Configuration method of secure policy
A technology of security policy and configuration method, applied in the field of mobile communication and information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039]
[0040] Table 1
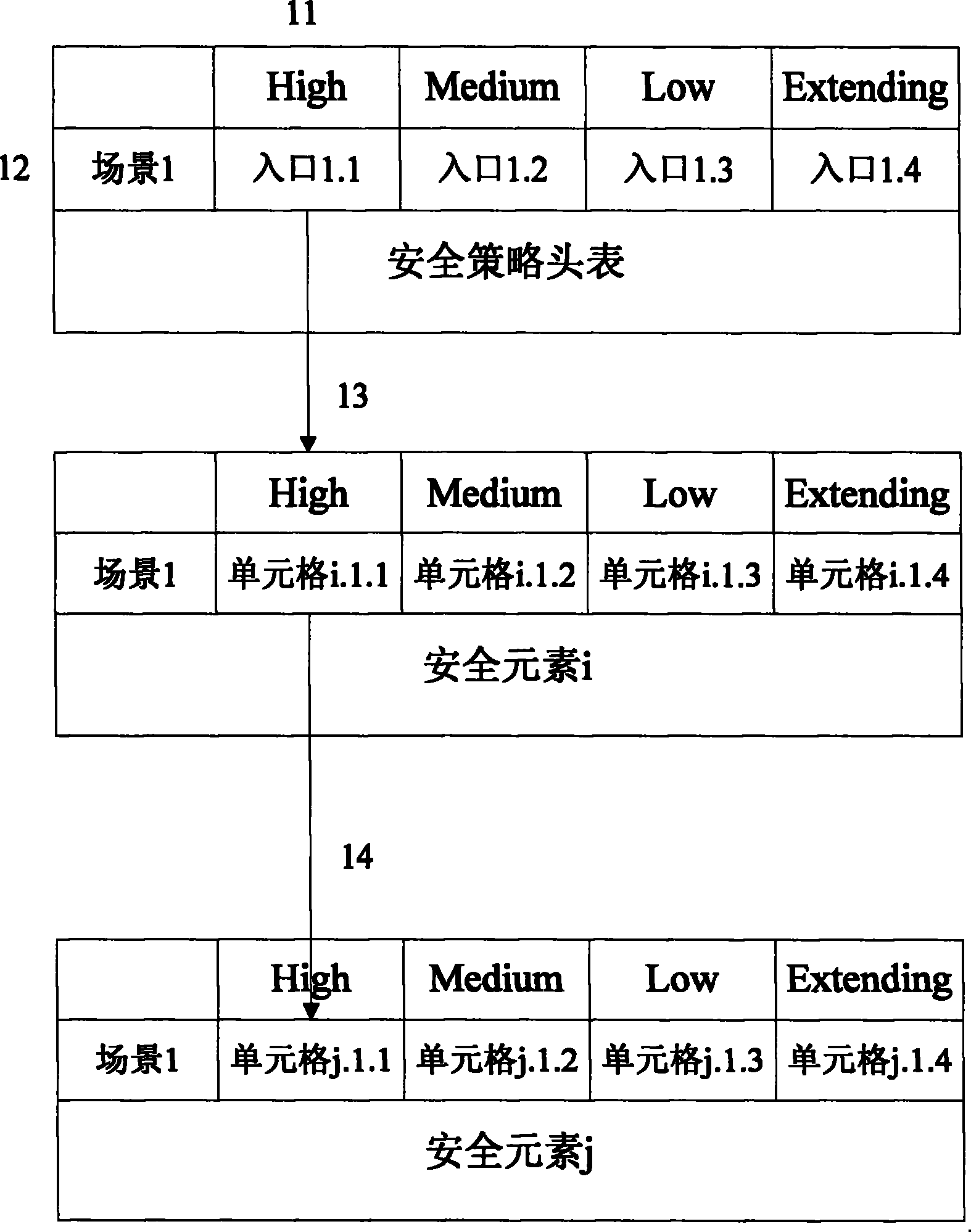
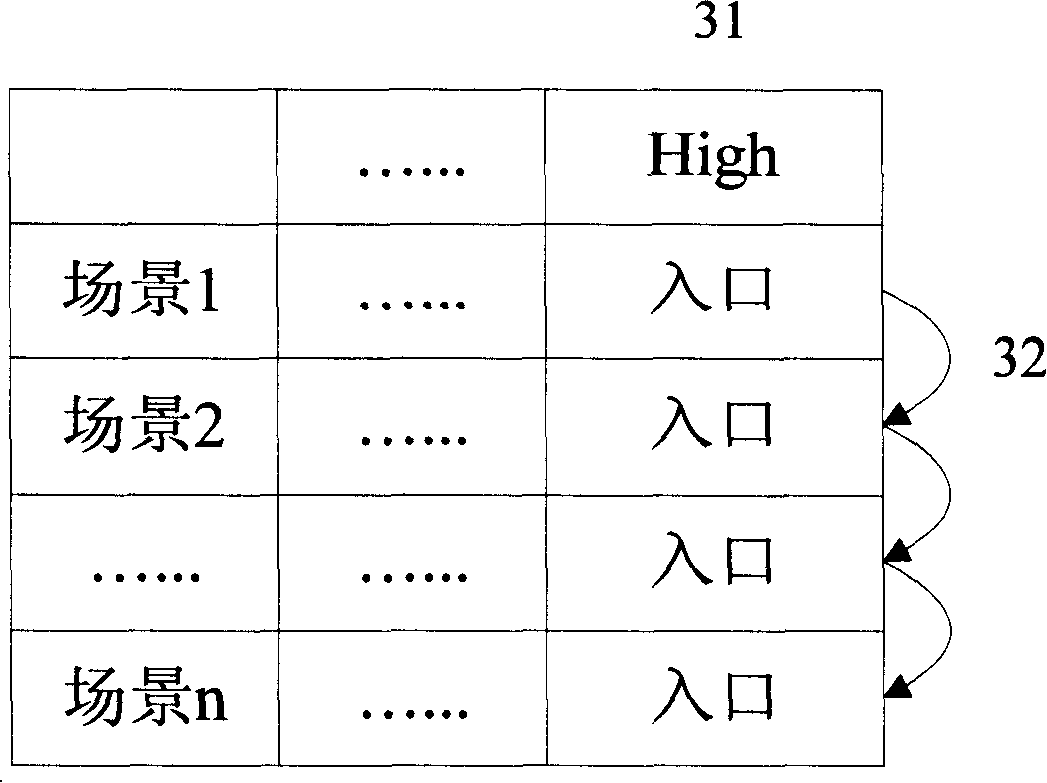
[0041] The security policy table includes: (1) security level, as a column (row) of the security policy table. (2) Scenario, which defines the abstraction of various services in terms of security, as a row (column) of the security policy table. (3) The entry is stored in the corresponding cell of the security policy table. Provides an entry point for