Method for implementing computer terminal safety admittance based on credible authentication gateway
A computer terminal and computer technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of not being able to verify whether the other party is credible, unable to verify the real identity of the other party, etc., to achieve uniqueness and avoid illegal tampering Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention is further described as follows in conjunction with accompanying drawing and embodiment:
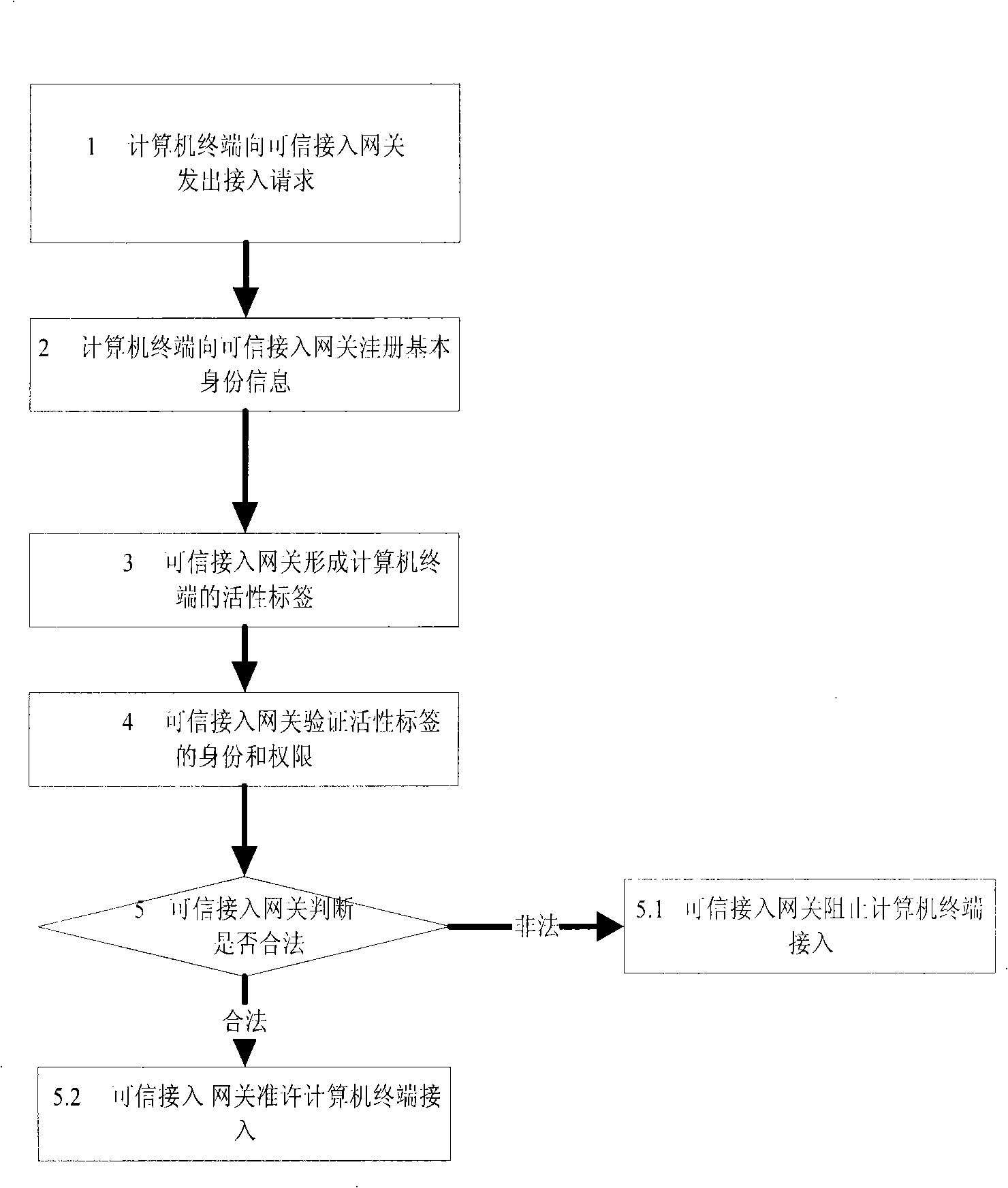
[0022] Such as figure 1 As shown, the described method for realizing security access of a computer terminal based on a trusted authentication gateway, the procedure is as follows: 1), the computer terminal sends an access request to the trusted authentication gateway; 2), the computer terminal sends an access request to the trusted authentication gateway; The gateway registers the basic identity information of the computer terminal, which is composed of hardware feature information and software feature information of the computer terminal; the hardware feature information of the computer terminal is machine identification, network card hardware number, hard disk serial number and hard disk data features , optical drive type and serial number, USB information, sound card information, graphics card information, when the hardware feature information is two of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com