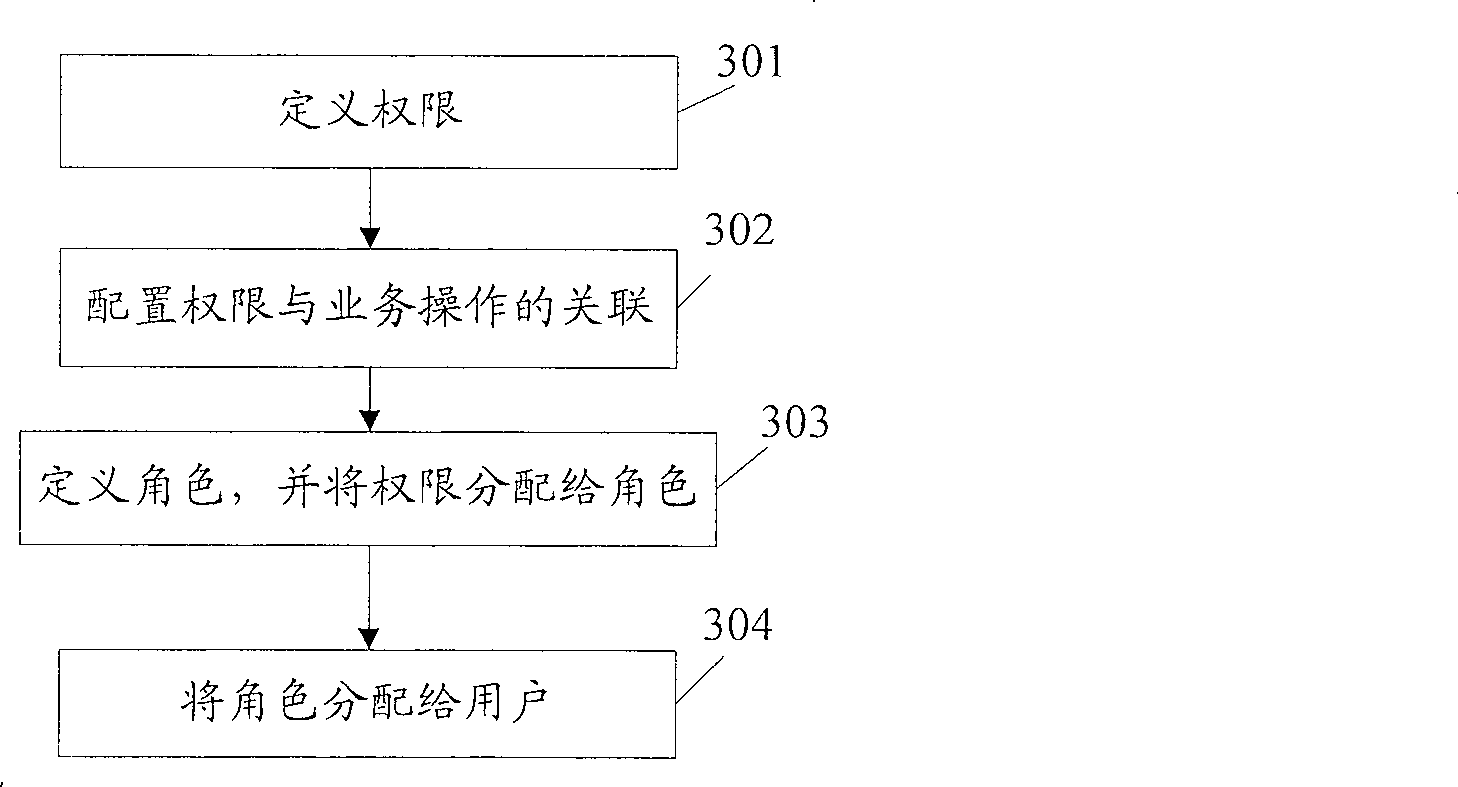
[0102] This embodiment specifically introduces the generation method of the relational database used for authority control, image 3 It is a schematic flowchart of a method for generating a relational database for authority control in this embodiment. As shown in the figure, this method includes the following steps:
[0103] Step 301: Define permissions.
[0104] Define the authority of the structure shown in Table 4, define the domain of semantic information in the authority, and use the semantic information as the authority control item, which becomes the inherent attribute of the authority. The semantic information includes constants, internal input objects, external input objects, logical operations and other custom information.
[0105] In order to facilitate the system to identify semantic objects, the following pre-definitions are made for each type of semantic objects:
[0106] First: For custom constant objects and internal objects, use specific prefix identificatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com