collecting security algorithm protocols. Its input is the selected security level and scenario, and its output is the entry of the algorithm protocol. As shown in Table 2 below.
[0042]
[0043] Table 2
[0044] The relationship between the two layers of elements in the above two tables can be expressed as: f(x, y)=z. Among them, the independent variables x and y are security levels and scenarios, the dependent variable z is the output, and the function f is the mapping relationship between x, y and z.
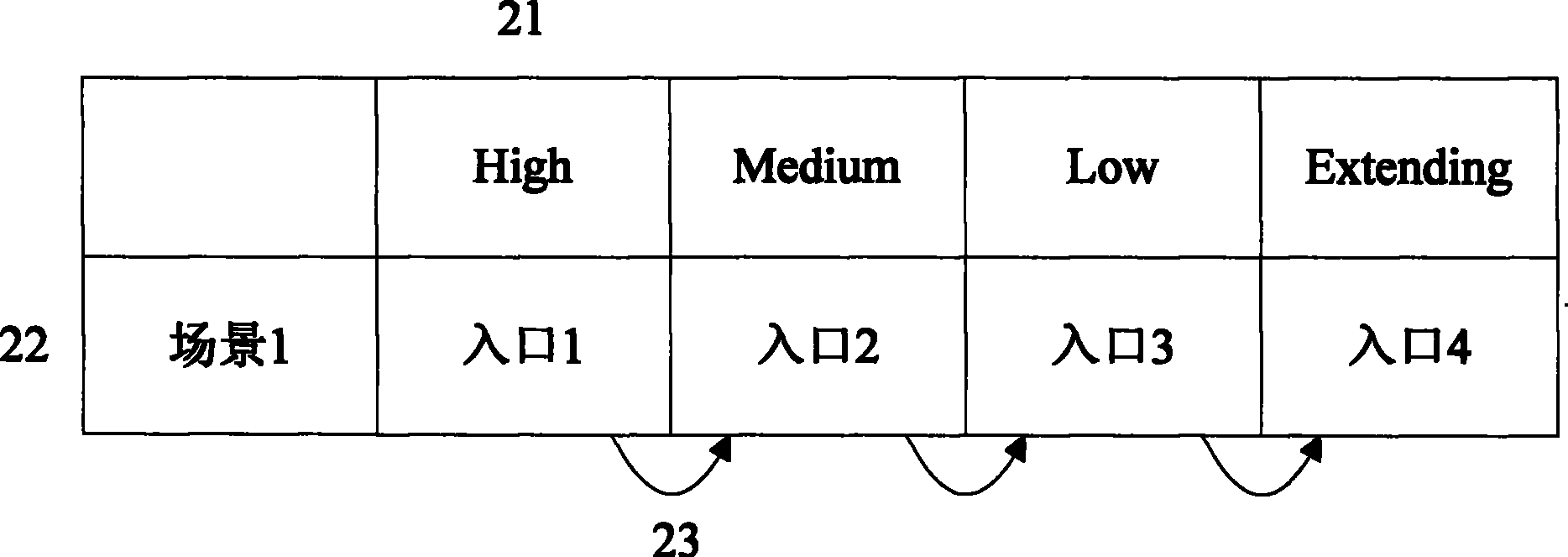
[0045] The security policy header table provides a unified entry when the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com