Method and device for packet flux monitoring
A message and flow technology, applied in the field of communication, can solve the problems of message discarding and obtaining enough tokens, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
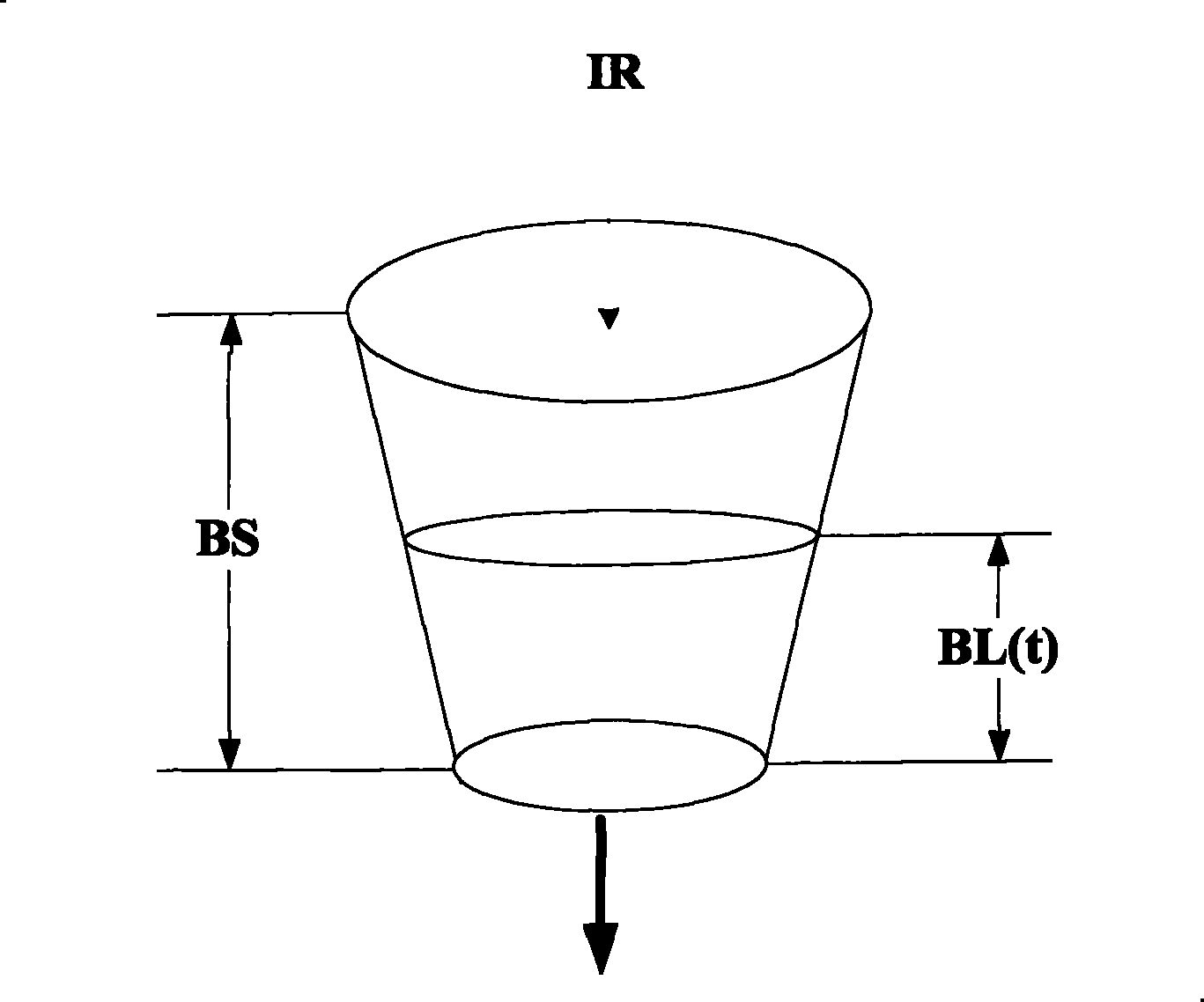
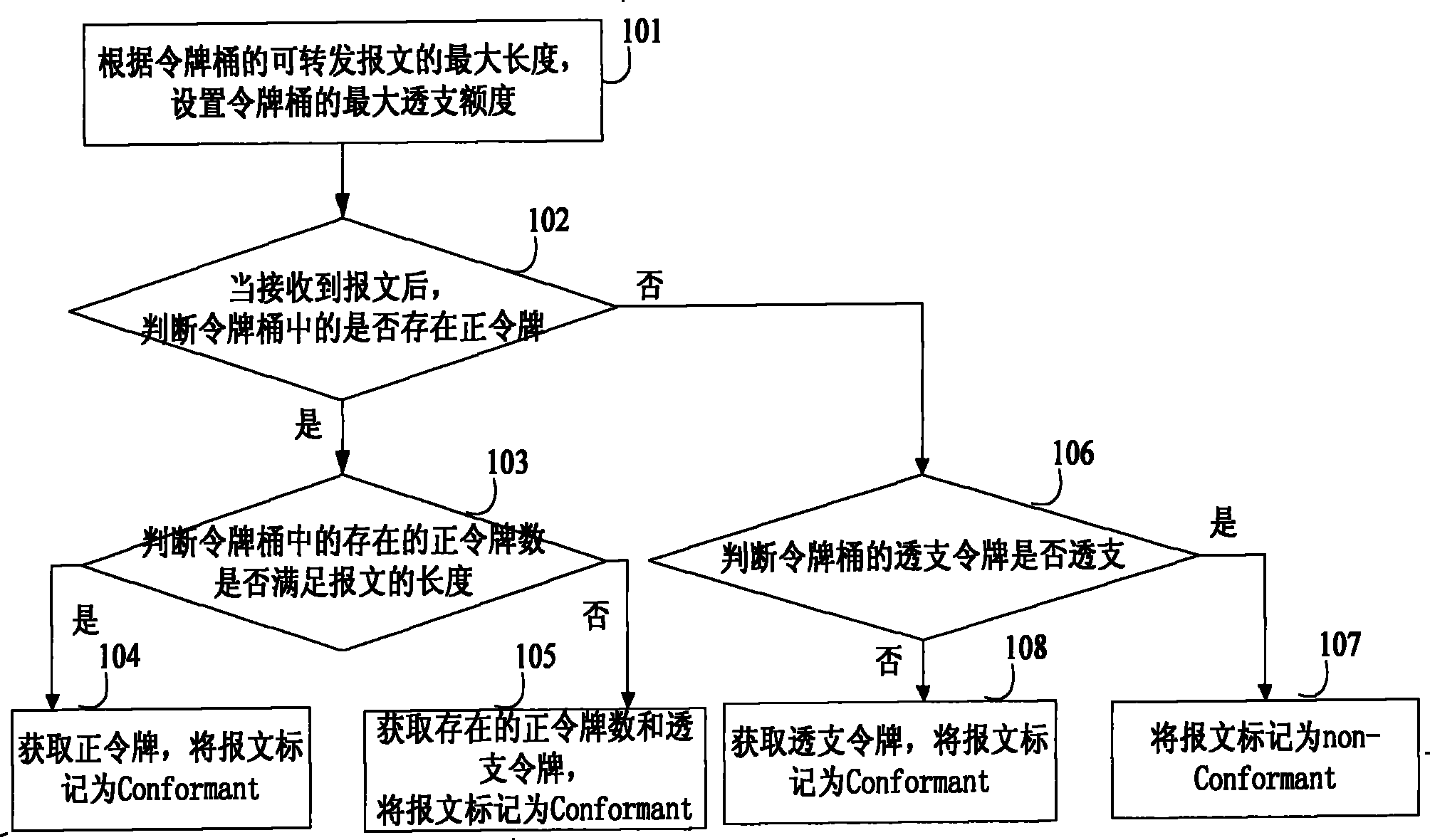
[0035] see image 3 , the embodiment of the present invention provides a method for traffic monitoring of messages. This embodiment takes obtaining tokens from a single token bucket as an example for illustration, and the details are as follows:
[0036] 101: Set the maximum overdraft limit of the token bucket according to the maximum length of the forwardable message of the token bucket.
[0037] Wherein, the maximum length of the message that can be forwarded by the token bucket is set as the maximum overdraft amount of the token itself, for example, the maximum length of the message that can be forwarded by the token bucket is 10240 bytes, then the maximum length of the token bucket The overdraft limit is 10240 bytes. When an overdraftable token is set for the token bucket, correspondingly, the value BL(tj) of the number of tokens in the token bucket can be negative. When it is negative, it means that the set overdraft token has been overdrawn, so , for token buckets, the...
