Configuration method of secure policy
A technology of security policy and configuration method, applied in the field of mobile communication and information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The specific implementation manners of the present invention will be described in further detail below in conjunction with the accompanying drawings.
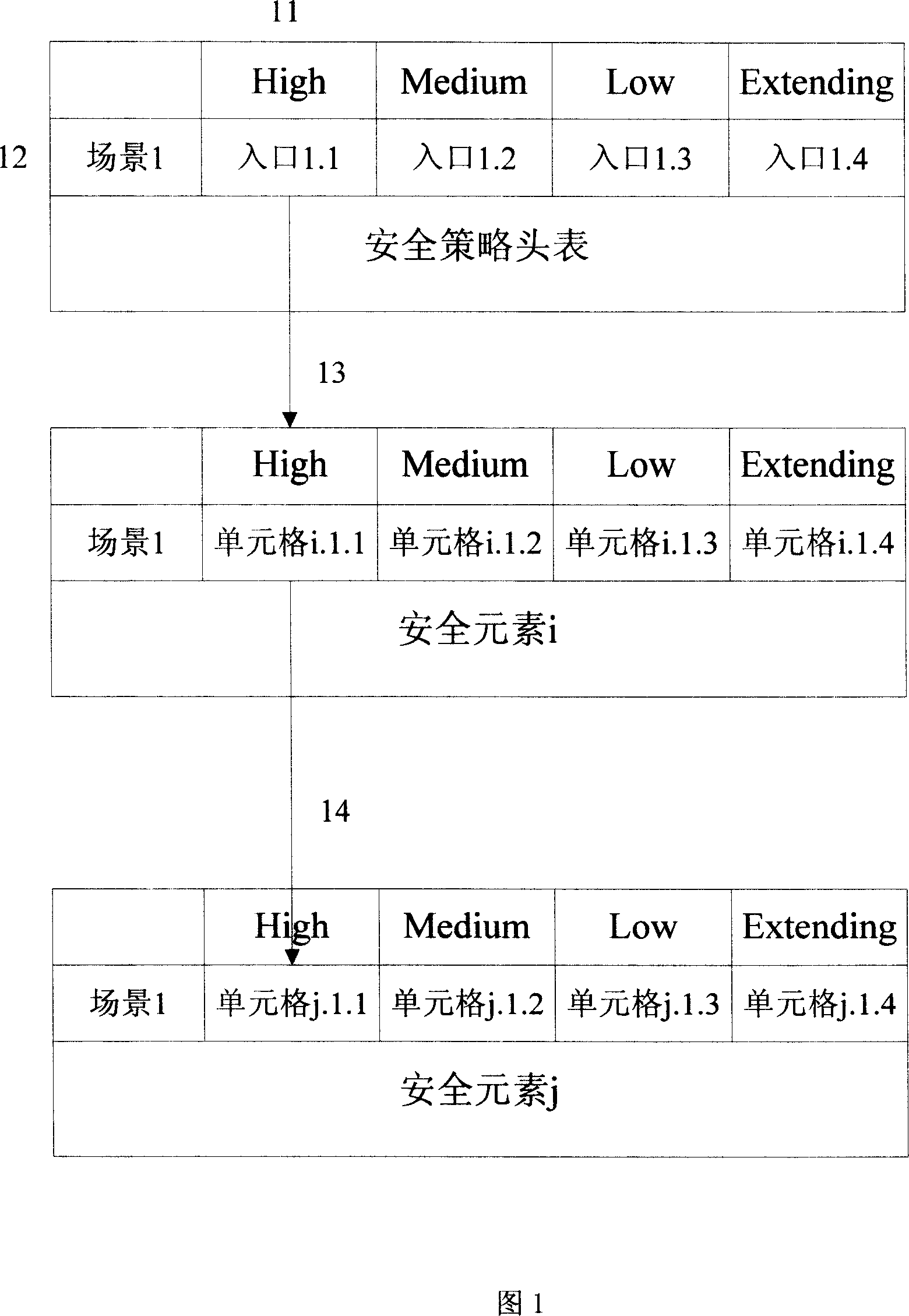
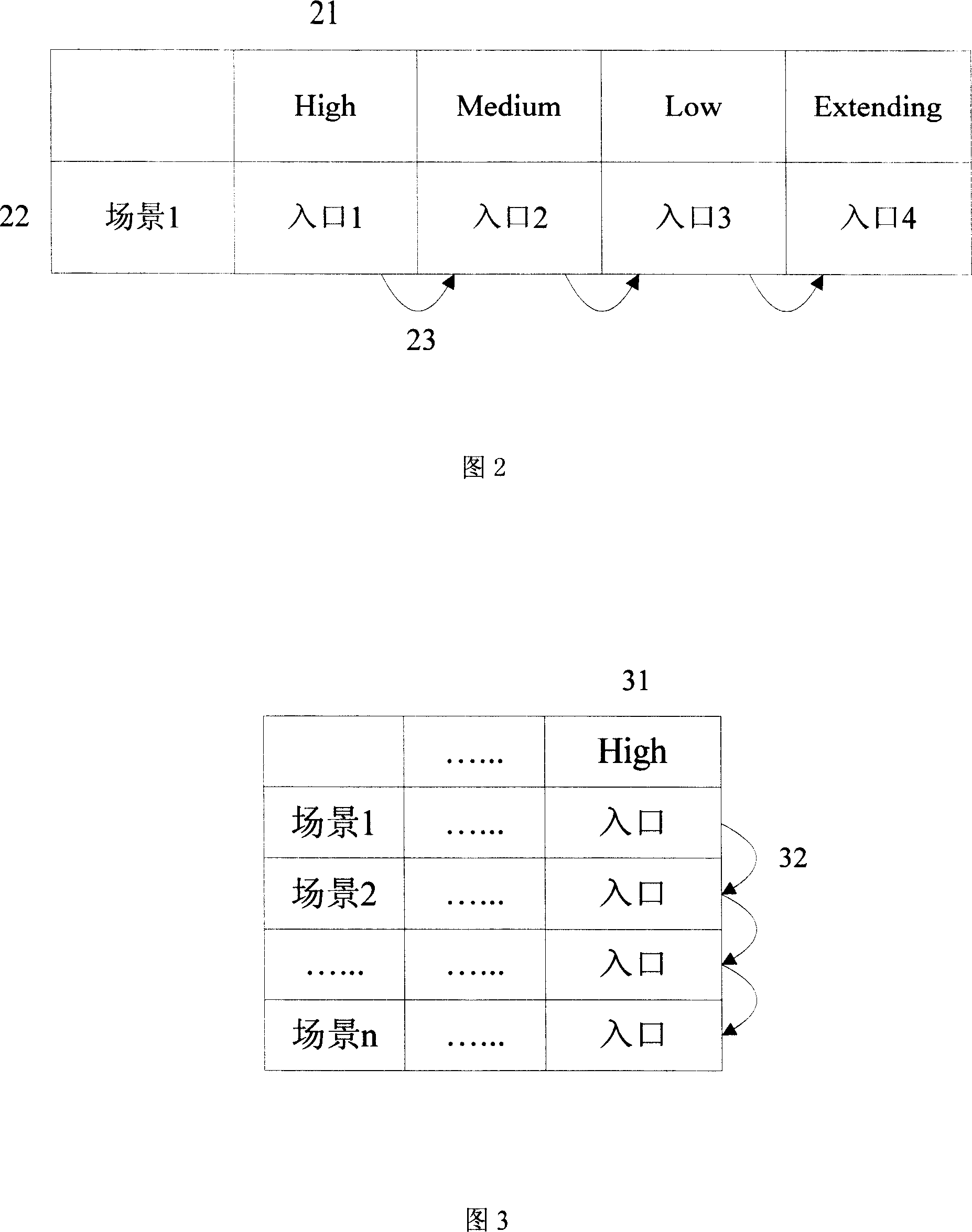
[0036] The division method of the security policy of the present invention is completed by the security policy table. The ITU-T's X805 standard describes eight security measures, called security elements, that can counter all major security threats. Includes access control, authentication, data confidentiality, communication security, data integrity, non-repudiation, availability, and privacy. According to the number of security elements, a security policy table is established for each security element. And before the security policy tables of all security elements, create a security policy header table.
[0037] Both the security policy header table and the security policy table described in the present invention are composed of two layers, wherein the security policy header table includes: (1) an input layer, includi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com