Embodiment 2
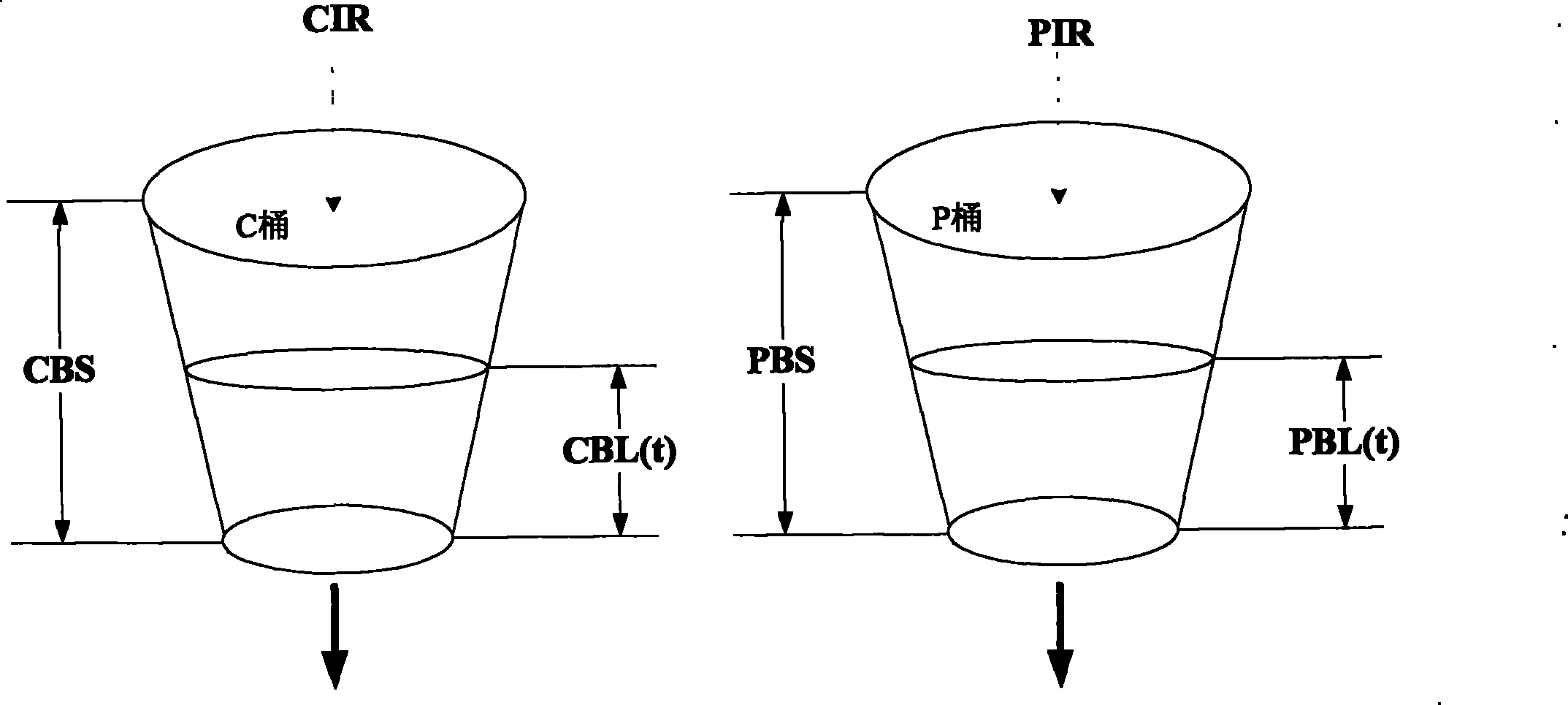
[0054] see Figure 5 , the embodiment of the present invention provides a method for traffic monitoring of messages. This embodiment takes token acquisition from a double token bucket (C bucket and P bucket) as an example, and uses the double token bucket as the color sense mode For example, please refer to the following content for details:
[0055] 201: According to the maximum length of the forwardable message of each token bucket, respectively set the maximum overdraft quota of the C token bucket and the P token bucket.
[0056] Among them, when setting the maximum overdraft quota of the C token bucket and the P token bucket, their values can be the same or different. For example, the maximum length of the message that can be forwarded by the C token bucket and the P token bucket is 10240 bytes , the maximum overdraft limit of the C token bucket and the P token bucket is 10240 bytes.
[0057] 202: Receive a message, judge whether the value of the token number in the P ...
Embodiment 3
[0068] see Figure 7 , the embodiment of the present invention provides a device for traffic monitoring of messages, the device includes:
[0069] The setting module is used to set the overdraft token in the token bucket;
[0070] The receiving module is used to receive the message and obtain the length of the message;
[0071] The acquisition module is used to determine whether the overdraft token of the token bucket is overdrawn when the length of the message is greater than the bucket depth of the token bucket, and if the judgment result is that the overdraft token of the token bucket is not overdrawn, then from the token bucket Obtain an overdraft token;
[0072] The forwarding module is configured to forward the message according to the token obtained from the token bucket, the token at least includes an overdraft token and corresponds to the length of the message.
[0073] In traffic monitoring, the single-token bucket mechanism and the double-token bucket mechanism a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com